2019-03-15 - QUICK POST: CHANGE IN PATTERNS FOR EMOTET POST-INFECTION TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- On 2019-03-14 as early as 21:43 UTC, Emotet started generated new post-infection traffic patterns, with HTTP POST requests instead of GET requests.
- The pcap from 2019-03-14 starts out with the previous post-infection traffic patterns for Emotet, but these patterns change at 21:43 UTC.
ASSOCIATED FILES:
- 2019-03-14-Emotet-with-Trickbot-infection-traffic.pcap.zip 15.8 MB (15,772,047 bytes)
- 2019-03-14-Emotet-and-Trickbot-malware-and-artifacts.zip 12.2 MB (12,238,690 bytes)
- 2019-03-15-Emotet-malspam-8-examples.zip 1.3 MB (1,318,311 bytes)
- 2019-03-15-attachments-from-Emotet-malspam-8-examples.zip 1.2 MB (1,227,633 bytes)
- 2019-03-15-1st-run-Emotet-infection-traffic-no-follow-up-malware.pcap.zip 1.8 MB (1,833,232 bytes)
- 2019-03-15-1st-run-Emotet-malware.zip 545 kB (545,014 bytes)
- 2019-03-15-2nd-run-Emotet-infection-traffic-with-Trickbot.pcap.zip 4.6 MB (4,604,520 bytes)
- 2019-03-15-2nd-run-Emotet-and-Trickbot-malware-and-artifacts.zip 4.0 MB (4,001,705 bytes)
IMAGES
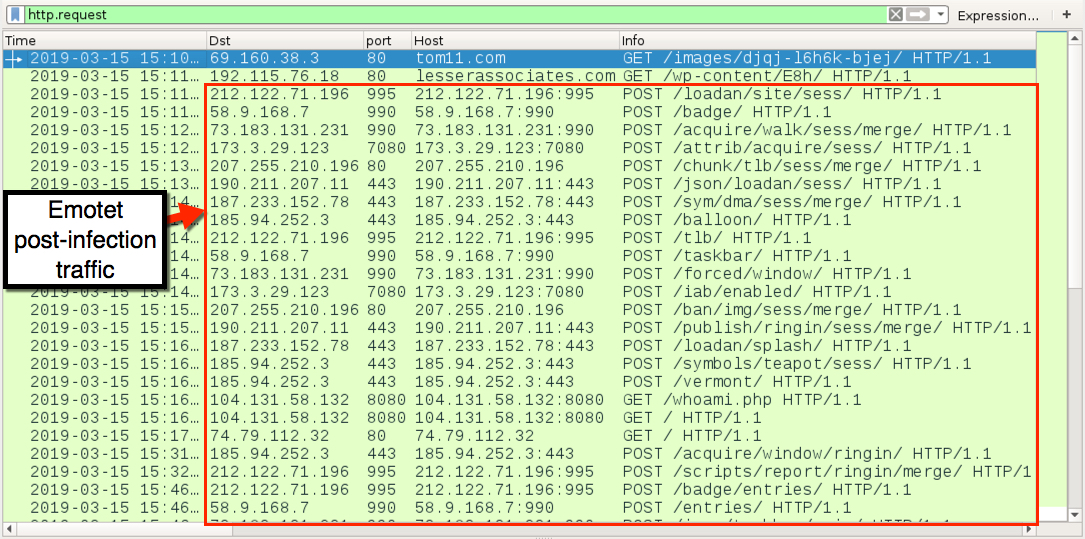
Shown above: Example of current Emotet post-infection traffic as seen in Wireshark.
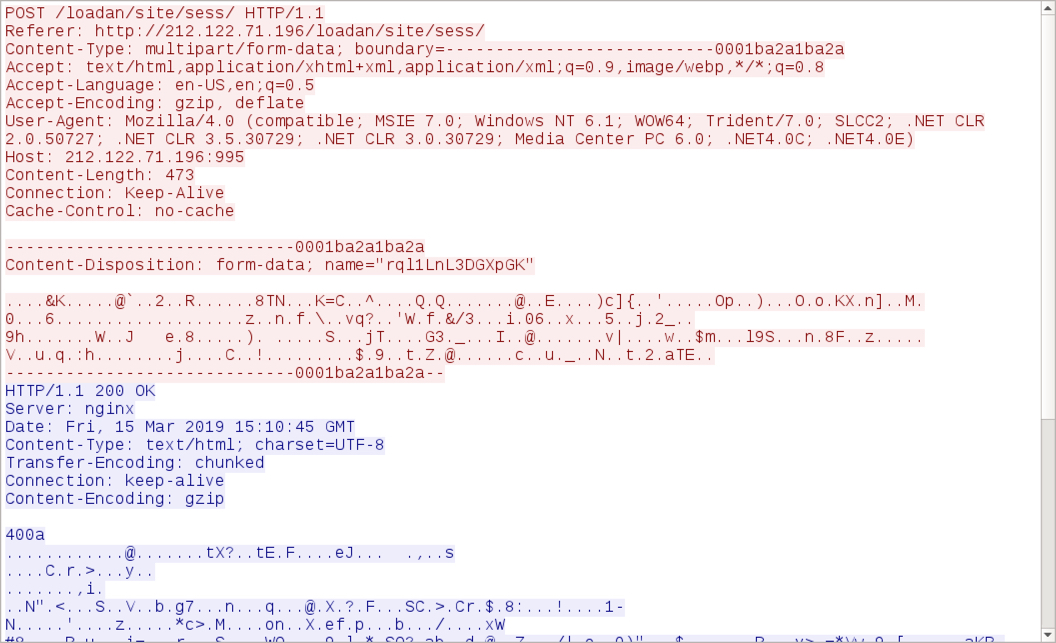
Shown above: TCP stream showing an example of current Emotet post-infection traffic.
Click here to return to the main page.
