2019-03-15 - MALSPAM PUSHES LOKIBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2019-03-15-Lokibot-malspam-0134-UTC.eml.zip 476 kB (476,242 bytes)
- 2019-03-15-Lokibot-infection-traffic.pcap.zip 4.1 kB (4,147 bytes)
- 2019-03-15-Lokibot-malware.zip 821 kB (821,073 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic related to this malware, I suggest the following URL:
- hxxp[:]//atelierdodoce.com[.]br/images/bannerss/fre.php
MALSPAM EXAMPLE
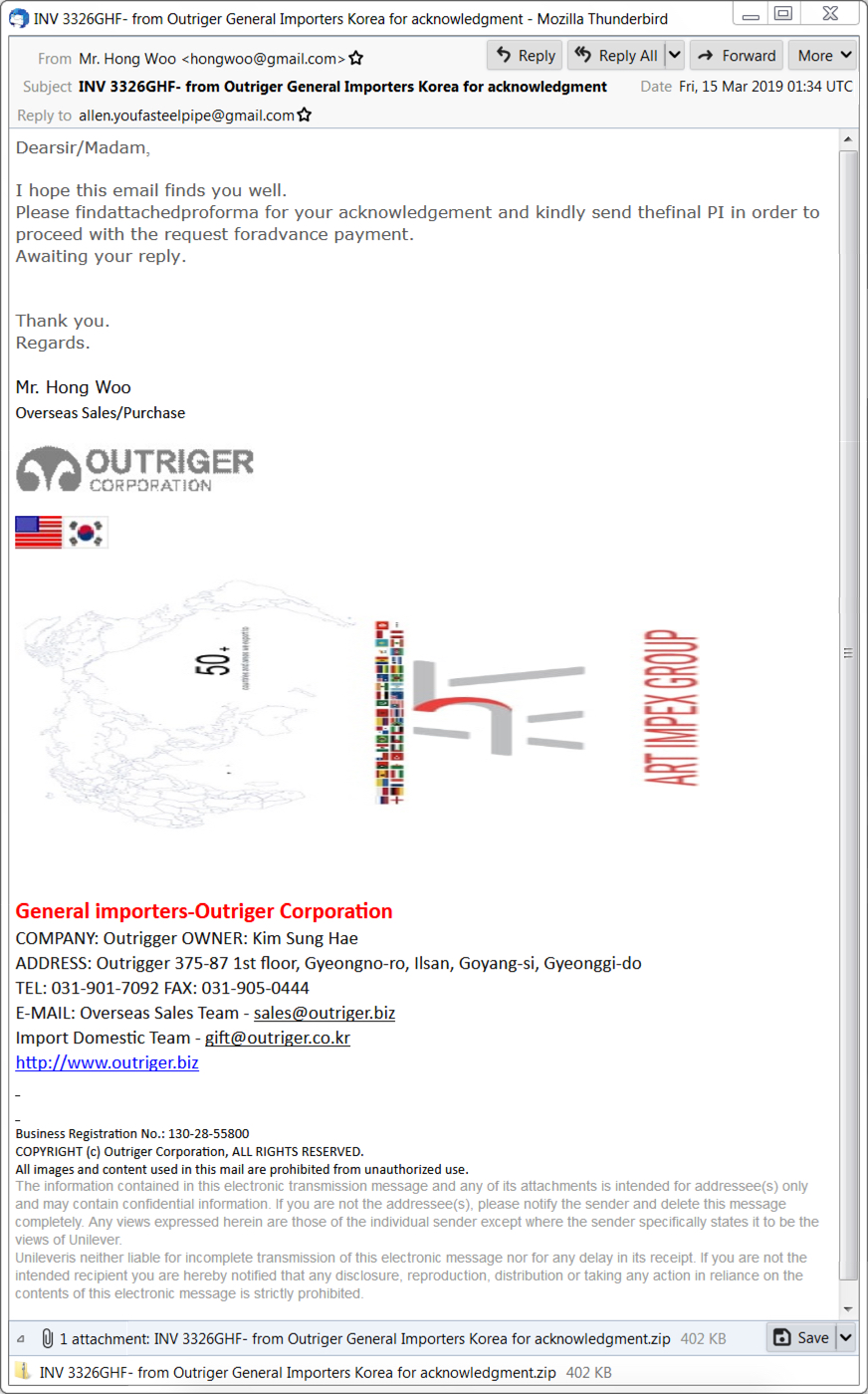
Shown above: Screenshot from the malspam.
HEADERS FROM TODAY'S LOKIBOT MALSPAM EXAMPLE
Authentication-Results: [removed]; iprev=pass policy.iprev="165.227.181[.]253"; spf=softfail smtp.mailfrom="hongwoo@gmail[.]com" smtp.helo="centos-s-2vcpu-4gb-nyc3-03"; dkim=none (message not signed) header.d=none; dmarc=fail (p=none; dis=none) header.from=gmail[.]com
Received: from [165.227.181.253] ([165.227.181.253:41356] helo=centos-s-2vcpu-4gb-nyc3-03)
by [removed] (envelope-from <hongwoo@gmail[.]com>) [removed];
Thu, 14 Mar 2019 21:42:49 -0400
Received: from [102.165.35[.]45] (helo=User)
by centos-s-2vcpu-4gb-nyc3-03 with esmtpa (Exim 4.91)
(envelope-from <hongwoo@gmail[.]com>)
id 1h4bkR-00031v-Qc; Fri, 15 Mar 2019 01:35:01 +0000
Reply-To: <allen.youfasteelpipe@gmail[.]com>
From: "Mr. Hong Woo"<hongwoo@gmail[.]com>
Subject: INV 3326GHF- from Outriger General Importers Korea for acknowledgment
Date: Fri, 15 Mar 2019 01:34 UTC
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="----=_NextPart_000_00D1_01C2A9A6.71AA6BD8"
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
Message-Id: <E1h4bkR-00031v-Qc@centos-s-2vcpu-4gb-nyc3-03>
MALWARE
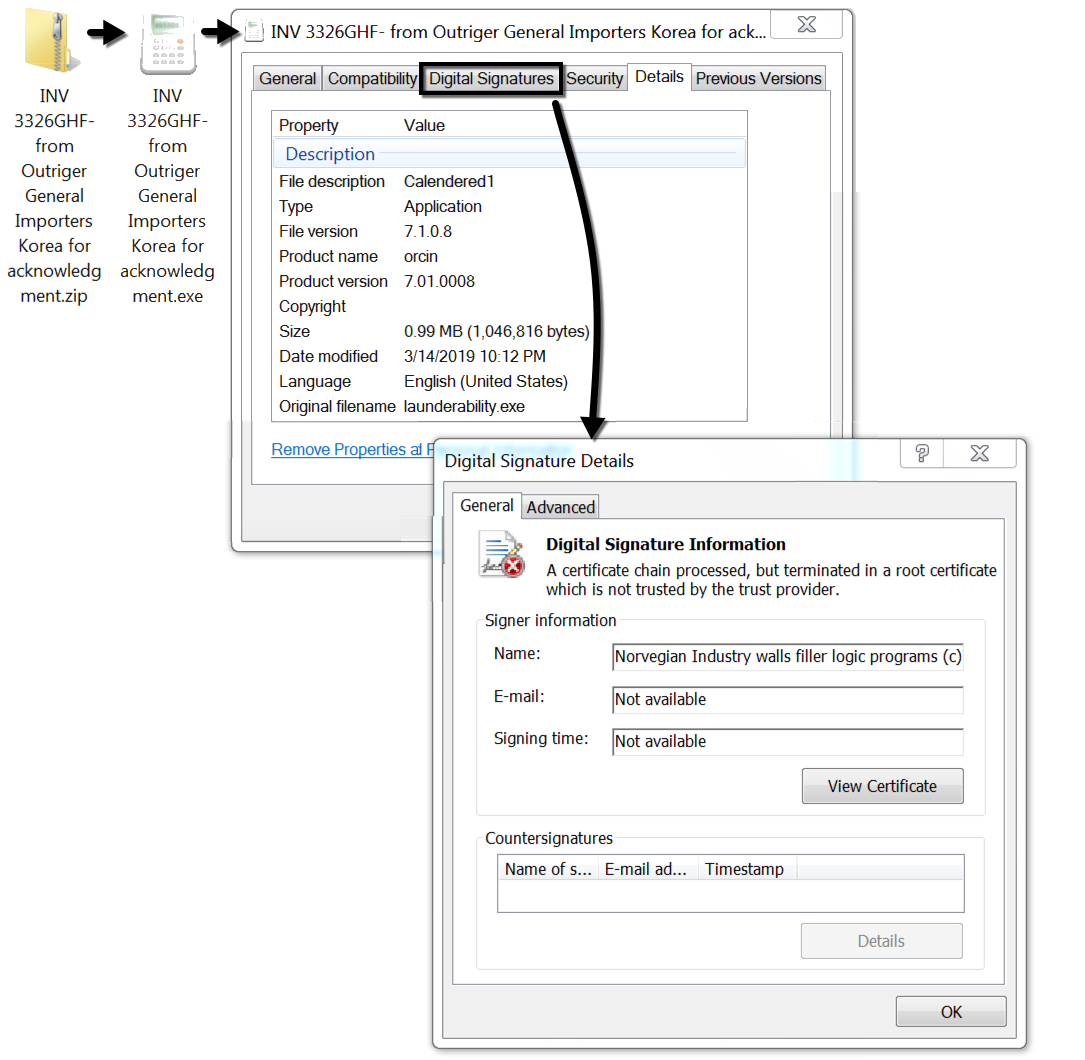
Shown above: Lokibot malware extracted from the attached zip archive.
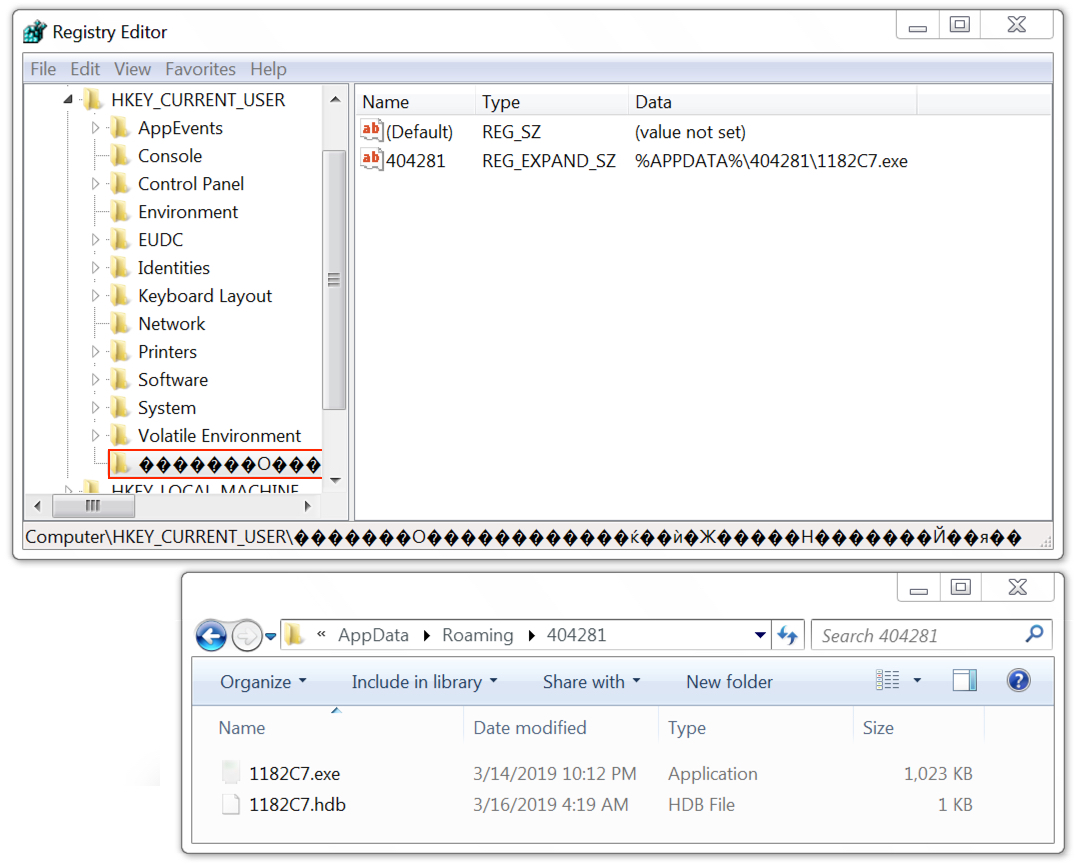
Shown above: Lokibot malware persistent on an infected Windows host.
MALWARE FROM AN INFECTION:
- SHA256 hash: 38ac35fd95358b84cd91d9ba55ceda9039dde7d908fb1ac736aa332d6d7d9e28
File size: 411,580 bytes
File name: INV 3326GHF- from Outriger General Importers Korea for acknowledgment.zip
File description: Zip archive attached to the malspam
- SHA256 hash: b7ef644b7883bbbbf5f0869b193d22190260570606646e61099a7df383144b41
File size: 1,046,816 bytes
File name: INV 3326GHF- from Outriger General Importers Korea for acknowledgment.exe
File location after infection: C:\Users\[username]\AppData\Roaming\[random hex string]\[random hex string].exe
File description: Lokibot malware--a Windows executable extracted from the above zip archive.
TRAFFIC
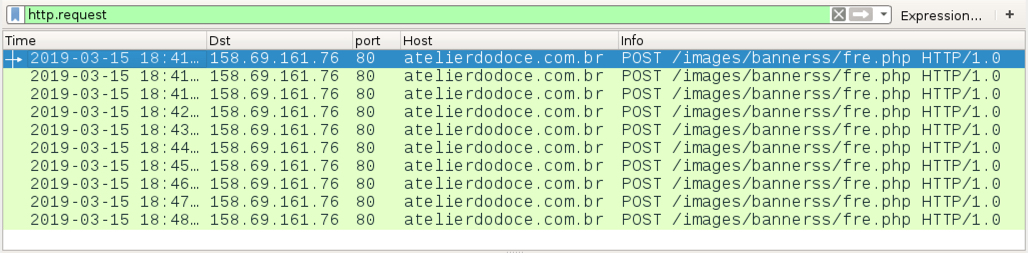
Shown above: Traffic from an infection filtered in Wireshark.
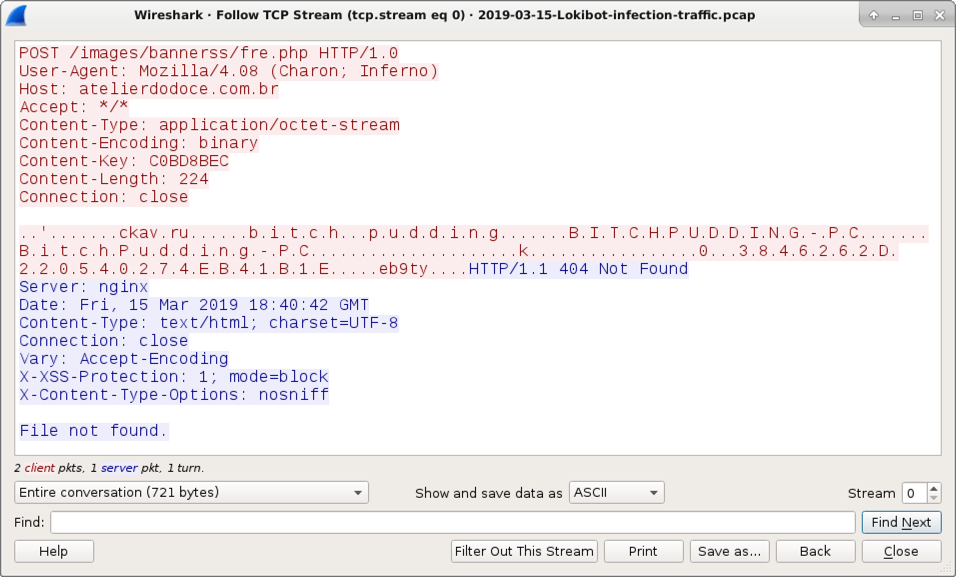
Shown above: TCP stream of the first HTTP request caused by this Lokibot sample.

TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 158.69.161[.]76 port 80 - atelierdodoce.com[.]br - POST /images/bannerss/fre.php
Click here to return to the main page.
