2019-03-20 - ANOTHER EXAMPLE OF SPELEVO EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the infection traffic: 2019-03-20-Spelevo-EK-sends-malware.pcap.zip 9.5 MB (9,461,802 bytes)
- 2019-03-20-Spelevo-EK-sends-malware.pcap (11,516,936 bytes)
- Zip archive of the malware & artifacts: 2019-03-20-Spelevo-EK-malware-and-artifacts.zip 3.5 MB (3,498,008 bytes)
- 2019-03-20-Spelevo-EK-HTML-with-iframe-for-flash-exploit.txt (1,802 bytes)
- 2019-03-20-Spelevo-EK-decoded-payload-from-infected-host.exe (2,181,896 bytes)
- 2019-03-20-Spelevo-EK-encoded-payload-sent-from-server.bin (2,186,254 bytes)
- 2019-03-20-Spelevo-EK-flash-exploit.swf (17,330 bytes)
- 2019-03-20-Spelevo-EK-landing-page.txt (28,207 bytes)
- 2019-03-20-registry-update-to-keep-malware-payload-persistent.txt (618 bytes)
NOTES:
- Earlier this month, @kafeine tweeted about Spelevo EK (link) and others have have also been tracking this.
- Here some posts tagged #SpelevoEK on Twitter.
- My previous blog post with 3 recent examples of Spelevo EK.
- Post-infection characteristics remind me of Shade (Troldesh) ransomware, but no files were encrypted, nor did I find any ransomware notifications on the infected host.
- Instead, I saw click-fraud traffic (click-fraud = generating traffic to websites to inflate stats and boost revenue based on pay-per-click online advertising).
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- copii.whatgoogle[.]xyz
TRAFFIC
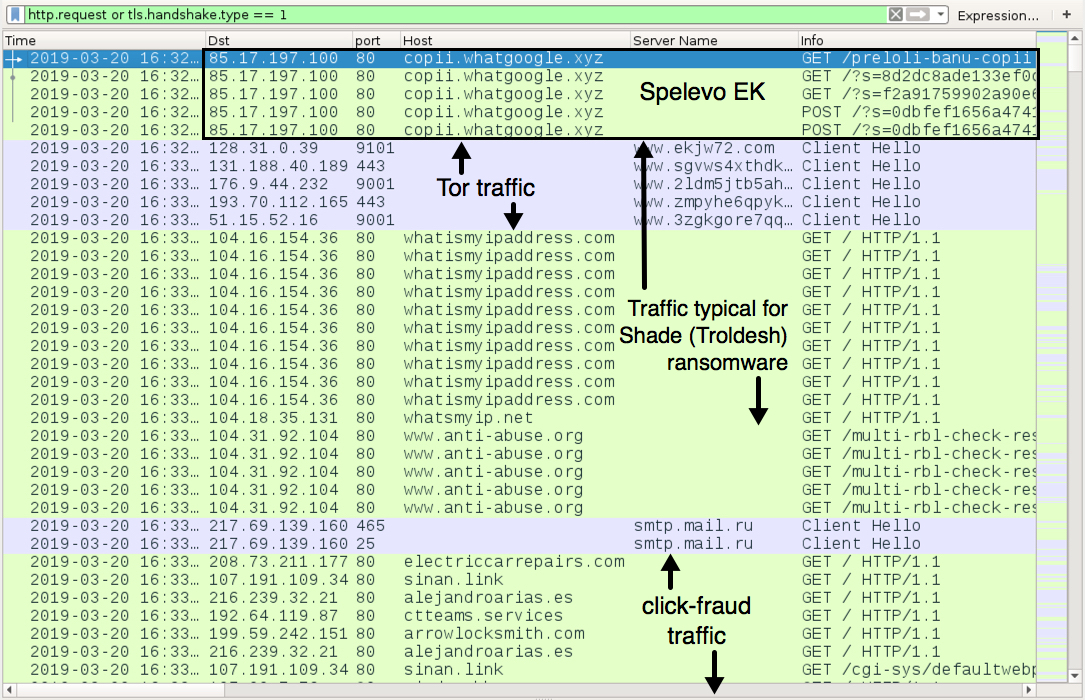
Shown above: Traffic from the infection filtered in Wireshark.
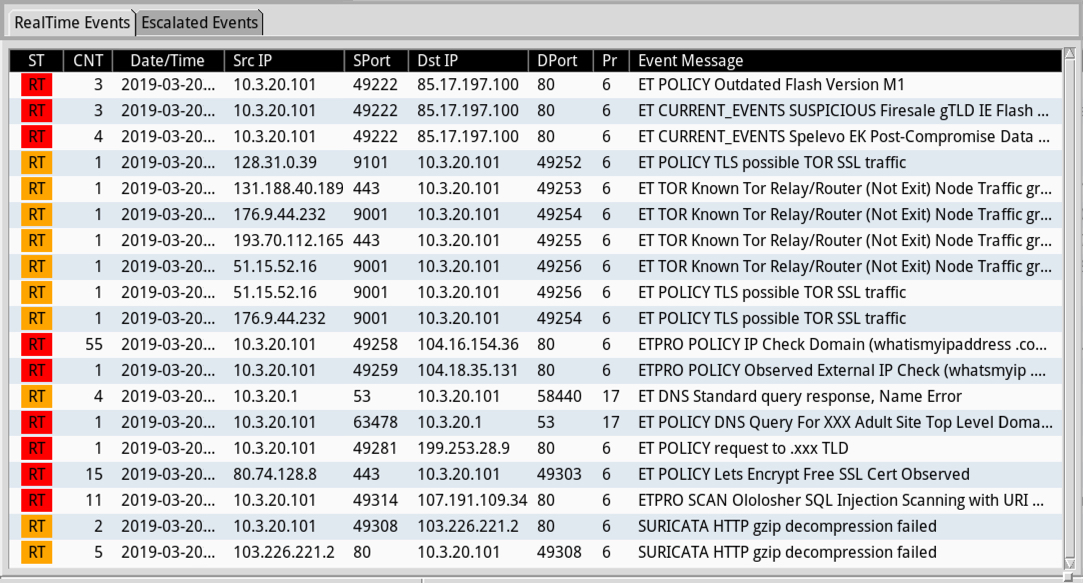
Shown above: Alerts from Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
SPELEVO EK TRAFFIC:
- 85.17.197[.]100 port 80 - copii.whatgoogle[.]xyz - GET /preloli-banu-copii
- 85.17.197[.]100 port 80 - copii.whatgoogle[.]xyz - GET /?s=8d2dc8ade133ef0ce0c759fd9309191bfl
- 85.17.197[.]100 port 80 - copii.whatgoogle[.]xyz - GET /?s=f2a91759902a90e6064ca429b2adbe00sw
- 85.17.197[.]100 port 80 - copii.whatgoogle[.]xyz - POST /?s=0dbfef1656a474176448ff964eb1df3cmf
- 85.17.197[.]100 port 80 - copii.whatgoogle[.]xyz - POST /?s=0dbfef1656a474176448ff964eb1df3cmf&e=00000111&p=1
POST-INFECITON TRAFFIC:
- various IP addresses over TCP ports 443 or 9001 - various domains - Tor traffic
- port 80 - whatismyipaddress[.]com
- port 80 - whatismyip[.]net
- port 80 - www.anti-abuse[.]org - GET /multi-rbl-check-results/?host=[victim's IP address]
- port 465 - smtp.mail[.]ru - SSL/TLS traffic for SMTP
- port 25 - smtp.mail[.]ru - SSL/TLS traffic for SMTP
- various IP addresses - various domains - click-fraud traffic
MALWARE
SPELEVO EK FLASH EXPLOIT:
- SHA256 hash: d4d1708e2ea1f897d2db66e0c1be8486a0bb62e0834d65d98991fe0f79cb7c11
File size: 17,330 bytes
File description: Spelevo EK Flash exploit seen on Wednesday 2019-03-20
SPELEVO EK PAYLOAD:
- SHA256 hash: 8ecf4f11e3ff132b88d72fa3dd458e1e2d1badfee892fed7d855228ecc9495a1
File size: 2,181,896 bytes
File location: C:\ProgramData\services\csrss.exe
File description: Payload caused Spelevo EK on Wednesday 2019-03-20, found on the infected Windows host
Any.Run analysis: https://app.any.run/tasks/91219a9f-f790-455e-a413-2a4ba3a83c3b
IMAGES
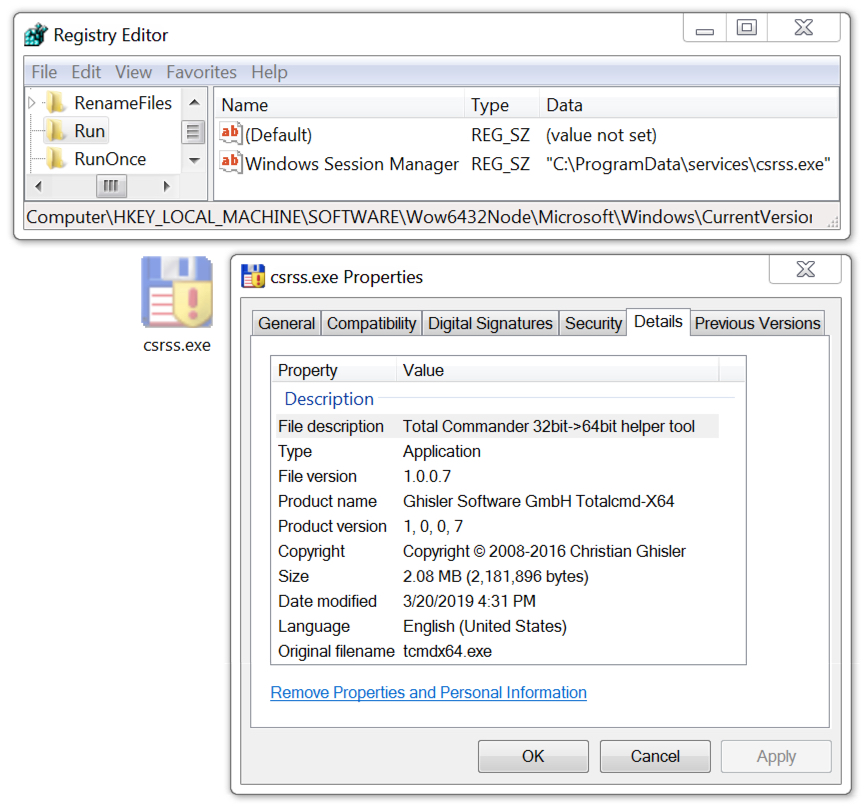
Shown above: Decoded EXE payload extracted from the infected Windows host, caused by Spelevo EK.
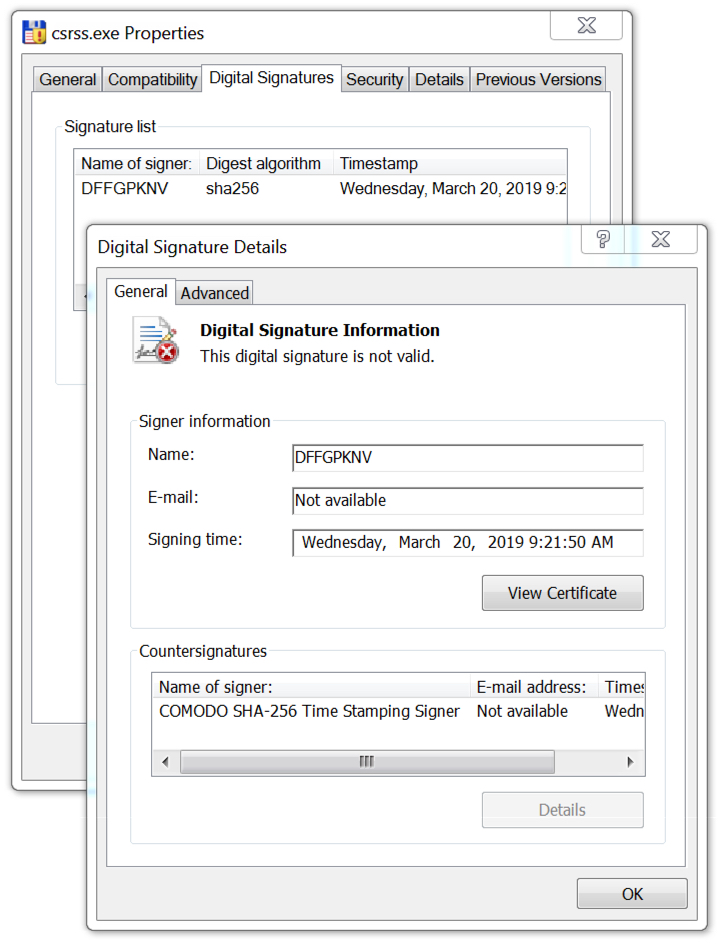
Shown above: Digital signature from the payload EXE.
Shown above: Some other artifacts seen on the infected Windows host.
Click here to return to the main page.
