2019-04-02 - DOCUSIGN-THEMED MALSPAM --> HANCITOR --> GOZI/ISFB (URSNIF)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Email example: 2019-04-02-Hancitor-malspam-example.eml.zip 2.0 kB (2,024 bytes)
- 2019-04-02-Hancitor-malspam-example.eml (5,528 bytes)
- Traffic: 2019-04-02-Hancitor-infection-with-Ursnif.pcap.zip 965 kB (964,973 bytes)
- 2019-04-02-Hancitor-infection-with-Ursnif.pcap (1,292,552 bytes)
- Malware: 2019-04-02-Hancitor-and-Ursnif-malware-and-artifacts.zip 2.8 MB (2,845,568 bytes)
- 2019-04-02-Hancitor-malware-binary.exe (290,816 bytes)
- 2019-04-02-Ursnif-retrieved-by-Windows-infected-host.exe (174,080 bytes)
- 2019-04-02-Word-doc-with-macro-for-Hancitor.doc (145,920 bytes)
- 2019-04-02-registry-updates-caused-by-Ursnif.txt (12,244,536 bytes)
NOTES:
- As always, my thanks to everyone who keeps an eye on this malspam and reports about it near-real-time on Twitter.
- More indicators in this Twitter thread by @James_inthe_box with info from today's Hancitor posted at this Pastebin link.
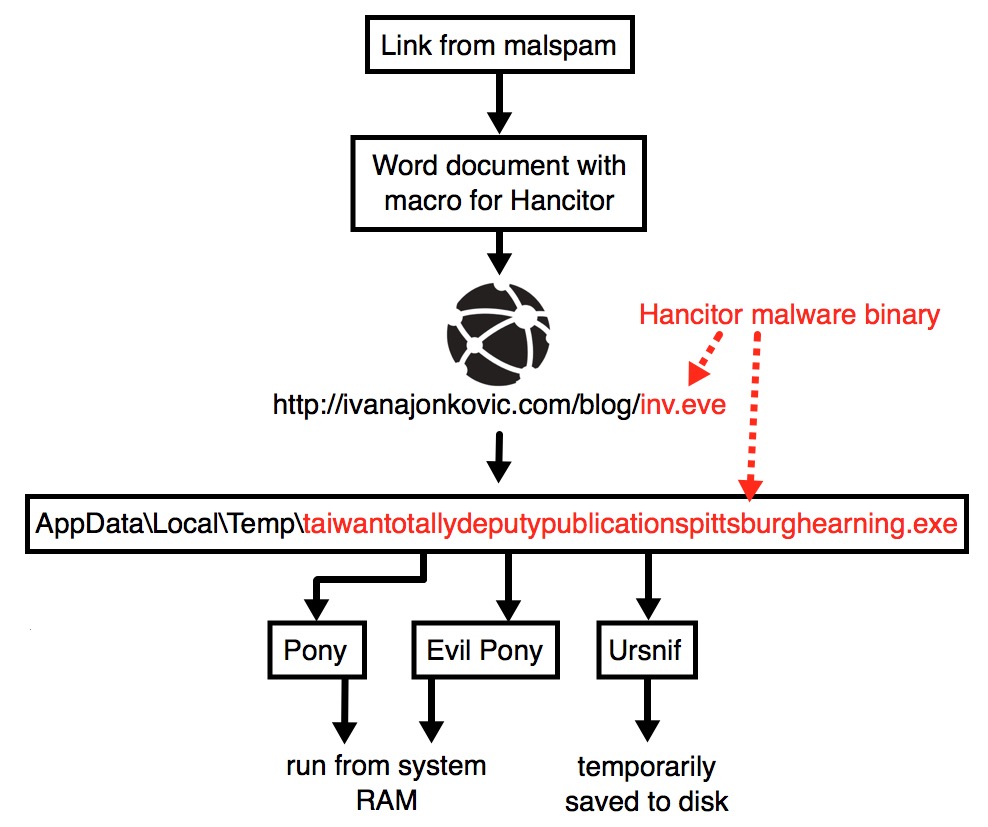
Shown above: Flow chart for today's Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- chaibuckz[.]com
- cognitionclassroom[.]com
- fastandup.co[.]in
- intecwi[.]org
- mcnconstruction[.]net
- propertiesfirst[.]com
- sewardsfollybarandgrill[.]net
- unlaca[.]info
- unlaca[.]net
- unlaca[.]org
- hxxp[:]//ivanajankovic[.]com/blog/inv.exe
- etsofevenghen[.]com
- hincasupheck[.]ru
- seromratbo[.]ru
- hxxp[:]//dokucenter.optitime[.]de/wp-content/plugins/auto-more-tag/1
- hxxp[:]//dokucenter.optitime[.]de/wp-content/plugins/auto-more-tag/2
- hxxp[:]//dokucenter.optitime[.]de/wp-content/plugins/auto-more-tag/3
- hxxp[:]//jointings[.]org/eng/wp-content/plugins/featurific-for-wordpress/1
- hxxp[:]//jointings[.]org/eng/wp-content/plugins/featurific-for-wordpress/2
- hxxp[:]//jointings[.]org/eng/wp-content/plugins/featurific-for-wordpress/3
- hxxp[:]//kitcross[.]ca/wp-content/plugins/autoptimize/1
- hxxp[:]//kitcross[.]ca/wp-content/plugins/autoptimize/2
- hxxp[:]//kitcross[.]ca/wp-content/plugins/autoptimize/3
- hxxp[:]//shawneklassen[.]com/wp-content/plugins/foobox-image-lightbox/1
- hxxp[:]//shawneklassen[.]com/wp-content/plugins/foobox-image-lightbox/2
- hxxp[:]//shawneklassen[.]com/wp-content/plugins/foobox-image-lightbox/3
- hxxp[:]//www.laxmigroup1986[.]com/wp-content/plugins/easy-responsive-tabs/1
- hxxp[:]//www.laxmigroup1986[.]com/wp-content/plugins/easy-responsive-tabs/2
- hxxp[:]//www.laxmigroup1986[.]com/wp-content/plugins/easy-responsive-tabs/3
EMAIL HEADERS
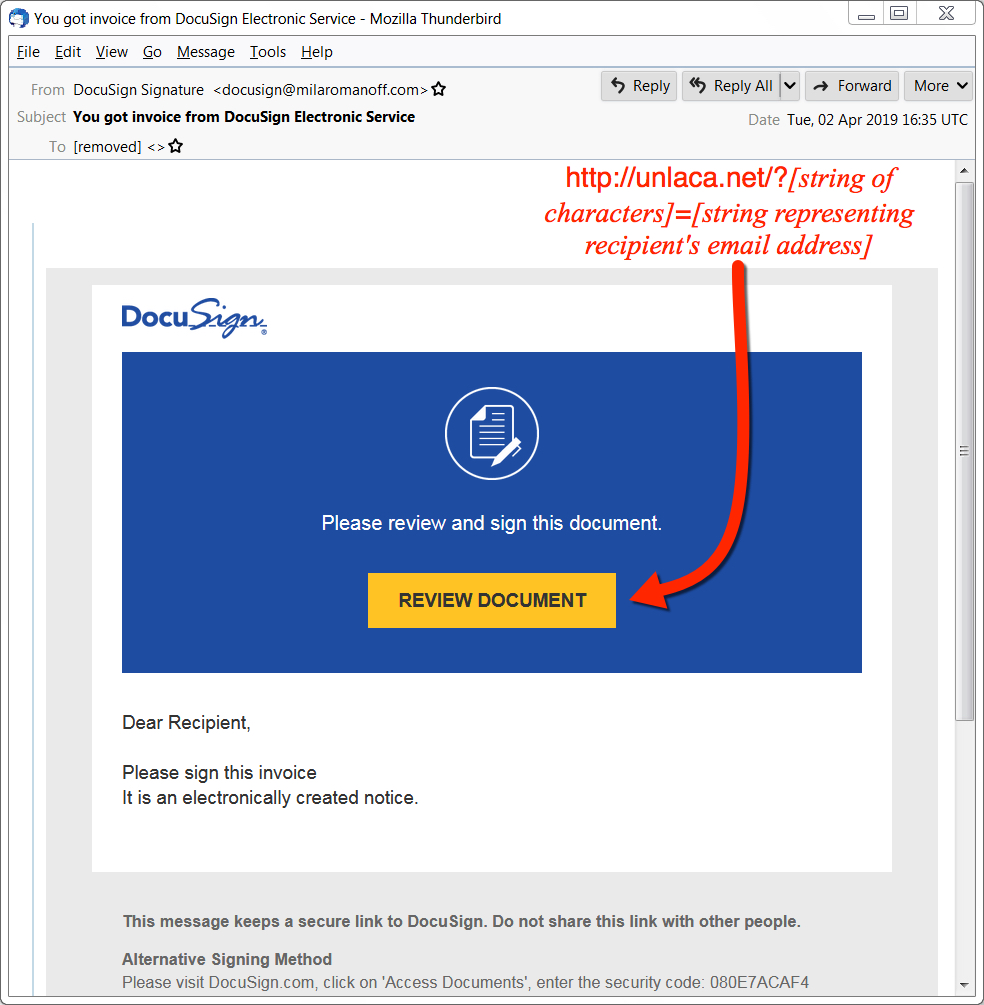
Shown above: Screenshot from an example of Hancitor malspam.
EMAIL HEADERS FROM TODAY'S HANCITOR MALSPAM EXAMPLE:
Received: from milaromanoff[.]com ([64.56.218[.]98]) by [removed] for [removed];
Tue, 02 Apr 2019 16:36:58 +0000 (UTC)
Date: Tue, 02 Apr 2019 11:35:04 -0500
MIME-Version: 1.0
X-Mailer: iPhone Mail (11A501)
Content-Transfer-Encoding: 7bit
Subject: You got invoice from DocuSign Electronic Service
Message-ID: <364EB70F.BFED560B@milaromanoff[.]com>
From: "DocuSign Signature " <docusign@milaromanoff[.]com>
Content-Type: text/html;
charset="utf-8"
To: [removed]
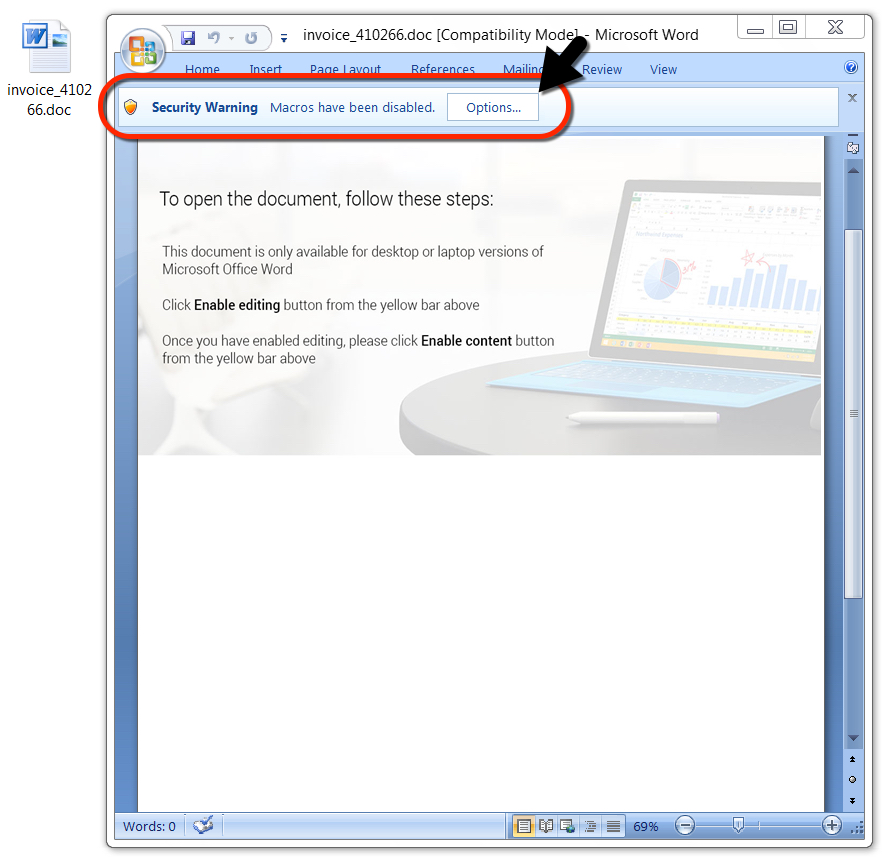
Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
LINKS IN THE EMAILS TO DOWNLOAD THE WORD DOCUMENT:
- hxxp[:]//chaibuckz[.]com/?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//cognitionclassroom[.]com/?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//fastandup.co[.]in/?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//intecwi[.]org/?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//mcnconstruction[.]net/?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//propertiesfirst[.]com/?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//sewardsfollybarandgrill[.]net/?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//unlaca[.]info/?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//unlaca[.]net/?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//unlaca[.]org/?[string of characters]=[encoded string representing recipient's email address]
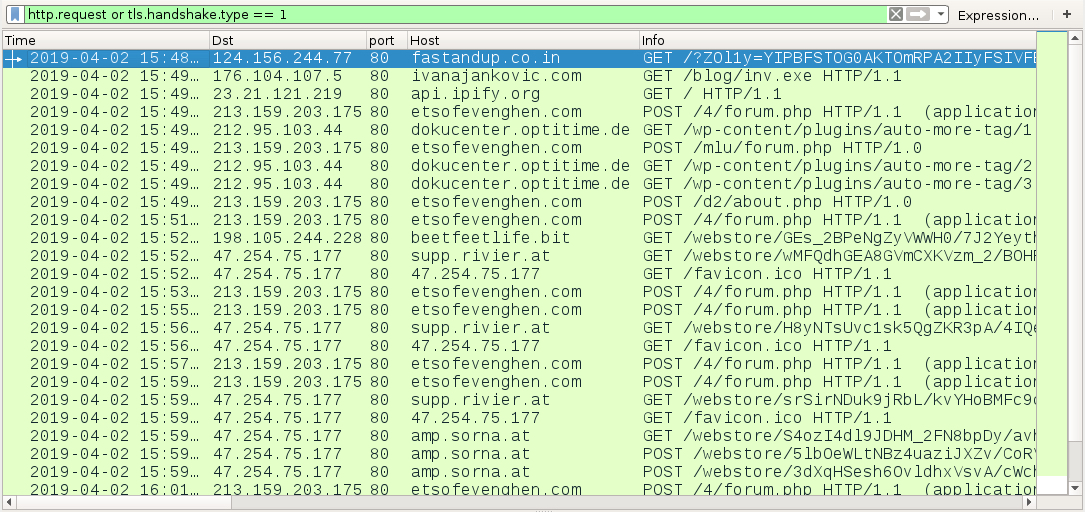
Shown above: HTTP traffic from today's infection filtered in Wireshark.
INITIAL HANCITOR INFECTION TRAFFIC:
- 124.156.244[.]77 port 80 - fastandup.co[.]in - GET/?[string of characters]=[encoded string representing recipient's email address]
- 176.104.107[.]5 port 80 - ivanajankovic[.]com - GET /blog/inv.exe
- port 80 - api.ipify.org - GET /
- 213.159.203[.]175 port 80 - etsofevenghen[.]com - POST /4/forum.php
- 213.159.203[.]175 port 80 - etsofevenghen[.]com - POST /mlu/forum.php
- 213.159.203[.]175 port 80 - etsofevenghen[.]com - POST /d2/about.php
- 212.95.103[.]44 port 80 - dokucenter.optitime[.]de - GET /wp-content/plugins/auto-more-tag/1
- 212.95.103[.]44 port 80 - dokucenter.optitime[.]de - GET /wp-content/plugins/auto-more-tag/2
- 212.95.103[.]44 port 80 - dokucenter.optitime[.]de - GET /wp-content/plugins/auto-more-tag/3
URSNIF POST-INFECTION HTTP TRAFFIC:
- 198.105.244[.]228 port 80 - beetfeetlife[.]
- bit
- GET /webstore/[long string of characters]/P - 47.254.75[.]177 port 80 - supp.rivier[.]at - GET /webstore/[long string of characters]/4
- 47.254.75[.]177 port 80 - 47.254.75[.]177 - GET /favicon.ico
- 47.254.75[.]177 port 80 - supp.rivier[.]at - GET /webstore/[long string of characters]/wXx
- 47.254.75[.]177 port 80 - supp.rivier[.]at - GET /webstore/[long string of characters]/5g
- 47.254.75[.]177 port 80 - amp.sorna[.]at - GET /webstore/[long string of characters]/hdk
- 47.254.75[.]177 port 80 - amp.sorna[.]at - POST /webstore/[long string of characters]/W
- 47.254.75[.]177 port 80 - amp.sorna[.]at - POST /webstore/[long string of characters]/D
URSNIF POST-INFECTION DNS TRAFFIC:
- 193.183.98[.]66 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 91.217.137[.]37 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 192.71.245[.]208 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 8.8.8[.]8 port 53 - DNS query for beetfeetlife[.]bit (response: Server No such name)
- 178.17.170[.]179 port 53 - DNS query for beetfeetlife[.]bit (no response)
- 82.196.9[.]45 port 53 - DNS query for beetfeetlife[.]bit (no response)
- 151.80.222[.]79 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 68.183.70[.]217 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 217.144.135[.]7 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 158.69.160[.]164 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 207.148.83[.]241 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 5.189.170[.]196 port 53 - DNS query for beetfeetlife[.]bit (response: NS a.dnspod.com NS b.dnspod.com NS c.dnspod.com)
- 217.144.132[.]148 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 94.247.43[.]254 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 188.165.200[.]156 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 159.89.249[.]249 port 53 - DNS query for beetfeetlife[.]bit (response: Server failure)
- 150.249.149[.]222 port 53 - DNS query for beetfeetlife[.]bit (no response)
- 193.183.98[.]66 port 53 - DNS query for api.sorna[.]at
- 193.183.98[.]66 port 53 - DNS query for supp.rivier[.]at
- port 53 - DNS query for resolver1.opendns[.]com (response: A resolver1.opendns[.]com A 208.67.222[.]222)
- 208.67.222[.]222port 53 - DNS query for PTR 222.222.67.208.in-addr[.]arpa
- 208.67.222[.]222port 53 - DNS query for myip.opendns[.]com
- 193.183.98[.]66 port 53 - DNS query for amp.sorna[.]at
- 193.183.98[.]66 port 53 - DNS query for cdn.avaregio[.]at (response: Server failure)
- 91.217.137[.]37 port 53 - DNS query for cdn.avaregio[.]at (response: Server failure)
FILE HASHES
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: 07a99580b94a4854a7e49ef38d03f070350baab088130b23d79dde29242eb346
File size: 145,920 bytes
File name: invoice_173908.doc (random numbers in the file name)
File description: Word document downloaded from link in Hancitor malspam. Has macro to cause Hancitor infection.
- SHA256 hash: 468200d4d207a7cc1df245b9670fcf9e3c491dd344643cd7edcf8a82f2cde214
File size: 290,816 bytes
File location: hxxp[:]//ivanajankovic[.]com/blog/inv.exe
File location: C:\Users\[username]\AppData\Local\Temp\taiwantotallydeputypublicationspittsburghearning.exe
File description: Hancitor malware EXE seen after enabling macro from downloaded Word document
- SHA256 hash: 2cccdc51aea02049dc7f96f510a13311f112096a7d870a97d70232356ddef42b
File size: 174,080 bytes
File location: C:\Users\[username]AppData\Local\Temp\BN13CB.tmp (random hex characters in file name)
File description: Ursnif EXE on 2019-04-02 retreived by Hancitor-infected host
Click here to return to the main page.
