2019-04-05 - QUICK POST: FAKE UPDATES CAMPAIGN PUSHES CHTHONIC BANKING TROJAN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
FILES:
- 2019-04-05-Fake-Updates-Campaign-pushes-Chthonic.pcap.zip 6.7 MB (6,744,016 bytes)
- 2019-04-05-Fake-Updates-Campaign-malware-and-artifacts.zip 582 kB (582,082 bytes)
- 2019-04-05-Fake-Updates-Campaign-indicators.txt.zip 2.0 kB (1,968 bytes)
ANOTHER EXAMPLE OF THE FAKE UPDATES PAGE CAPTURED IN FIDDLER:
- 2019-04-05-fake-updates-campaign-from-www.med.ufro.cl.saz.zip 3.5 MB (3,487,501 bytes)
IMAGES
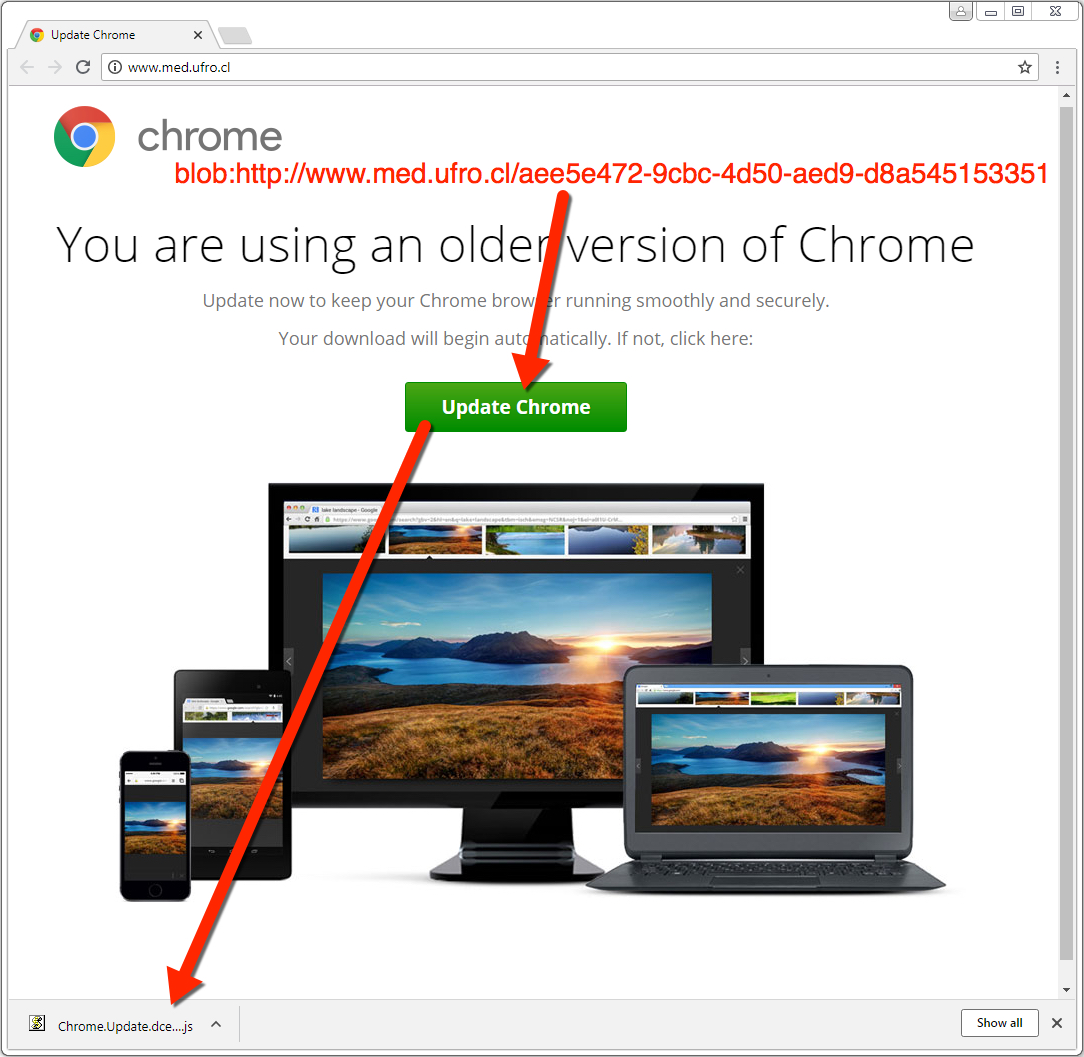
Shown above: Example of fake Chrome update page when using the Chrome web browser.
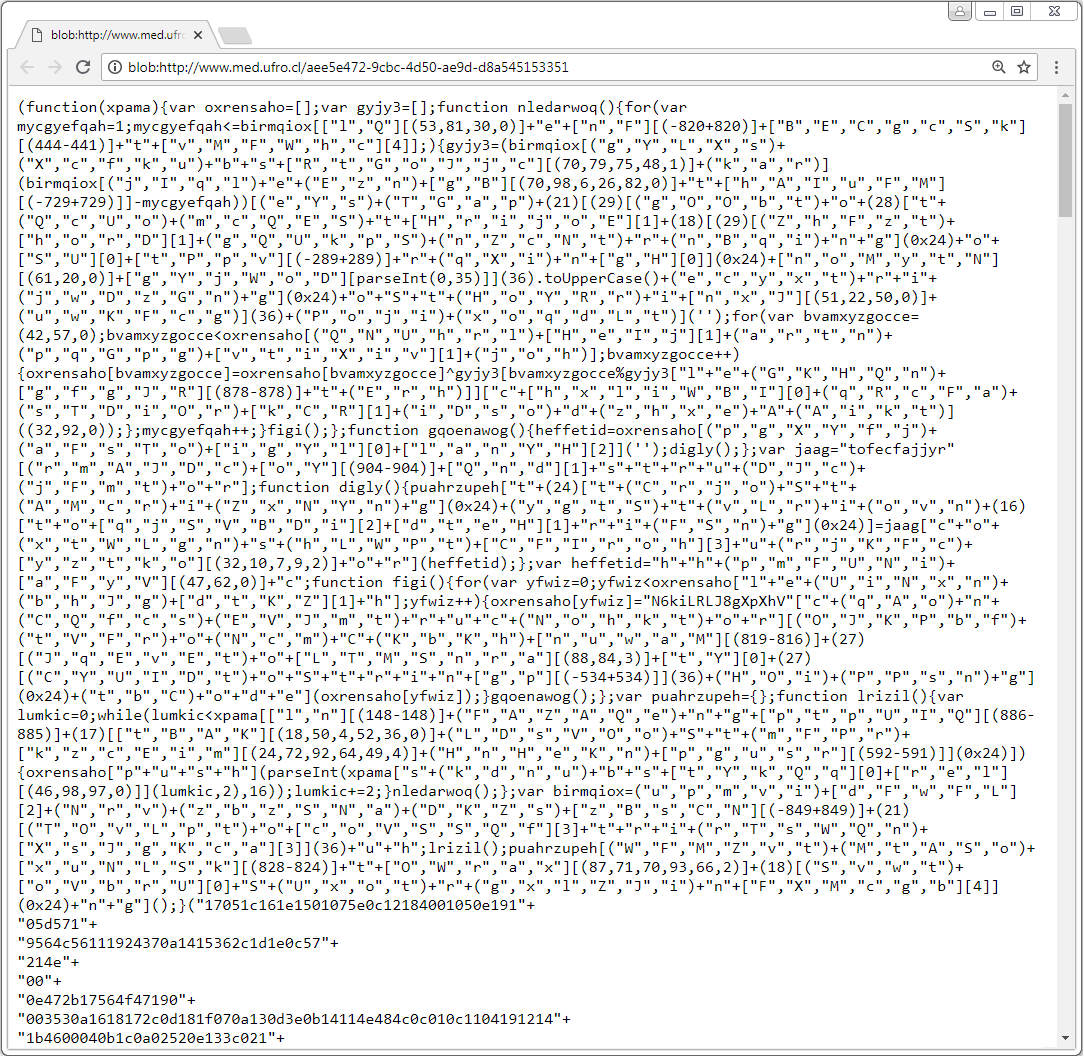
Shown above: Link from fake update page appears to retrieve info from original site that kicked off this infection chain.
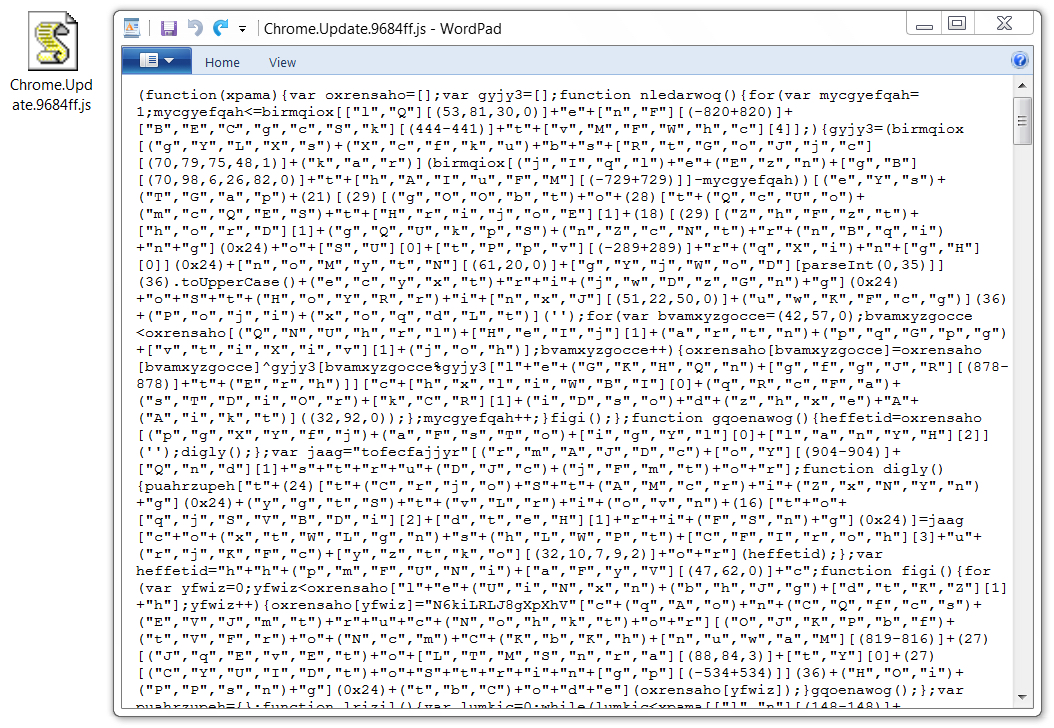
Shown above: Downloaded .js file. The last six hexadecimal characters before .js in the file name are different for each download.
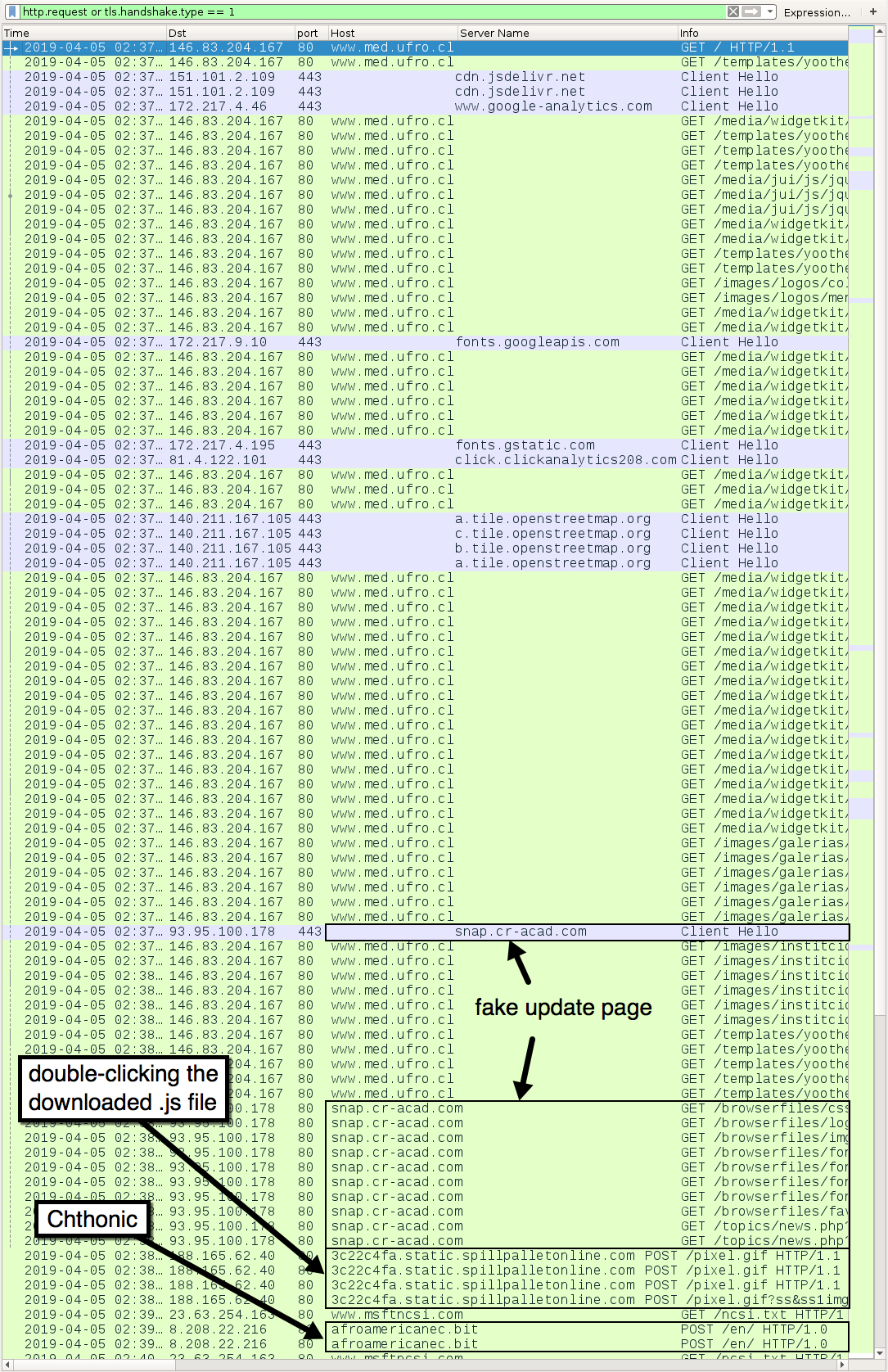
Shown above: Traffic from an infection filtered in Wireshark.
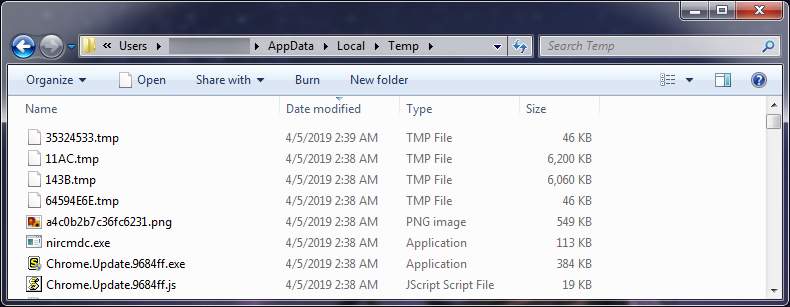
Shown above: Artifacts from an infected Windows host.
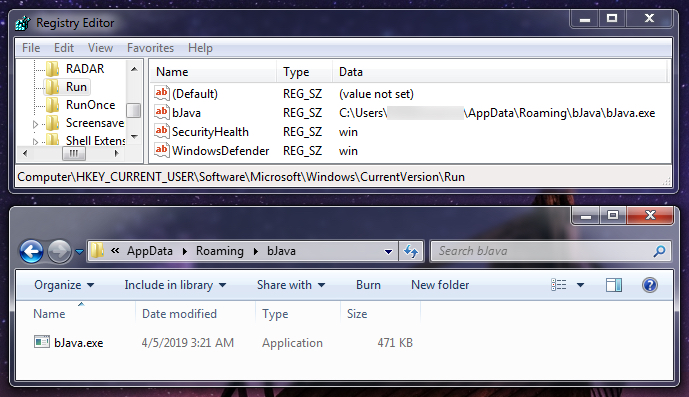
Shown above: Chthonic banking Trojan persistent on an infected Windows host.
Click here to return to the main page.
