2019-05-01 - MALSPAM WITH PASSWORD-PROTECTED WORD DOC PUSHES ICEDID
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Email: 2019-05-01-associated-malspam.zip 42 kB (42,060 bytes)
- 2019-04-26-malspam-with-password-protected-Word-doc.eml (68,500 bytes)
- Traffic: 2019-05-01-password-protected-doc-infection-traffic.pcap.zip 6.3 MB (6,257,521 bytes)
- 2019-05-01-password-protected-doc-infection-traffic.pcap (6,992,374 bytes)
- Malware: 2019-05-01-malware-and-artifacts-from-infection.zip 3.4 MB (3,407,583 bytes)
- 2019-04-26-password-protected-Word-doc-from-malspam.doc (48,640 bytes)
- 2019-05-01-IcedID-malware-retrieved-by-macro-from-password-protected-Word-doc.exe (181,760 bytes)
- 2019-05-01-Sw9JKmXqaSj.exe-from-192_243_108_248.exe (207,872 bytes)
- 2019-05-01-Tinx86_14.exe-from-192_243_108_248.exe (2,787,328 bytes)
- 2019-05-01-scheduled-task-to-keep-IcedID-persistent.txt (3,228 bytes)
- 2019-05-01-sin.png-from-155_138_134_133.exe (626,688 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and domains (note: these are de-fanged):
- hxxp[:]//209.141.34[.]8/amsi.jpg
- hxxp[:]//92.243.108[.]248/Sw9JKmXqaSj.exe
- hxxp[:]//192.243.108[.]248/Tinx86_14.exe
- hxxp[:]//155.138.134[.]133/sin.png
- marakusta[.]at
- saudienter[.]pw

Shown above: An example of this malspam from Friday, 2019-04-26.

Shown above: The attached Word document after unlocking it with the password.
TRAFFIC
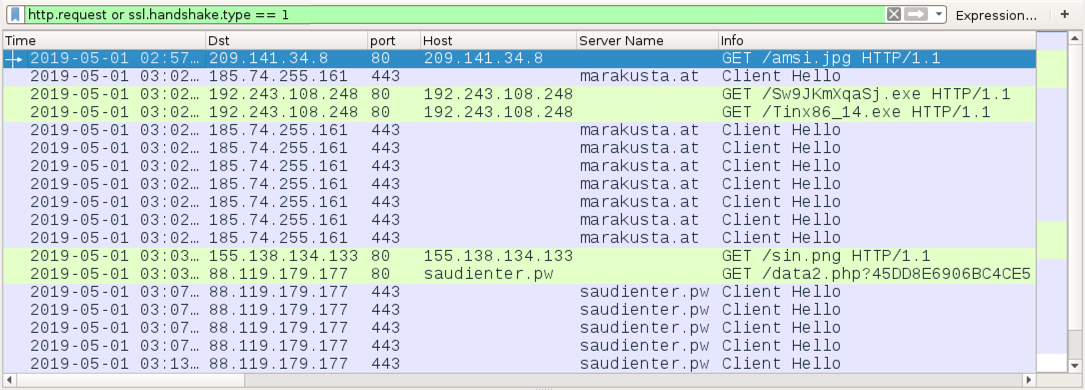
Shown above: Traffic from an infection filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 209.141.34[.]8 port 80 - 209.141.34[.]8 - GET /amsi.jpg
- 185.74.255[.]161 port 443 - marakusta[.]at - HTTPS/SSL/TLS traffic caused by IcedID (Bokbot)
- 192.243.108[.]248 port 80 - 192.243.108[.]248 - GET /Sw9JKmXqaSj.exe
- 192.243.108[.]248 port 80 - 192.243.108[.]248 - GET /Tinx86_14.exe
- 155.138.134[.]133 port 80 - 155.138.134[.]133 - GET /sin.png
- 88.119.179[.]177 port 80 - saudienter[.]pw - GET /data2.php?0123456789ABCDEF
- 88.119.179[.]177 port 443 - saudienter[.]pw - HTTPS/SSL/TLS traffic caused by IcedID (Bokbot)
FILE HASHES
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: b39964fd7962b989f6a3307a917b778db7323c29383e5a16e26b0a6ee0411433
File size: 48,640 bytes
File name: Rhiannon resume.doc
File description: Password-protected Word doc from malspam on 2019-04-26 (password: 1212)
- SHA256 hash: d040d4e593e3f5d50cddb100581494d67d339d6e10a526d3cec716add08530a3
File size: 181,760 bytes
File location: C:\Users\[username]\AppData\Local\Temp\inboxmvprocessingpersianbearinglegitimate.exe
File description: IcedID malware on 2019-05-01 retrieved by macro from password protected Word doc.
- SHA256 hash: 8a72c512dcf9232382f658de8b84dee433c54abe027f666185b7a3dc26f96d22
File size: 207,872 bytes
File location: hxxp[:]//192.243.108[.]248/Sw9JKmXqaSj.exe
File description: Trickbot-related EXE caused by the IcedID infection.
- SHA256 hash: aab328799dd16255acfc812e83a0f65bbab42e9eab2e369a3ab6192a7823885c
File size: 2,787,328 bytes
File location: hxxp[:]//192.243.108[.]248/Tinx86_14.exe
File description: Another Trickbot-related EXE caused by the IcedID infection.
- SHA256 hash: db66f95053252791bd9d4a654779749e86e888473d8898dddbb2e193576a659d
File size: 626,688 bytes
File location: hxxp[:]//155.138.134[.]133/sin.png
File description: Trickbot EXE retrieved by one of the above Trickbot-related executable files.
Click here to return to the main page.
