2019-07-03 - QUICK POST: HANCITOR INFECTION WITH COBALT STRIKE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2019-07-03-Hancitor-malspam-example.eml.zip 2.5 kB (2,531 bytes)
- 2019-07-03-Hancitor-infection-with-Cobalt-Strike.pcap.zip 520 kB (519,771 bytes)
- 2019-07-03-Hancitor-and-Cobalt-Strike-malware-and-artifacts.zip 354 kB (354,176 bytes)
NOTES:
- Since Monday 2019-07-01, Hancitor infections have included Cobalt Strike activity as noted by @James_inthe_box, @VK_Intel, and others (Twitter link).
- I didn't see it in the Hancitor I posted on 2019-07-01, but I did see Cobalt Strike act ivity from my Hancitor infection yesterday.
- I saw more Cobalt Strike activity during my Hancitor infection today. See the images below for details.
IMAGES
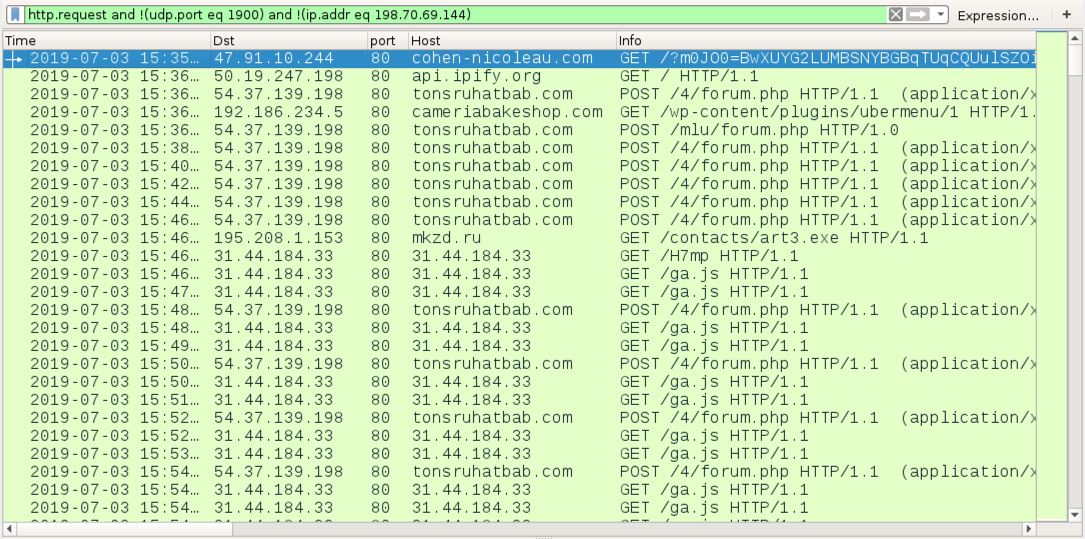
Shown above: Traffic from the infection filtered in Wireshark.
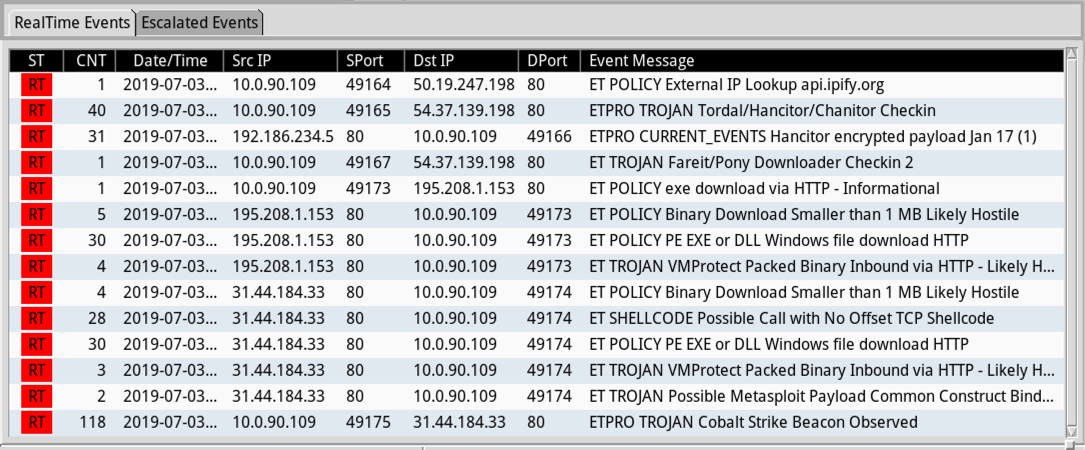
Shown above: Alerts from the traffic using Security Onion with Suricata and the Emergingthreats Pro ruleset viewed through Squil.

Shown above: Further beaconing activity related to Cobalt Strike.
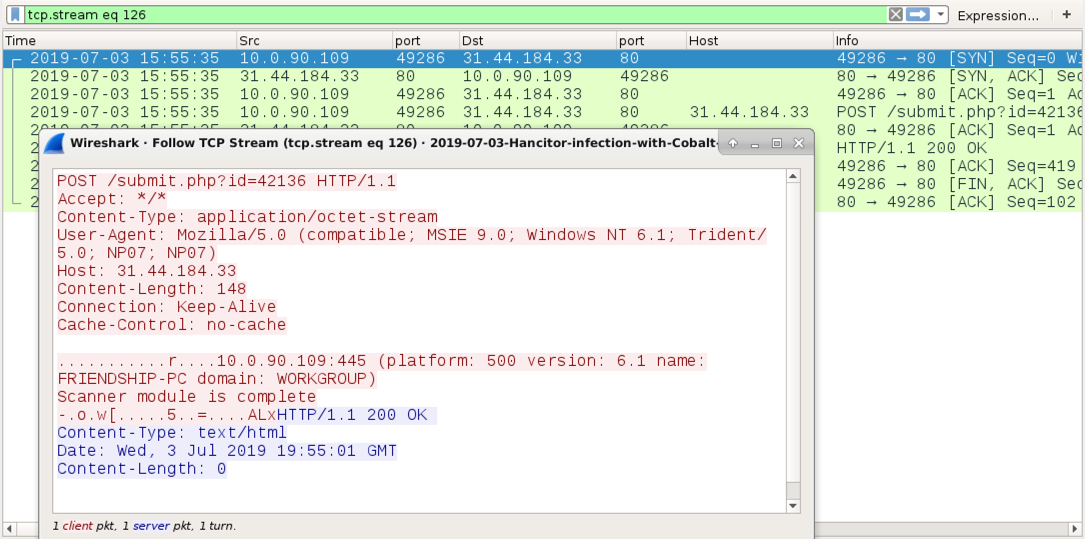
Shown above: Some contents of the Cobalt Strike callback traffic.
Click here to return to the main page.
