2019-10-17 - DATA DUMP: GOZI/ISFB (URSNIF) INFECTION TRAFFIC FROM ITALIAN MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2019-10-17-Ursnif-IOCs.txt.zip 1.3 kB (1,271 bytes)
- 2019-10-17-Ursnif-IOCs.txt (2,558 bytes)
- 2019-10-17-Ursnif-infection-from-Italian-malspam.pcap.zip 2.3 MB (2,260,847 bytes)
- 2019-10-17-Ursnif-infection-from-Italian-malspam.pcap (4,801,007 bytes)
- 2019-10-17-malware-and-artifacts-from-Ursnif-infection.zip 3.8 MB (3,809,220 bytes)
- 2019-10-17-Word-doc-with-macro-for-Ursnif.doc (78,848 bytes)
- 2019-10-17-initial-Ursnif-binary.exe (3,715,072 bytes)
- 2019-10-17-javascript-dropped-by-macro-from-Word-doc.txt (1,454 bytes)
- 2019-10-17-Windows-registry-updates-from-Ursnif.txt (10,579,864 bytes)
IMAGES
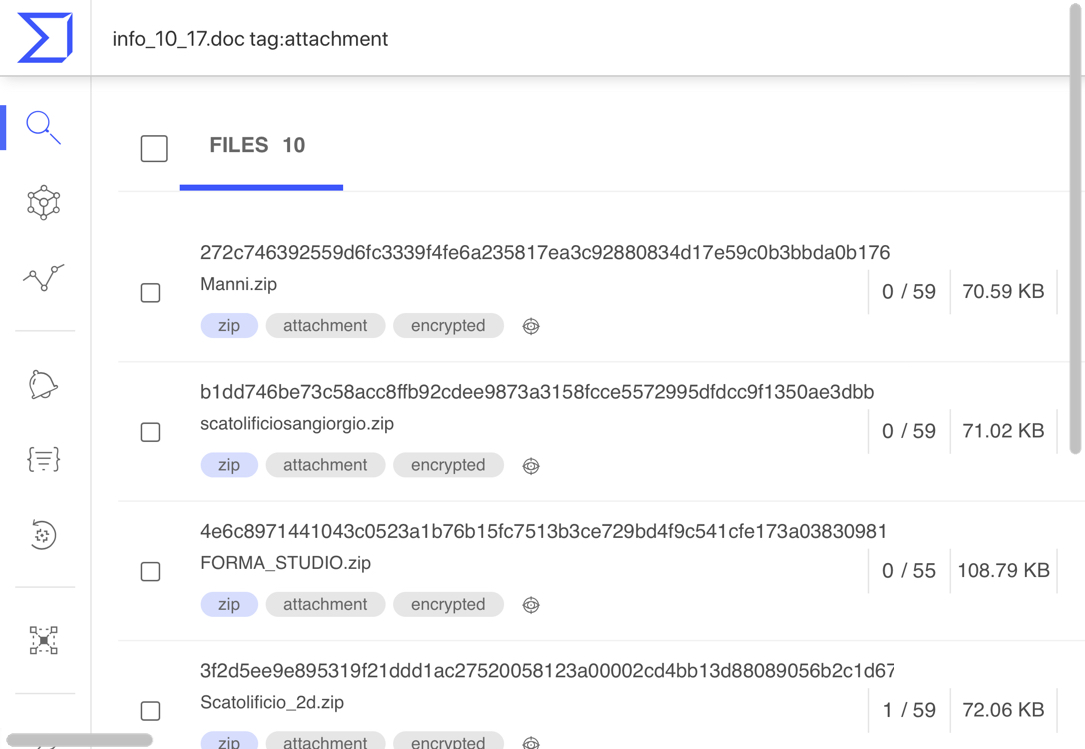
Shown above: Searching for malspam pushing today's Ursnif in VirusTotal.
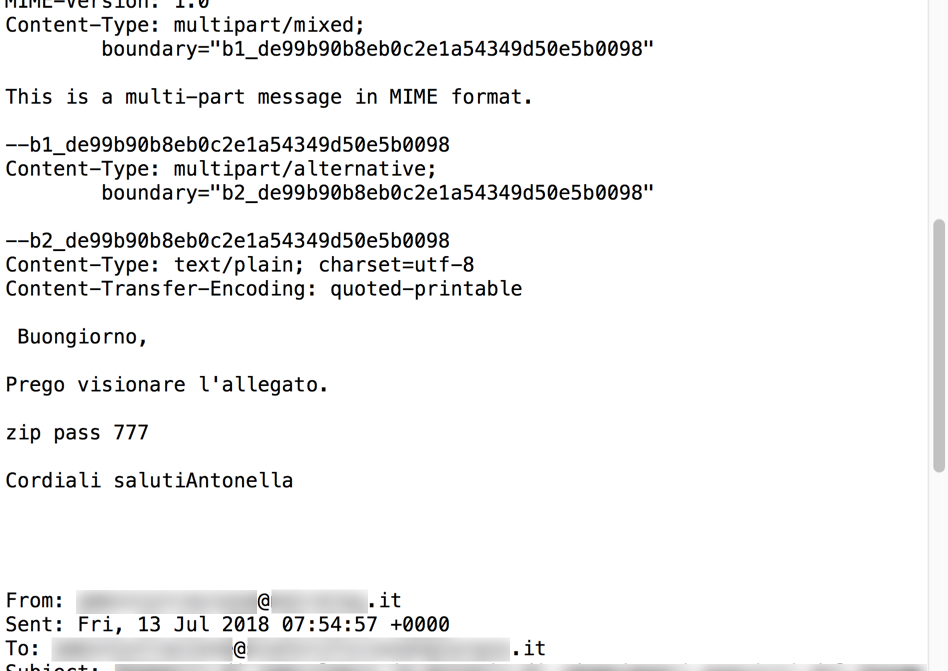
Shown above: Still the same "777" password for zip archives attached to this malspam.
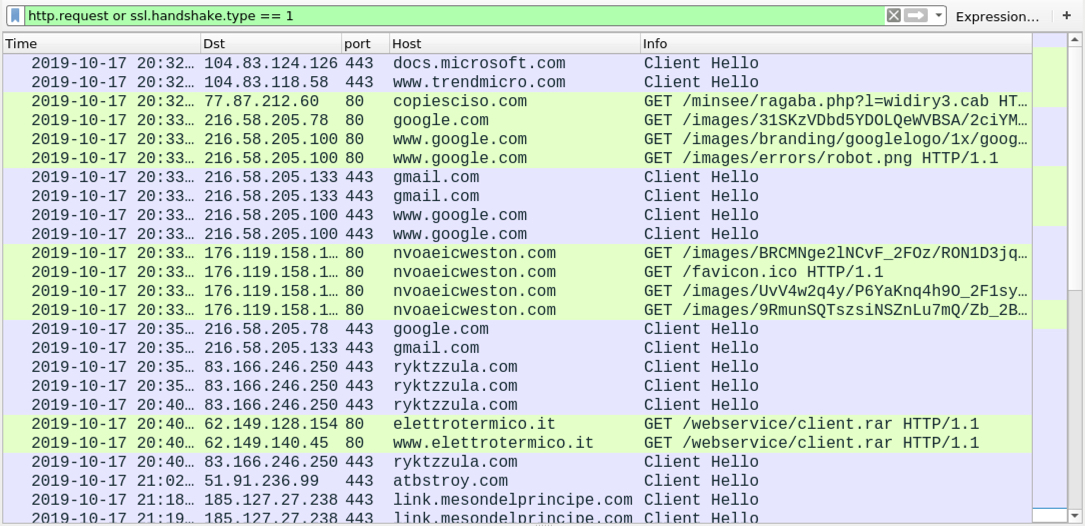
Shown above: Traffic from a santized pcap of the infection traffic.
Click here to return to the main page.
