2019-11-13 - DATA DUMP: ICEDID INFECTION WITH ANUBIS VNC AND TRICKBOT IN AD ENVIRONMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- In this infection, Trickbot spread from the client to its domain controller.
- I missed the Anubis VNC traffic on 94.103.9[.]196 over TCP port 8080 in this pcap when I originally made this post.
- For more information on Anubis VNC, see: https://blog.nviso.eu/2023/03/20/icedids-vnc-backdoors-dark-cat-anubis-keyhole/
ASSOCIATED FILES:
- 2019-11-13-IcedID-infection-with-Anubis-VNC-and-Trickbot-in-AD-environment.pcap.zip 78.2 MB (78,219,073 bytes)
- 2019-11-13-malware-and-artifacts-from-IcedID-infection-with-Anubis-VNC-and-Trickbot-in-AD-environment.zip 32.2 MB (32,245,022 bytes)
IMAGES
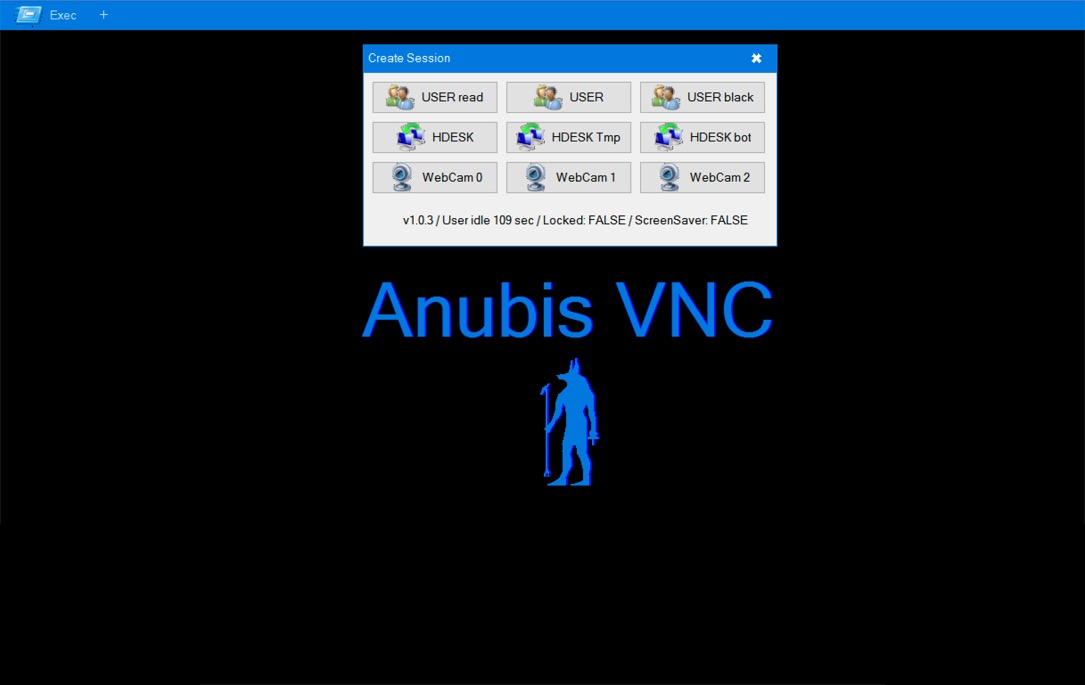
Shown above: Screenshot of video from the decoded VNC traffic.
Click here to return to the main page.
