2019-11-27 - EMOTET EPOCH 3 INFECTED WINDOWS CLIENT AS SPAMBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2019-11-27-Emotet-epoch-3-infected-Windows-client-as-spambot.pcap.zip 20 MB (19,994,798 bytes)
NOTES:
- This is traffic from the middle of an Emotet infection, where the infected Windows host was acting as a spambot.
IMAGES
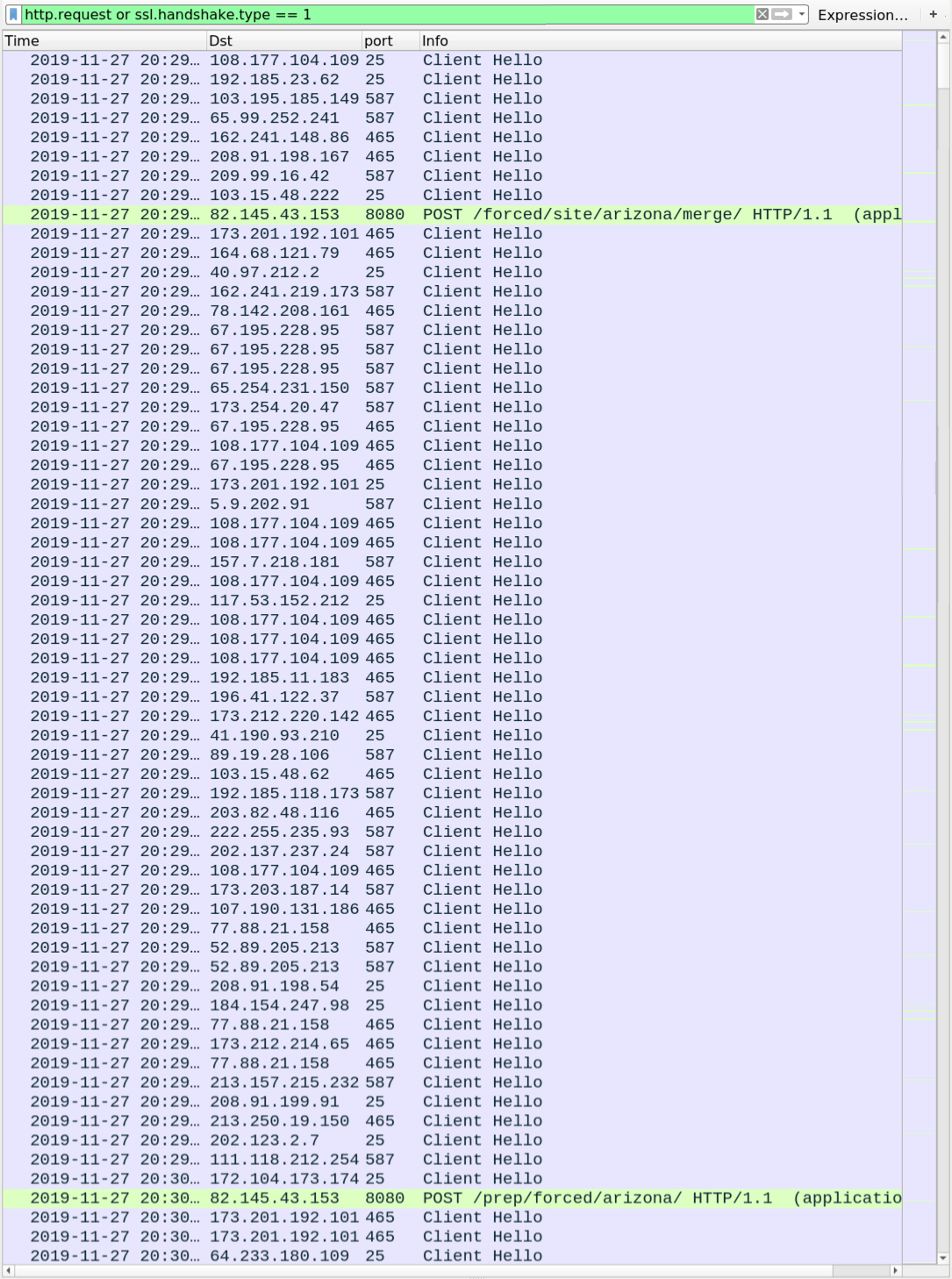
Shown above: Infection traffic filtered in Wireshark.
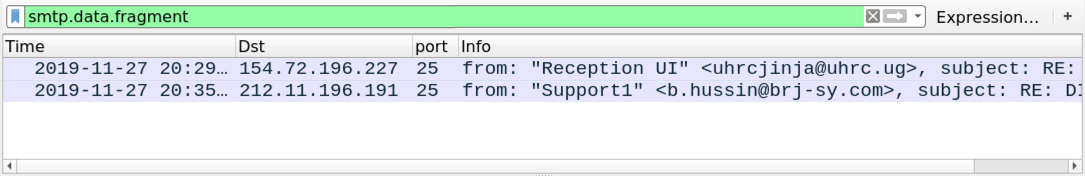
Shown above: Filtering to see if any of the malspam was sent using unencrypted SMTP.
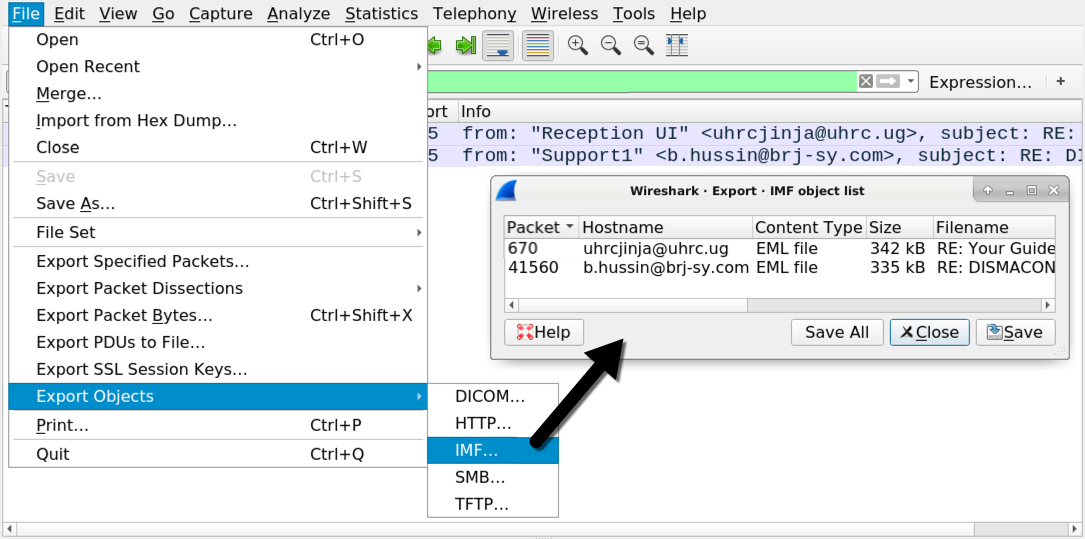
Shown above: Exporting IMF (Internet Mail Format) items from the pcap.
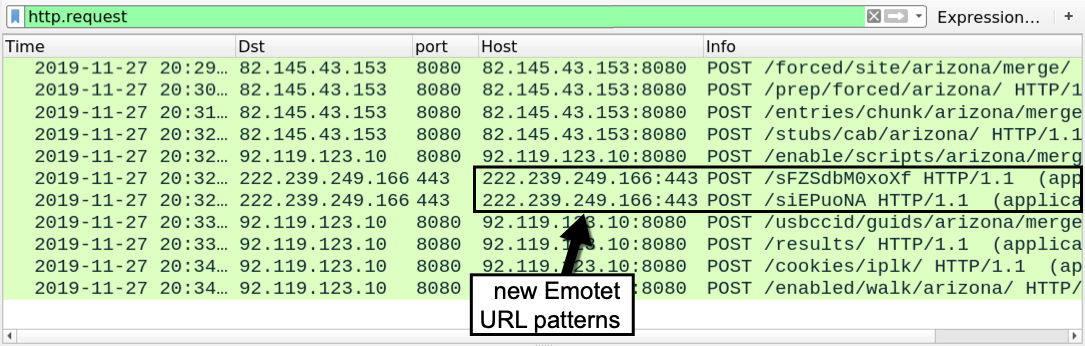
Shown above: Filtering on HTTP post-infection traffic for Emotet in this pcap.
Click here to return to the main page.
