2019-12-23 - RIG EK SENDS MALWARE PAYLOAD I CANNOT IDENTIFY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2019-12-23-Rig-EK-sends-a-payload-I-cannot-identify.pcap.zip 6.5 MB (6,475,956 bytes)
- 2019-12-23-Rig-EK-sends-a-payload-I-cannot-identify.pcap (6,837,996 bytes)
- 2019-12-23-malware-and-artifacts-from-Rig-EK-infection.zip 5.6 MB (5,612,175 bytes)
- 2019-12-23-Rig-EK-artifact-n.t.txt
- 2019-12-23-Rig-EK-landing-page.txt
- 2019-12-23-Rig-EK-malware-payload.exe
- 2019-12-23-registry-entry-for-the-malware.txt
- Users/username/AppData/Roaming/Cugifo/
- Users/username/AppData/Roaming/Dahag/efobba.uf
- Users/username/AppData/Roaming/Ofeb/ygebe.dei
- Users/username/AppData/Roaming/Uggeeh/ubugce.hagoi
- Users/username/AppData/Roaming/Acadh/duygoboh.fub
- Users/username/AppData/Roaming/Ecuf/ofca.hahe
- Users/username/AppData/Roaming/Ciog/
- Users/username/AppData/Roaming/Geca/cuefc.od
- Users/username/AppData/Roaming/Ybcide/guag.exe
- Users/username/AppData/Roaming/Cacoce/difaadu.ech
- Users/username/AppData/Roaming/Udech/offyb.efeh
- Users/username/AppData/Roaming/Abba/efcahoe.yb
- 2019-12-23-post-infection-traffic-from-malware-MITM-for-HTTPS-traffic.zip 8.6 MB (8,580,237 bytes)
- 2019-12-23-post-infection-traffic-from-malware-MITM-for-HTTPS-traffic.pcap (9,009,575 bytes)
- SSLKeysLogFile.txt (3,894 bytes)
NOTES:
- I got the pcap with MitM for HTTPS traffic from the Any.Run sandobx and sanitized it for this blog post.
IMAGES
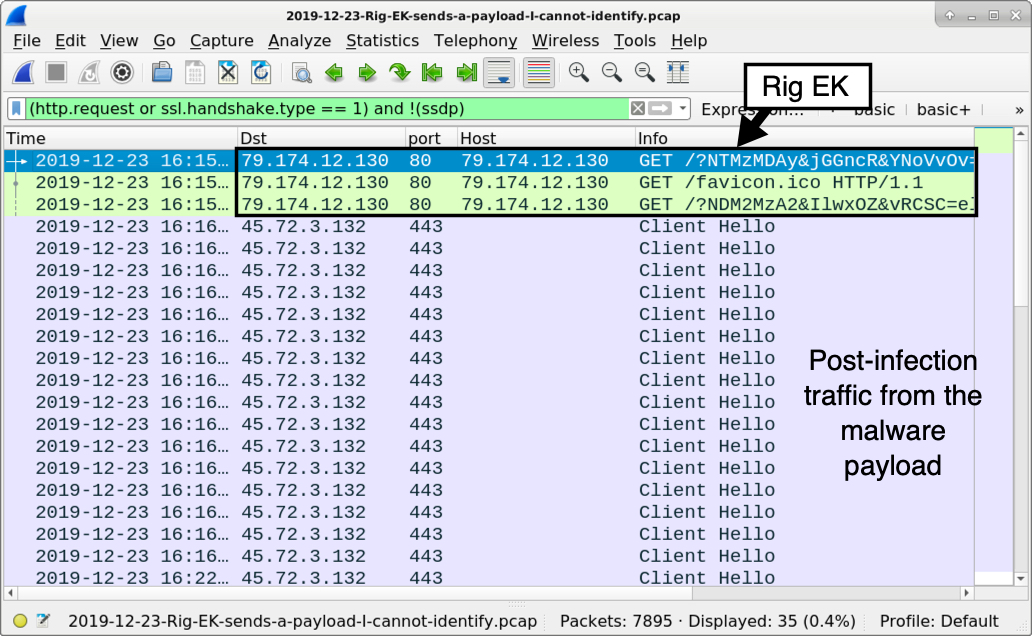
Shown above: Traffic from my lab infection filtered in Wireshark.
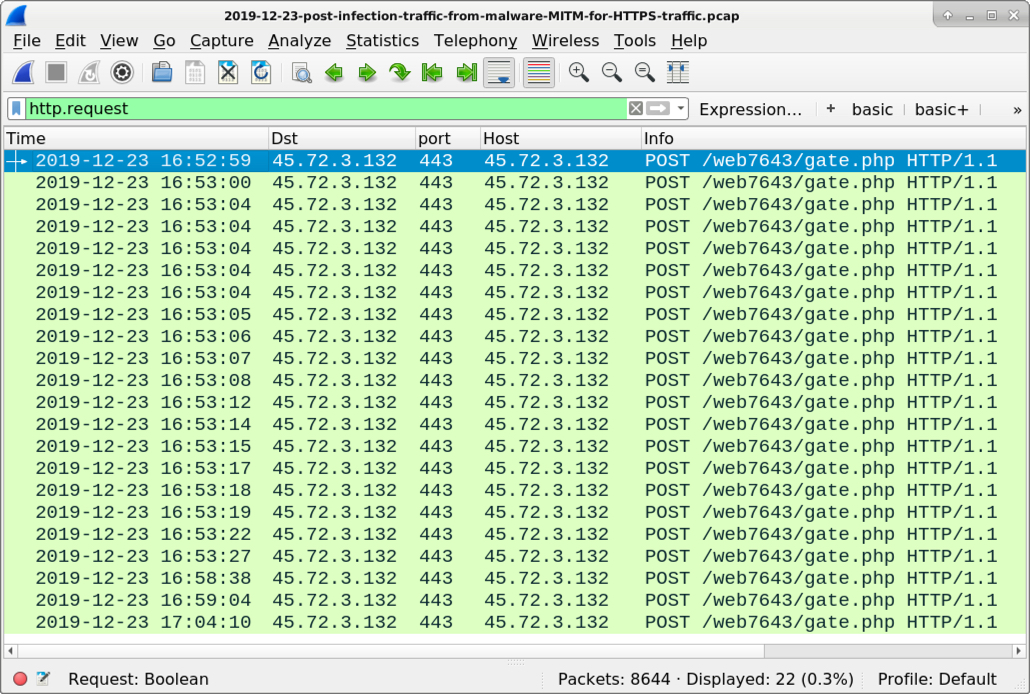
Shown above: HTTPS traffic caused by the malware (ran through the Any.Run sandbox) decrypted and filtered in Wireshark.
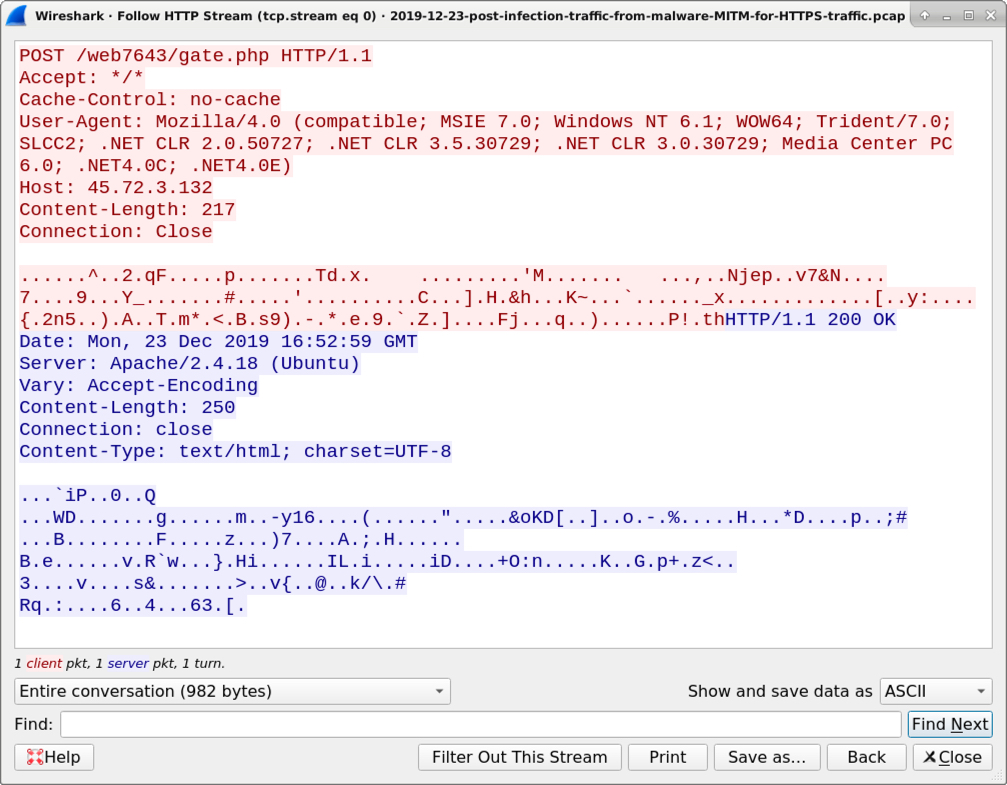
Shown above: One of the decrypted GET requests in HTTPS traffic caused by the malware.
Click here to return to the main page.
