2020-01-15 - QUICK POST: MALSPAM PUSHING REVENGE RAT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-01-15-RevengeRAT-infection-traffic.pcap.zip 555 kB (555,426 bytes)
- 2020-01-15-RevengeRAT-infection-traffic.pcap (661,632 bytes)
- 2020-01-15-malware-and-artifacts-from-RevengeRAT-infection.zip 450 kB (450,159 bytes)
- 2020-01-15-C-Users-bfett-AppData-Roaming-efinhodabumbum.vbs.txt (9,028 bytes)
- 2020-01-15-XLS-attachment-with-macro-for-Revenge-RAT.bin (229,376 bytes)
- 2020-01-15-malspam-pushing-RevengeRAT.eml (316,582 bytes)
- 2020-01-15-p_1472t0ztm1.jpg-from-a.top4top.io.txt (178,634 bytes)
- 2020-01-15-p_14754cwzr1-from-h.top4top.io.txt (9,028 bytes)
- 2020-01-15-p_1475rf4dz1.jpg-from-e.top4top.io.txt (316,417 bytes)
- 2020-01-15-registry-update-for-RevengeRAT.txt (590 bytes)
NOTES:
- The attached spreadsheet was submitted to the Any.Run sandbox, which revealed the HTTPS URLs in the traffic (link).
IMAGES
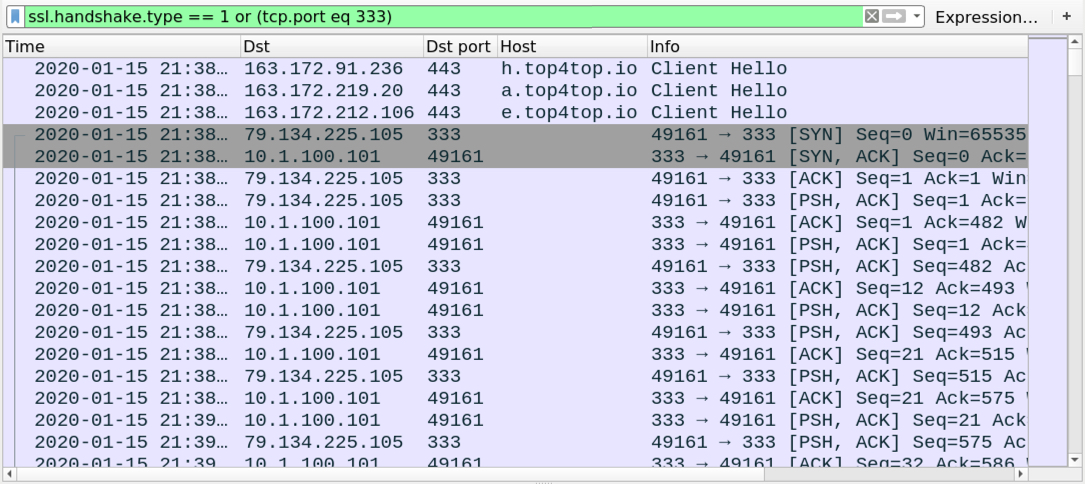
Shown above: Traffic from the infection filtered in Wireshark.

Shown above: TCP stream from the RevengeRAT callback traffic.
Click here to return to the main page.
