2020-01-23 - GERMAN MALSPAM PUSHES URSNIF (GOZI/ISFB)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-01-23-Ursnif-IOCs.txt.zip 2.8 kB (2,806 bytes)
- 2020-01-23-Ursnif-IOCs.txt (8,852 bytes)
- 2020-01-23-Ursnif-malspam-4-email-examples.zip 499 kB (498,616 bytes)
- 2020-01-23-Ursnif-malspam-example-1-of-4-0755-UTC.eml (163,039 bytes)
- 2020-01-23-Ursnif-malspam-example-2-of-4-0950-UTC.eml (173,339 bytes)
- 2020-01-23-Ursnif-malspam-example-3-of-4-0938-UTC.eml (170,776 bytes)
- 2020-01-23-Ursnif-malspam-example-4-of-4-1053-UTC.eml (167,974 bytes)
- 2020-01-23-Ursnif-infection-with-Ursnif-variant-as-follow-up-malware.pcap.zip 2.5 MB (2,477,854 bytes)
- 2020-01-23-Ursnif-infection-with-Ursnif-variant-as-follow-up-malware.pcap (2,884,627 bytes)
- 2020-01-23-Ursnif-malware-and-artifacts.zip 6.8 MB (6,821,552 bytes)
- 2020-01-23-Ursnif-DLL-retrieved-using-XSL-file-example-1-of-4.bin (176,128 bytes)
- 2020-01-23-Ursnif-DLL-retrieved-using-XSL-file-example-2-of-4.bin (176,128 bytes)
- 2020-01-23-Ursnif-DLL-retrieved-using-XSL-file-example-3-of-4.bin (176,128 bytes)
- 2020-01-23-Ursnif-DLL-retrieved-using-XSL-file-example-4-of-4.bin (176,128 bytes)
- 2020-01-23-XSL-file-dropped-after-enabling-macros-on-Word-doc-example-1-of-4.txt (3,694 bytes)
- 2020-01-23-XSL-file-dropped-after-enabling-macros-on-Word-doc-example-2-of-4.txt (3,687 bytes)
- 2020-01-23-XSL-file-dropped-after-enabling-macros-on-Word-doc-example-3-of-4.txt (3,928 bytes)
- 2020-01-23-XSL-file-dropped-after-enabling-macros-on-Word-doc-example-4-of-4.txt (3,975 bytes)
- 2020-01-23-another-Urnsif-variant-EXE-as-follow-up-malware-retrieved-by-Ursnif-infected-host.bin (1,026,048 bytes)
- 2020-01-23-example-of-registry-update-after-follow-up-Ursnif-variant-infection.txt (11,508,802 bytes)
- 2020-01-23-example-of-registry-update-caused-by-initial-Ursnif-infection.txt (10,693,630 bytes)
- 2020-01-23-extracted-Word-doc-with-macro-for-Ursnif-example-1-of-4.doc (127,878 bytes)
- 2020-01-23-extracted-Word-doc-with-macro-for-Ursnif-example-2-of-4.doc (127,845 bytes)
- 2020-01-23-extracted-Word-doc-with-macro-for-Ursnif-example-3-of-4.doc (127,906 bytes)
- 2020-01-23-extracted-Word-doc-with-macro-for-Ursnif-example-4-of-4.doc (127,673 bytes)
- 2020-01-23-password-protected-zip-archive-with-Word-doc-for-Ursnif-password-333-example-1-of-4.zip (117,028 bytes)
- 2020-01-23-password-protected-zip-archive-with-Word-doc-for-Ursnif-password-333-example-2-of-4.zip (116,997 bytes)
- 2020-01-23-password-protected-zip-archive-with-Word-doc-for-Ursnif-password-333-example-3-of-4.zip (117,062 bytes)
- 2020-01-23-password-protected-zip-archive-with-Word-doc-for-Ursnif-password-333-example-4-of-4.zip (116,825 bytes)
NOTES:
- I also saw German malspam pushing Ursnif on Tuesday 2020-01-21 (documented) and Wednesday 2020-01-22 (not documented).
- The follow-up malware in this case was another Ursnif variant, the same type documented on 2020-01-21.
- See this ISC diary for details on the malspam and infection traffic from Tuesday 2020-01-21.
IMAGES
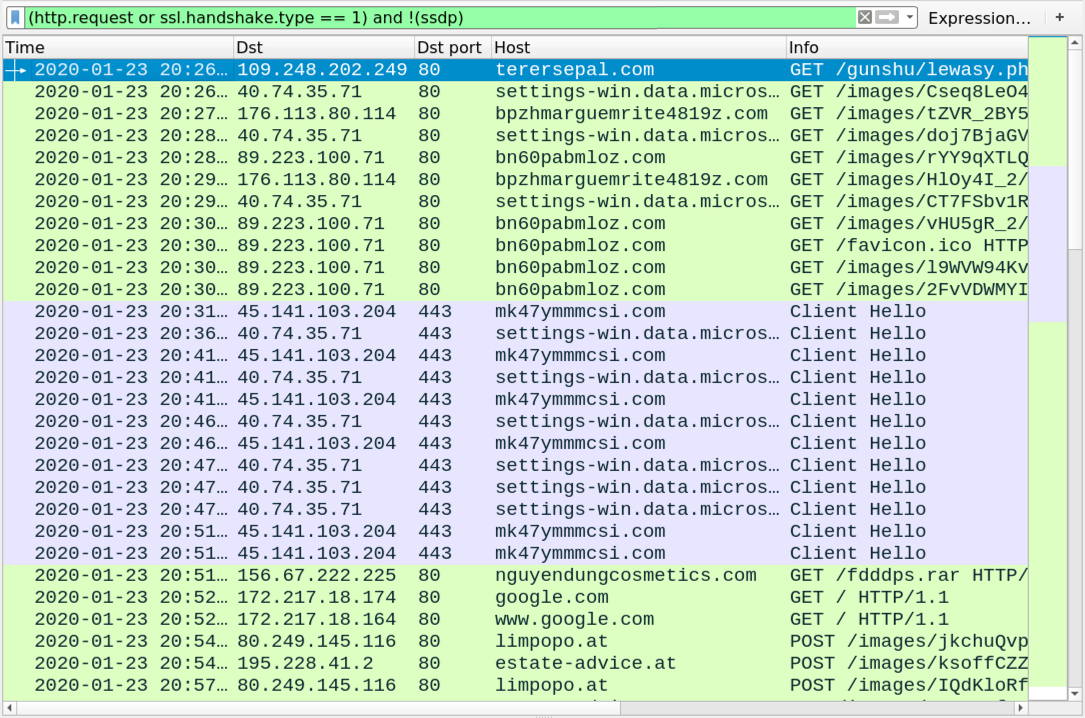
Shown above: Traffic from an infection filtered in Wireshark.
Click here to return to the main page.
