2020-03-10 - GERMAN MALSPAM WITH PASSWORD-PROTECTED ZIP FILES PUSHING URSNIF (GOZI/ISFB)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-03-10-Ursnif-IOCs.txt.zip kB (1,196 bytes)
- 2020-03-10-Ursnif-IOCs.txt (2,364 bytes)
- 2020-03-10-Ursnif-infection-from-German-malspam-with-password-protected-zip-attachment.pcap.zip 1.5 MB (1,465,314 bytes)
- 2020-03-10-Ursnif-infection-from-German-malspam-with-password-protected-zip-attachment.pcap (1,672,493 bytes)
- 2020-03-10-German-malspam-pushing-Ursnif-0702-UTC.eml.zip kB (45,593 bytes)
- 2020-03-10-German-malspam-pushing-Ursnif-0702-UTC.eml (60,680 bytes)
- 2020-03-10-Ursnif-malware-and-artifacts.zip 2.3 MB (2,276,038 bytes)
- 2020-03-10-Word-doc-with-macro-for-Ursnif.bin (70,656 bytes)
- 2020-03-10-initial-Ursnif-binary-DLL.bin (680,960 bytes)
- 2020-03-10-password-protected-zip-archive-password-123.zip (41,881 bytes)
- 2020-03-10-registry-update-to-keep-Ursnif-infection-persistent.txt (4,630,784 bytes)
IMAGES
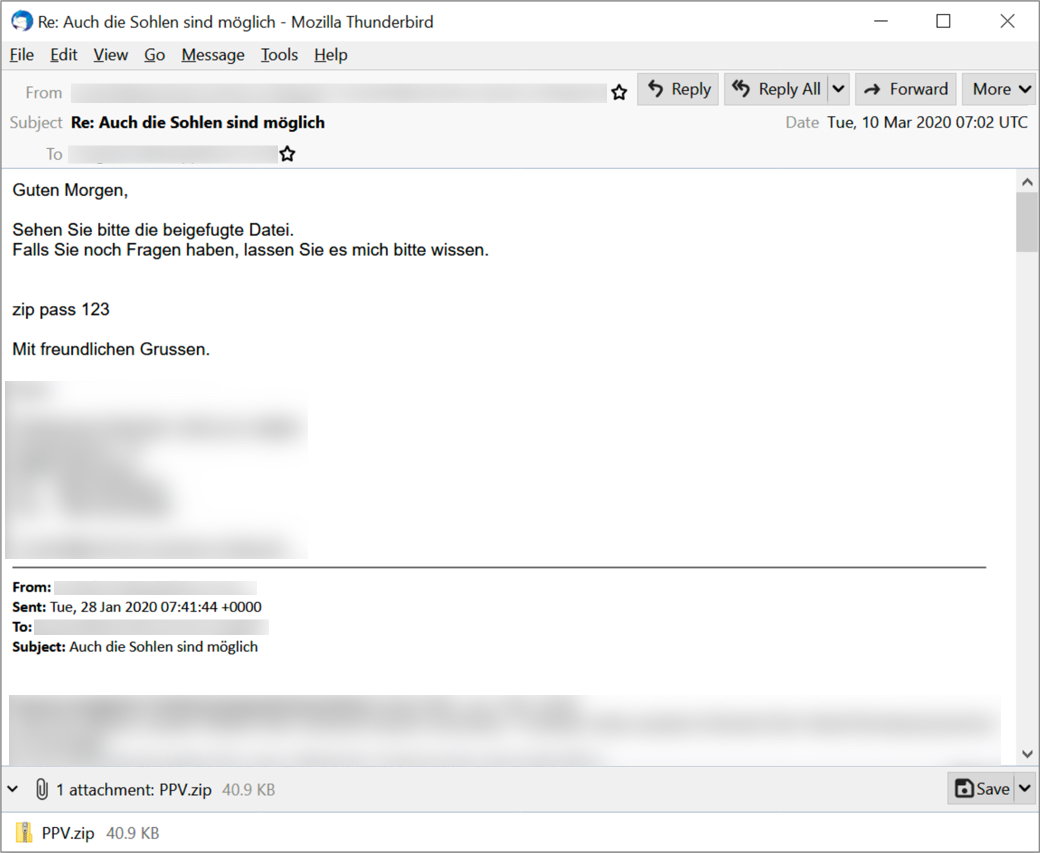
Shown above: Example of German malspam pushing Ursnif on 2020-03-10.
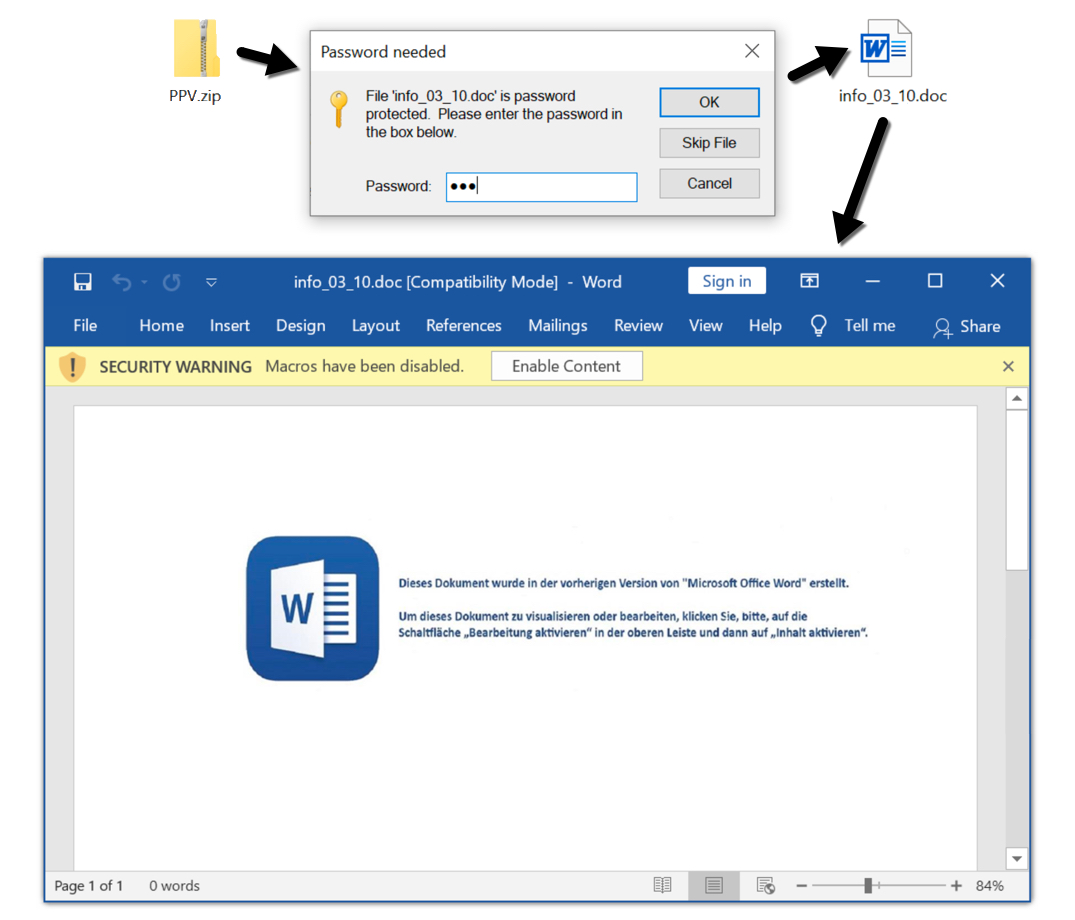
Shown above: Extracting a Word doc from the password-protected zip file.
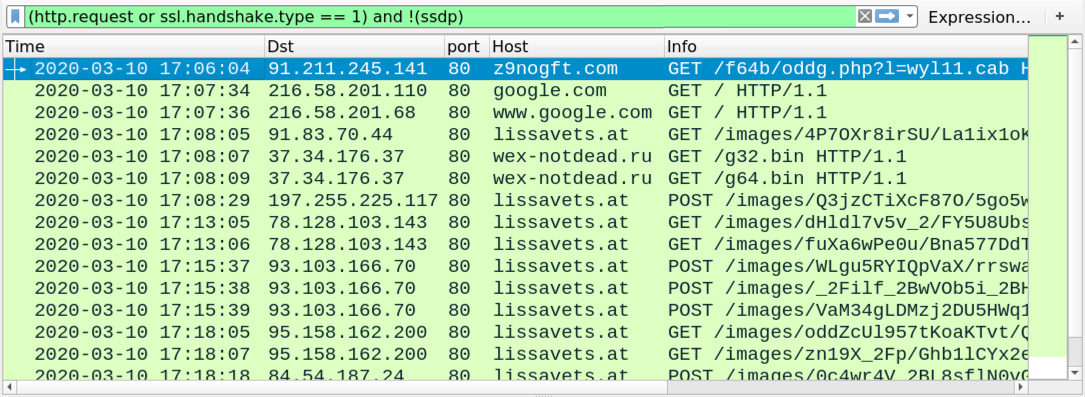
Shown above: Traffic from the infection filtered in Wireshark.
Click here to return to the main page.
