2020-03-12 - WORD DOC MACRO CAUSES A MALWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-03-12-infection-IOCs.txt.zip 1.6 kB (1,624 bytes)
- 2020-03-12-infection-IOCs.txt (3,670 bytes)
- 2020-03-12-infection-traffic.pcap.zip 10.2 MB (10,180,696 bytes)
- 2020-03-12-infection-traffic.pcap (10,574,029 bytes)
- 2020-03-12-malware-and-artifacts.zip 9.6 MB (9,552,006 bytes)
- Invoice.doc (427,476 bytes)
- MyImages/Louu6hbte.exe (621,568 bytes)
- MyImages/presskey.cmd (22,213 bytes)
- MyImages/presskey.jse (160 bytes)
- MyImages/presskey.jse4 (160 bytes)
- MyImages/presskey.jse5 (338,244 bytes)
- MyImages/presskey2.cmd (160 bytes)
- MyImages/tlofgkkjl15g5k.vbs (0 bytes)
- Roaming/Avex/ozkaar.zu (0 bytes)
- Roaming/Faaxho/pofiagq.biu (956,907 bytes)
- Roaming/Gabo/agcoxyob.yfzu (268,800 bytes)
- Roaming/Ifud/iwgoa.cea (3,365,559 bytes)
- Roaming/Ipdoud/fudoixaf.ono (490,292 bytes)
- Roaming/Reoxpi/ufko.wyudn (318,882 bytes)
- Roaming/Riov/koba.ru (303,224 bytes)
- Roaming/Ruyp/
- Roaming/Tytiw/ozutpoow.exe (1,267,712 bytes)
- Roaming/Ycuvi/anzoa.zo (1,968,439 bytes)
- Roaming/Ykimxo/
- Roaming/Ykyz/icgur.ugig (130,560 bytes)
IMAGES
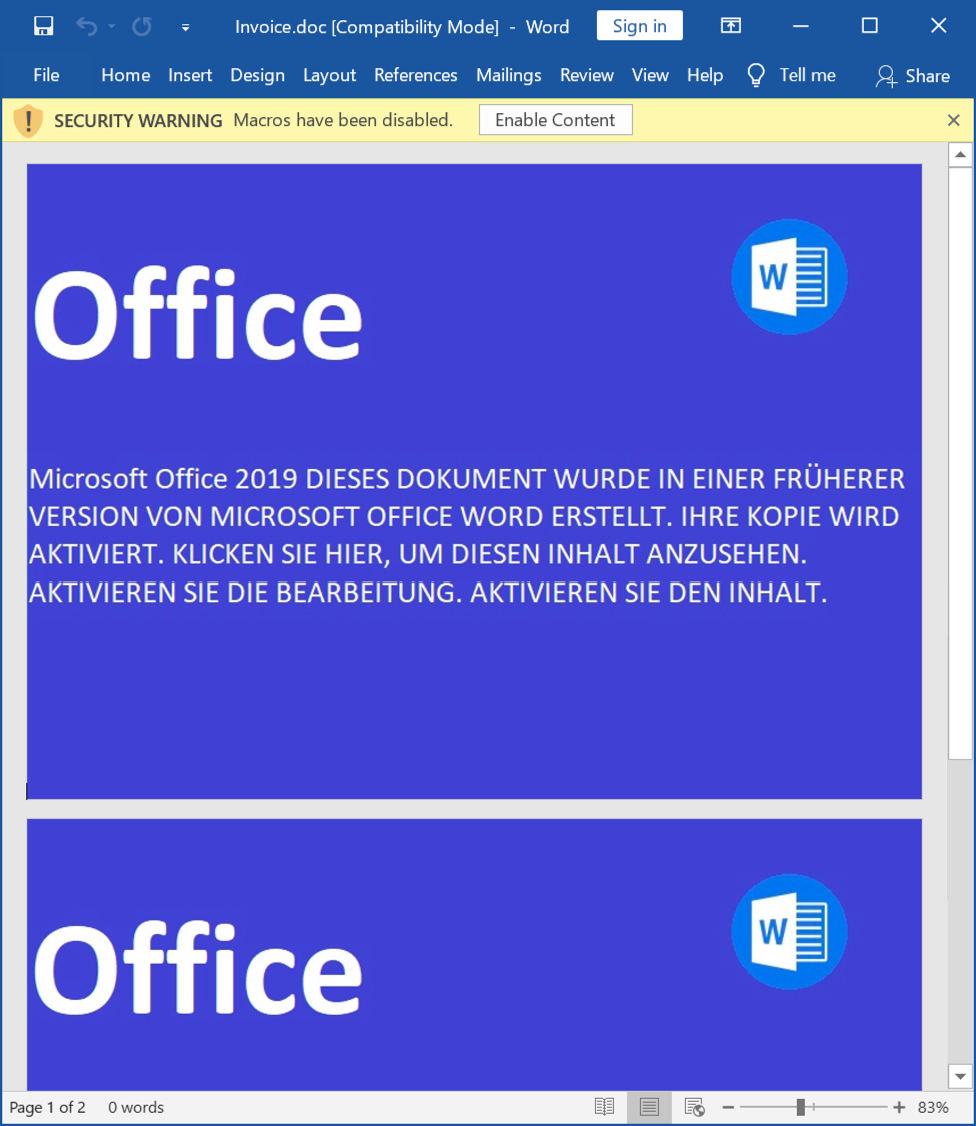
Shown above: Word doc with macros to kick off this infection.
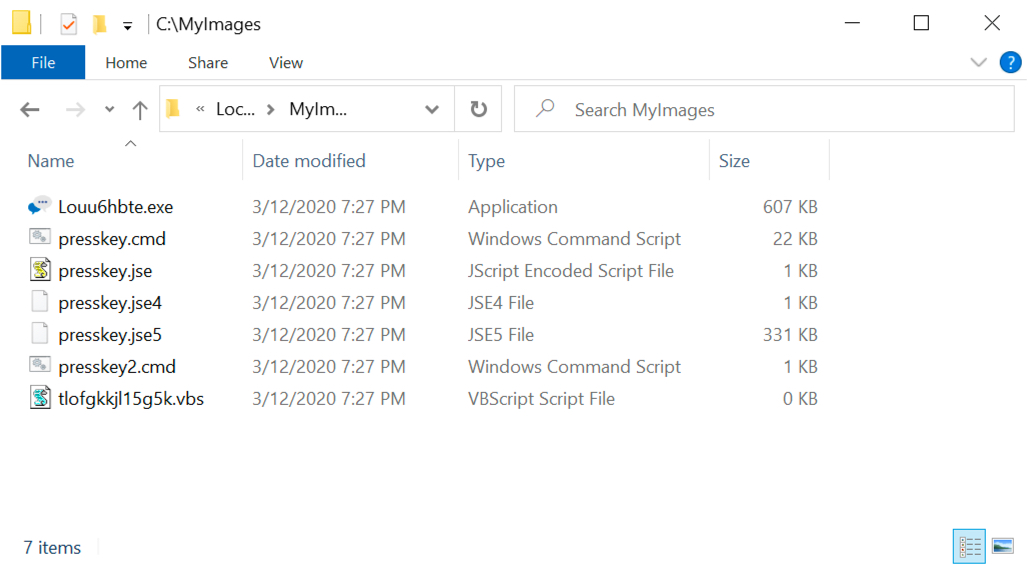
Shown above: Artifacts created immediately after enabling macros.
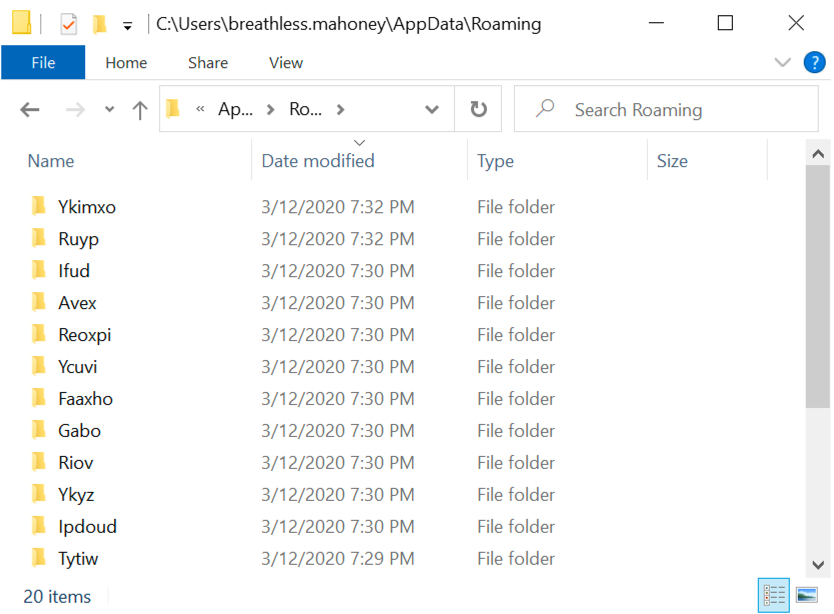
Shown above: Folders created in the infected user's AppData\Roaming directory.
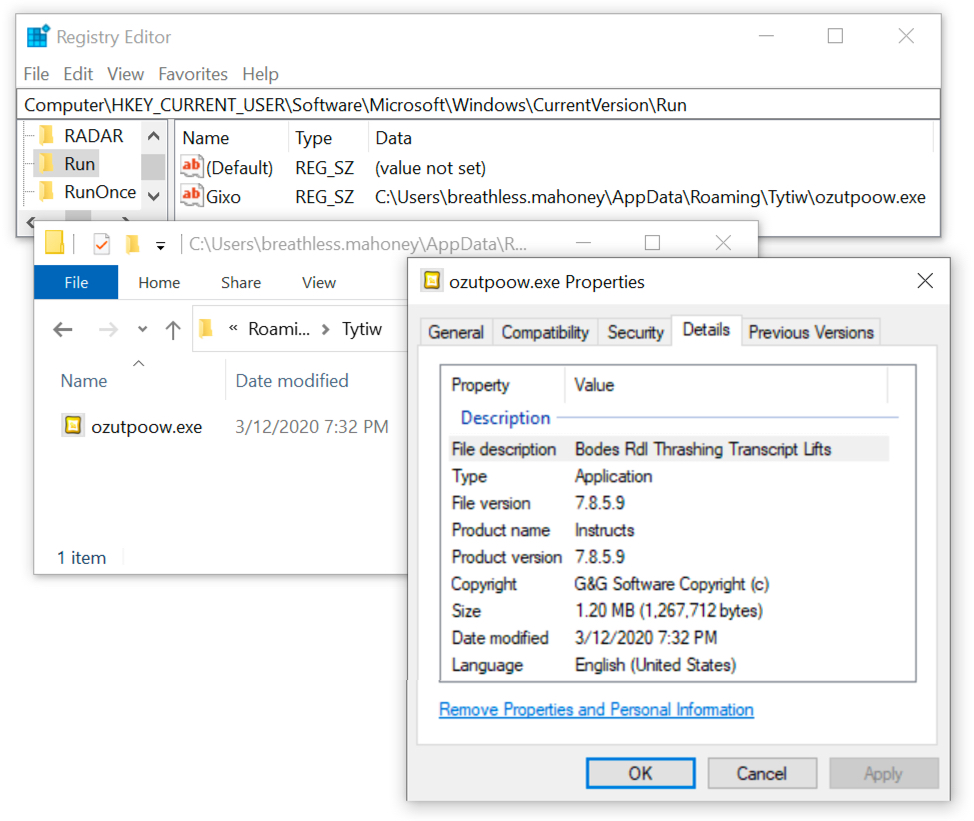
Shown above: Malware persistent on the infected Windows 10 host.
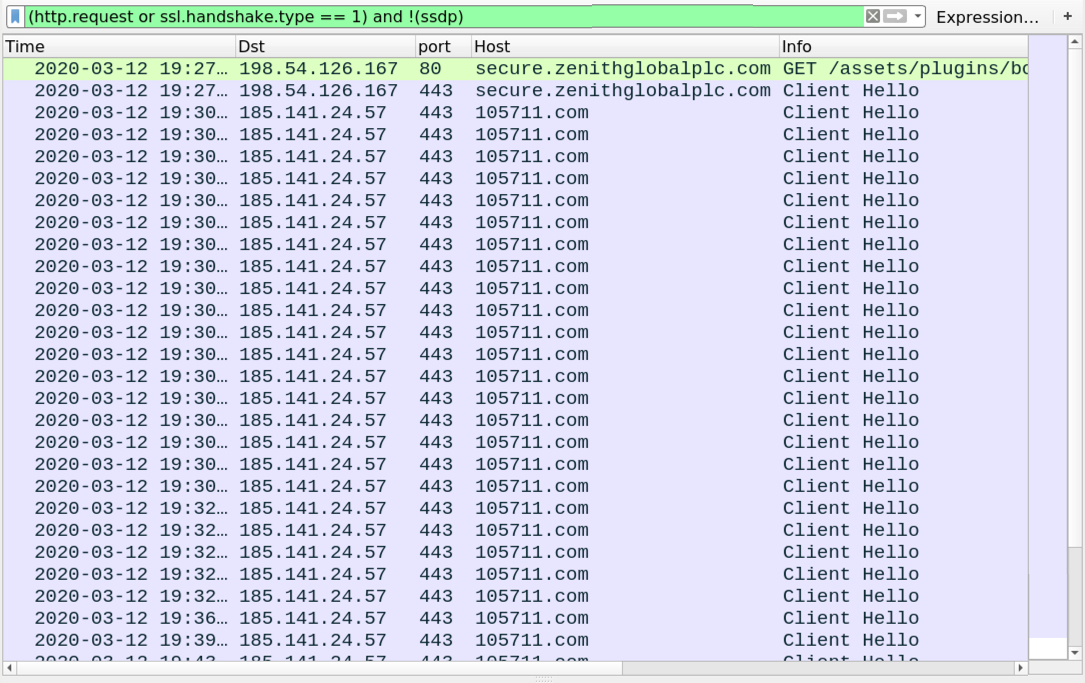
Shown above: Traffic from the infection filtere din Wireshark.
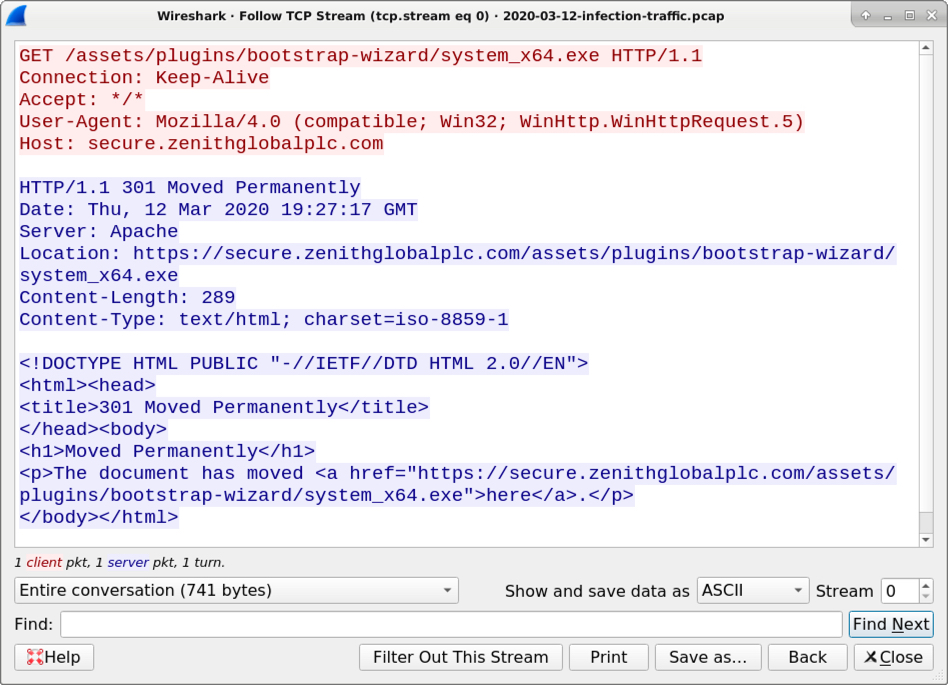
Shown above: HTTP request for a malware EXE.
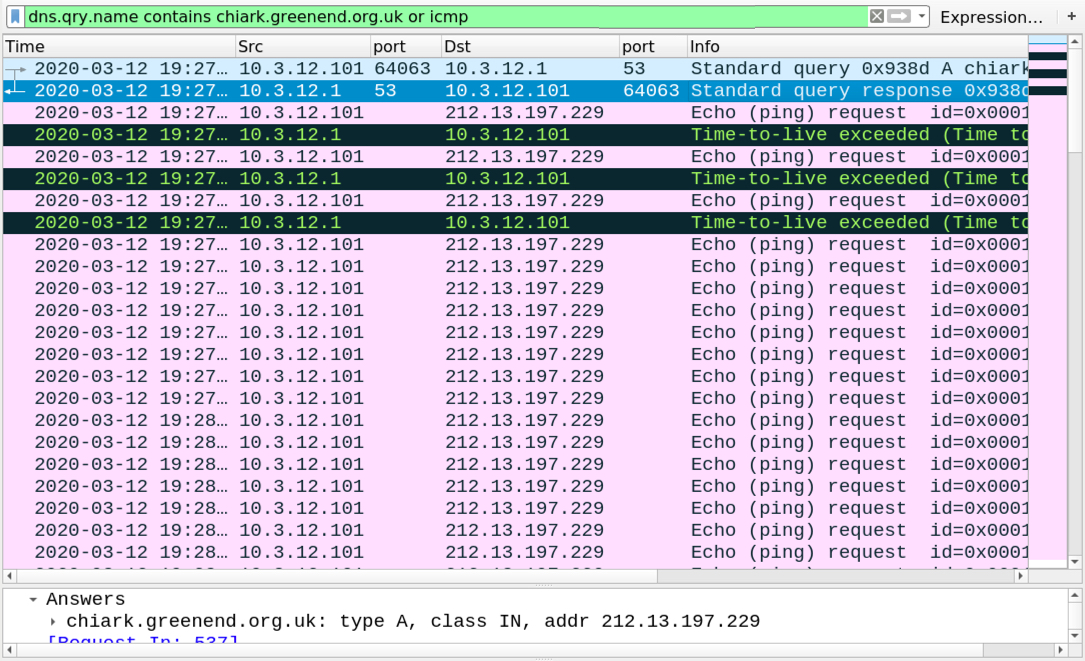
Shown above: DNS query to a UK domain followed by ICMP traffic to the address for that domain.
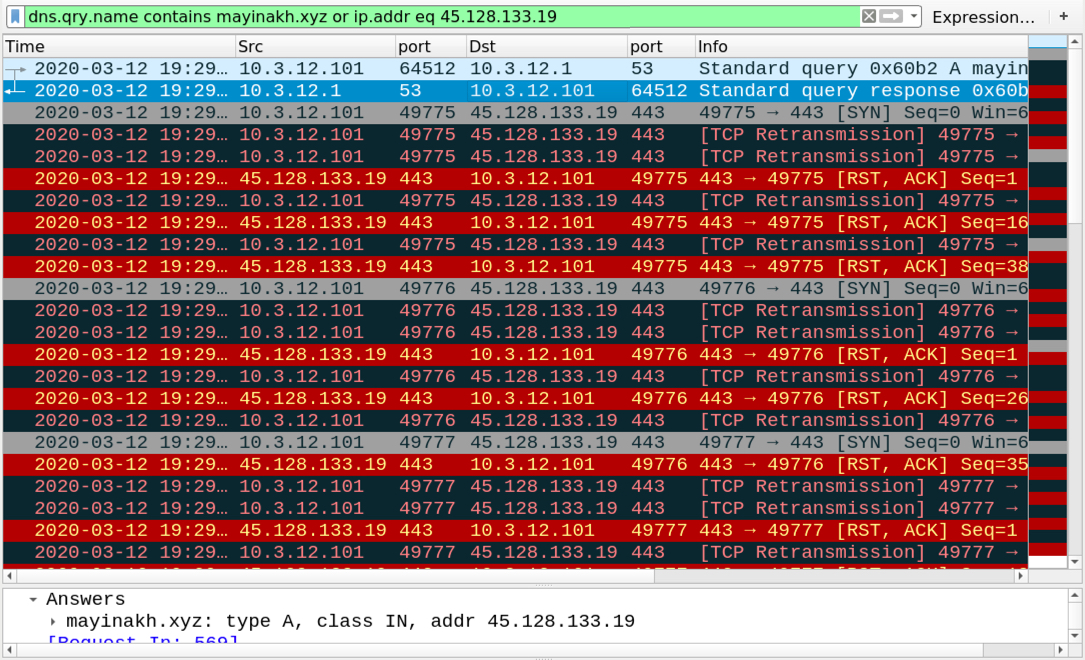
Shown above: DNS query to an XYZ domain followed by attempted TCP connections.
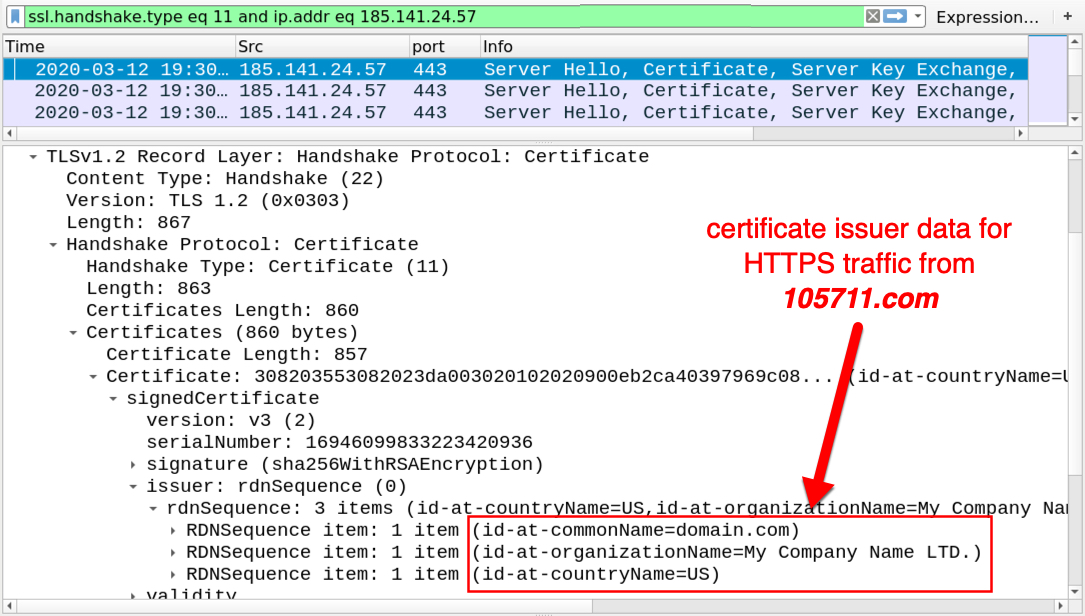
Shown above: Certificate issuer data for traffic to 105711[.]com.
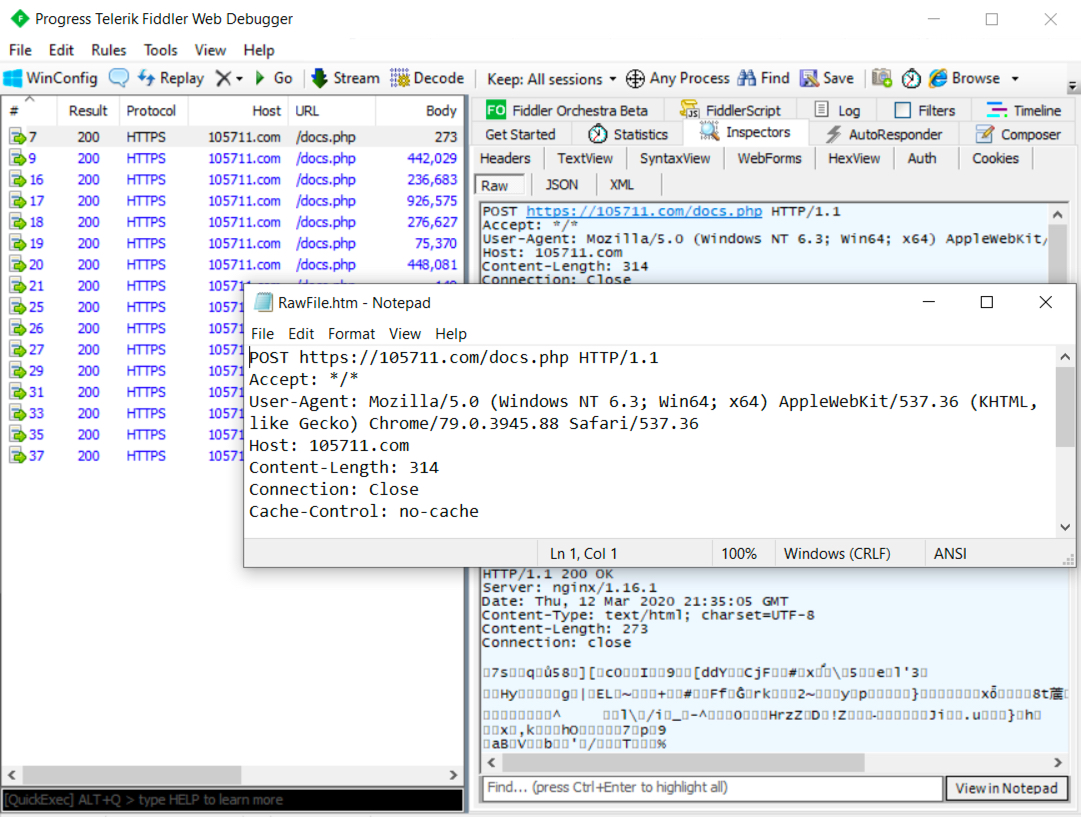
Shown above: Fiddler capture showing HTTPS traffic to 105711[.]com.
Click here to return to the main page.
