2020-03-19 - ENGLISH MALSPAM PUSHES URSNIF (GOZI/IFSB)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-03-19-Ursnif-IOCs.txt.zip 1.2 kB (1,236 bytes)
- 2020-03-19-Ursnif-IOCs.txt (1,943 bytes)
- 2020-03-19-Ursnif-infection-traffic.pcap.zip 647 kB (646,922 bytes)
- 2020-03-19-Ursnif-infection-traffic.pcap (997,531 bytes)
- 2020-03-19-Ursnif-malware-and-artifacts.zip 2.5 MB (2,520,270 bytes)
- 2020-03-19-Word-doc-with-macro-for-Ursnif.bin (60,279 bytes)
- 2020-03-19-initial-Ursnif-DLL-retreived-after-enabling-Word-macro.bin (347,136 bytes)
- 2020-03-19-not-malicious-copy-of-MSHTA.EXE-dropped-after-enabling-Word-macro.bin (13,312 bytes)
- 2020-03-19-password-protected-zip-archive-password-333.zip (54,224 bytes)
- 2020-03-19-registry-update-caused-by-Ursnif.txt (10,799,368 bytes)
- 2020-03-19-script-dropped-after-enabling-macros.txt (1,928 bytes)
NOTES:
- Chain of events: malspam --> password-protected zip attachment --> extracted Word doc --> enable macros --> Ursnif
IMAGES
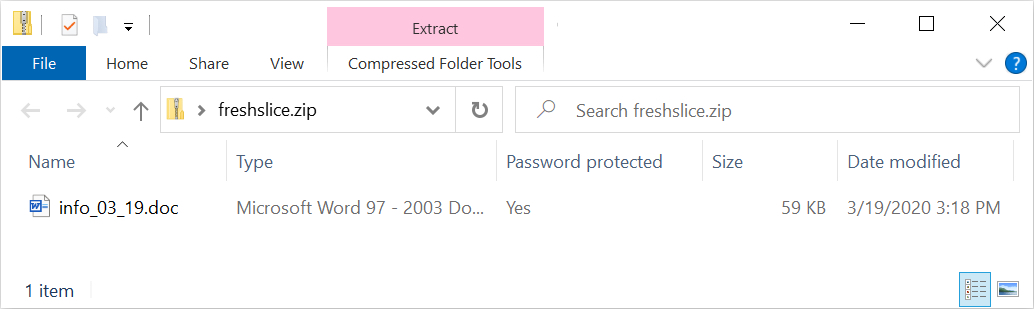
Shown above: Example of an attachment from this malspam.
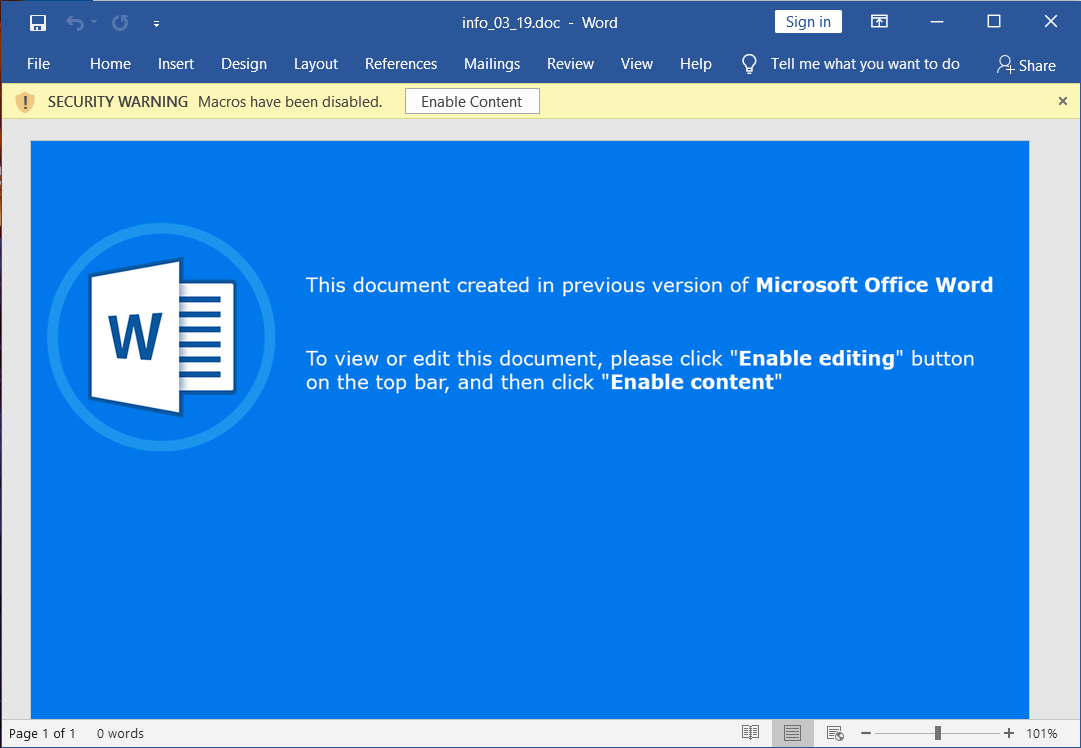
Shown above: Screenshot of the Word doc.
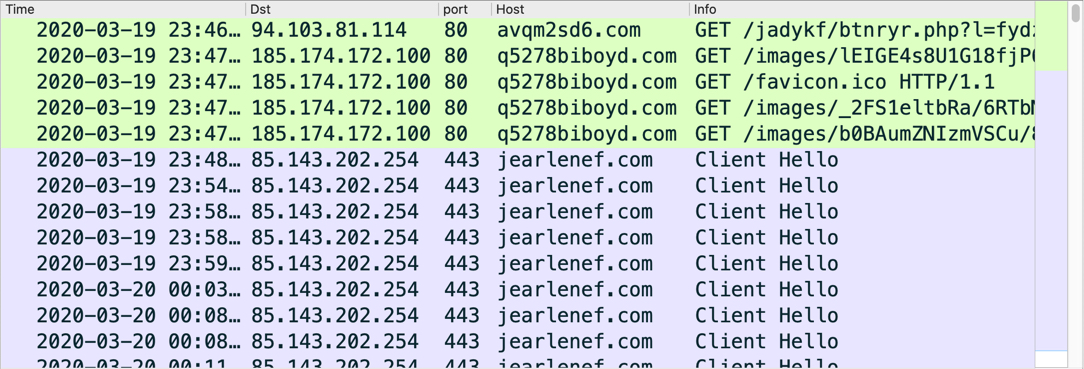
Shown above: Traffic from an infection filtered in Wireshark.
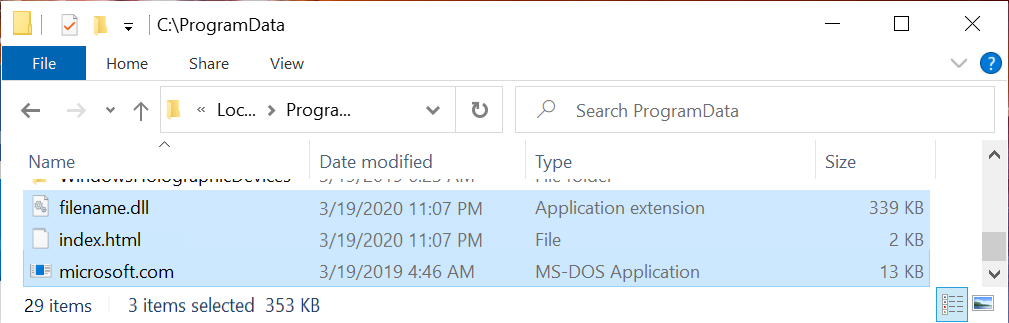
Shown above: Some items seen after enabling macros on the Word doc.
Click here to return to the main page.
