2020-03-23 - INFO_03_23.DOC PUSHES MALWARE (VALAK, MAYBE?)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-03-23-infection-IOCs.txt.zip 2.0 kB (1,958 bytes)
- 2020-03-23-infection-traffic-from-info_03_23.pcap.zip 270 kB (270,381 bytes)
- 2020-03-23-malware-and-artifacts.zip 380 kB (380,011 bytes)
IMAGES
Shown above: Extracting info_03_23.doc from the zip archive.
Shown above: Screenshot of the Word doc.
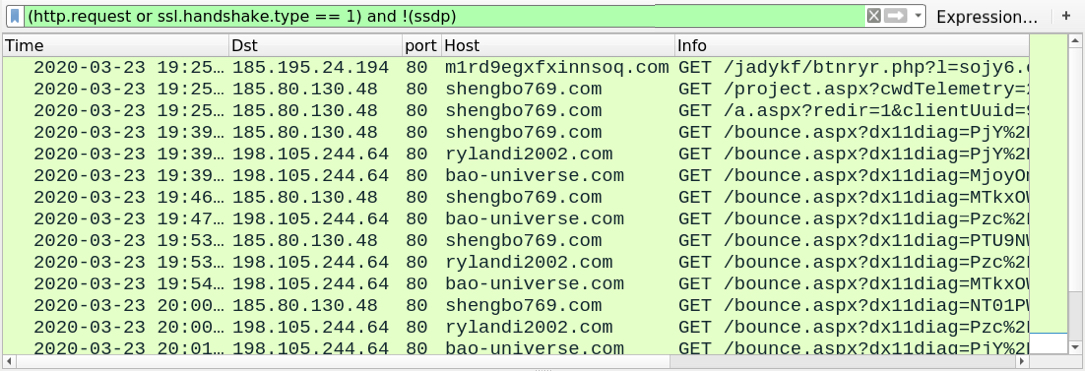
Shown above: Traffic from the infection filtered in Wireshark.
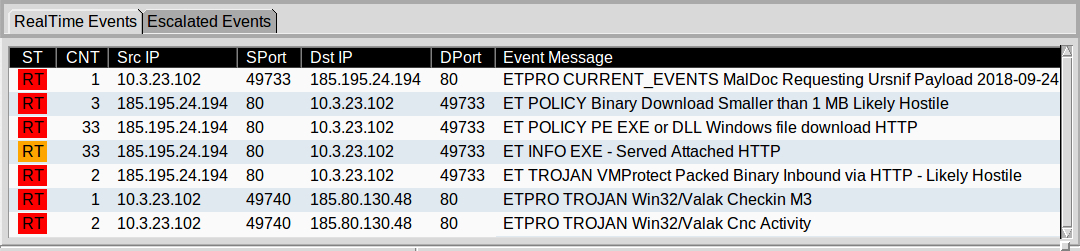
Shown above: Alerts using the ETPRO ruleset from Suricata using Sguil in Security Onion.
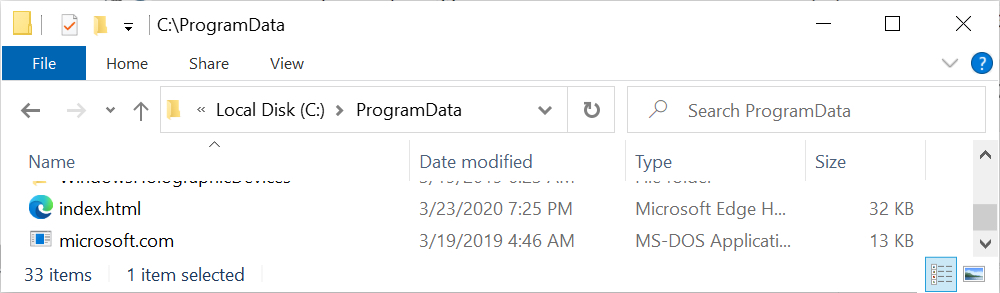
Shown above: Initial artifacts dropped after enabling macros.
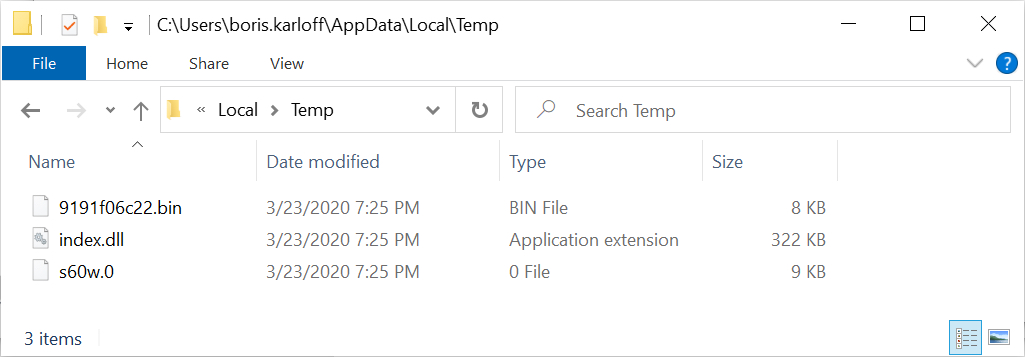
Shown above: Follow-up malware/artifacts.
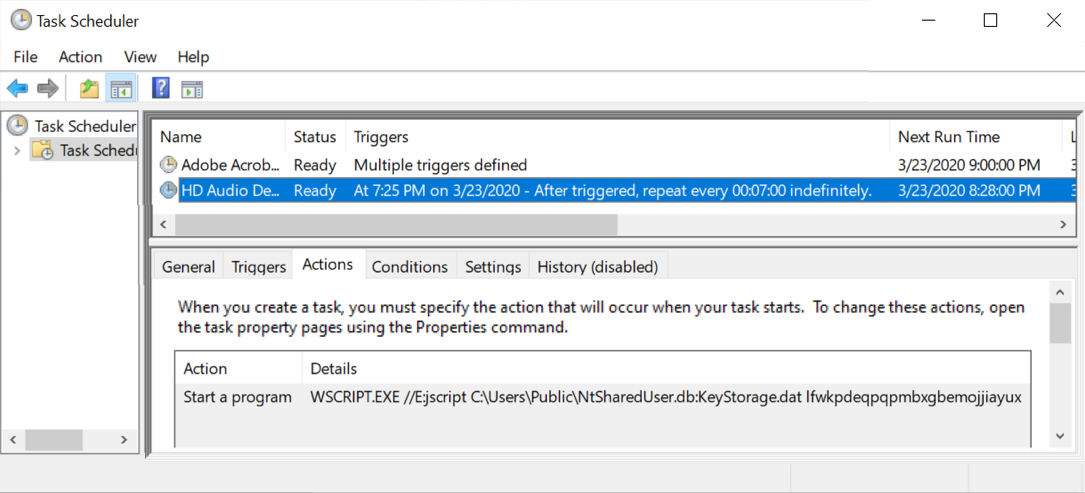
Shown above: Scheduled task to keep the infection persistent, indicating use of an Alternate Data Stream (ADS).
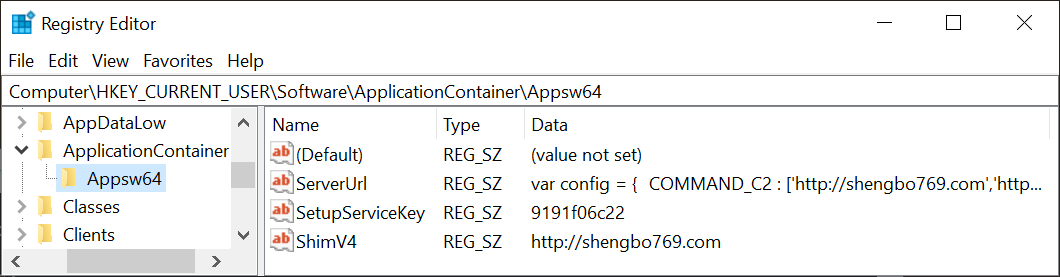
Shown above: Windows registry updates created during this infection.
Click here to return to the main page.
