2020-03-26 - INFORMATION_03_26.DOC PUSHES ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-03-26-ZLoader-IOCs.txt.zip 2.1 kB (2,147 bytes)
- 2020-03-26-example-of-malspam-pushing-ZLoader.txt.zip 122 kB (122,156 bytes)
- 2020-03-26-ZLoader-infection-traffic.pcap.zip 8.3 MB (8,324,485 bytes)
- 2020-03-26-ZLoader-malware-and-artifacts.zip 8.6 MB (8,579,745 bytes)
NOTES:
- This particular campaign has been pushing Ursnif since sometime in 2018.
- Starting earlier this month, I've sometimes seen other malware instead of Ursnif.
IMAGES
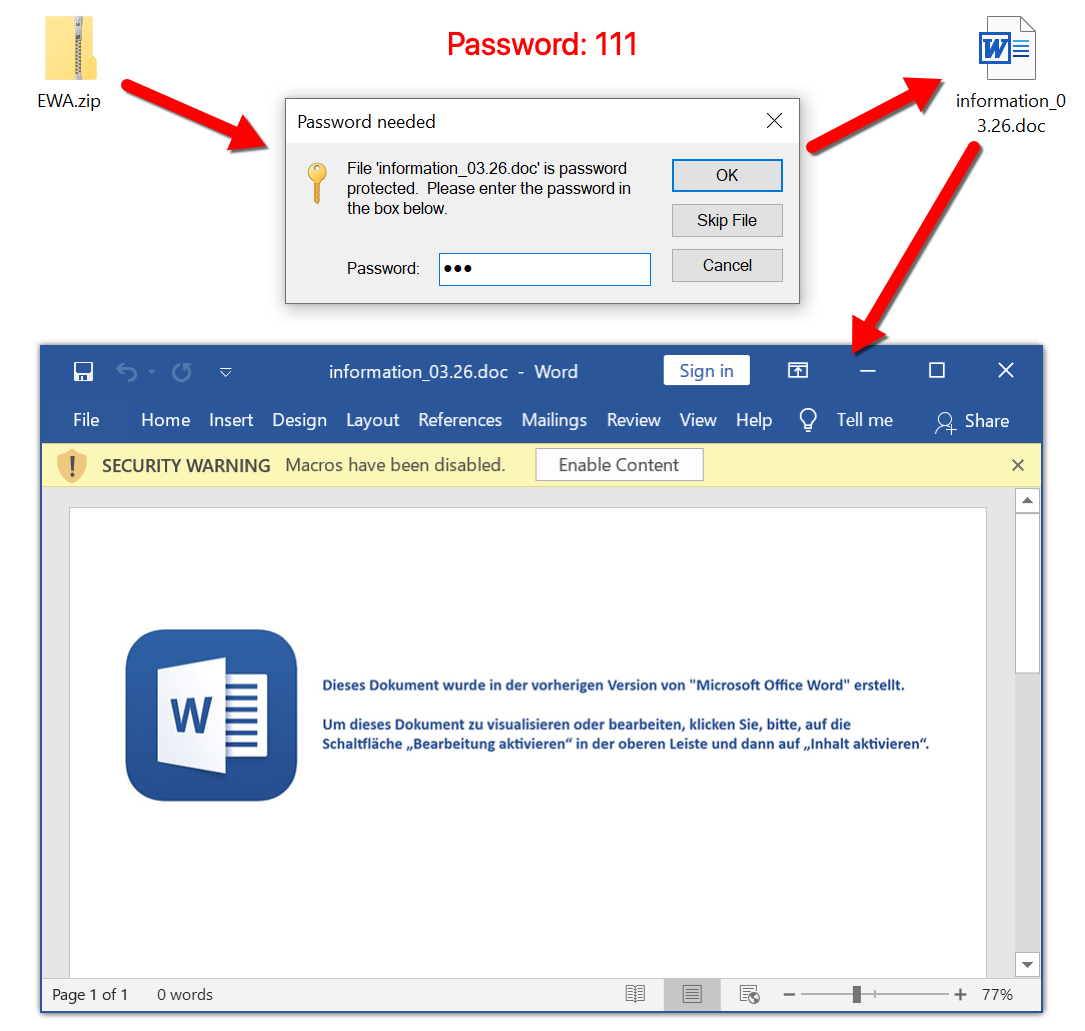
Shown above: Extracting information_03_26.doc from the zip archive.
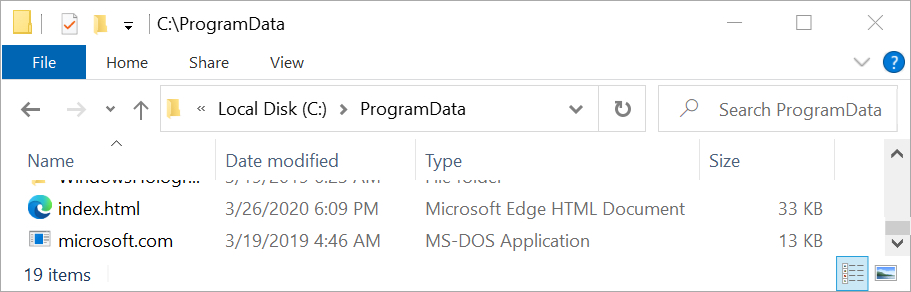
Shown above: Artifact immediately dropped after enabling macros on information_03_26.doc.
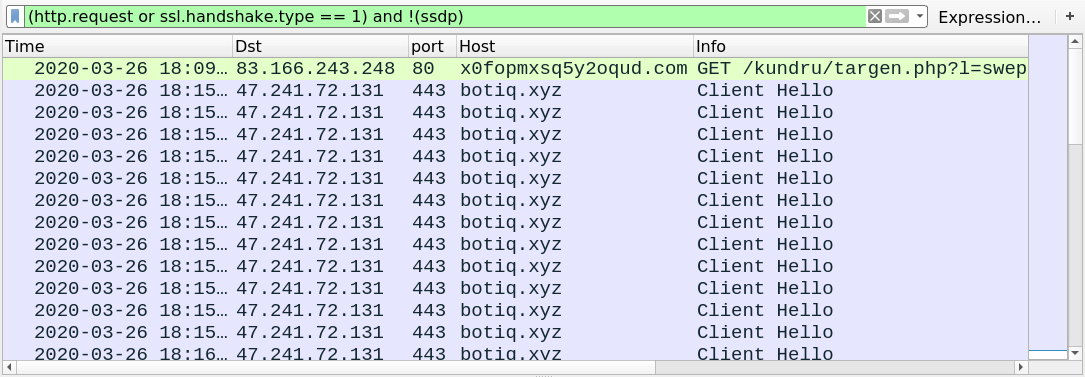
Shown above: Traffic from the infection filtered in Wireshark.
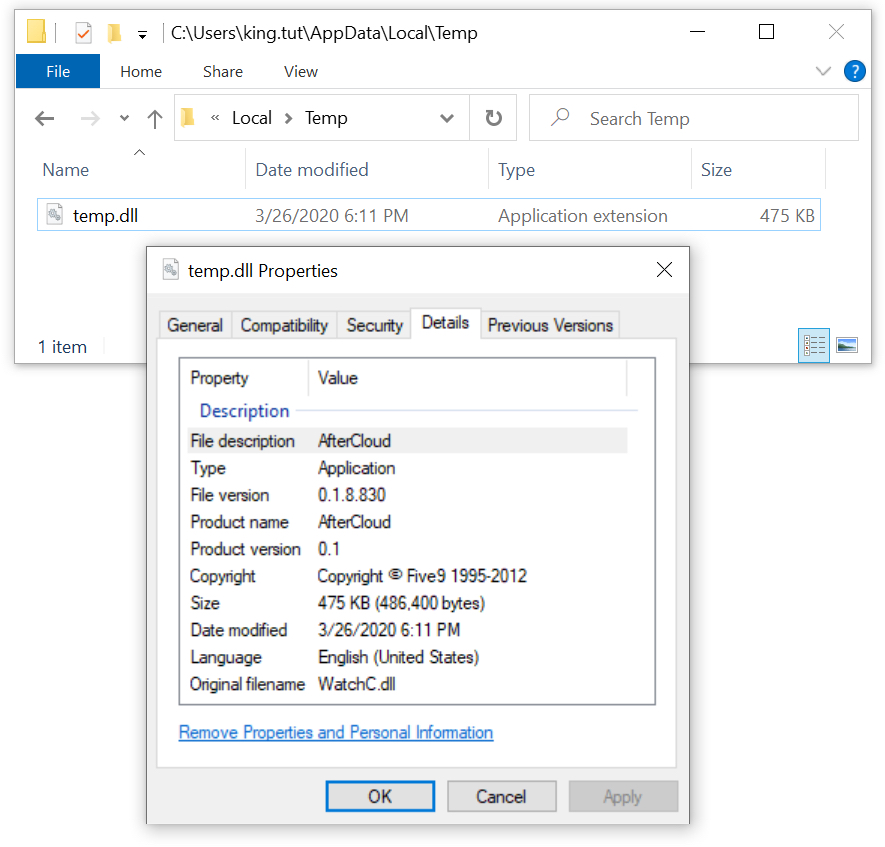
Shown above: The initial DLL seen in today's wave for this campaign. In this case, it's ZLoader.
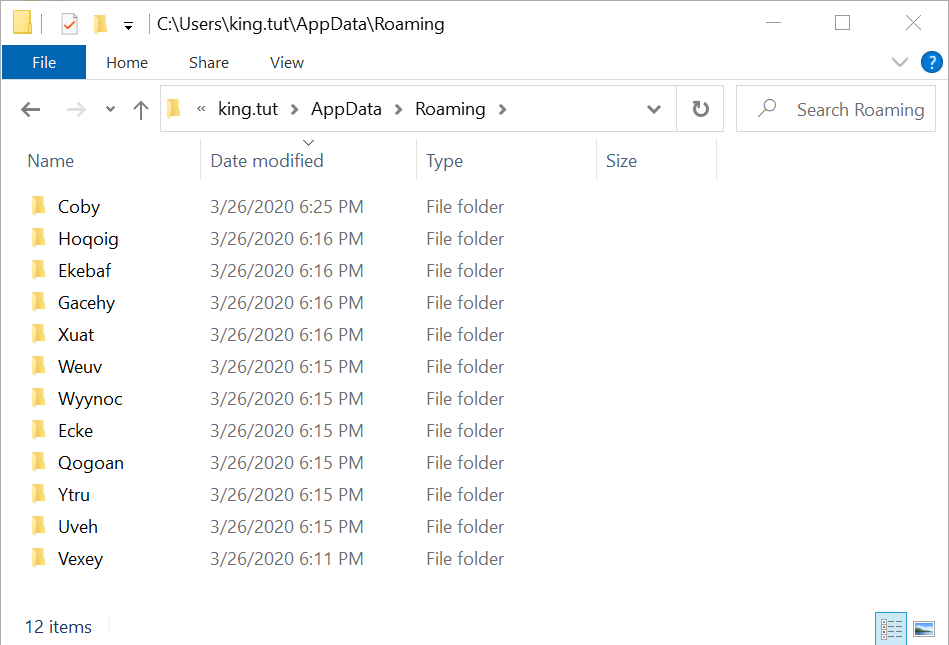
Shown above: Some of the decoy folders created along with the folder for the persistent ZLoader DLL.
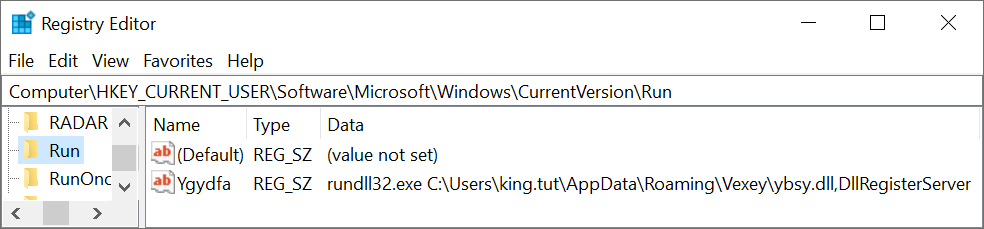
Shown above: Registry update to keep the ZLoader infection persistent.
Click here to return to the main page.
