2020-03-27 - PRICE_REQUEST_9830.DOC PUSHES ICEDID (BOKBOT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-03-27-IcedID-IOCs.txt.zip 1.5 kB (1,518 bytes)
- 2020-03-27-IcedID-infection-traffic.pcap.zip 5.1 MB (5,074,906 bytes)
- 2020-03-27-IcedID-malware-and-artifacts.zip 1.4 MB (1,401,369 bytes)
NOTES:
- This is my second IcedID sample since 2020-03-20 that doesn't generate any websocket traffic over HTTP (see my 2020-03-20 blog post for the first sample).
IMAGES
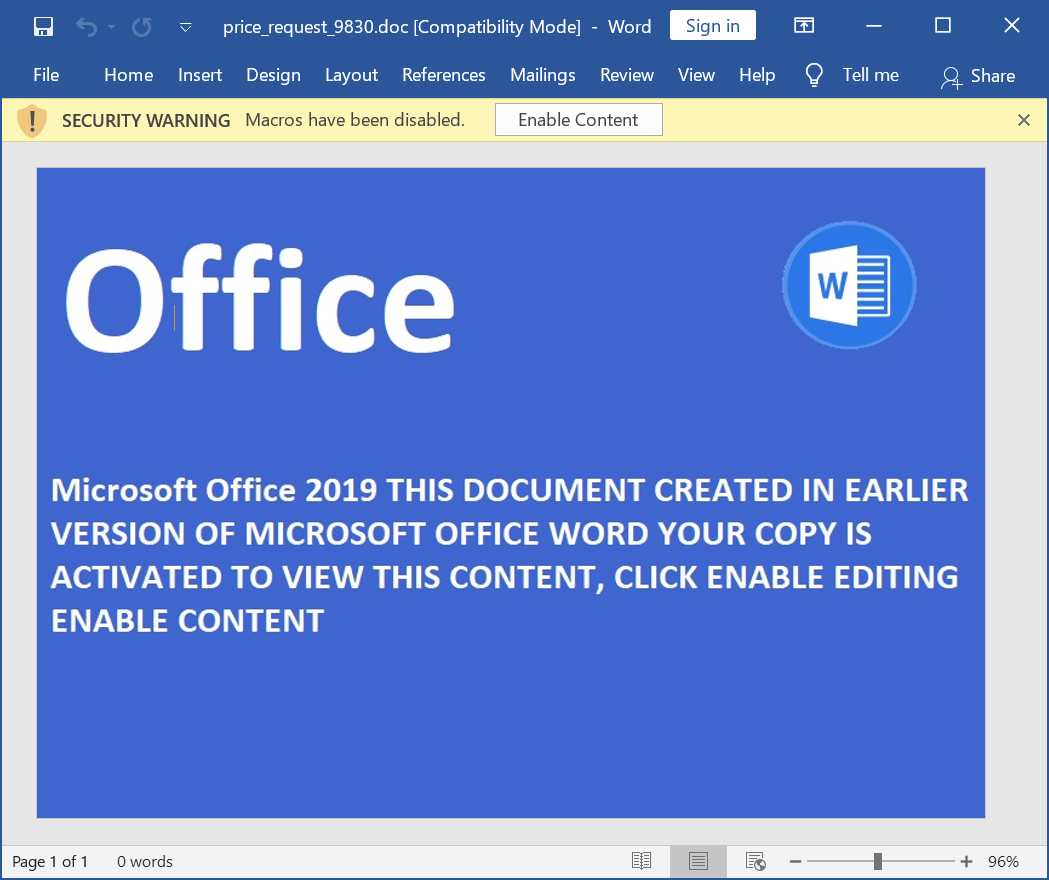
Shown above: Screenshot of price_request_9830.doc.
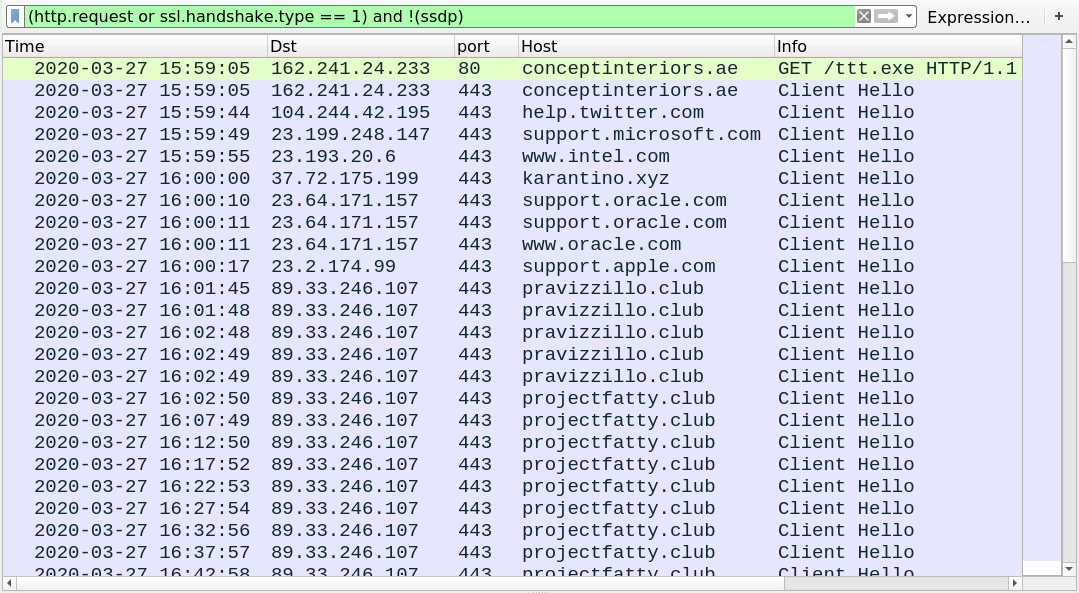
Shown above: Traffic from the infection filtered in Wireshark.
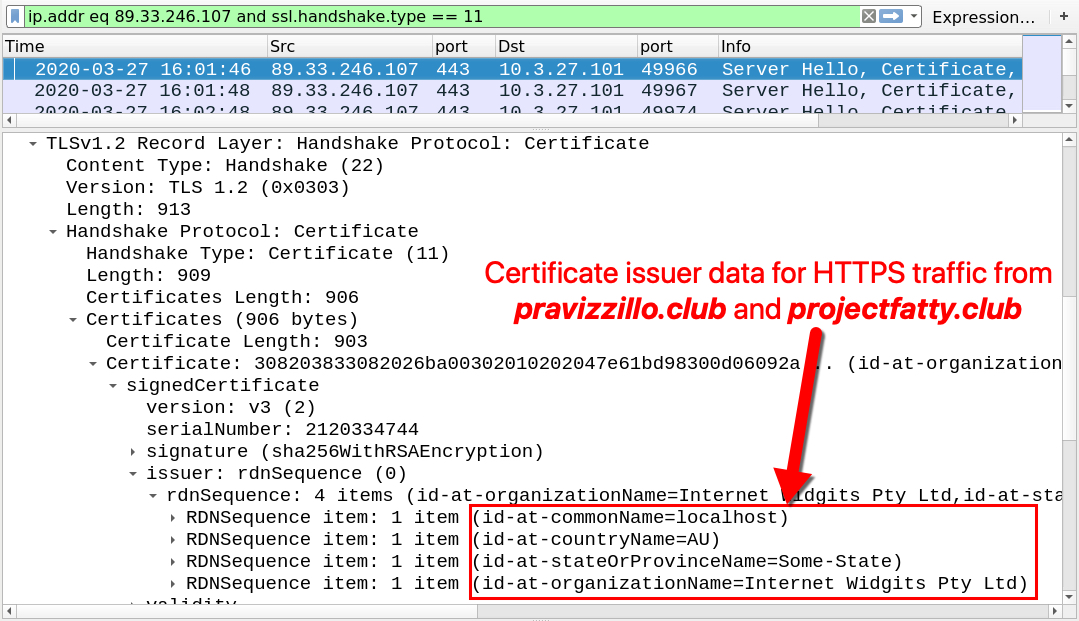
Shown above: Certificate issuer data from the IcedID post-infection HTTPS traffic.
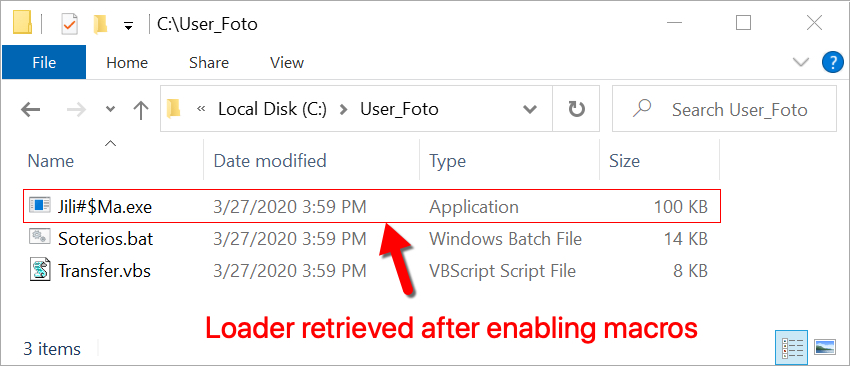
Shown above: Artifacts that appeared after enabling macros.
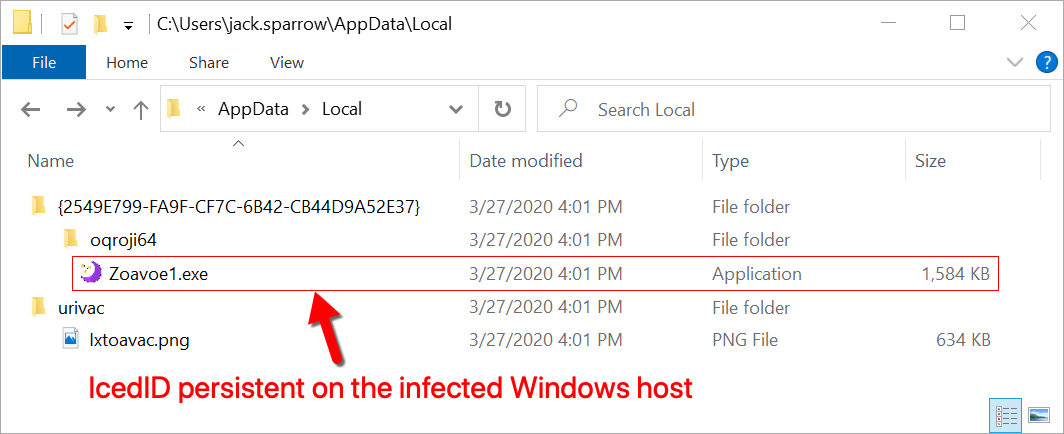
Shown above: IcedID persistent on the infected Windows host.
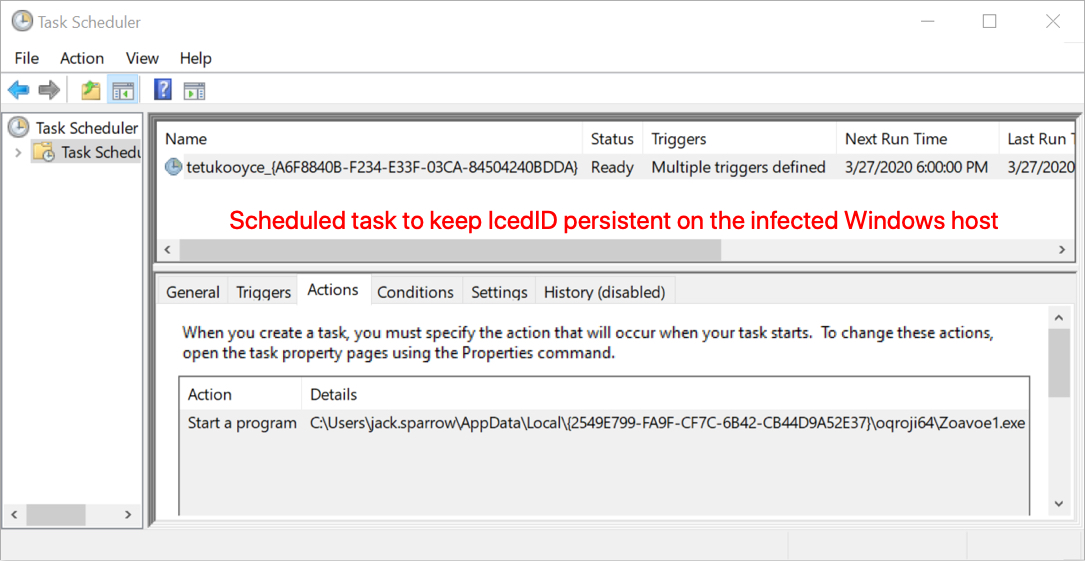
Shown above: Scheduled task to keep IcedID persistent.
Click here to return to the main page.
