2020-04-14 - TWO INFECTIONS FOR GULOADER WITH NETWIRE RAT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-04-14-GuLoader-for-NetWire-RAT-IOCs.txt.zip 1.2 kB (1,151 bytes)
- 2020-04-14-GuLoader-for-NetWire-RAT-IOCs.txt (2,506 bytes)
- 2020-04-14-GuLoader-for-NetWire-RAT-two-pcaps.zip 645 kB (644,661 bytes)
- 2020-04-14-GuLoader-for-NetWire-RAT-1st-run.pcap (393,992 bytes)
- 2020-04-14-GuLoader-for-NetWire-RAT-2nd-run.pcap (403,266 bytes)
- 2020-04-14-GuLoader-for-NetWire-RAT-malware-and-artifacts.zip 407 kB (406,886 bytes)
- 2020-04-14-1st-run-downloaded-Word-doc-with-macro-for-GuLoader.bin (150,895 bytes)
- 2020-04-14-1st-run-GuLoader-EXE-from-hunchasko.com.bin (53,248 bytes)
- 2020-04-14-1st-run-registry-update-for-GuLoader.txt (610 bytes)
- 2020-04-14-2nd-run-downloaded-Word-doc-with-macro-for-GuLoader.bin (150,848 bytes)
- 2020-04-14-2nd-run-GuLoader-EXE-from-crowe.llc.bin (53,248 bytes)
- 2020-04-14-2nd-run-registry-update-for-GuLoader.txt (584 bytes)
- 2020-04-14-both-runs-Tax_file.bin-from-sharefile2020.com.bin (151,616 bytes)
NOTES:
- This looks very similar to traffic from last month that I wrote about in a blog for Palo Alto Networks (link).
IMAGES
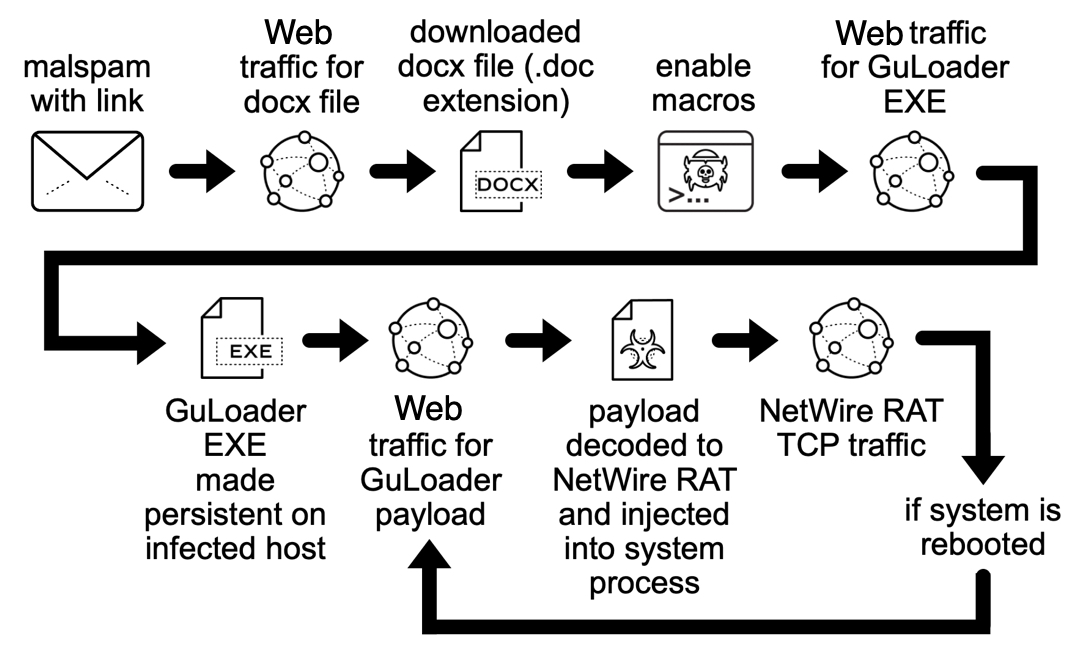
Shown above: Flow chart for this chain of events (slightly modified from my Palo Alto Networks blog post).
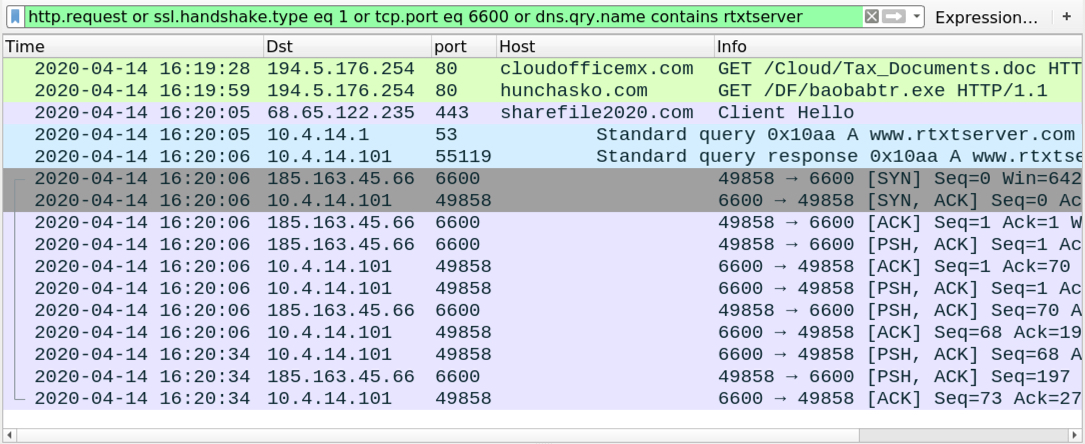
Shown above: Traffic from the 1st run filtered in Wireshark.
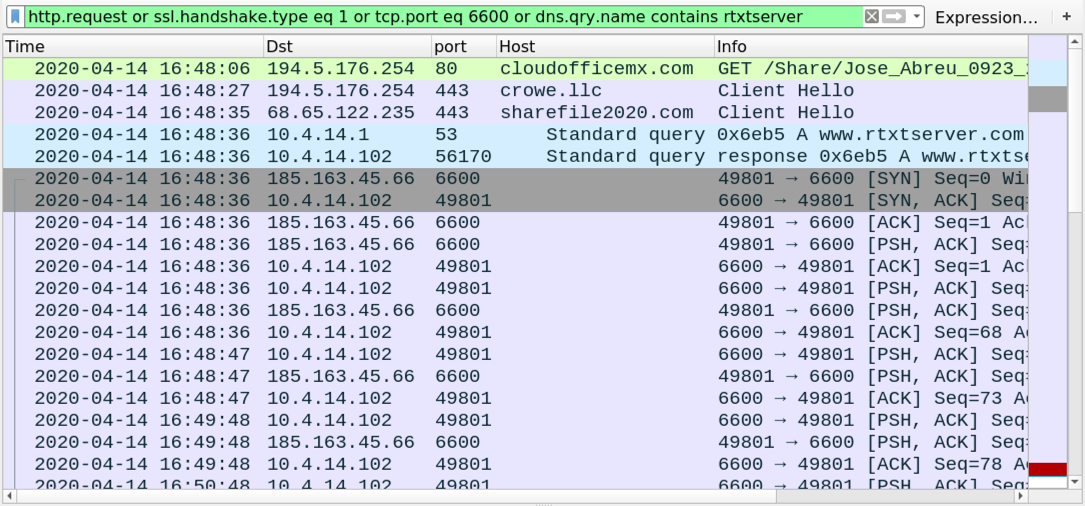
Shown above: Traffic from the 2nd run filtered in Wireshark.
Click here to return to the main page.
