2020-05-27 - MALSPAM --> PASSWORD-PROTECTED ZIP --> WORD DOC --> VALAK --> ICEDID (BOKBOT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-05-27-IOCs-from-Valak-infection-with-IcedID.txt.zip 2.4 kB (2,406 bytes)
- 2020-05-27-IOCs-from-Valak-infection-with-IcedID.txt (4,263 bytes)
- 2020-05-27-Valak-malspam-2-examples.zip 178 kB (177,551 bytes)
- 2020-05-27-Valak-malspam-example-1-of-2.eml (109,610 bytes)
- 2020-05-27-Valak-malspam-example-2-of-2.eml (165,444 bytes)
- 2020-05-27-six-examples-of-Word-docs-with-macros-for-Valak.zip 383 kB (383,259 bytes)
- input-05.27.2020.doc (75,428 bytes)
- instrument indenture.05.27.2020.doc (74,953 bytes)
- prescribe .05.27.20.doc (75,343 bytes)
- require_05.27.2020.doc (75,342 bytes)
- statistics,05.20.doc (75,114 bytes)
- tell,05.27.2020.doc (74,951 bytes)
- 2020-05-27-traffic-from-Valak-infection-with-IcedID.pcap.zip 5.9 MB (5,912,083 bytes)
- 2020-05-27-traffic-from-Valak-infection-with-IcedID.pcap (6,719,965 bytes)
- 2020-05-27-malware-and-artifacts-from-Valak-infection-with-IcedID.zip 2.4 MB (2,446,733 bytes)
- 2020-05-27-registry-updates-for-Valak.txt (175,180 bytes)
- ProgramData/13560864.dat (363,008 bytes)
- Users/Public/ADS-info-for-prnjobs.data.txt (976 bytes)
- Users/Public/explorer.js (4,855 bytes)
- Users/Public/prnjobs.data (1,026 bytes)
- Users/Public/prnjobs.data_258b390d.bin (396,850 bytes)
- Users/Public/prnjobs.data_84dee9df.bin (399,344 bytes)
- Users/Public/xSsGKcUqL.vA_YV (11,742 bytes)
- Users/username/AppData/Local/Temp/8c3adeff31.bin (18,944 bytes)
- Users/username/AppData/Local/Temp/~4700343.tmp (233,799 bytes)
- Users/username/AppData/Local/Temp/~5058796.tmp (233,799 bytes)
- Users/username/AppData/Local/Temp/~5155078.exe (229,376 bytes)
- Users/username/AppData/Local/{B1B5AC6F-3E78-1E5A-0252-DA0653AF3E6B}/{85448282-01B8-C8D4-4900-1A4C2079DDA7}/buuzac.png (667,077 bytes)
- Users/username/AppData/Roaming/df.dll (409,600 bytes)
- Users/username/AppData/Roaming/ilat/username/Zisifu2.exe (229,376 bytes)
IMAGES
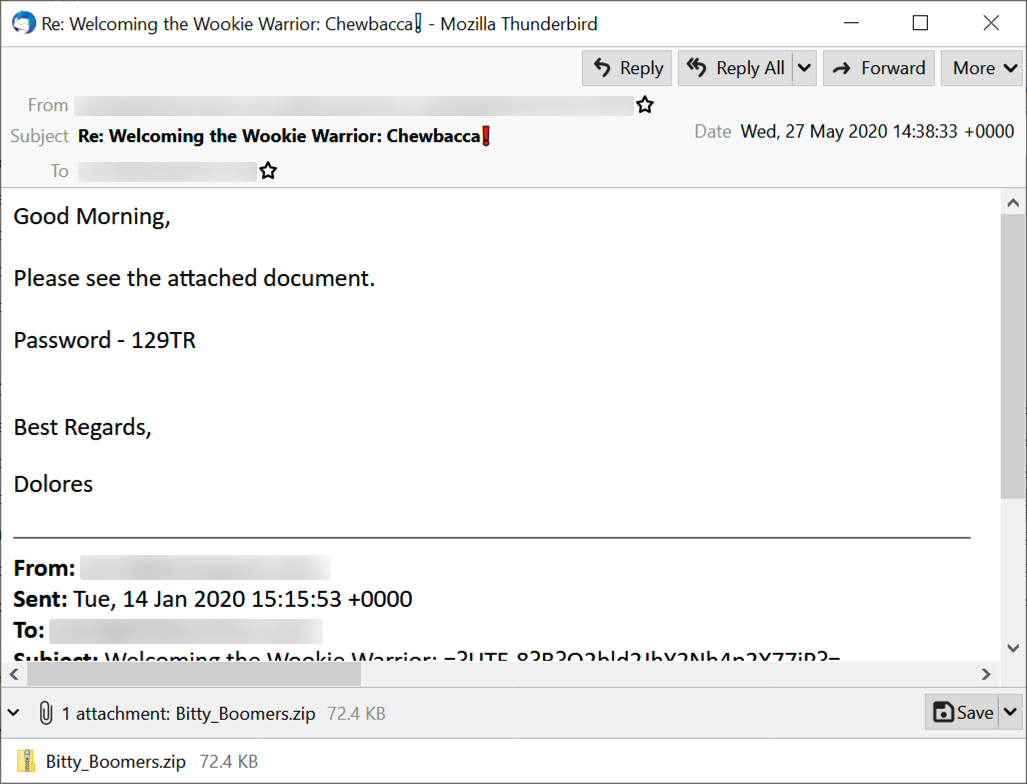
Shown above: Screenshot from a malspam messages, example 1 of 2.
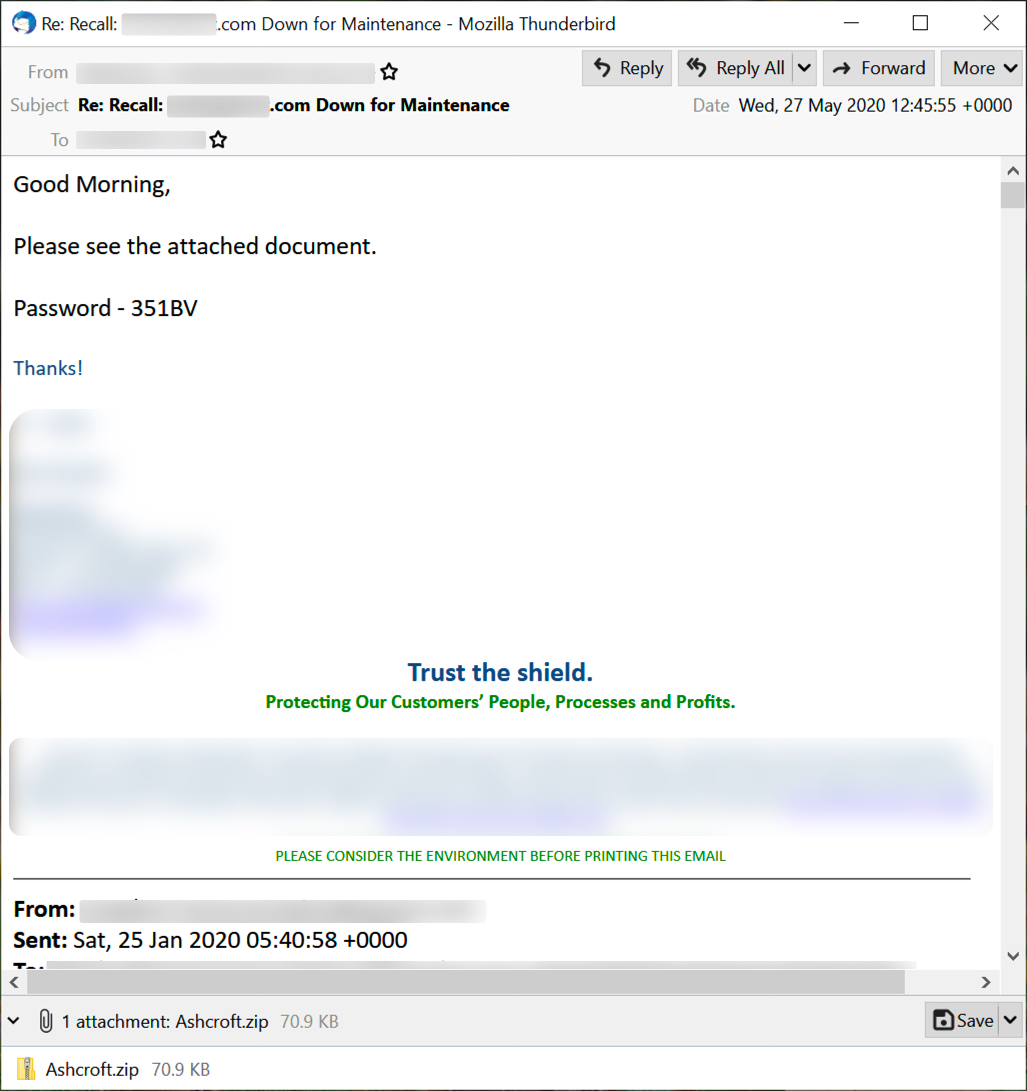
Shown above: Screenshot from a malspam messages, example 2 of 2.
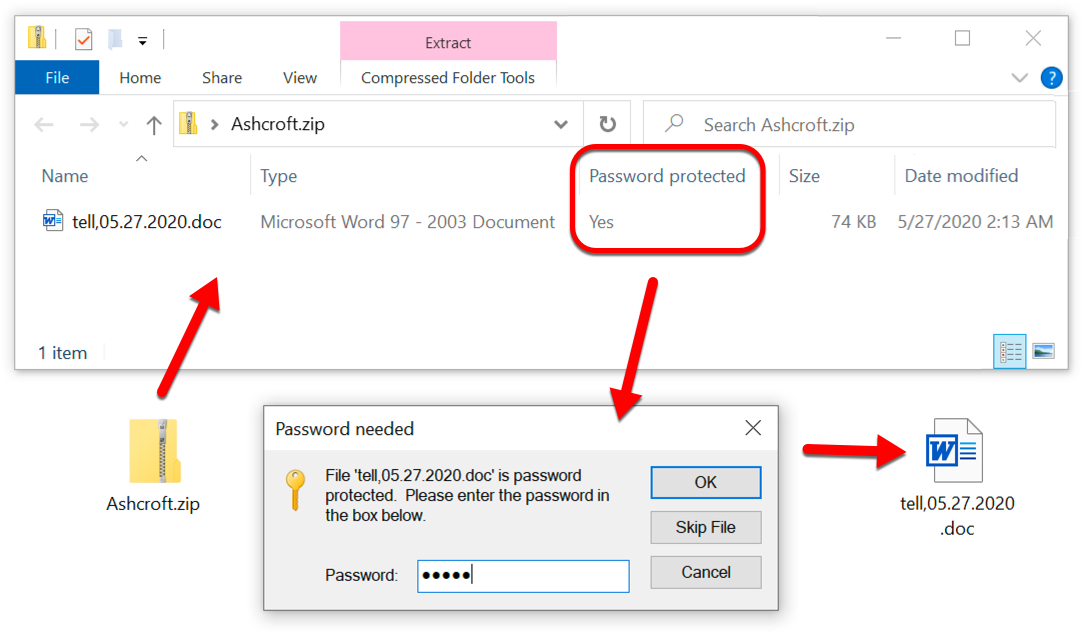
Shown above: Extacting a Word doc from one of the password-protected zip attachments.
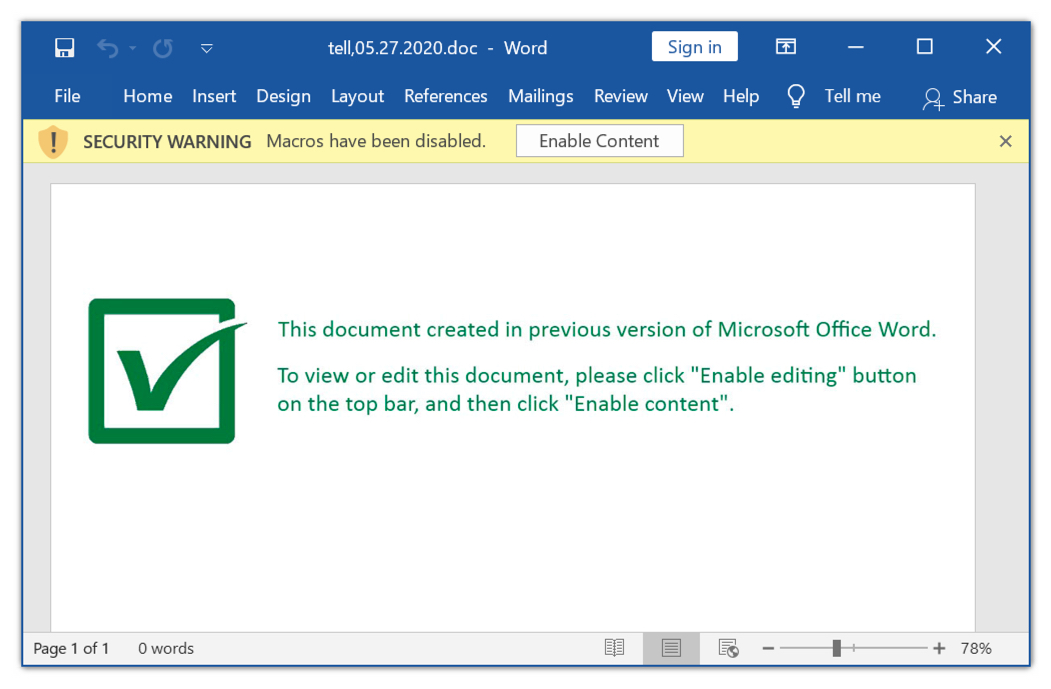
Shown above: Screenshot of the extracted Word doc.
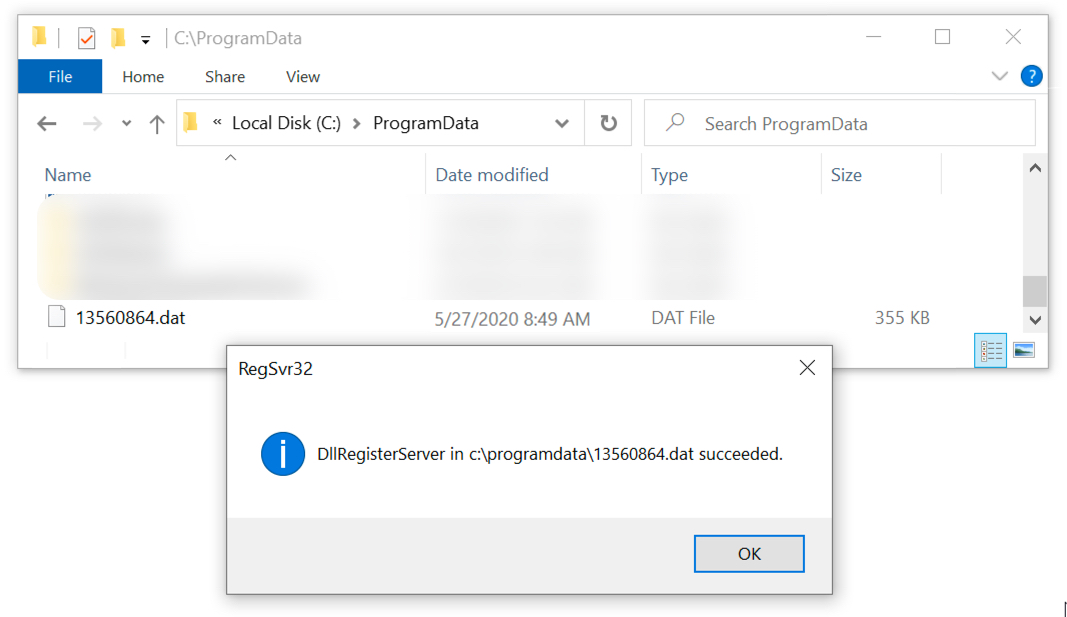
Shown above: Initial Valak DLL after enabling macros on the Word doc.
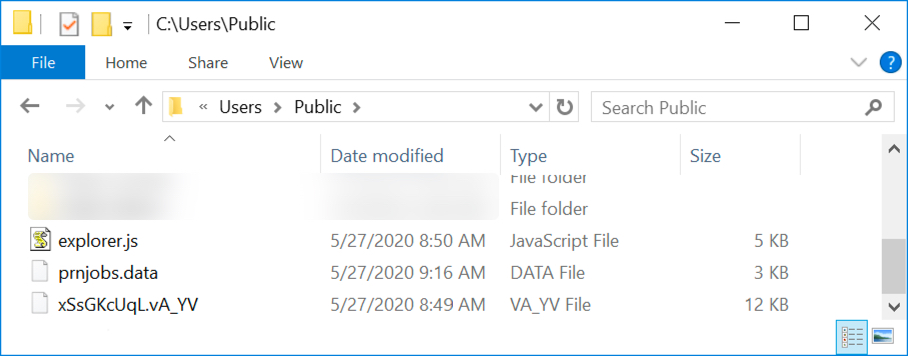
Shown above: Files in the Public user directory created by Valak.
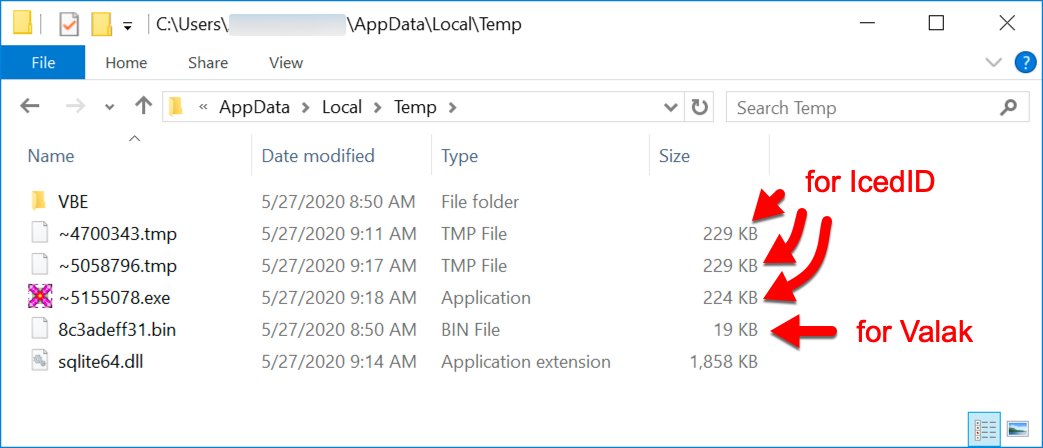
Shown above: Files in the infected user's AppData\Local\Temp directory for Valak and IcedID.
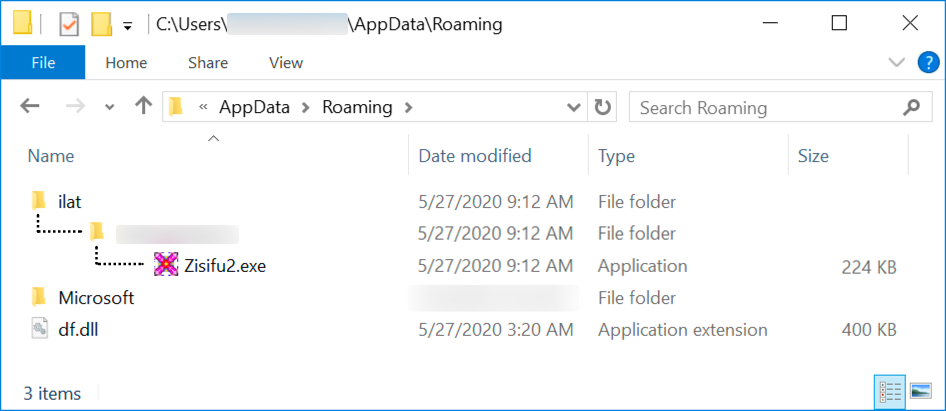
Shown above: IcedID persistent on the infected Windows host, and another DLL (don't know what that one's for).
Shown above: Image file with embedded/encoded data related to the IcedID infection.
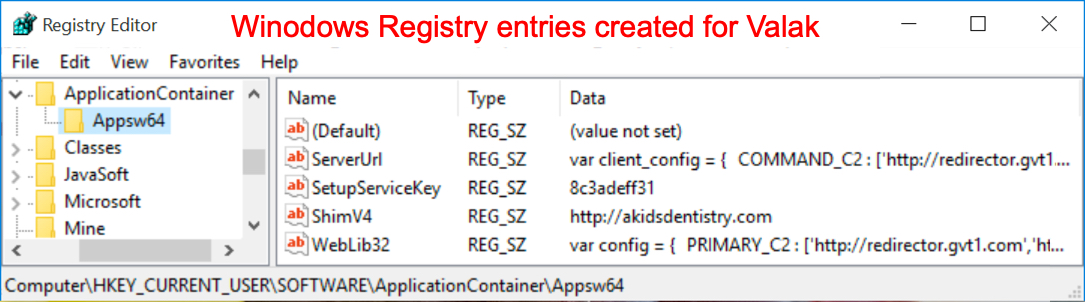
Shown above: Registry updates to help keep the Valak infection persistent.
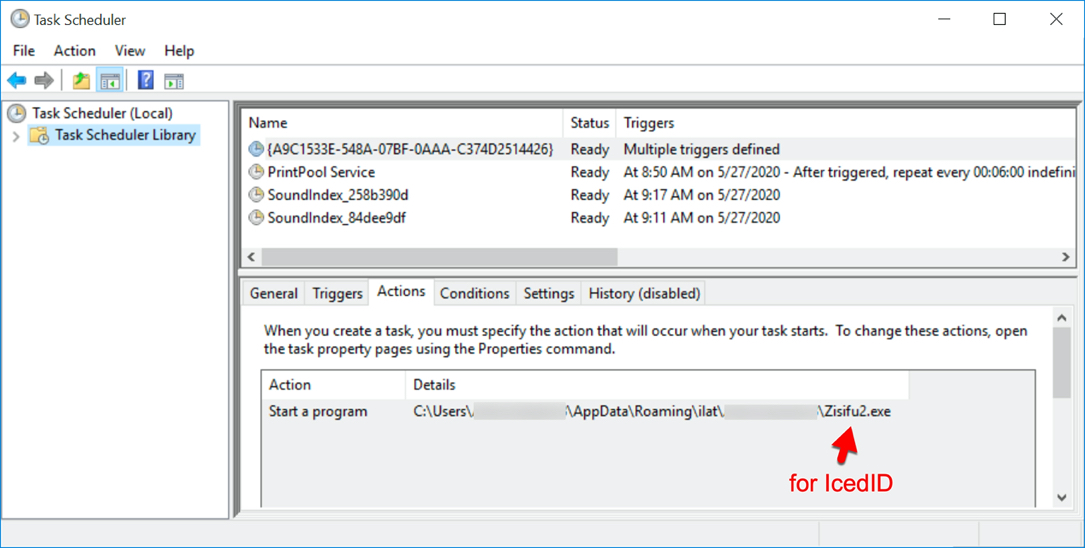
Shown above: Scheduled task to keep IcedID persistent.
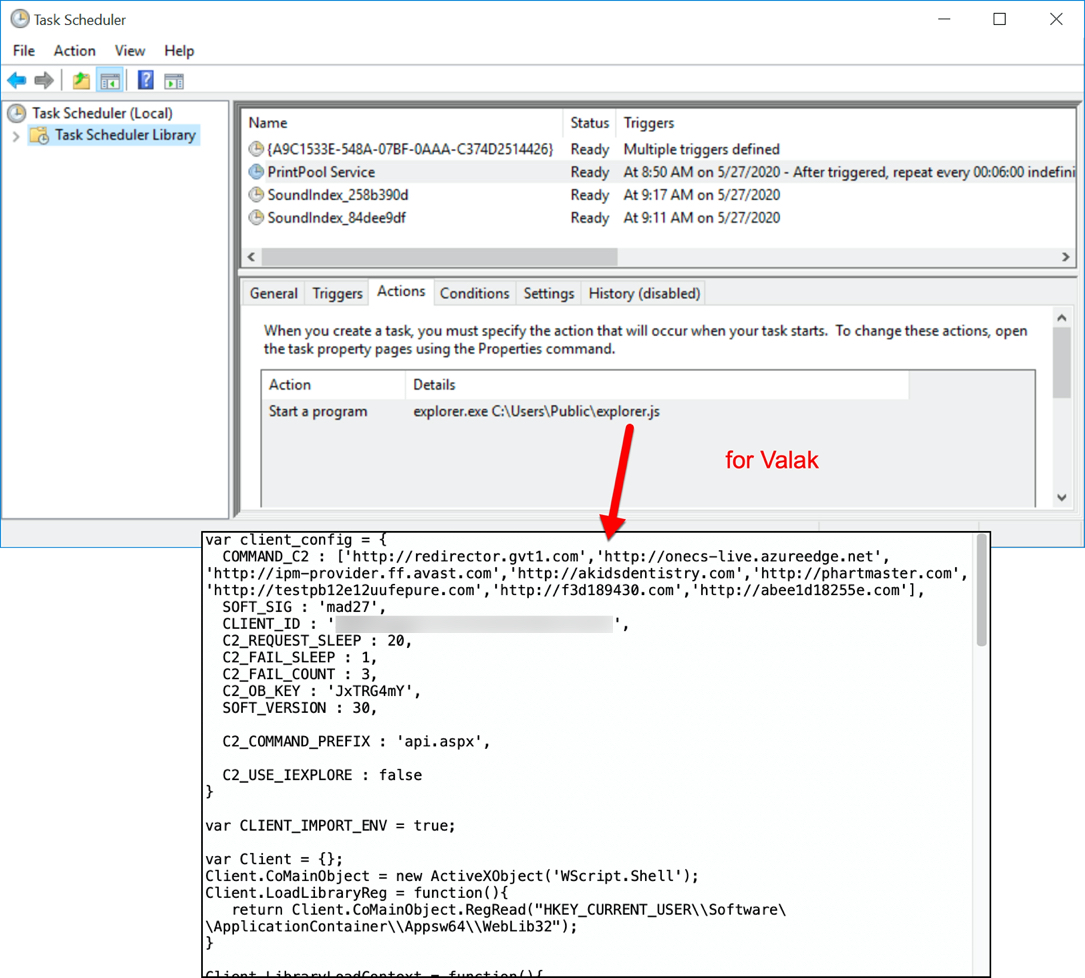
Shown above: Scheduled task to keep Valak persistent.
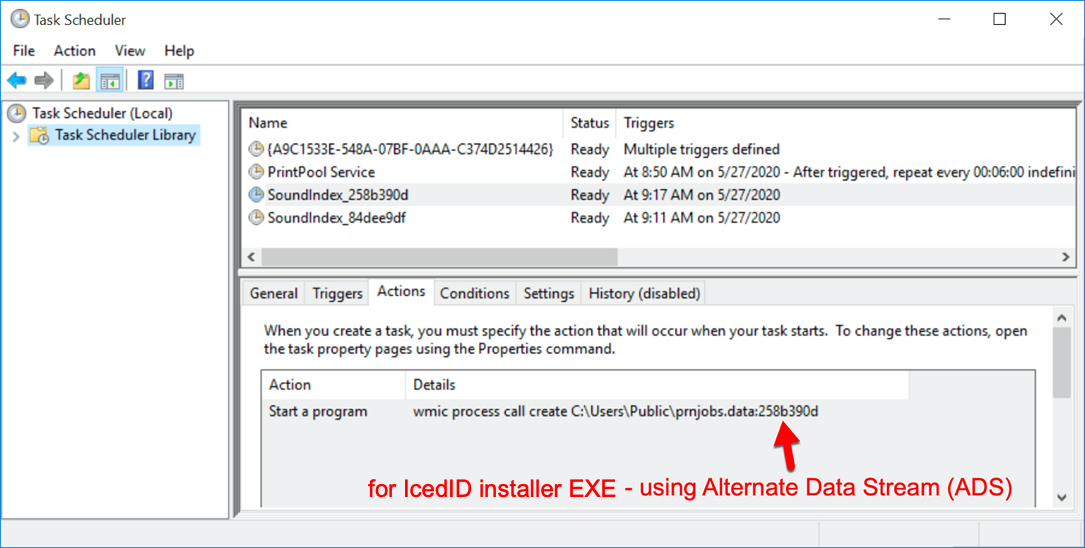
Shown above: Scheduled task to run follow-up malware, where we see Alternate Data Stream (ADS) used to hide an EXE installer for IcedID.
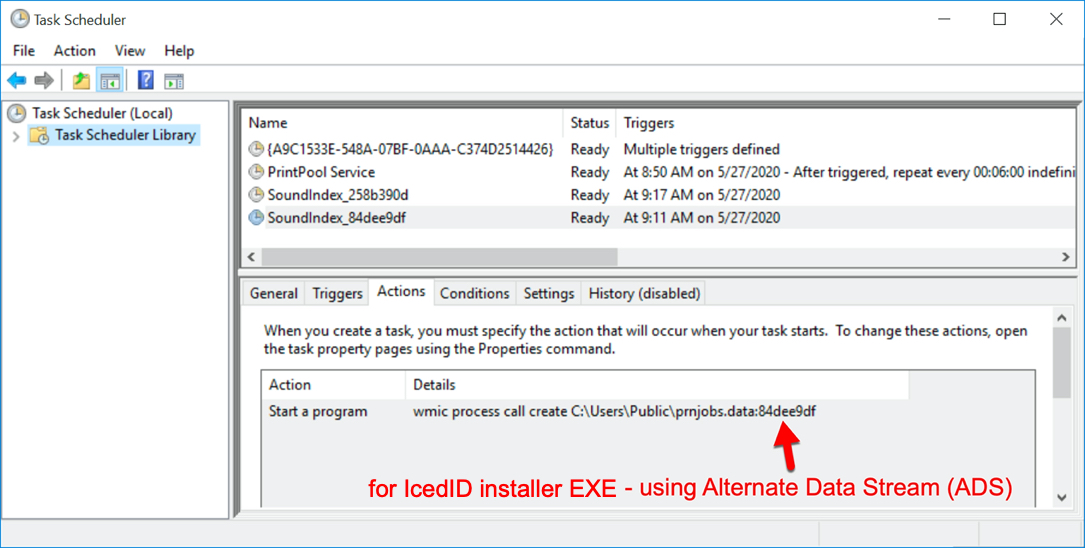
Shown above: Scheduled task to run another follow-up malware item, where an Alternate Data Stream (ADS) is used to hide another EXE installer for IcedID.
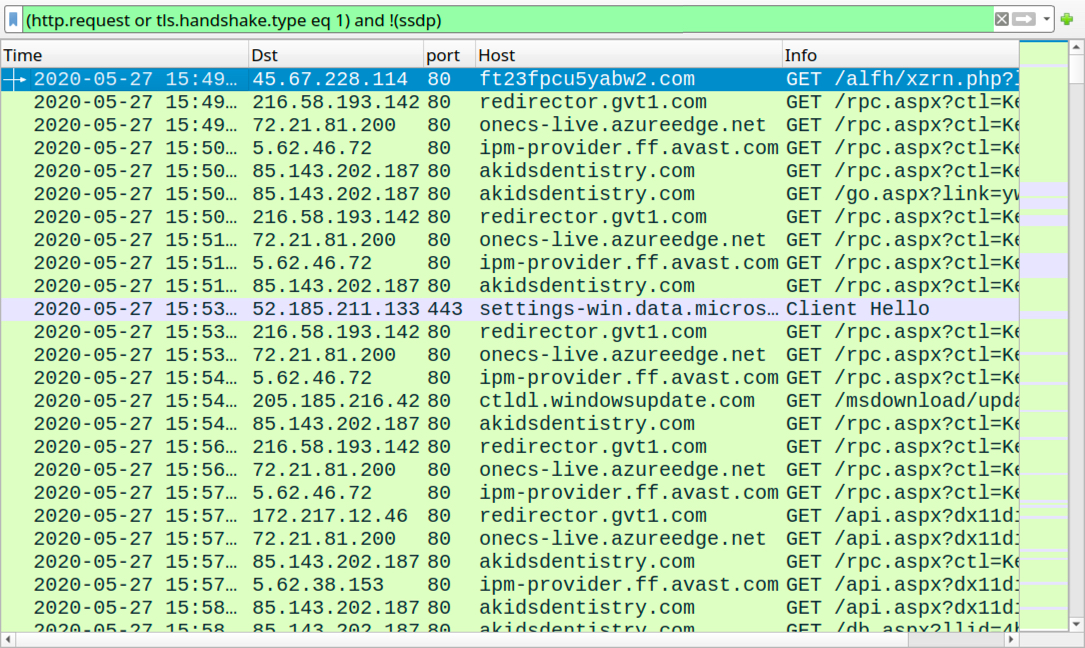
Shown above: Traffic from the start of the Valak infection filtered in Wireshark.
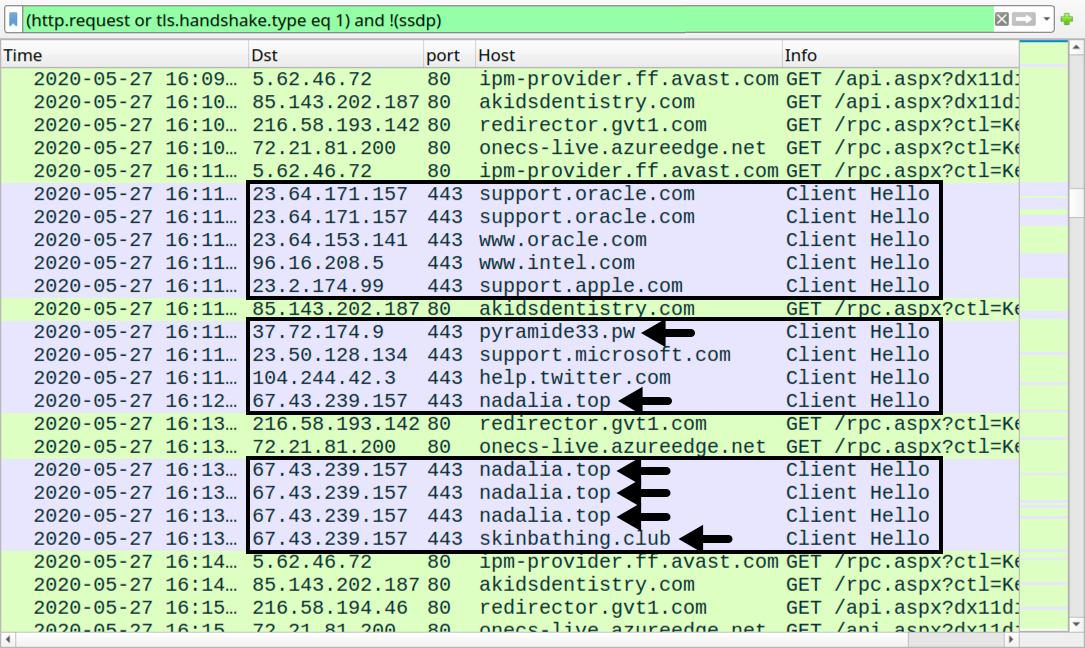
Shown above: Later traffic showing where the infected host picks up IcedID, with arrows highlighting the IcedID domains.
Click here to return to the main page.
