2020-06-03 - VALAK (SOFT_SIG: MAD29) INFECTION WITH ICEDID (BOKBOT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-06-03-Valak-and-IcedID-IOCs.txt.zip 2.1 kB (2,149 bytes)
- 2020-06-03-Valak-and-IcedID-IOCs.txt (4,781 bytes)
- 2020-06-03-example-of-malpsam-with-attachment-for-Valak.eml.zip 139 kB (139,129 bytes)
- 2020-06-03-example-of-malpsam-with-attachment-for-Valak.eml (190,718 bytes)
- 2020-06-03-Valak-infection-with-IcedID.pcap.zip 6.2 MB (6,208,090 bytes)
- 2020-06-03-Valak-infection-with-IcedID.pcap (6,781,957 bytes)
- 2020-06-03-some-malware-and-artifacts-for-Valak-and-IcedID.zip 3.1 MB (3,083,326 bytes)
- 2020-06-03-Word-doc-with-macro-for-Valak.bin (121,111 bytes)
- 2020-06-03-registry-updates-for-Valak.txt (111,574 bytes)
- 2020-06-03-zip-attachment-from-malspam-password-264RS.zip (125,149 bytes)
- ProgramData/28215025.dat (311,808 bytes)
- Users/Public/iVIwVADQD.eLxan (11,782 bytes)
- Users/Public/diskdiag.ini_ADS_info_a1fc7c5c.txt ( bytes)
- Users/Public/Disk0.js (4,858 bytes)
- Users/Public/diskdiag.ini (2,054 bytes)
- Users/Public/diskdiag.ini_a1fc7c5c.bin (3,871,232 bytes)
- Users/username/AppData/Local/Temp/~6476288.tmp (227,655 bytes)
- Users/username/AppData/Local/Temp/79e5036f32.bin (25,600 bytes)
- Users/username/AppData/Roaming/{1C66F8E1-7670-7926-3C20-88F29C49A372}/anokko.exe (223,232 bytes)
- Users/username/AppData/Roaming/username/gozeac.png (667,077 bytes)
IMAGES
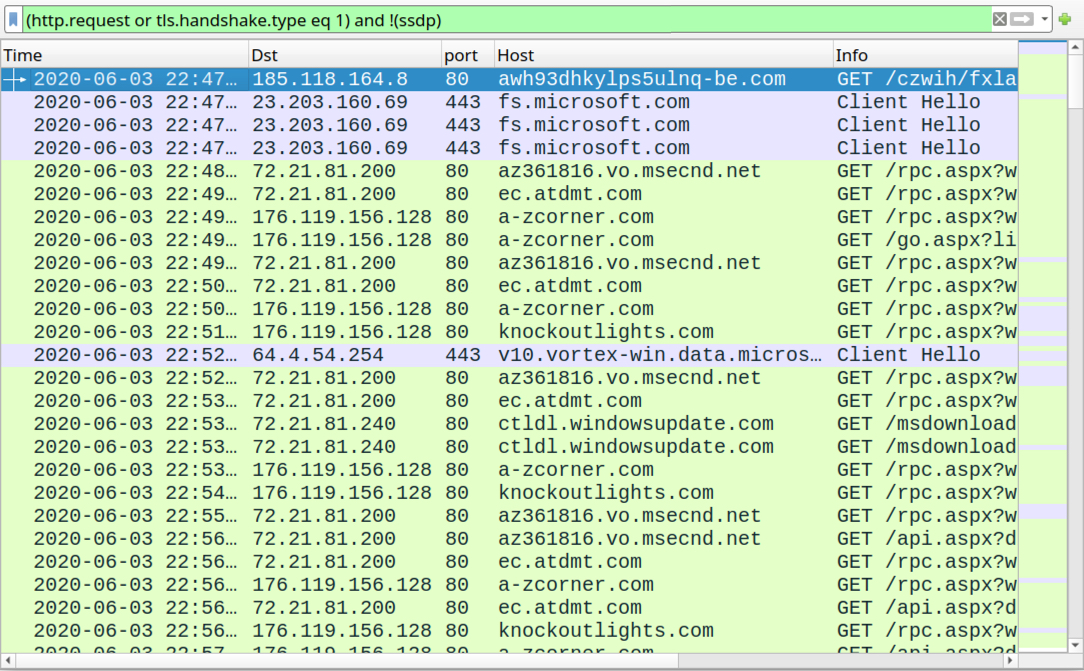
Shown above: Traffic from the beginning of an infection filtered in Wireshark.
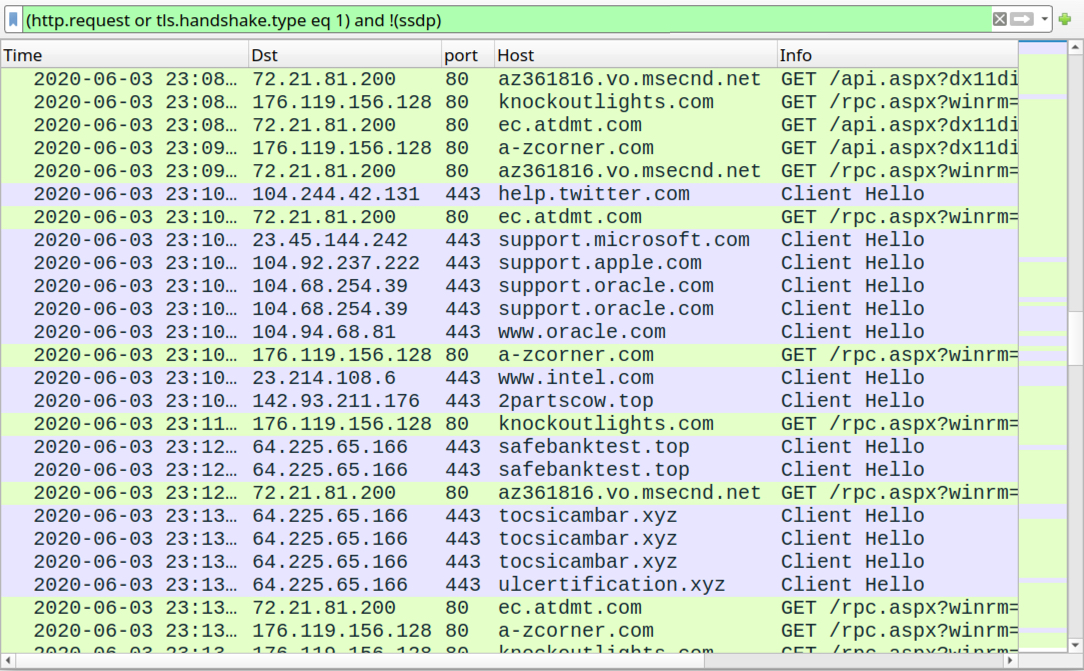
Shown above: Traffic from later during the infection, where we see indicators of IcedID.
Click here to return to the main page.
