2020-06-10 - QUICK POST: TRICKBOT GTAG GI6 INFECTION IN AD ENVIRONMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-06-10-Trickbot-gtag-gi6-infection-traffic.pcap.zip 12.8 MB (12,840,706 bytes)
- 2020-06-10-Trickbot-gtag-gi6-malware-and-artifacts.zip 12.2 MB (12,203,567 bytes)
NOTES:
- This Trickbot infection happened in an Active Directory (AD) environment with a Domain Controller (DC).
- The infected Win7 client is at 10.6.10[.]197 (CINCINATTI-PC) and the DC is at 10.6.10[.]6 (2THUMBSUP-DC).
- The DC was infected through Trickbot's "nworm" module.
- For some background on nworm, see: Goodbye Mworm, Hello Nworm: TrickBot Updates Propagation Module.
- Click on any of the below images for a higher-resolution view of the image.
- This was originally reported by @abuse_ch as part of a malspam campaign using Black Lives Matter-themed emails to push Trickbot (link to tweet).
IMAGES
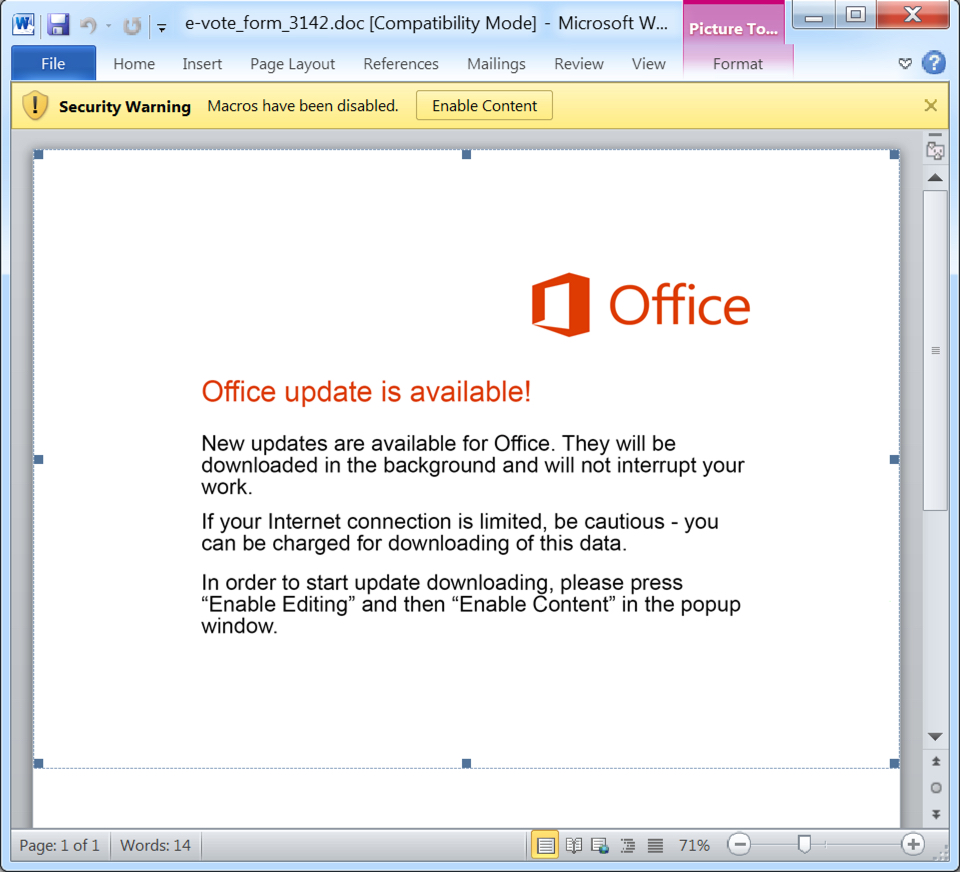
Shown above: Screenshot of the Word doc used to generate this infection traffic.
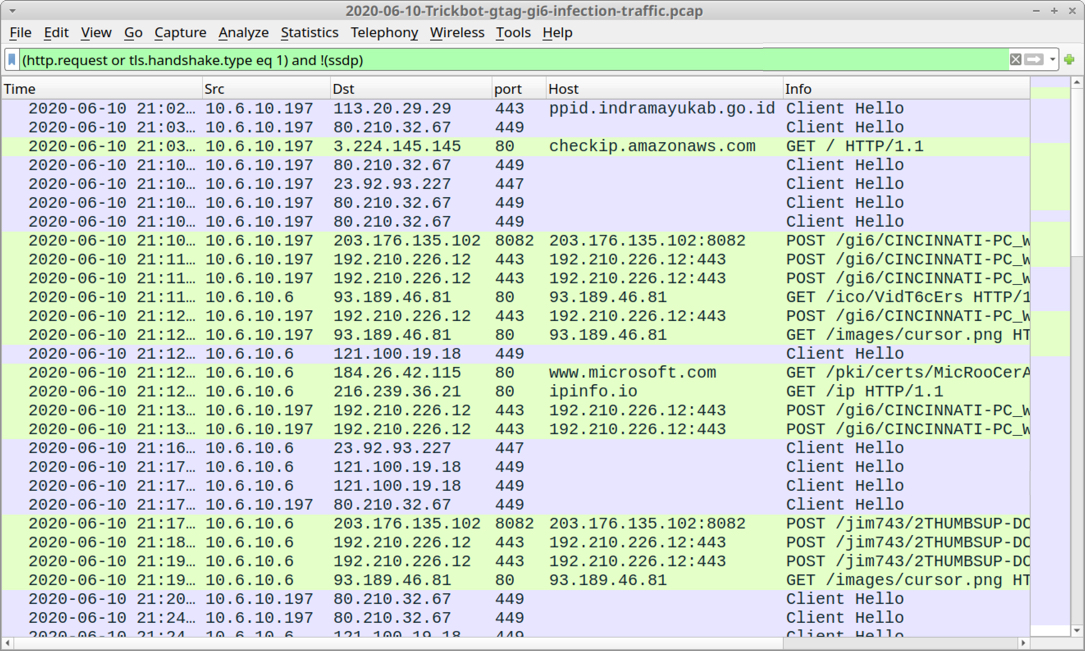
Shown above: Traffic from the infection filtered in Wireshark.
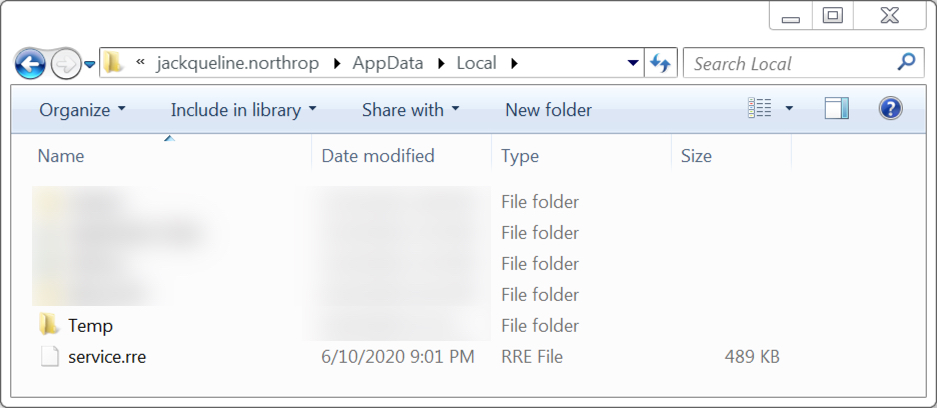
Shown above: Initial location of the Trickbot DLL downloaded over HTTPS after enabling Word macros.
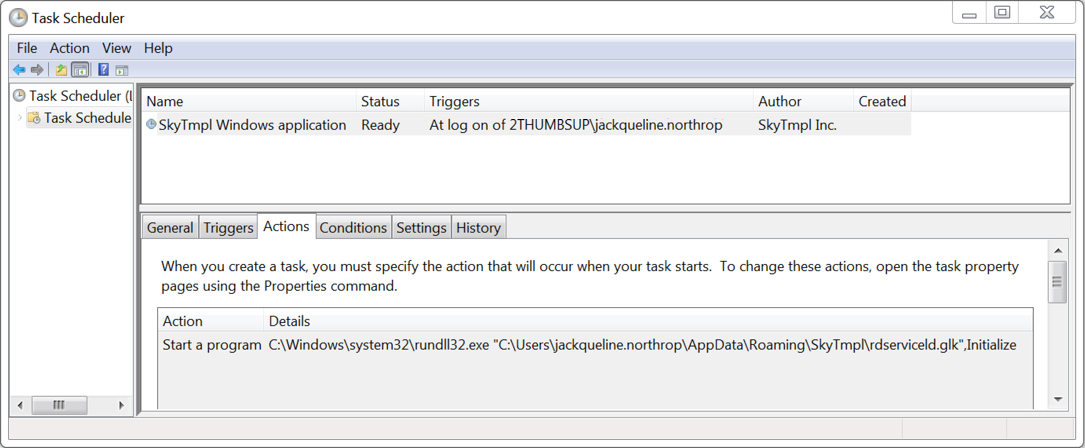
Shown above: Scheduled task to keep the Trickbot infection persistent.
Shown above: Directory with the persistent Trickbot DLL.

Shown above: Trickbot modules on the infected Win7 host.
Click here to return to the main page.
