2020-06-10 - URSNIF (GOZI/IFSB) INFECTION WITH URSNIF VARIANT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-06-10-Ursnif-with-Ursnif-IOCs.txt.zip 4.2 kB (4,225 bytes)
- 2020-06-10-Ursnif-with-Ursnif-IOCs.txt (7,519 bytes)
- 2020-06-10-Ursnif-with-Ursnif-infection-traffic.pcap.zip 4.8 MB (4,835,563 bytes)
- 2020-06-10-Ursnif-with-Ursnif-infection-traffic.pcap (5,419,771 bytes)
- 2020-06-10-Ursnif-with-Ursnif-malware-and-artifacts-from-infected-host.zip 5.9 MB (5,923,882 bytes)
- 2020-06-10-additional-registry-updates-after-followup-Ursnif.txt (5,615,006 bytes)
- 2020-06-10-initial-registry-updates-Ursnif.txt (5,614,256 bytes)
- 40958169.dat (258,048 bytes)
- 93296.exe (4,268,544 bytes)
- rule-06.20.doc (118,766 bytes)
IMAGES
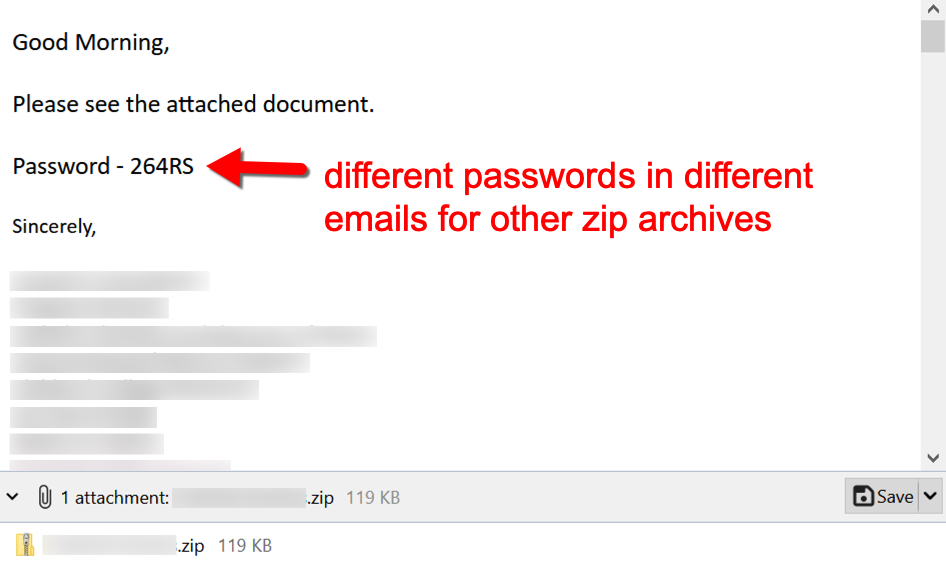
Shown above: Malspam from this campaign spoofs legitimate email chains.
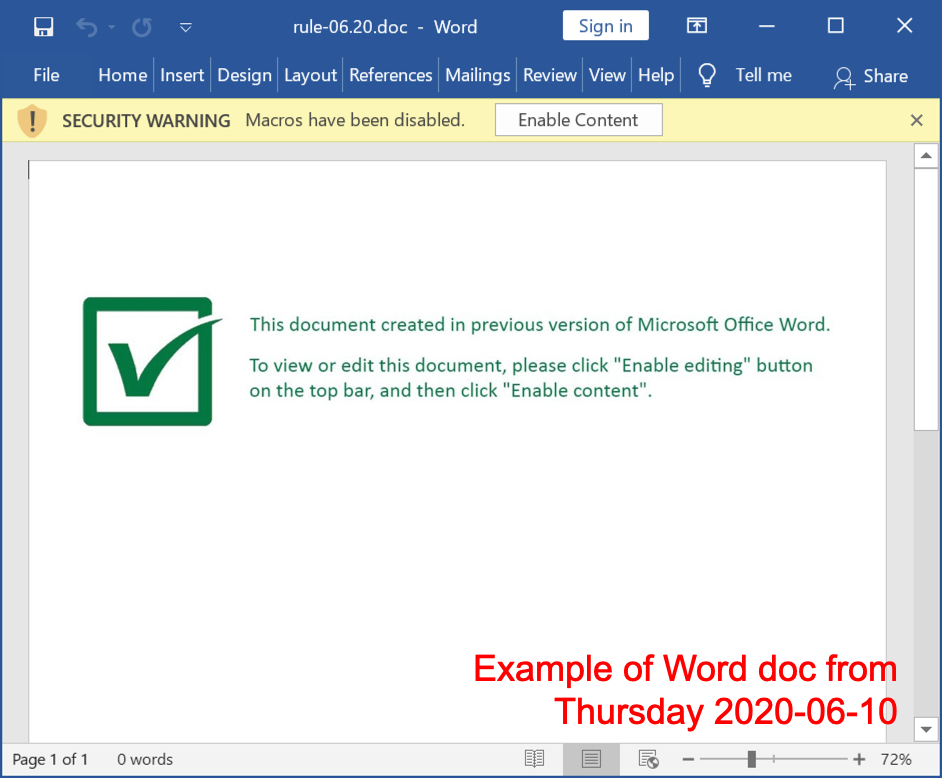
Shown above: Screenshot of a Word doc extracted from one of the password-protected zip archive first seen on 2020-06-10.
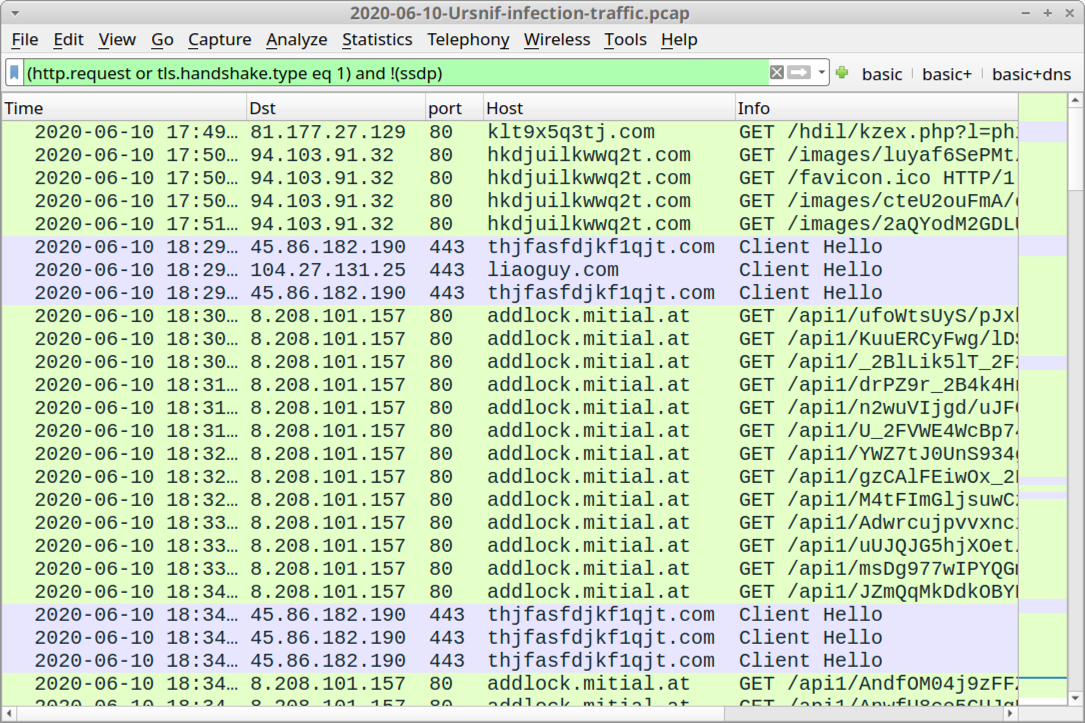
Shown above: Traffic from an infection filtered in Wireshark.
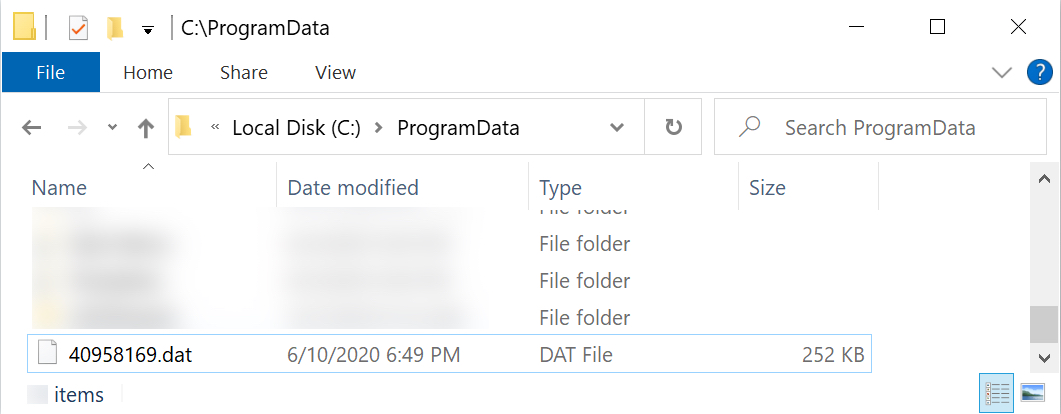
Shown above: Initial malware, a DLL for Ursnif (Gozi/IFSB).
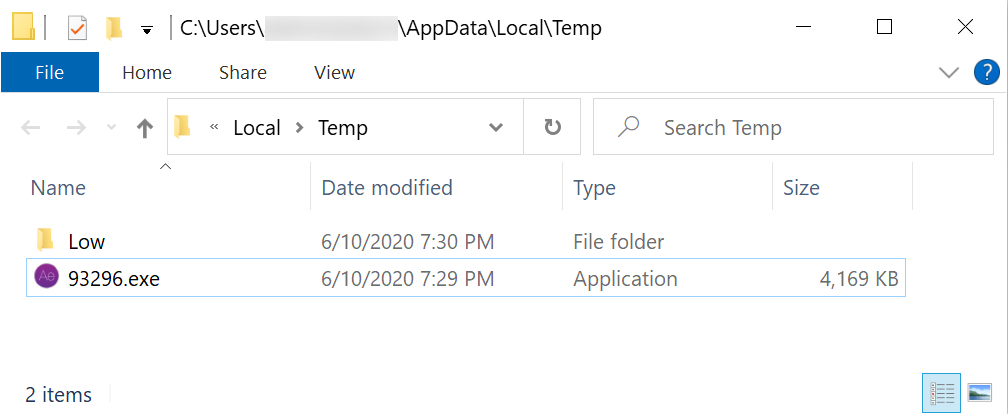
Shown above: Follow-up malware, an EXE for an Ursnif variant.
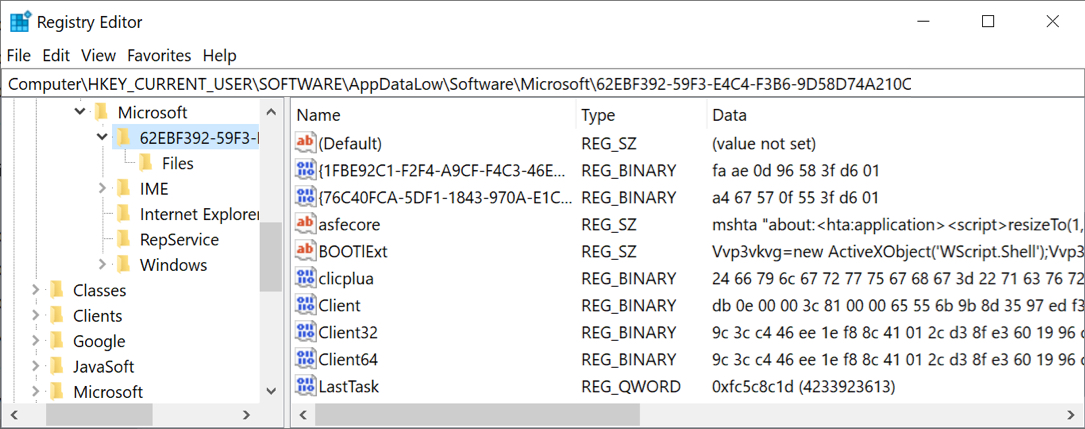
Shown above: Registry updates caused by both Ursnif malwares.
Click here to return to the main page.
