2020-06-12 - QAKBOT (QBOT) SPX139 INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-06-12-IOCs-for-Qakbot-spx139-with-ZLoader.txt.zip 1.6 kB (1,591 bytes)
- 2020-06-12-Qakbot-spx139-with-ZLoader-infection-traffic.pcap.zip 17.4 MB (17,362,131 bytes)
- 2020-06-12-malware-and-artifacts-for-Qakbot-spx139-with-ZLoader.zip 9.4 MB (9,373,822 bytes)
IMAGES
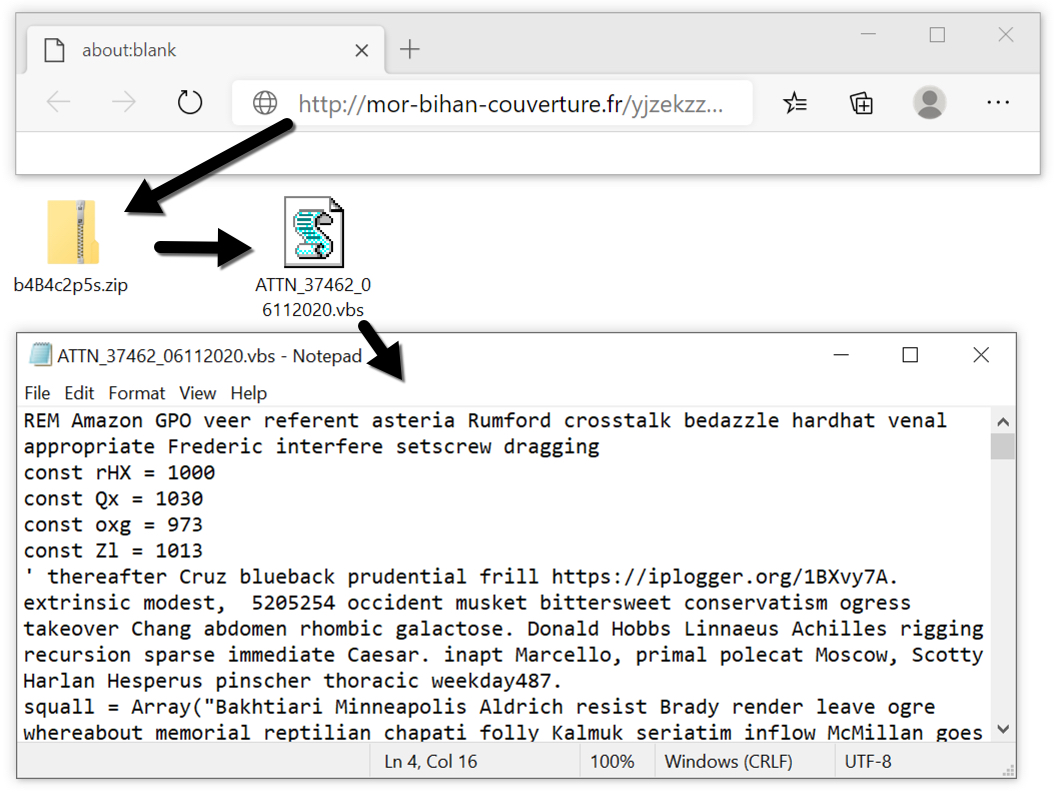
Shown above: Downloading the zip archive from a link in the malspam, and extacting the VBS file.
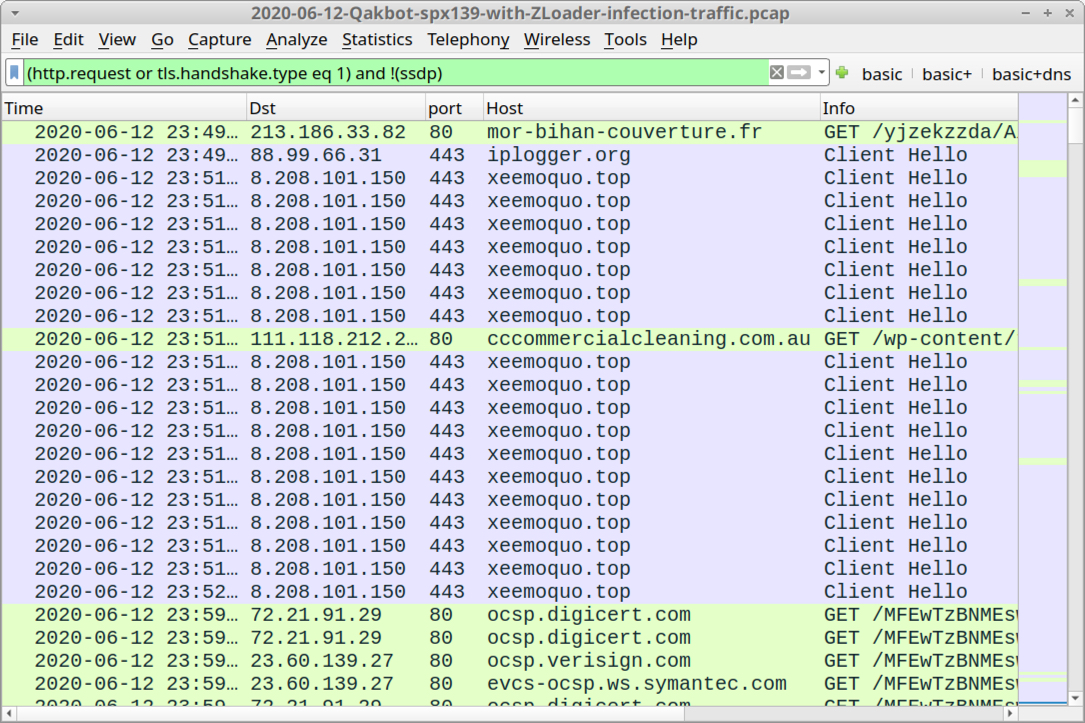
Shown above: Traffic from the infection filtered in Wireshark.
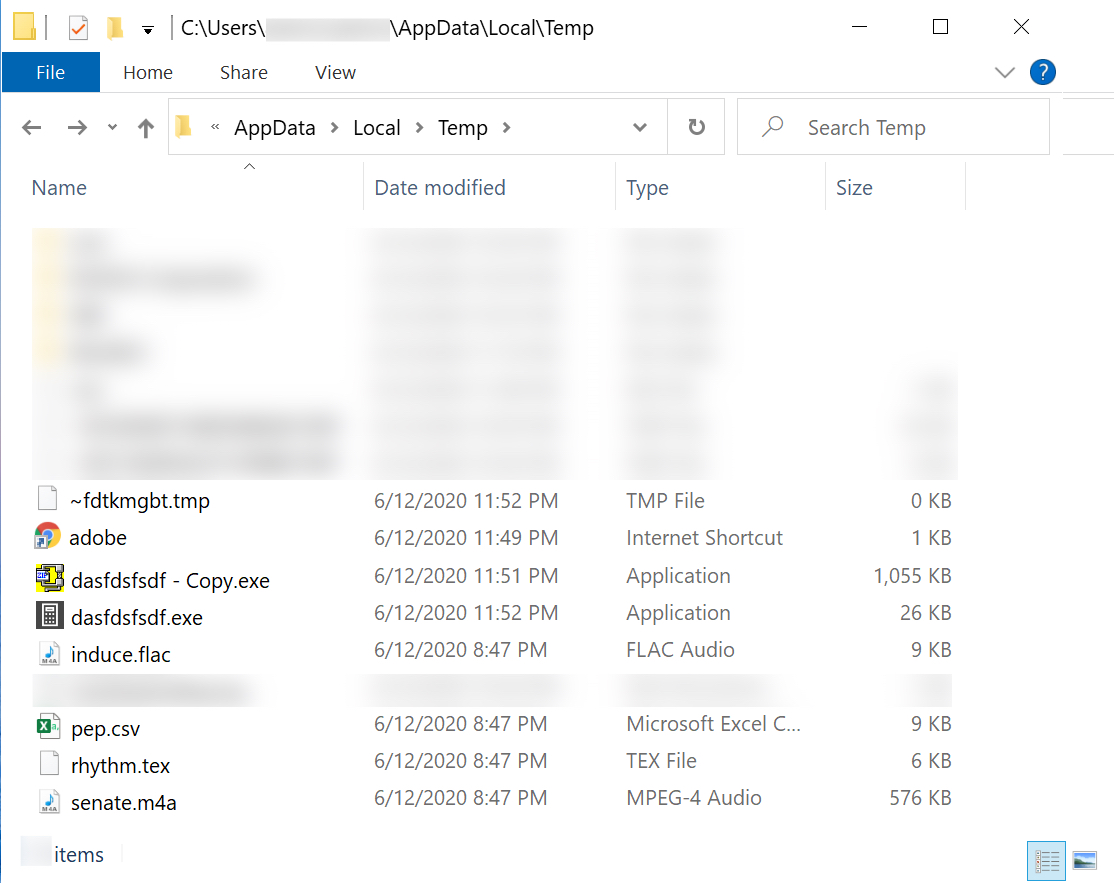
Shown above: Files in the AppData\Local\Temp folder seen during this infection.
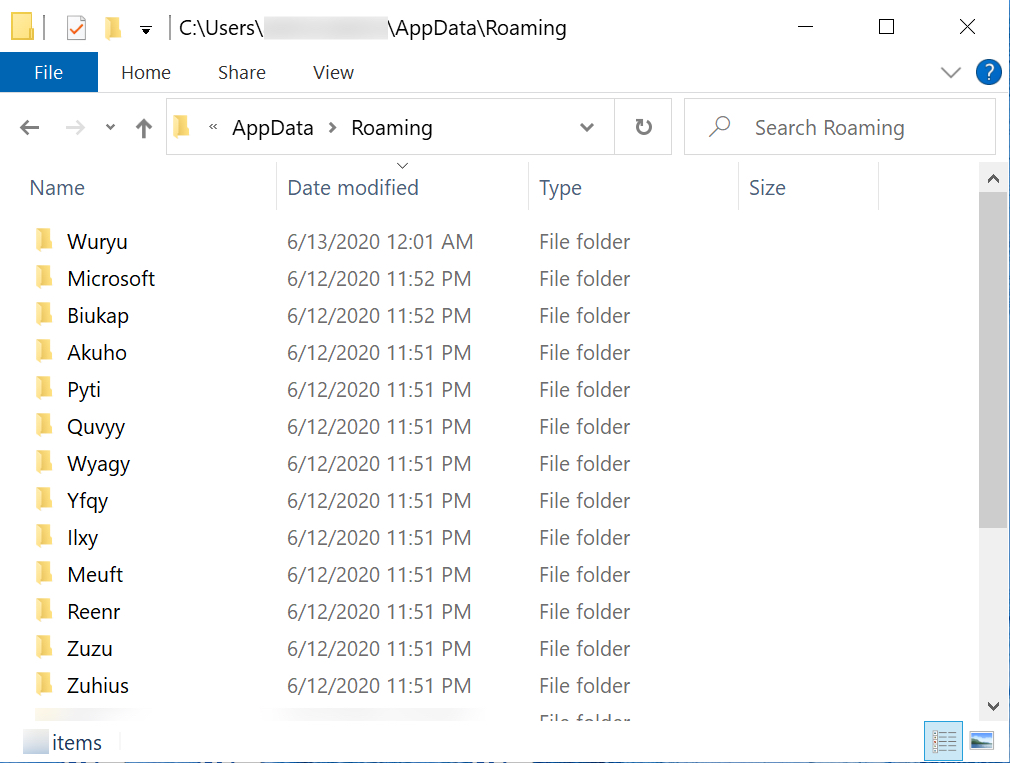
Shown above: Some of the decoy directories created by ZLoader.
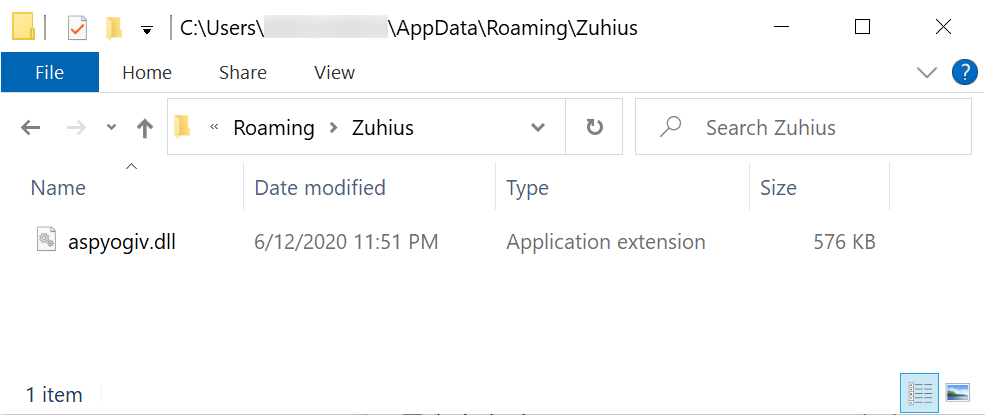
Shown above: Final location of ZLoader on the infected Windows host.
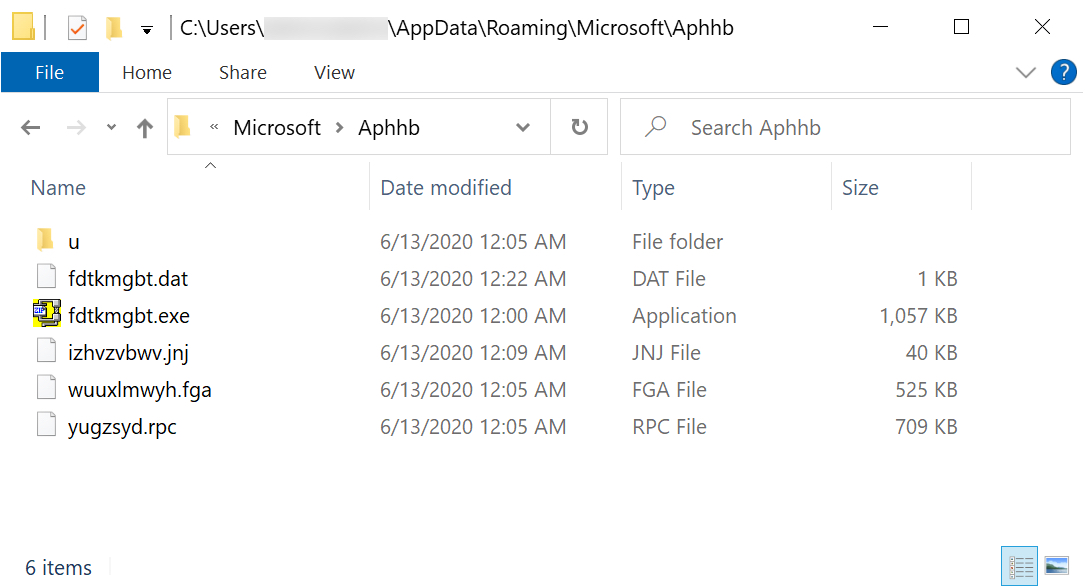
Shown above: Qakbot persistent on the infected Windows host.
Click here to return to the main page.
