2020-11-06 - POSSIBLE AGENT TESLA (AGENTTESLA)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES
- 2020-11-06-IOCs-for-possible-Agent-Tesla.txt.zip 1.2 kB (1,201 bytes)
- 2020-11-06-malspam-pushing-possible-AgentTesla.eml.zip 432 kB (432,305 bytes)
- 2020-11-06-possible-Agent-Tesla-traffic.pcap.zip 664 kB (664,266 bytes)
- 2020-11-06-possible-Agent-Tesla-malware-and-artifacts.zip 1.7 MB (1,694,046 bytes)
NOTES:
- This one would not run on a VM, so I had to use a physical host.
- This looks like Agent Tesla (AgentTesla), but the format for emails exfiltrating stolen victim data looks a little different than previous Agent Tesla samples I've investigated.
IMAGES
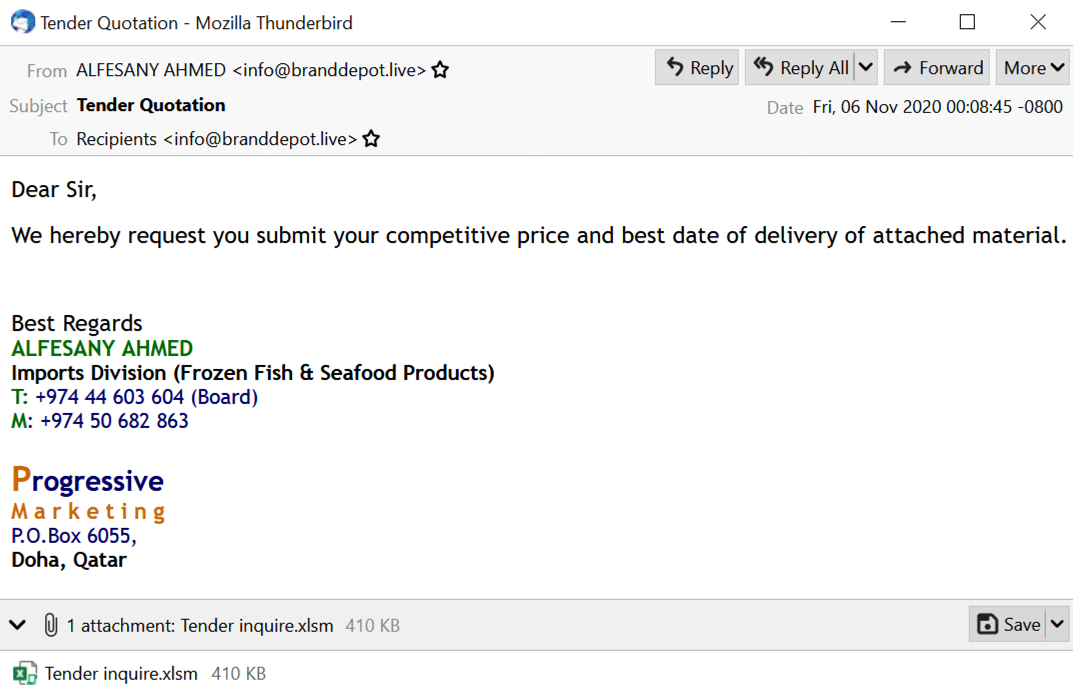
Shown above: Screen shot of malspam pushing possible Agent Tesla.

Shown above: Screen shot of attached spreadsheet with macro for the malware.
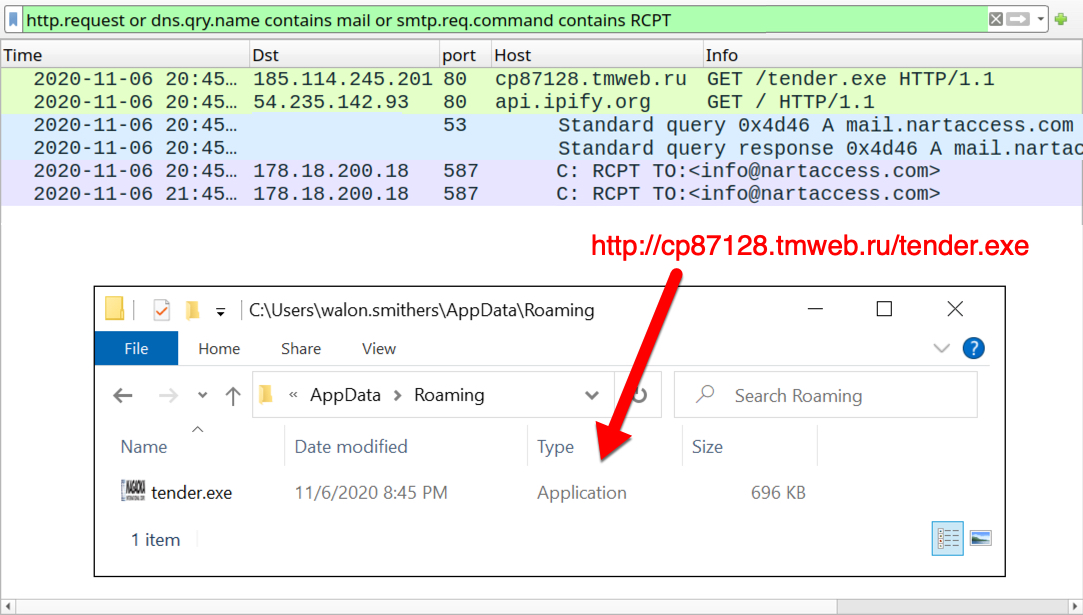
Shown above: Traffic from the infection filtered in Wireshark, and the initial malware EXE saved to my infected lab host.
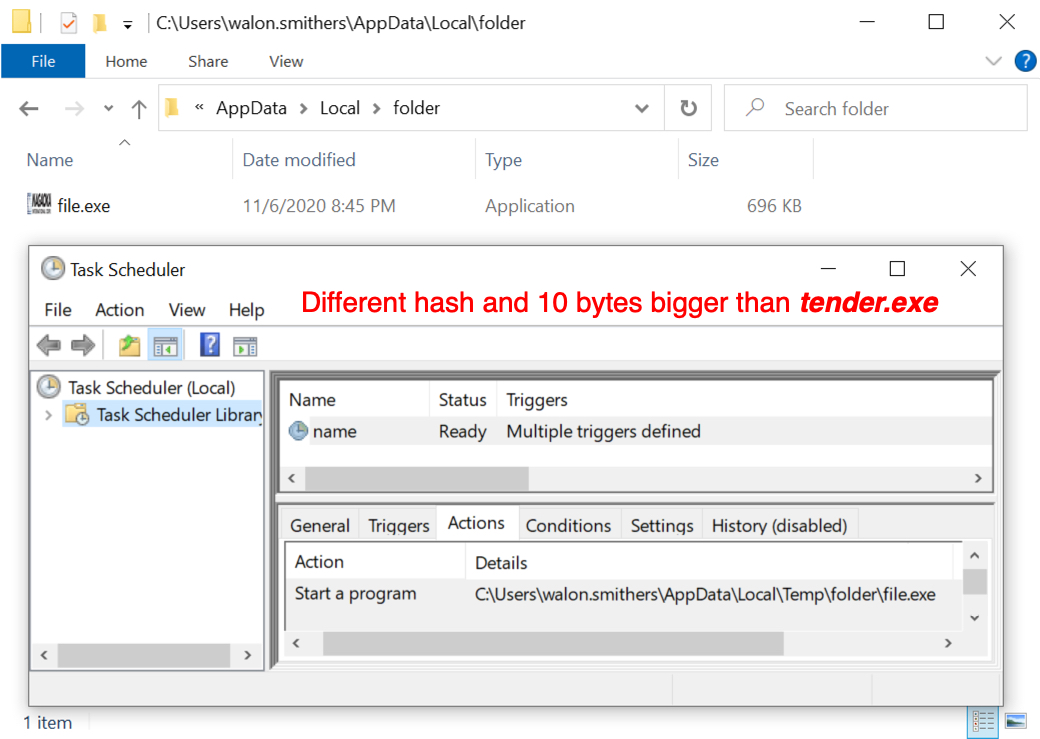
Shown above: Malware persistent on my infected lab host.
Click here to return to the main page.
