2021-02-05 (FRIDAY) - SPELEVO EXPLOIT KIT (EK) SENDS SHARIK/SMOKELOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-02-05-IOCs-for-Spelevo-EK-sending-SmokeLoader.txt.zip 1.0 kB (966 bytes)
- 2021-02-05-IOCs-for-Spelevo-EK-sending-SmokeLoader.txt (1,562 bytes)
- 2021-02-05-Spelevo-EK-sends-SmokeLoader.pcap.zip 397 kB (397,132 bytes)
- 2021-02-05-Spelevo-EK-sends-SmokeLoader.pcap (521,458 bytes)
- 2021-02-05-Spelevo-EK-and-SmokeLoader-malware-and-artifacts.zip 119 kB (119,183 bytes)
- 2021-02-05-scheduled-task-for-for-SmokeLoader.txt (3,602 bytes)
- 2021-02-05-Spelevo-EK-Flash-exploit.swf.bin (22,035 bytes)
- 2021-02-05-Spelevo-EK-landing-page.txt (39,735 bytes)
- 2021-02-05-Spelevo-EK-payload-SmokeLoader-EXE.bin (104,960 bytes)
- 2021-02-05-Spelevo-EK-second-HTML-page.txt (1,908 bytes)
IMAGES
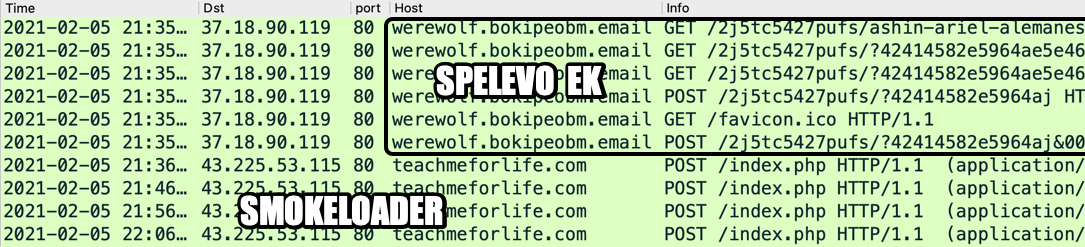
Shown above: Traffic from the infection filtered in Wireshark.
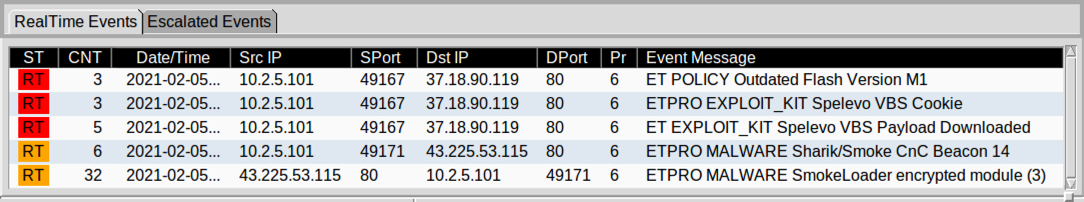
Shown above: Alerts from the infection from Security Onion 16.04 using Squil with Sucirata and the ETPRO ruleset.

Shown above: Sharik/SmokeLoader post-infection traffic.
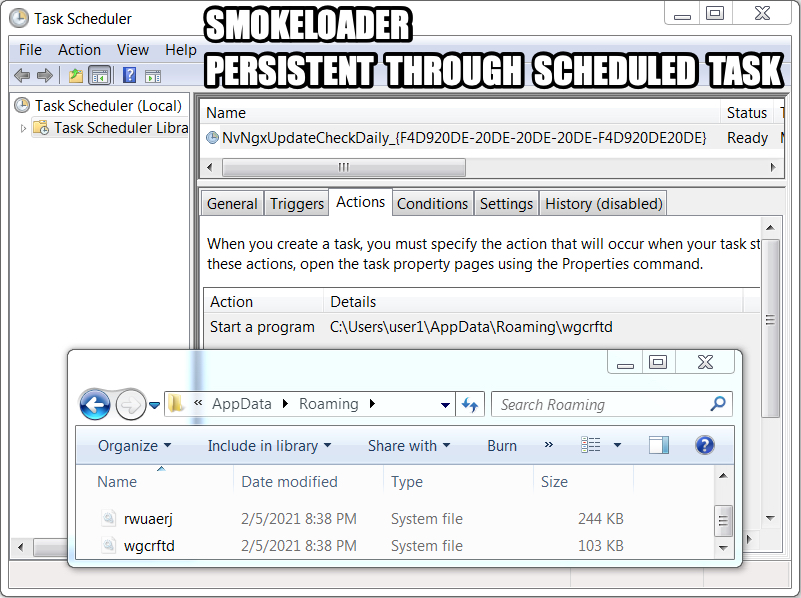
Shown above: Sharik/SmokeLoader persistent on an infected Windows 7 host.
Click here to return to the main page.
