2021-02-22 (MONDAY) - ICEDID (BOKBOT) FROM SAME TYPE OF URL THAT NORMALLY DELIVERS QAKBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-02-22-IOCs-for-IcedID-infection.txt.zip 1.6 kB (1,598 bytes)
- 2021-02-22-IOCs-for-IcedID-infection.txt (2,651 bytes)
- 2021-02-22-IcedID-infection-traffic.pcap.zip 8.8 kB (8,837,406 bytes)
- 2021-02-22-IcedID-infection-traffic.pcap (9,336,185 bytes)
- 2021-02-22-malware-and-artifacts-from-IcedID-infection.zip 8.8 MB (8,767,877 bytes)
- 2021-02-22-scheduled-task-for-IcedID.txt (3,914 bytes)
- document-550193913.xls (93,696 bytes)
- user1/rieuro.vnt (3,115,520 bytes)
- user1/local/Temp/directx32.tmp (3,110,400 bytes)
- user1/local/{3EBBD96D-9EB0-D370-8F85-A89B5E4EBD7E}/zilifc64.dll (3,110,400 bytes)
- user1/Roaming/PlayTravel/license.dat (340,874 bytes)
NOTE:
- HTTPS URL generated by the Excel macro ends with /ds/2202.gif which normally would deliver Qakbot, but today it delivered IcedID.
IMAGES

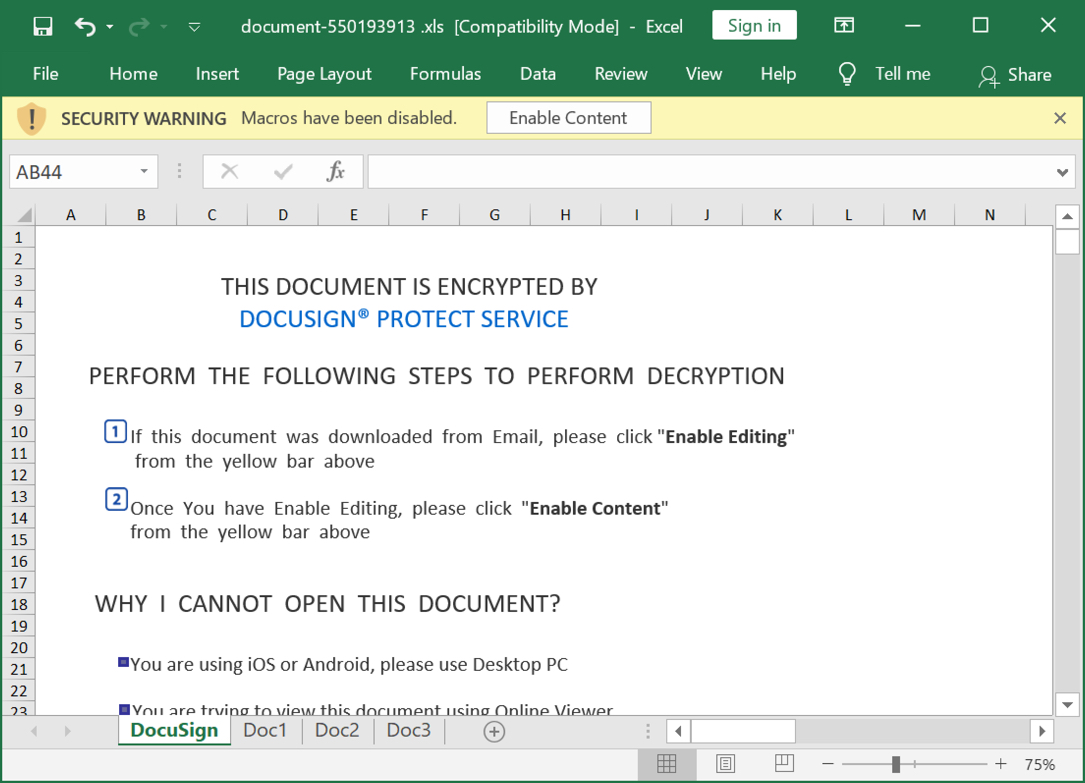
Shown above: Screenshot of the Excel spreadsheet used for today's infection.
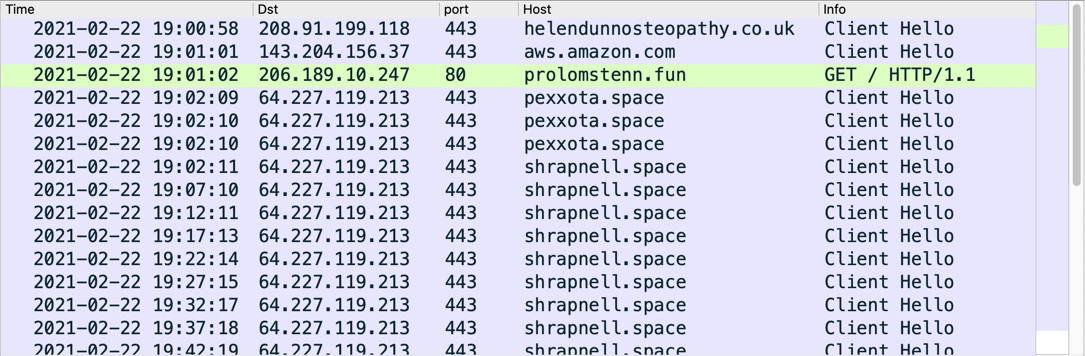
Shown above: Traffic from the infection filtered in Wireshark.
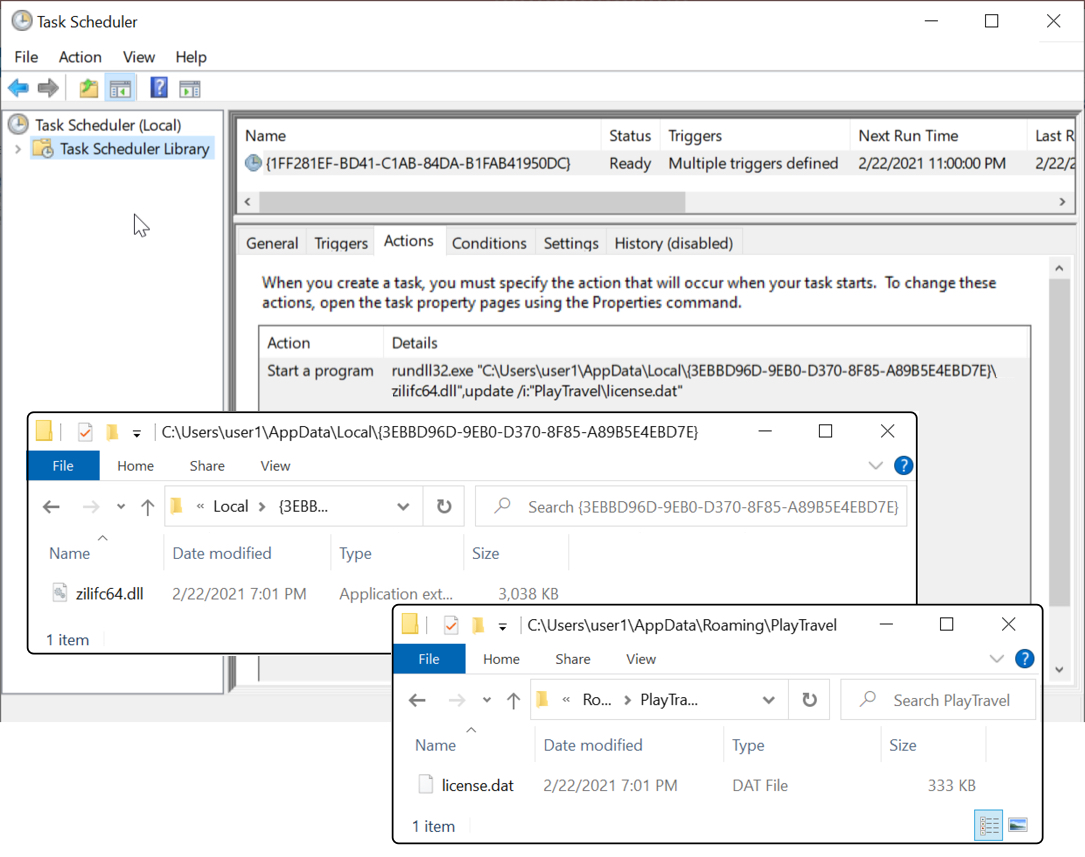
Shown above: IcedID persistent on the infected Windows host.
Click here to return to the main page.
