2021-07-12 (MONDAY) - TRICKBOT GTAG ROB106
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-07-12-Trickbot-gtag-rob106-malspam-2-examples.zip 69 kB (69,152 bytes)
- 2021-07-12-Trickbot-malspam-1610-UTC.eml (51,382 bytes)
- 2021-07-12-Trickbot-malspam-1613-UTC.eml (38,977 bytes)
- 2021-07-12-Trickbot-gtag-rob106-infection-traffic.pcap.zip 8.0 MB (7,992,365 bytes)
- 2021-07-12-Trickbot-gtag-rob106-infection-traffic.pcap (9,058,261 bytes)
- 2021-07-12-malware-and-artifacts-for-Trickbot-gtag-rob106.zip 6.8 MB (6,831,527 bytes)
- 2021-07-12-scheduled-task-for-Trickbot-gtag-rob106.txt (3,592 bytes)
- AppData/Local/Temp/lKVdXIL.bin (808,448 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/grabber_temp.INTEG.RAW (19,563 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/importDll.txt (23,397 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/cn/juewqd.txt (1,931,824 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/en-EN/importDll64 (1,819,936 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/en-EN/pwgrabb64 (473,984 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/en-EN/pwgrabc64 (166,736 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/en-EN/injectDll64 (756,592 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/en-EN/networkDll64 (519,536 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/settings.ini (36,944 bytes)
- AppData/Roaming/nvidiaRaysL1TF19/jplKVdXILhn.htb (808,448 bytes)
- Zoom_Conference_Invitation_1625.js (73,212 bytes)
- Zoom_Conference_Invitation_1625.zip (36,563 bytes)
- Zoom_Conference_Invitation_4152.js (59,330 bytes)
- Zoom_Conference_Invitation_4152.zip (27,191 bytes)
NOTES:
- Starting this week, I've noticed some unusual activity with Trickbot modules related to the web browsers on an infected Windows host.
- I'm seeing one of the Trickbot modules check for and access the following browsers: Internet Exporer, Edge, Chrome, and Firefox.
- This infection was done on a Windows 7 host in an Active Directory environment, so encoded/encrypted artifacts for the modules were saved to disk.
IMAGES
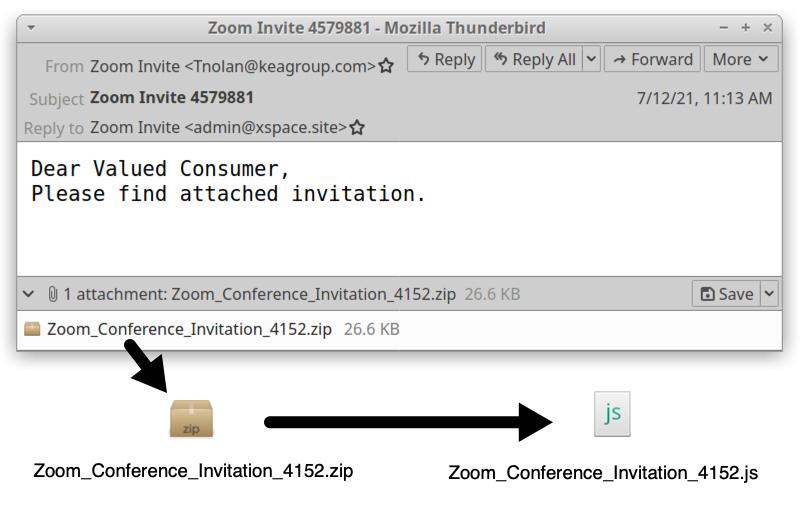
Shown above: Screenshot from one of the emails.
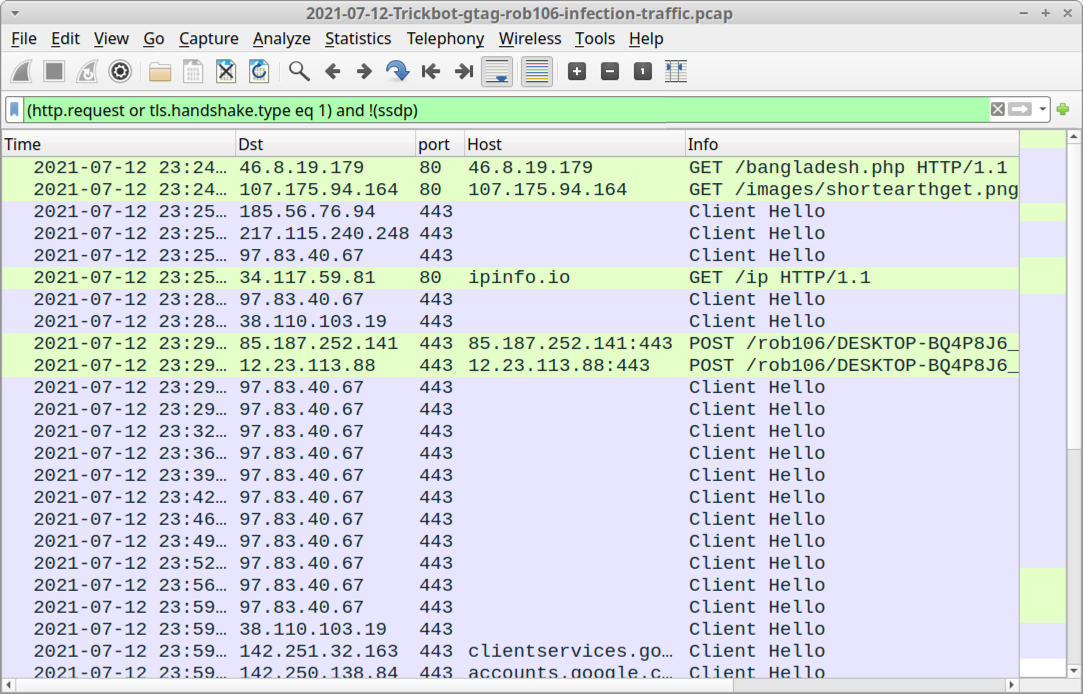
Shown above: Traffic from an infection filtered in Wireshark.
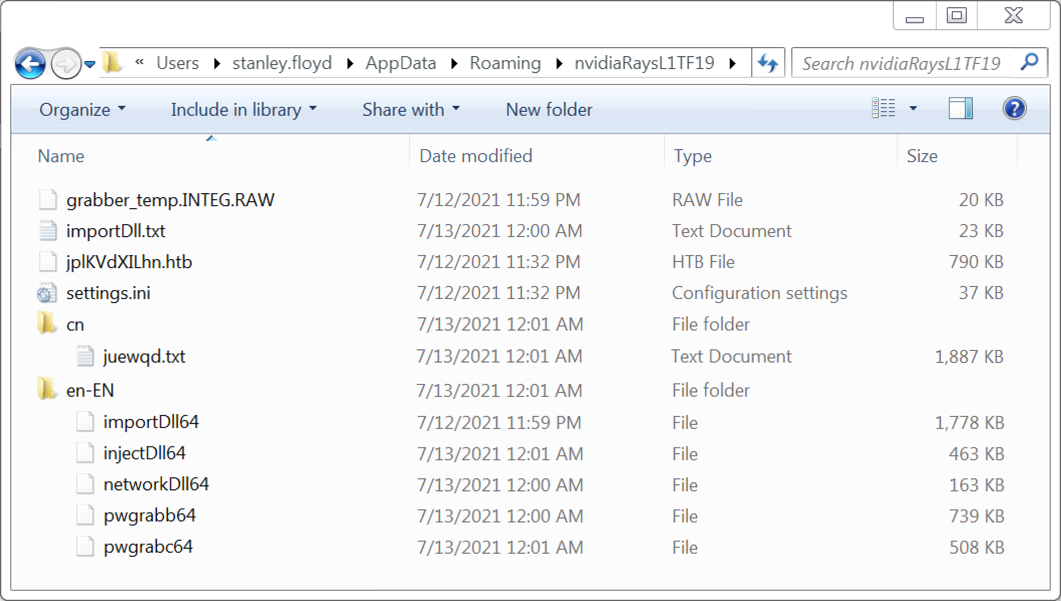
Shown above: Some artifacts from the infected Windows host.
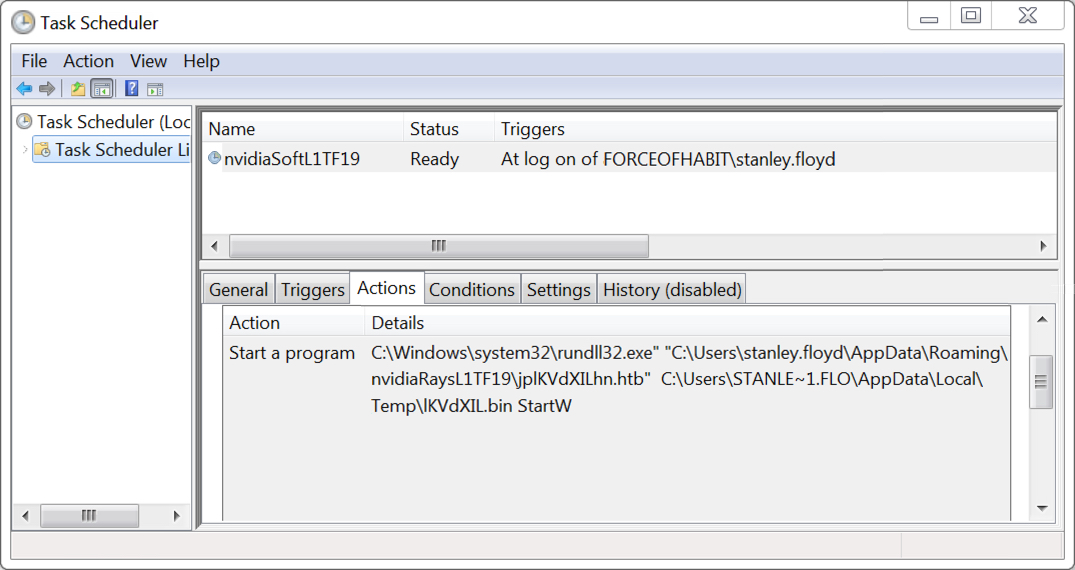
Shown above: Scheduled task to keep Trickbot infection persistent.
Click here to return to the main page.
