2022-02-01 (TUESDAY) - HANCITOR (CHANITOR/MAN1/MOSKALVZAPOE/TA511) INFECTION WITH COBALT STRIKE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2022-02-01-IOCs-for-Hancitor-and-Cobalt-Strike.txt.zip 3.2 kB (3,263 bytes)
- 2022-02-01-Hancitor-malspam-33-examples.zip 81.9 kB (81,915 bytes)
- 2022-02-01-Hancitor-infection-with-Cobalt-Strike.pcap.zip 2.2 MB (2,227,550 bytes)
- 2022-02-01-Hancitor-malware-and-artifacts.zip 6.4 MB (6,435,737 bytes)
IMAGES
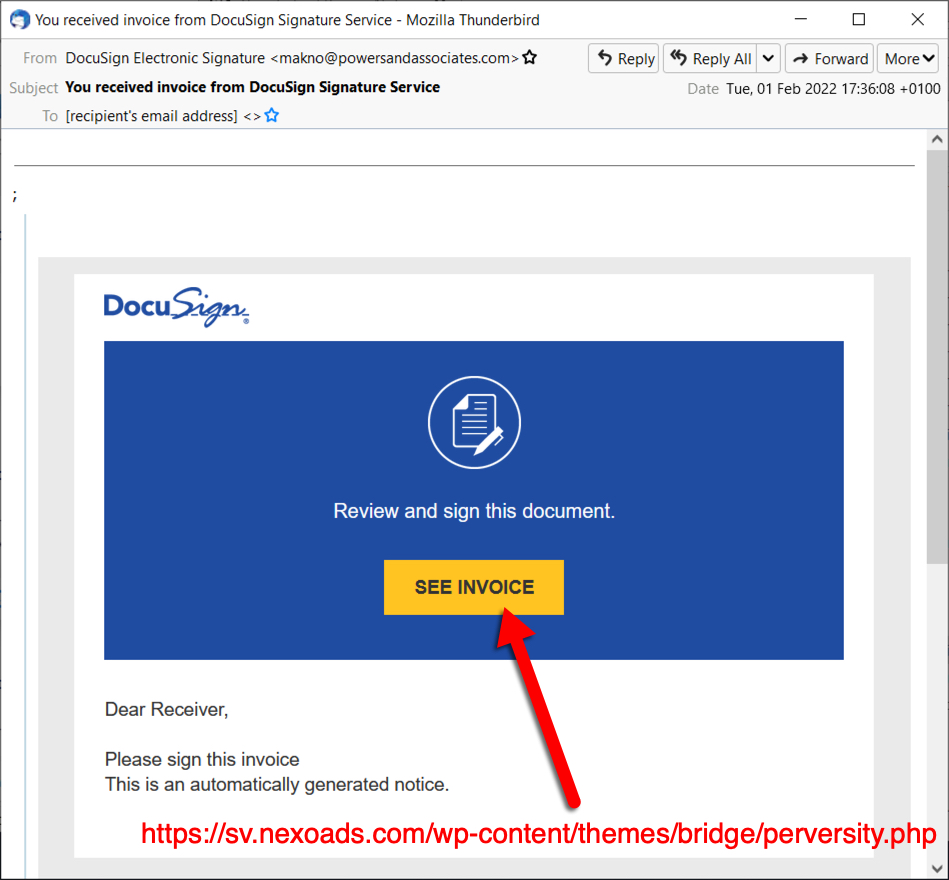
Shown above: Screenshot from one of the emails.
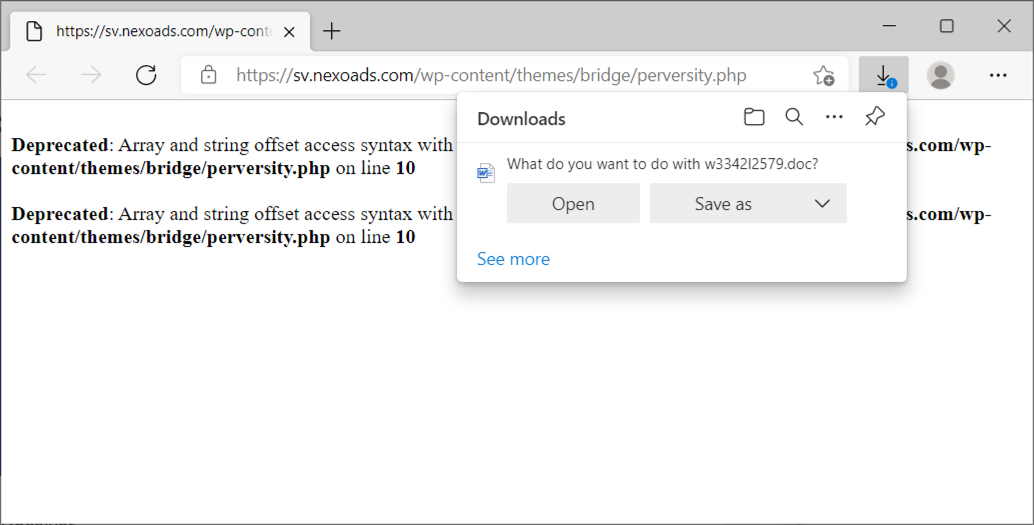
Shown above: Link from the email returned a Word doc.
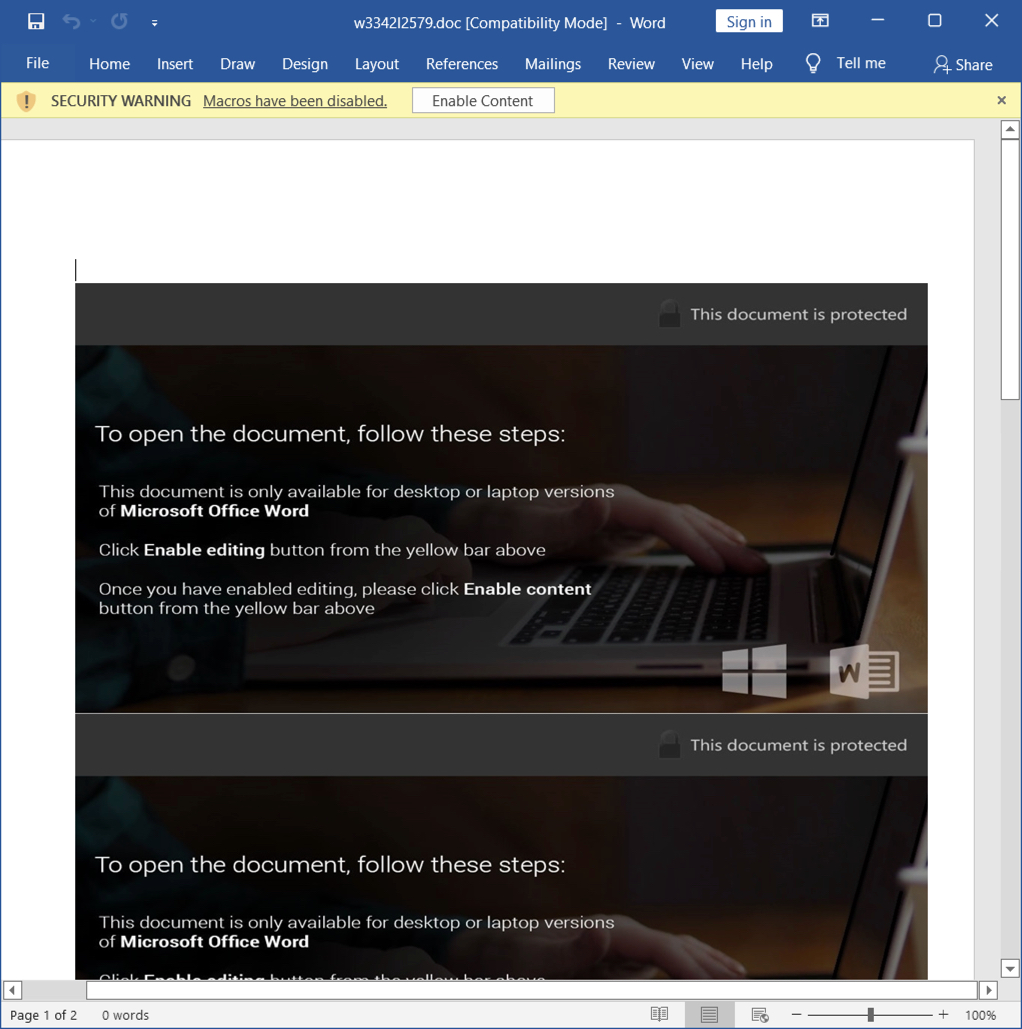
Shown above: Screenshot of the Hancitor Word doc.
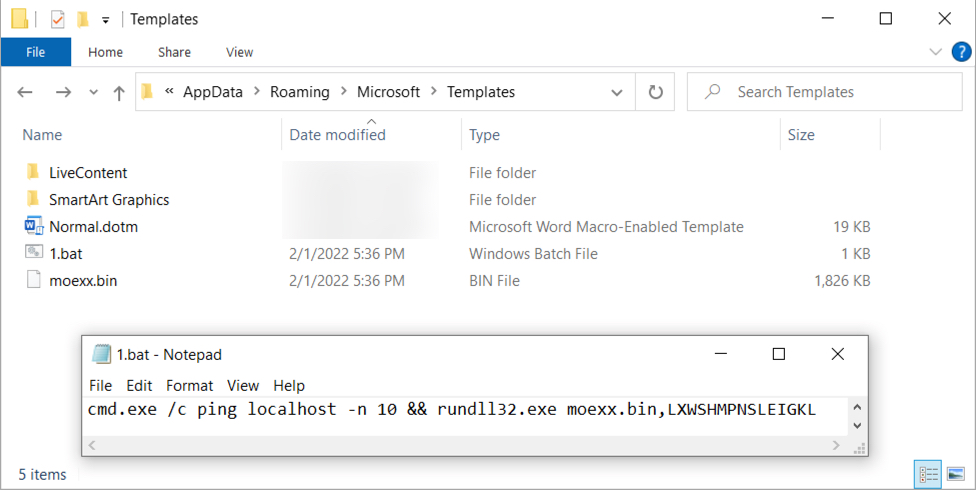
Shown above: Batch file and Hancitor DLL (moexx.bin) on the infected Windows host.
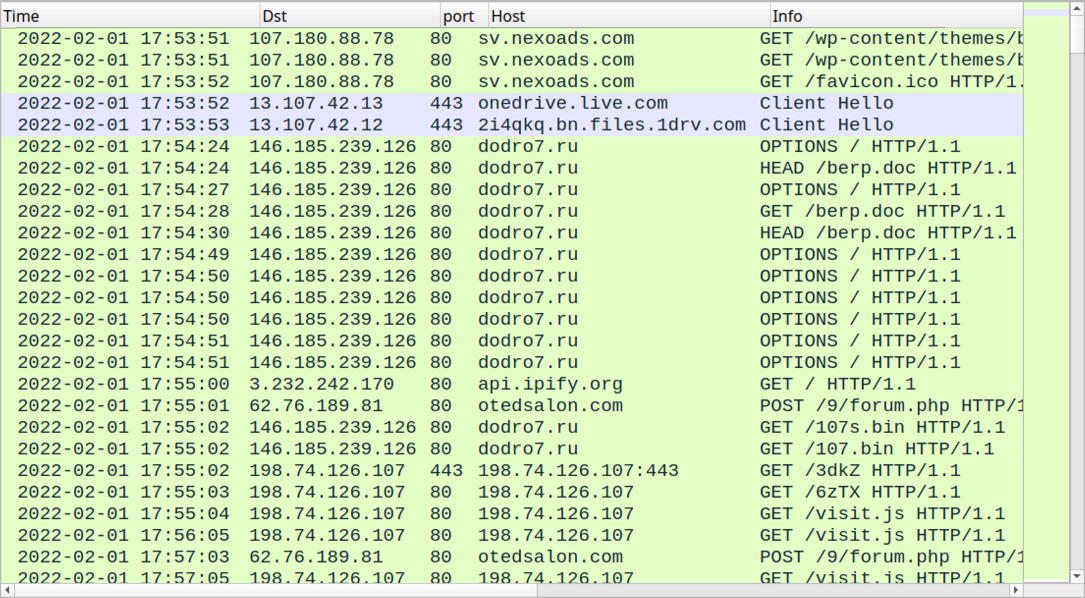
Shown above: Traffic from the infection filtered in Wireshark.
Click here to return to the main page.
