2022-07-01 (FRIDAY) - MONSTER LIBRA (TA551) SVCREADY INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- Sometime in April 2022, Monster Libra (TA551) began distributing a new malware family named SVCready.
- Today's infection used a Word document with an English language template.
- More information on SVCready can be found here.
- Some data on Monster Libra can be found here.
- My previous post on this: https://www.malware-traffic-analysis.net/2022/06/08/index.html.
ASSOCIATED FILES:
- 2022-07-01-IOCs-for-SVCready-infection.txt.zip 2.1 kB (2,096 bytes)
- 2022-07-01-SVCready-infection.pcap.zip 14.5 MB (14,483,482 bytes)
- 2022-07-01-SVCready-malware-and-artifacts.zip 4.2 MB (4,161,163 bytes)
INDICATORS
MALWARE:
SHA256 hash: d75077838fc33ec2769f958b1035346cd67da083f77a2edaa01375b19ba960b2
- File size: 2,915,744 bytes
- File name: dybb_document_07.01.2022.doc
- File description: Example of English language template Word document with macros for SVCready
SHA256 hash: 6cbe0e1f046b13b29bfa26f8b368281d2dda7eb9b718651d5856f22cc3e02910
- File size: 61,440 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\r78AD.tmp.exe
- File description: Copy of rundll32.exe (not inherently malicious)
SHA256 hash: 64ea06acffb3905ff1f7255d45f8f333821bce10f6c40ab8121af72d74706907
- File size: 892,928 bytes
- Initial saved location: C:\Users\[username]\AppData\Local\Temp\y6A72.tmp.dll
- Persistent location: C:\Users\[username]\AppData\Roaming\Microsoft\1472CB9B-F02A-4372-A322-9EA6FA0E2E75.b9V
- File description: SVCready DLL
- Run method: rundll32.exe [filename], DllRegisterServer
- Note 1: The persistent SVCready DLL is copied to a new name approximately every 30 to 45 minutes.
- Note 2: The scheduled task is updated to relfect the new name of the SVCready DLL
- Note 3: Old copies of the SVCready DLL remain under C:\Users\[username]\AppData\Roaming\Microsoft\
INFECTION TRAFFIC DOMAINS/IP ADDRESSES:
- 109.68.215[.]242 port 80 - foryousbissnesnet[.]quest
- 109.68.215[.]242 port 80 - marinesss[.]su
INFECTION TRAFFIC URLS:
- foryousbissnesnet[.]quest - POST /xl/ruiohmc/uhgvrkr HTTP/1.1
- foryousbissnesnet[.]quest - POST /xl/ruiohmc HTTP/1.1 (text/plain)
- foryousbissnesnet[.]quest - POST /xl/ruiohmc HTTP/1.1
- foryousbissnesnet[.]quest - POST /xl/ruiohmc/truheru HTTP/1.1
- marinesss[.]su - POST /xl/ruiohmc/uhgvrkr HTTP/1.1
- marinesss[.]su - POST /xl/ruiohmc HTTP/1.1 (text/plain)
- marinesss[.]su - POST /xl/ruiohmc HTTP/1.1
- marinesss[.]su - POST /xl/ruiohmc/truheru HTTP/1.1
IMAGES
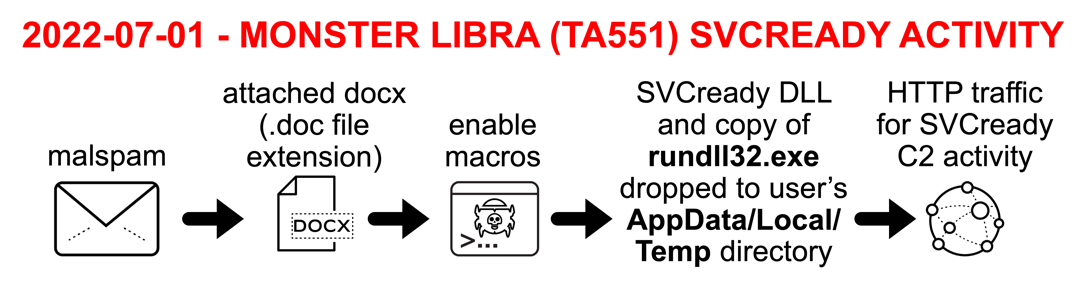
Shown above: Chain of events for this SVCready infection.

Shown above: Word document with macros for SVCready.
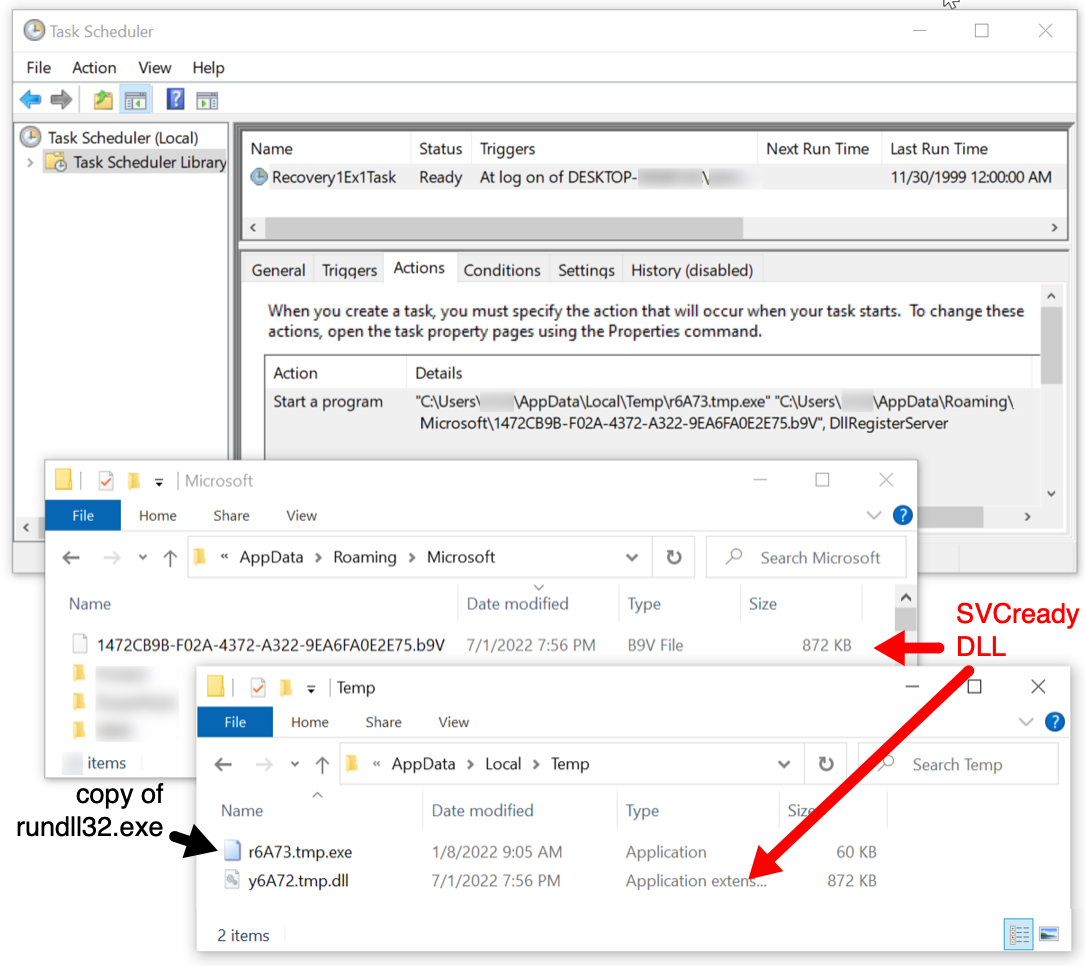
Shown above: Scheduled task and malware/artifacts from the infection.
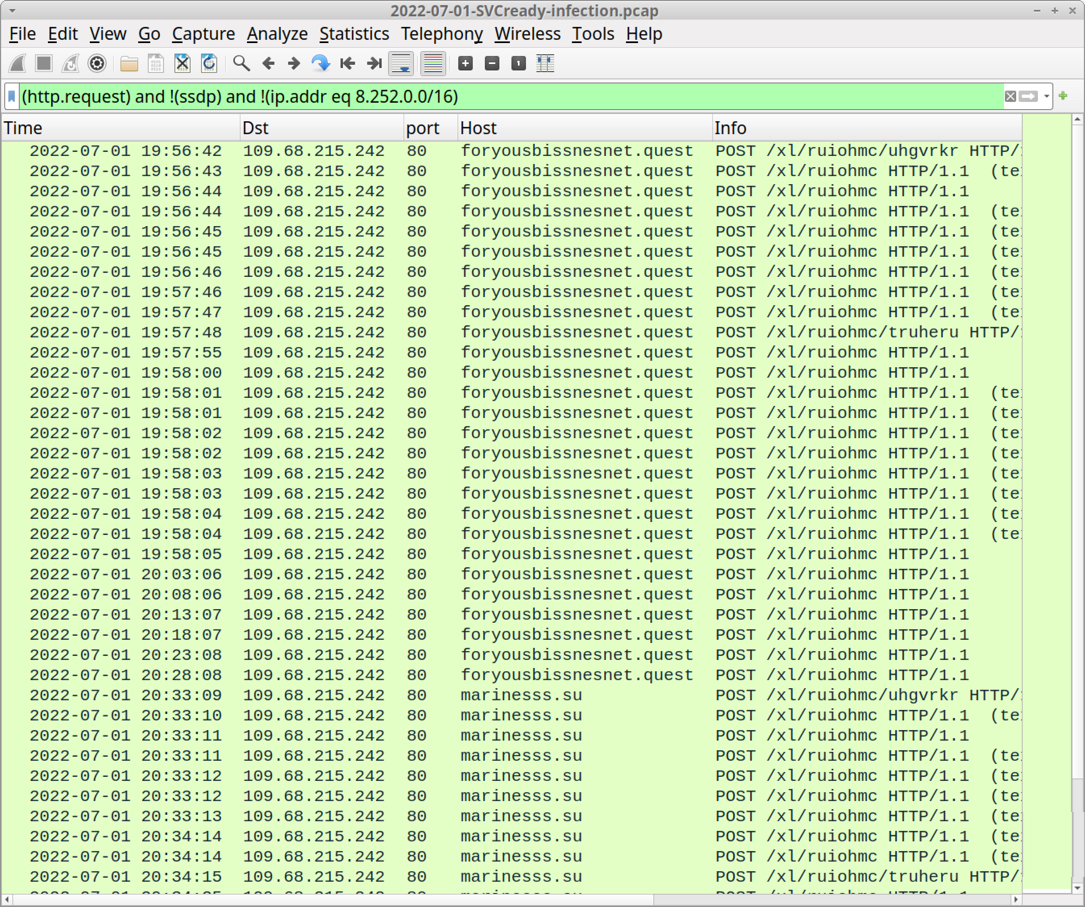
Shown above: Traffic from the infection filtered in Wireshark.

Shown above: TCP stream of SVCready C2 traffic.
Click here to return to the main page.
