2022-08-30 (TUESDAY) - FOLLOW-UP SLIVER TRAFFIC FROM BUMBLEBEE INFECTION (SLIVER)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- I can't share the full pcap, but I extracted the unidentified TLSv1.3 traffic over TCP port 8557, in case someone can figure out what it is.
- UPDATE: I was informed through a trusted source this traffic was caused by malware based on Sliver.
ASSOCIATED FILES:
- 2022-08-30-Sliver-traffic-after-a-Bumblebee-infection.pcap.zip 21.0 kB (21,026 bytes)
INDICATORS
FILE USED TO GENERATE THIS INFECTION:
- Powershell script (.ps1) file: link to sample on bazaar.abuse.ch
TRAFFIC:
- Bumblebee HTTPS (TLSv1.2) traffic: 142.11.234[.]238:443
- Unidentified TLSv1.3 traffic: 65.20.115[.]15:8557
- Cobalt Strike HTTPS (TLSv1.3) traffic: 23.19.58[.]94:443
- Cobalt Strike HTTPS (TLSv1.3) traffic: 23.81.246[.]152:443
IMAGES
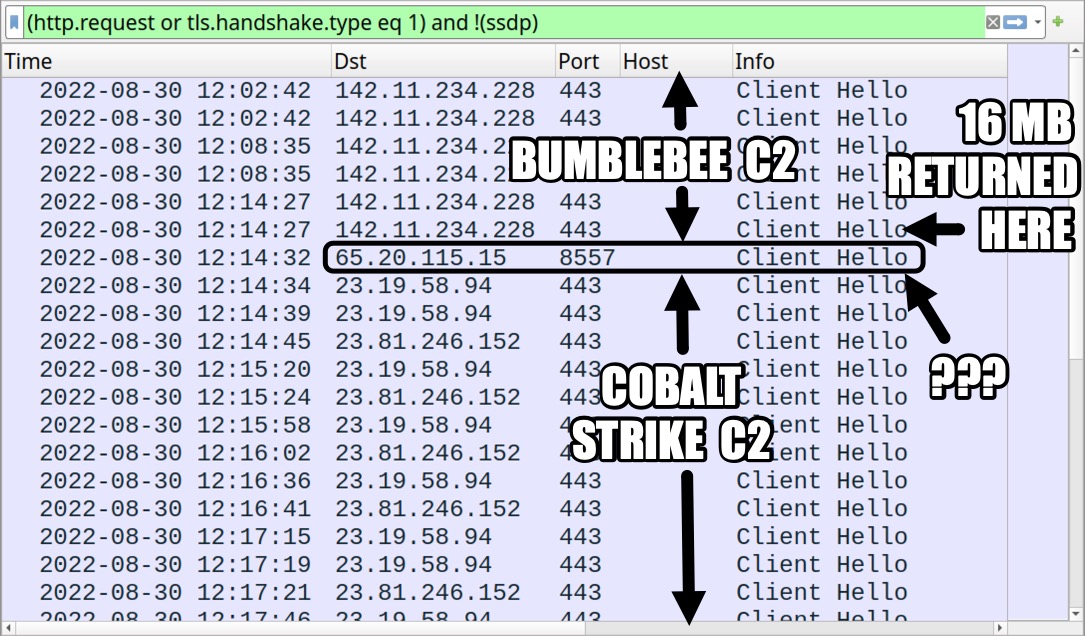
Shown above: Traffic from the infection filtered in Wireshark.
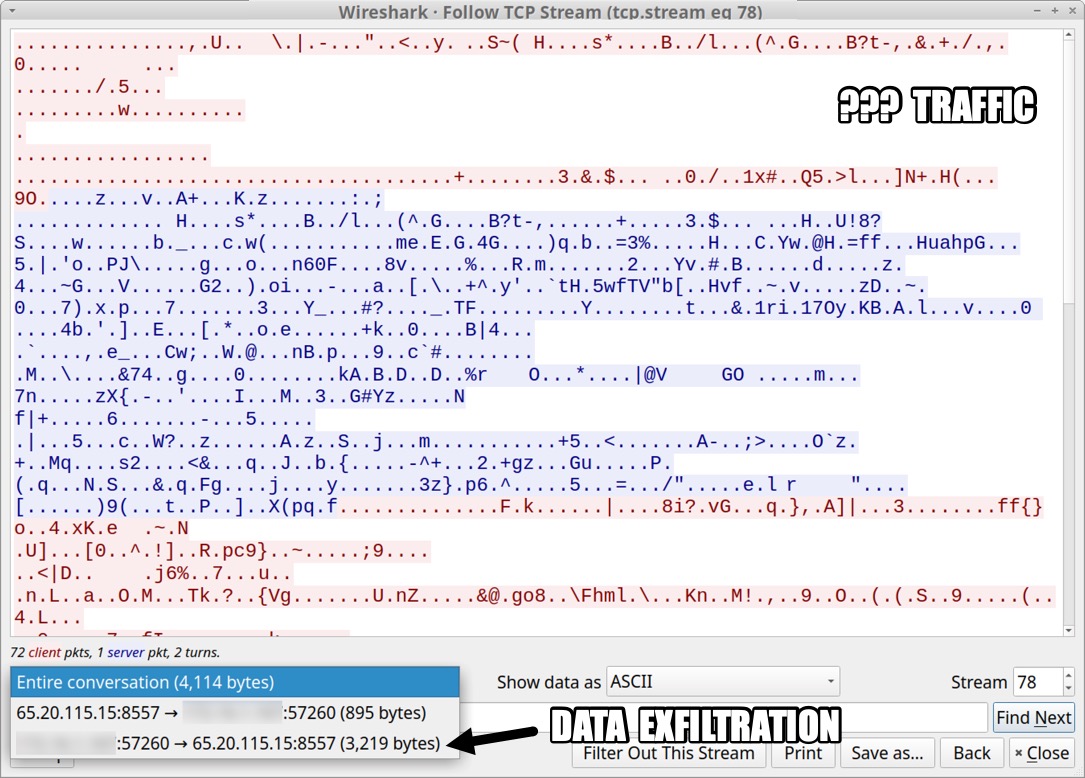
Shown above: TCP stream of the unidentified TLSv1.3 traffic over TCP port 8557.
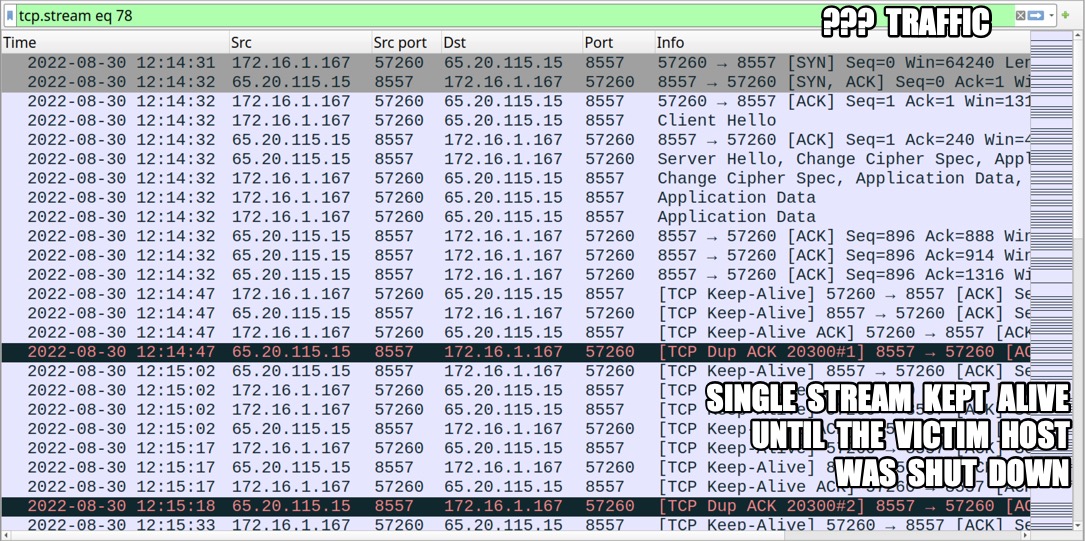
Shown above: TCP stream of the unidentified TLSv1.3 traffic over TCP port 8557 kept alive while victim host was active.
Click here to return to the main page.
