2022-10-06 (THURSDAY) - HTML SMUGGLING --> ICEDID (BOKBOT) --> COBALT STRIKE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2022-10-06-IOCs-for-IcedID-with-Cobalt-Strike.txt.zip 2.3 kB (2,344 bytes)
- 2022-10-06-IcedID-with-Cobalt-Strike-santized-and-carved.pcap.zip 2.3 MB (2,267,371 bytes)
- 2022-10-06-IcedID-and-Cobalt-Strike-malware-and-artifacts.zip 7.6 MB (7,559,845 bytes)
IMAGES
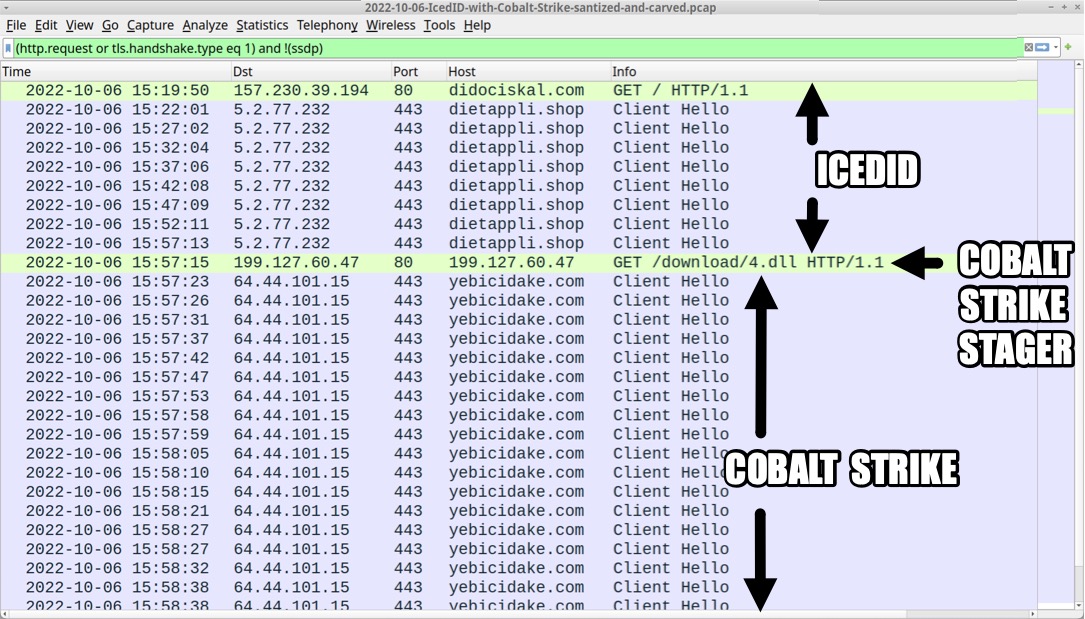
Shown above: Traffic from the infection filtered in Wireshark.
2022-10-06 (THURSDAY) - ICEDID (BOKBOT) WITH COBALT STRIKE
INFECTION CHAIN:
- email --> HTML file --> password-protected zip --> ISO --> Windows shortcut runs installer DLL --> IcedID C2 --> Cobalt Strike
NOTES:
- Same type of HTML smuggling reported on 2022-10-04 (https://twitter.com/Unit42_Intel/status/1577773890012594177)
- Unlike that previous infection, today contained no traffic over TCP port 8080 (see above reference).
HTML ATTACHMENT, PASSWORD-PROTECTED ZIP ARCHIVE, AND EXTRACTED ISO IMAGE:
- SHA256 hash: 6568d1938debb7b49ce8278358b86a1b47c238da690feb058496f187fe6c8bd0
- File size: 1,743,877 bytes
- File name: [redacted]-file-10.06.2022.html
- File description: HTML file seen as Email attachment
- Sample: https://bazaar.abuse.ch/sample/6568d1938debb7b49ce8278358b86a1b47c238da690feb058496f187fe6c8bd0/
- Note: Thanks to @k3dg3 for making this publicly avaiable!
- SHA256 hash: 240c9be328a474eafe94889428949dae6c2f5ca068c33fb6ed63ebde144f7574
- File size: 1,222,677 bytes
- File name: d755ab64-50f8-4faa-bd40-559682f92698.zip
- File description: password-protected zip archive presented by the above HTML file
- Password: yBGpjJ5W
- SHA256 hash: b22dd6ed2c9dc341d8133f9ca28d9d8c4b7682b9a3d3963385f70a230e425de4
- File size: 2,052,096 bytes
- File name: file-3b2d0fe4-496b-40dd-a420-ac2202ed92fc.iso
- File description: ISO image extracted from the above zip archive
CONTENTS OF ISO IMAGE:
- SHA256 hash: d639d883cc0aebc48f5f5427a90fec25d61d6071603f6ee25efe6354ba495ff2
- File size: 2,002 bytes
- File name: file-3b2d0fe4-496b-40dd-a420-ac2202ed92fc.lnk
- File description: Windows shortcut used to run IcedID installer DLL
- SHA256 hash: e493a191a3cf0f90a85b02e46f8cb325828bbd570f5e7359e3542bbd93a91918
- File size: 695,808 bytes
- File name: 0d027b85-d430-4c43-82b9-631ba9008fa9.U1o
- File description: IcedID installer DLL (64-bit)
- Run method: rundll32.exe [filename],#1
- SHA256 hash: 573a25373c30ac1101ac4e6688a764be96b9ceb64b1a1d76016f67980005901b
- File size: 982,831 bytes
- File name: 76571cfa-1f0b-468e-80e6-bf023b27189d.png
- File description: Decoy image shown when running the above Windows shortcut, not inherently malicious
FILES FOR ICEDID SEEN DURING THE INFECTION:
- SHA256 hash: d6b53df3dc6a4b4729733e1ca9524ad3e47222c7a41fb55bf49ae8fbc2206de1
- File size: 1,050,683 bytes
- File description: gzip binary from didociskal[.]com used to create license.dat and persistent IcedID DLL
- SHA256 hash: 8bae218c7d1759c65c92a5a06d23749734ae67be12707a5dad8cb4f23e35e635
- File size: 686,592 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\step_64.dat
- File description: 64-bit DLL for IcedID created by the initial IcedID installer DLL
- SHA256 hash: 55be890947d021fcc8c29af3c7aaf70d8132f222e944719c43a6e819e84a8f8b
- File size: 363,338 bytes
- File location: C:\Users\[username]\AppData\Roaming\LemonBullet\license.dat
- File description: data binary used to run persistent IcedID DLL
- Note: First submitted to VirusTotal on 2022-09-23
- SHA256 hash: ceb6a9a00bf123250c0393e67a6f75e93f2c2ef1b39e4978a95c59f0916bb804
- File size: 686,592 bytes
- File location: C:\Users\[username]\AppData\Roaming\{3804B787-D8DB-D07A-4865-17ED5EDE20A8}\uhbuoxmp1.dll
- File description: 64-bit DLL for IcedID persistent on the infected host
- Run method: rundll32.exe [filename],#1 --zoow="[path to license.dat]"
COBALT STRIKE STAGER
- SHA256 hash: ebece5533902a021c27c67a3342e551499dae65b033410d468e9f3a1145f4c57
- File size: 1,243,648 bytes
- File location: hxxp[:]//199.127.60[.]47/download/4.dll
- File location: C:\Users\[username]\AppData\Local\Temp\Gukaoy2.dll
- File description: 64-bit DLL stager for Cobalt Strike
- Run method: regsvr32.exe /s [filename]
TRAFFIC FROM THE INFECTION:
INSTALLER RETRIEVES GZIP BINARY:
- 157.230.39[.]194 port 80 - didociskal[.]com - GET /
ICEDID C2 TRAFFIC:
- 5.2.77[.]232 port 443 - dietappli[.]shop - HTTPS traffic
TRAFFIC TO RETRIEVE COBALT STRIKE STAGER DLL:
- 199.127.60[.]47 port 80 - 199.127.60[.]47 - GET /download/4.dll
COBALT STRIKE C2 TRAFFIC:
- 64.44.101[.]15 port 443 - yebicidake[.]com - HTTPS traffic
- Note: within the TLSv1.2 tunnel using 64.44.101[.]15, the initial URL for Cobalt Strike was
hxxps[:]//google.co[.]uk/image-directory/panel.gif
Click here to return to the main page.
