2022-10-12 (WEDNESDAY): ICEDID (BOKBOT) --> COBALT STRIKE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
REFERENCE:
ASSOCIATED FILES:
- 2022-10-12-IOCs-for-IcedID-with-Cobalt-Strike.txt.zip 2.4 kB (2,348 bytes)
- 2022-10-12-traffic-for-IcedID-infection-with-Cobalt-Strike-carved-and-sanitized.zip 5.7 MB (5,718,228 bytes)
- 2022-10-12-IcedID-and-Cobalt-Strike-malware.zip 1.9 MB (1,941,171 bytes)
IMAGES
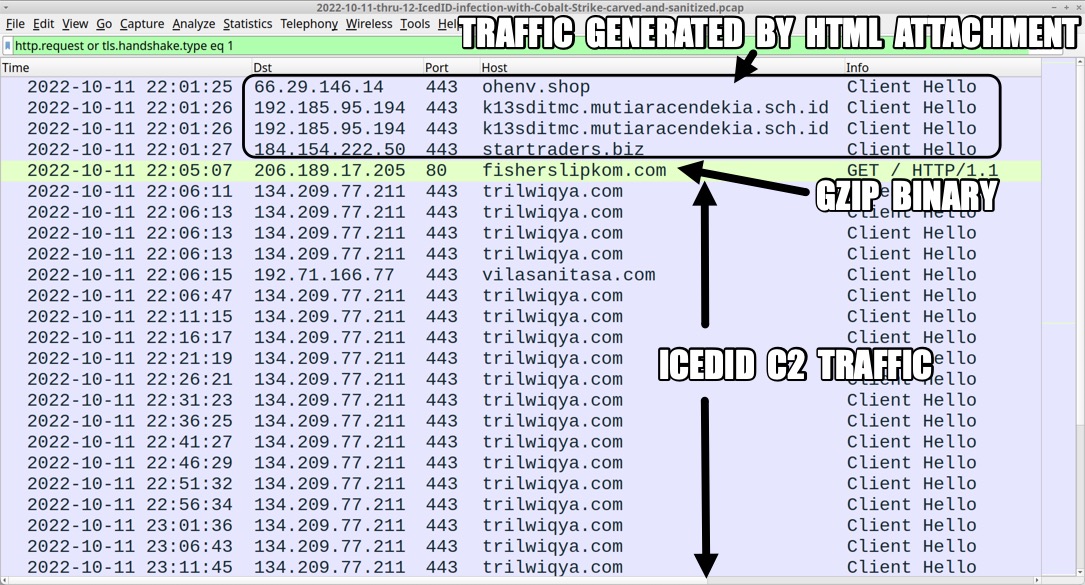
Shown above: Traffic from the infection filtered in Wireshark (1 of 2).
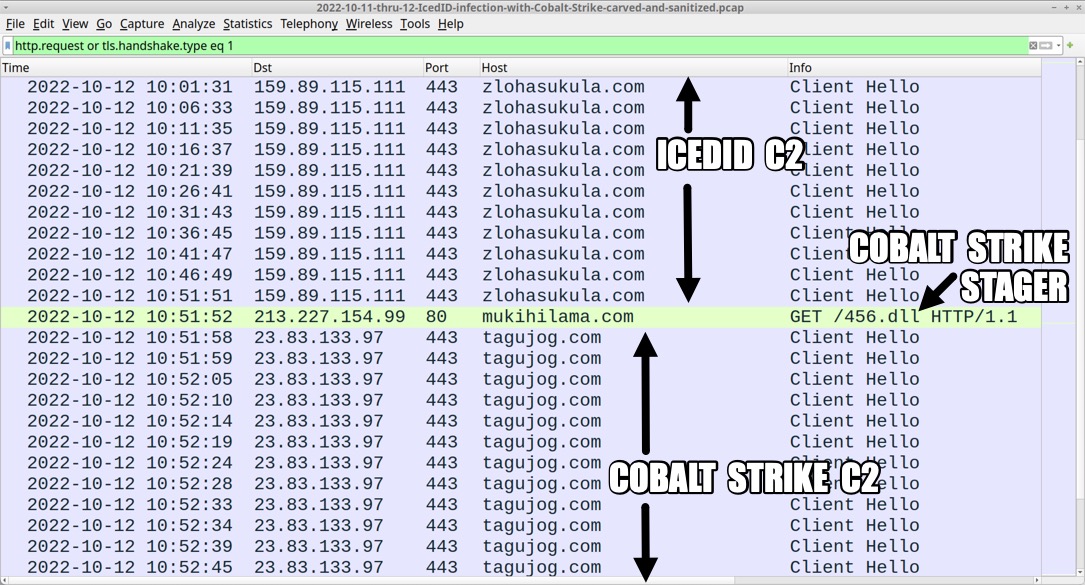
Shown above: Traffic from the infection filtered in Wireshark (2 of 2).
2022-10-11 (TUESDAY) THRU 10-12 (WEDNESDAY): ICEDID (BOKBOT) --> COBALT STRIKE INFECTION CHAIN: - email --> HTML file --> password-protected zip --> ISO --> Windows shortcut runs DLL --> IcedID C2 --> Cobalt Strike HTML ATTACHMENT, PASSWORD-PROTECTED ZIP, AND EXTRACTED ISO IMAGE: - SHA256 hash: 492872d37e6a72bc0d90c74ef52e88550d2a64aa33813cefe64e69b1e1b145f8 - File size: 410,683 bytes - File name: invoice_945416.PDF.html - File description: HTML attachment from malspam - SHA256 hash: a9e4f2f460ea05f33fec7d79df5e65e13dc4a1f06ba22df261bbd49fcc4118f8 - File size: 227,686 bytes - File name: Invoice_584894.zip - File description: password-protected zip archive presented by above HTML file - Password: 556 - SHA256 hash: ab3ac2a34c3a3641a1cb1a52d615cfb50cf308e90ed4acea48a7cd1a0fe92c40 - File size: 919,552 bytes - File name: invoice.iso - File description: ISO image extracted from the above zip archive CONTENTS OF ISO IMAGE: - invdocs.doc.lnk: MS Windows shortcut - GLANCE\AIRLINE.DAT: PE32+ executable (DLL) (console) x86-64, for MS Windows - GLANCE\EXECUTE.TXT: Unicode text, UTF-8 text, with very long lines (1785) - GLANCE\FDA.PNG: PNG image data, 983 x 622, 8-bit/color RGB, non-interlaced - GLANCE\HEADS.PNG: PNG image data, 983 x 622, 8-bit/color RGB, non-interlaced - GLANCE\MINUS.cmd: ASCII text, with CRLF line terminators - GLANCE\ROADS.TXT: Unicode text, UTF-8 text, with very long lines (2195) - GLANCE\SPANK.TXT: Unicode text, UTF-8 text, with very long lines (2195) - GLANCE\WISE.TXT: Unicode text, UTF-8 text, with very long lines (1785) - SHA256 hash: cfd78ef75ae4ccfd806afc09dcd2b5b5b5e5946f1b2269b8f103d51b032d398b - File size: 1,380 bytes - File name: invdocs.doc.lnk - File description: Windows shortcut used to run GLANCE\MINUS.cmd - SHA256 hash: c5e1f85728ef1e0d20e766d267168a133b58cfed9977dcb46a70a4950ac9c1ae - File size: 77 bytes - File name: GLANCE\MINUS.cmd - File description: .cmd batch script run by the above Windows shortcut - SHA256 hash: 85fcfca51a30525feefa12252866ed9d72a7f778515f39b3539f487e8b70c2bb - File size: 66,560 bytes - File name: GLANCE\AIRLINE.DAT - File description: IcedID installer DLL (64-bit) run by the above .cmd file - Run method: rundll32.exe [filename],#1 FILES FOR ICEDID SEEN DURING THE INFECTION: - SHA256 hash: 18331bff8ca38c70fe2b7e9e412f4e555ea7778a4924bda4abd6585b7d0107ac - File size: 423,131 bytes - File description: gzip binary from fisherslipkom.com used to create license.dat and persistent IcedID DLL - SHA256 hash: a0f5450deb333336e9d157e94647381036e7a9107ec842b24a9624d59cbfd59a - File size: 364,522 bytes - File location: C:\Users\[username]\AppData\Roaming\JumpCake\license.dat - File description: data binary used to run persistent IcedID DLL - Note: new license.dat first submitted to VirusTotal today - SHA256 hash: 9b763b54ea4873f304faf0d592b28d8e659cdeae879c5bbf0f4b4825e4d0dc4f - File size: 57,856 bytes - File location: C:\Users\[username]\AppData\Local\uqef\Fauzmipw.dll - File description: 64-bit DLL for IcedID persistent on the infected host - Run method: rundll32.exe [filename],#1 --id="[path to license.dat]" INFECTION TRAFFIC: TRAFFIC GENERATED BY HTML FILE FOR PASSWORD-PROTECTED ZIP: - 66.29.146[.]14:443 - ohenv[.]shop - HTPS traffic - 192.185.95[.]194:443 - k13sditmc.mutiaracendekia.sch[.]id - HTPS traffic - 184.154.222[.]50:443 - startraders[.]biz - HTPS traffic URLS FROM THE ABOVE HTTPS TRAFFIC: - hxxps[:]//ohenv[.]shop/?6l3wueXz40rEoabGR2FPuwWW44rj3kFXa9JAGRE66l3wueXz40rEoabGR2FPuwWW44rj3kFXa9JAGRE6 - hxxps[:]//k13sditmc.mutiaracendekia.sch[.]id/hideousness.php - hxxps[:]//startraders[.]biz/sh/sh/?d3e4f46ee6f617ac469095e65ed8d5b5d3e4f46ee6f617ac469095e65ed8d5b5 INSTALLER DLL RETRIEVES GZIP BINARY: - 206.189.17[.]205 port 80 - fisherslipkom[.]com - GET / ICEDID C2 TRAFFIC: - 134.209.77[.]211 port 443 - trilwiqya[.]com - HTTPS traffic - 192.71.166[.]77 port 443 - vilasanitasa[.]com - HTTPS traffic - 159.89.115[.]111 port 443 - zlohasukula[.]com - HTTPS traffic - 5.255.102[.]24 port 443 - plenomils[.]homes - HTTPS traffic - 5.255.102[.]24 port 443 - chattyprettyhot[.]com - HTTPS traffic - 192.71.166[.]77 port 443 - alohabrunda[.]com - HTTPS traffic COBALT STRIKE STAGER: - 213.227.154[.]99 port 80 - mukihilama[.]com - GET /456.dll COBALT STRIKE C2 TRAFFIC: - 23.83.133[.]97 port 443 - tagujog[.]com - HTTPS traffic COBALT STRIKE MALWARE: - SHA256 hash: be9ae4f35c971037fd5762105e3f5bb6657fc27e37a42663878fc954ddfaeff5 - File size: 168,448 bytes - File location: hxxp[:]//mukihilama[.]com/456.dll - File location: C:\Users\[username]\AppData\Local\Temp\[random name].dll - File description: 64-bit DLL for Cobalt Strike - Run method: regsvr32.exe [filename]
Click here to return to the main page.
