2023-01-18 (WEDNESDAY) - GOOGLE AD --> FAKE LIBRE OFFICE PAGE --> ICEDID (BOKBOT) --> COBALT STRIKE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2023-01-18-IOCs-for-fake-LibreOffice-page-to-IcedID-to-Cobalt-Strike.txt.zip 2.4 kB (2,361 bytes)
- 2023-01-18-IcedID-with-Cobalt-Strike-2-pcaps.zip 4.7 MB (4,736,942 bytes)
- 2023-01-18-IcedID-with-Cobalt-Strike-malware-and-artifacts.zip 4.1 MB (4,083,507 bytes)
IMAGES
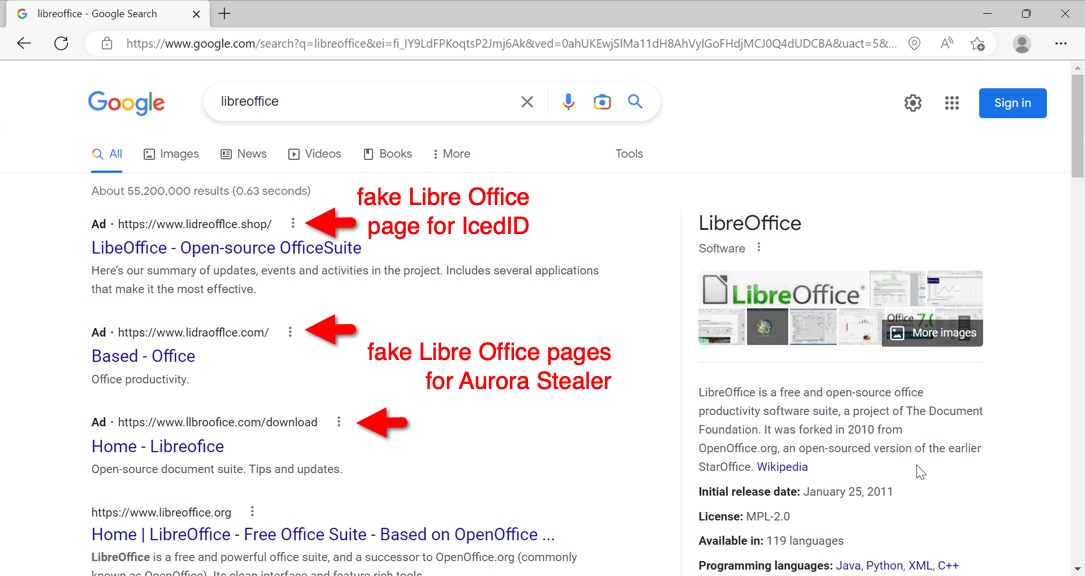
Shown above: I found 3 malicious web sites after a Libre Office search in Google.
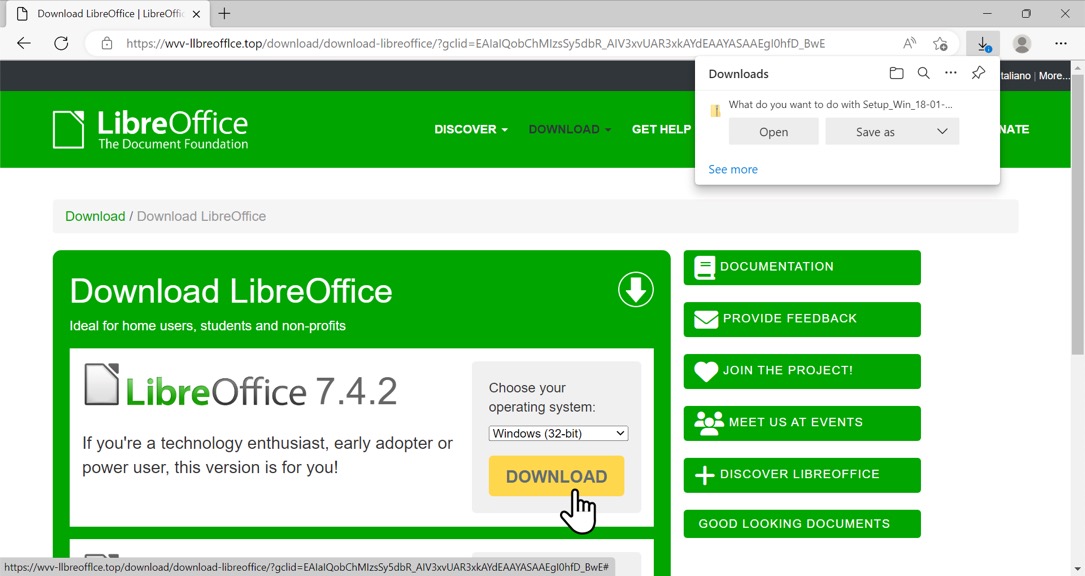
Shown above: Downloading a malicious file from the fake Libre Office page.
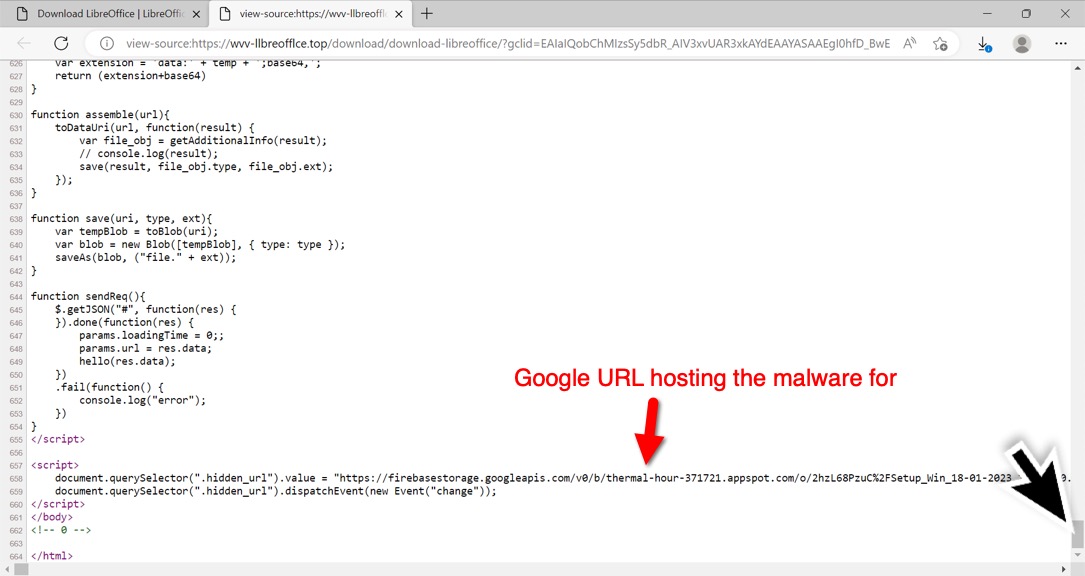
Shown above: Finding the Google URL hosting the malware I downloaded.
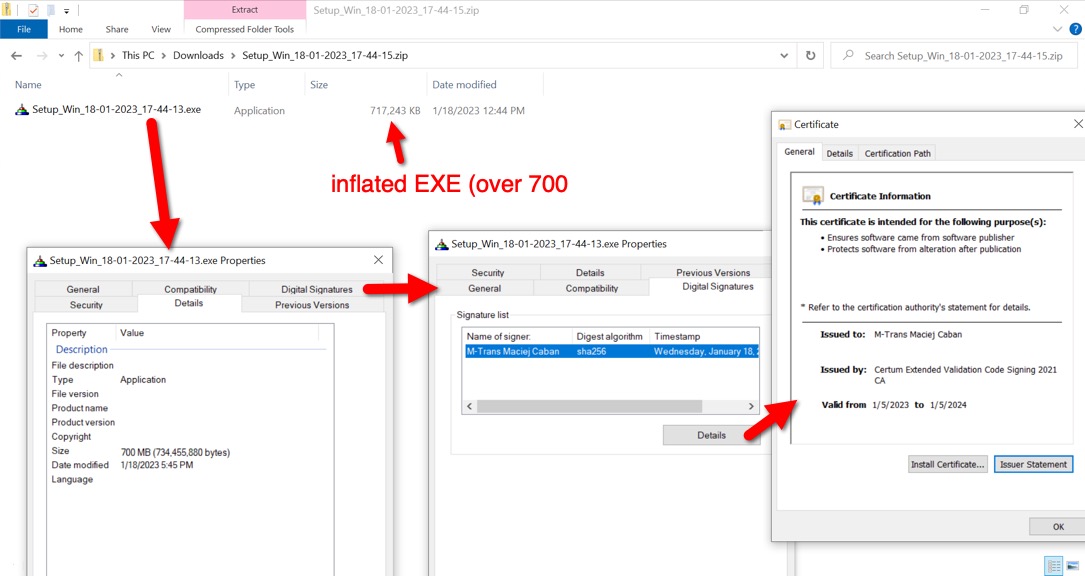
Shown above: Contents of downloaded zip archive are an inflated EXE with a digital signature.
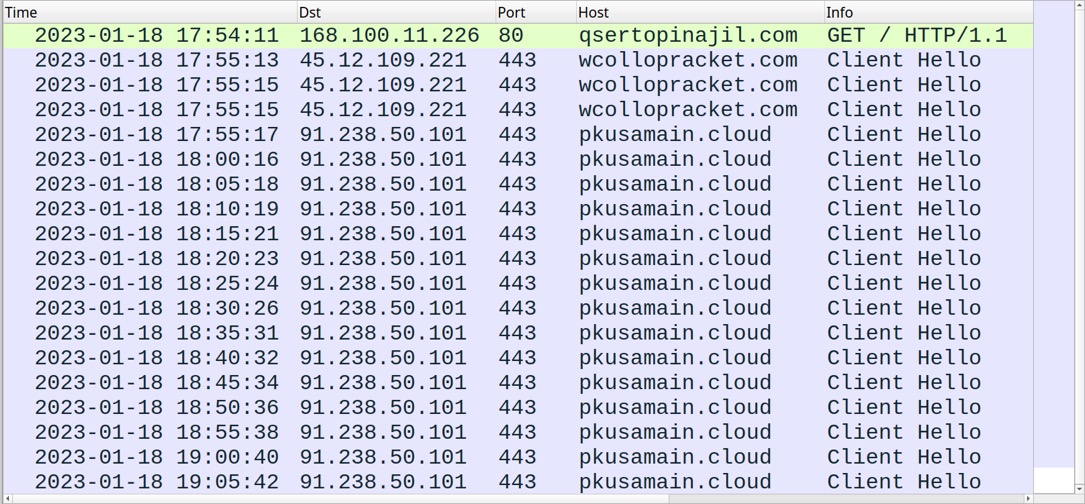
Shown above: Initial traffic from the IcedID infection filtered in Wireshark.
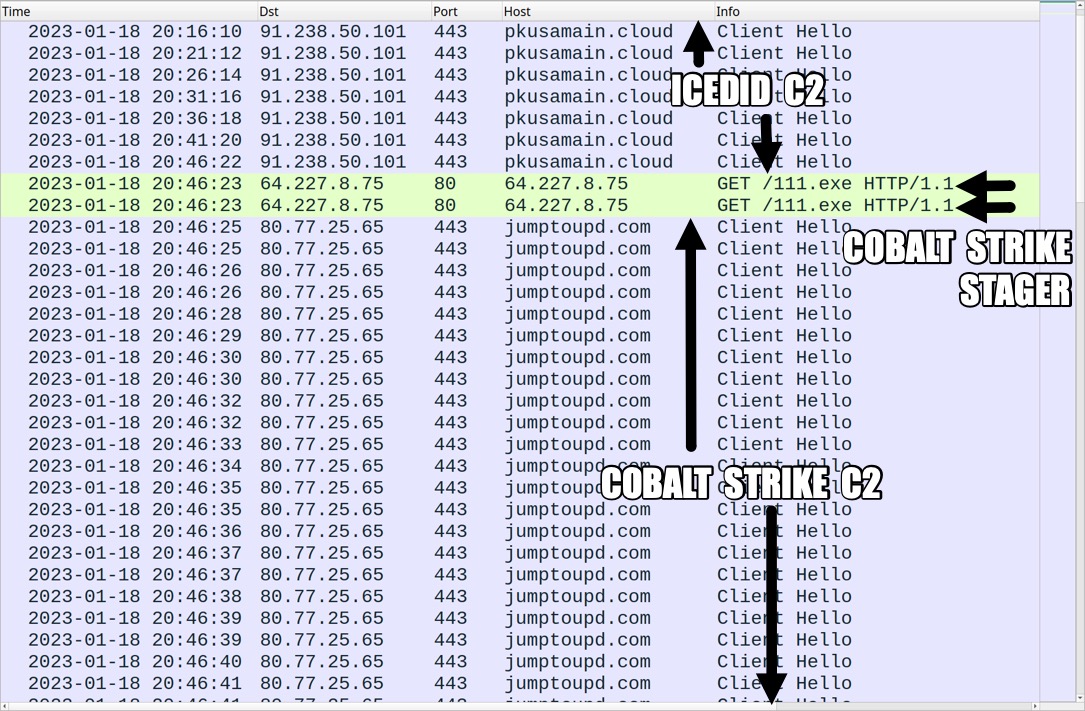
Shown above: Traffic for the Cobalt Strike stager and Cobalt Strike C2 filtered in Wireshark.
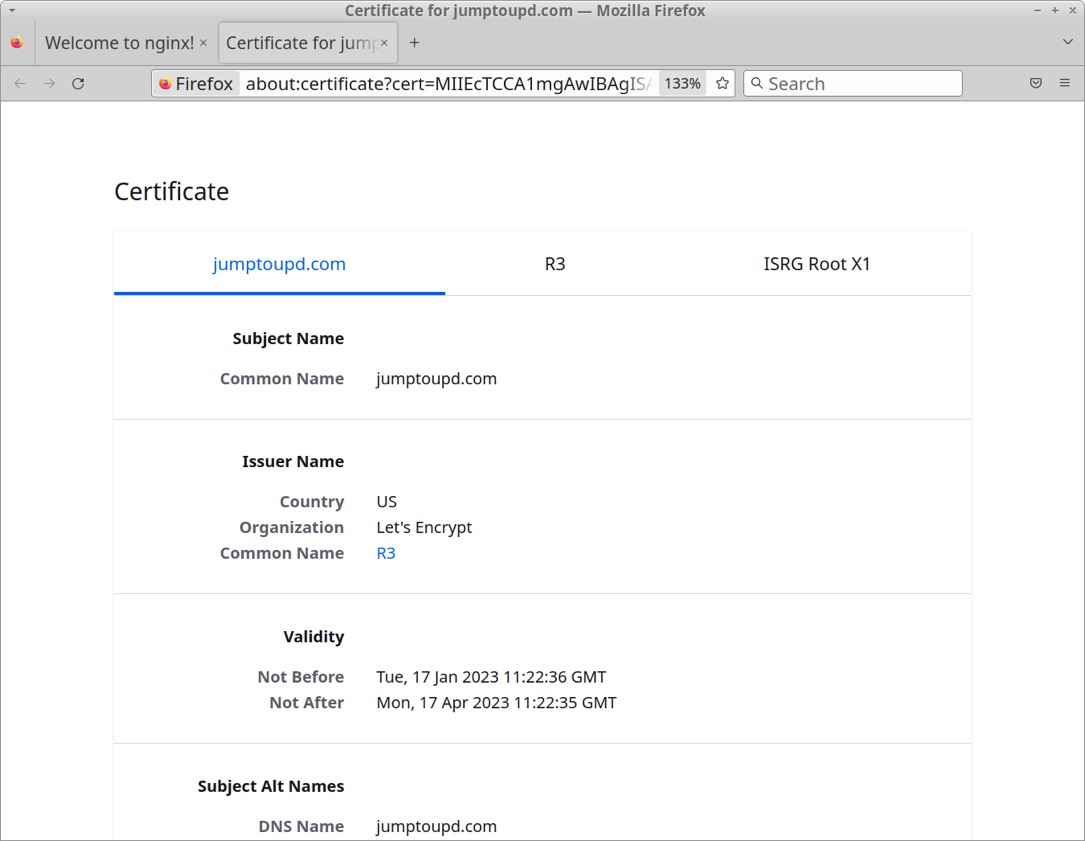
Shown above: Certificate issuer data for the Cobalt Strike server shows it was likely set up yesterday (2023-01-17).
2023-01-18 (WEDNESDAY) - GOOGLE AD --> FAKE LIBRE OFFICE PAGE --> ICEDID (BOKBOT) --> COBALT STRIKE GOOGLE AD: - hxxps[:]//www.googleadservices[.]com/pagead/aclk?sa=L&ai=DChcSEwjg5sW41dH8AhW7FdQBHVHXDj0YABACGgJvYQ&ae=2&ohost=www.google.com &cid=CAASJeRoAcUhHktCQP1pFzLdaNJqTQfzHfDuB093QYvylt_SqYex4Pw&sig=AOD64_1RdayVj2gQNVLrJG7CAo_9zDJFbg&q&adurl&ved=2ahUKEwju1L6 41dH8AhVYk2oFHQYYBO0Q0Qx6BAgGEAE FAKE LIBRE OFFICE PAGE: - hxxps[:]//wvv-llbreofflce.top/download/download-libreoffice/?gclid=EAIaIQobChMI4ObFuNXR_AIVuxXUAR1R1w49EAAYASAAEgJBePD_BwE URL FOR ICEDID MALWARE DOWNLOAD: - hxxps[:]//firebasestorage.googleapis[.]com/v0/b/poised-conduit-371717.appspot.com/o/fsSaijoYHM%2F Setup_Win_18-01-2023_17-47-34.zip?alt=media&token=d916c991-feab-4544-acd7-2f3dd85bb6d7 OTHER GOOGLE ADS FOR FAKE LIBREOFFICE PAGES PUSHING AURORA STEALER: - hxxps[:]//www.googleadservices[.]com/pagead/aclk?sa=L&ai=DChcSEwjg5sW41dH8AhW7FdQBHVHXDj0YABADGgJvYQ&ae=2&ohost=www.google.com &cid=CAASJeRoAcUhHktCQP1pFzLdaNJqTQfzHfDuB093QYvylt_SqYex4Pw&sig=AOD64_0zee5mp3biEcnieV15oHlKYR4Okg&q&adurl&ved=2ahUKEwju1L6 41dH8AhVYk2oFHQYYBO0Q0Qx6BAgIEAE - hxxps[:]//lidraofflce[.]com/?gclid=EAIaIQobChMI4ObFuNXR_AIVuxXUAR1R1w49EAAYAiAAEgJ8WPD_BwE - hxxps[:]//lidraofflce[.]com/bsdg/file.php - hxxps[:]//obsqroject[.]com/LibreOffice_7.4.4_Win_x64.exe <-- obsqroject[.]com off-line, so this doesn't work - hxxps[:]//www.googleadservices[.]com/pagead/aclk?sa=L&ai=DChcSEwjg5sW41dH8AhW7FdQBHVHXDj0YABABGgJvYQ&ae=2&ohost=www.google.com &cid=CAASJeRoAcUhHktCQP1pFzLdaNJqTQfzHfDuB093QYvylt_SqYex4Pw&sig=AOD64_2ggq6KzYQxUQUxt5I7vsNZy07V0g&q&adurl&ved=2ahUKEwju1L6 41dH8AhVYk2oFHQYYBO0Q0Qx6BAgHEAE - hxxps[:]//llbroofice[.]com/?gclid=EAIaIQobChMI4ObFuNXR_AIVuxXUAR1R1w49EAAYAyAAEgJQd_D_BwE - hxxps[:]//llbroofice[.]com/bsfg/file.php - hxxps[:]//obsqroject[.]com/LibreOffice_7.4.4_Win_x64.exe <-- obsqroject[.]com off-line, so this doesn't work DOWNLOADED ZIP AND EXTRACTED EXE: - SHA256 hash: 7fa1fbd2c625269c408d515a7f7a2289e19f5f5d3cef46a96300212071215649 - File size: 994,496 bytes - File name: Setup_Win_18-01-2023_17-44-15.zip - File type: Zip archive data, at least v2.0 to extract, compression method=deflate - File location: hxxps[:]//firebasestorage.googleapis[.]com/v0/b/poised-conduit-371717.appspot.com/o/ fsSaijoYHM%2FSetup_Win_18-01-2023_17-47-34.zip?alt=media&token=d916c991-feab-4544-acd7-2f3dd85bb6d7 - File description: File downloaded from fake Libre Office page - SHA256 hash: 030e7b73e8d7bb187183f3087b8ec5756a8c71698f198754cf5299c86e044199 - File size: 734,455,880 bytes - File name: Setup_Win_18-01-2023_17-44-13.exe - File type: PE32+ executable (GUI) x86-64, for MS Windows - File description: Inflated 64-bit EXE for IcedID installer, extracted from the above zip archive - SHA256 hash: bd67e49c2ca15156c54956655928723063eca5b4d90ae22dd6ce1029ba596b35 - File size: 453,896 bytes - File description: Above IcedID installer EXE, carved to remove all the null-byte padding FILES FROM AN INFECTION: - SHA256 hash: 40a5055e4095e65d0daec0085dcc769bae623e31ad514d767bb4a9ee03d5d894 - File size: 1,376,003 bytes - File location: hxxp[:]//qsertopinajil[.]com/ - File type: gzip compressed data, was "Tray.txt", from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 4391883 - File description: Gzip binary retrieved by the IcedID downloader - SHA256 hash: 509628d0ce1f30b6ce77aa484fb687aa23fa9d7ee73ed929e149eee354b3a3b0 - File size: 352,906 bytes - File location: C:\Users\[username]\AppData\Roaming\CradleEdge\license.dat - File type: data - File description: Data binary used to run persistent IcedID DLL - SHA256 hash: 66d0b38ee38559a6e0a09b9c54d647b9dbb40457c8b6d566fad9a5920622b527 - File size: 1,022,344 bytes - File location: C:\Users\[username]\AppData\Roaming\[username]\[username]\Ecriid4.dll - File type: PE32+ executable (DLL) (console) x86-64, for MS Windows - File description: 64-bit DLL for persistent IcedID infection - Run method: rundll32.exe [filename],init --icib="[path to license.dat]" - SHA256 hash: cedf2f478d0acc217522682a10f37c28894733f15f80df85333c7894043dcd98 - File size: 955,392 bytes - File location: hxxp[:]//64.227.8[.]75/111.exe - File location: C:\Users\[username]\AppData\Local\Temp\[6 random characters].exe - File type: PE32+ executable (GUI) x86-64, for MS Windows - File description: 64-bit EXE stager for Cobalt Strike FAKE LIBRE OFFICE WEBSITE: - 46.173.218[.]229 port 443 - wvv-llbreofflce[.]top - HTTPS traffic ZIP DOWNLOAD: - hxxps[:]//firebasestorage.googleapis[.]com/v0/b/poised-conduit-371717.appspot.com/o/fsSaijoYHM%2F Setup_Win_18-01-2023_17-47-34.zip?alt=media&token=d916c991-feab-4544-acd7-2f3dd85bb6d7 ICEDID TRAFFIC: - 168.100.11[.]226 port 80 - qsertopinajil[.]com - GET / - 45.12.109[.]221 port 443 - wcollopracket[.]com - HTTPS traffic - 91.238.50[.]101 port 443 - pkusamain[.]cloud - HTTPS traffic COBALT STRIKE TRAFFIC: - 64.227.8[.]75 port 80 - 64.227.8[.]75 - GET /111.exe - 80.77.25[.]65 port 443 - jumptoupd[.]com - HTTPS traffic
Click here to return to the main page.
