30 DAYS OF FORMBOOK: DAY 2, TUESDAY 2023-06-06 - "CG62"
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- This the is 2nd of 30 infection runs on new Formbook samples during the next month or two.
- Today's sample is from a .rar archive submitted to VirusTotal on Tuesday 2023-06-06.
ASSOCIATED FILES:
- 2023-06-06-IOCs-for-Formbook-infection.txt.zip 2.5 kB (2,494 bytes)
- 2023-06-06-Formbook-infection.pcap.zip 12.0 MB (11,986,144 bytes)
- 2023-06-06-Formbook-malware-and-artifacts.zip 1.4 MB (1,379,425 bytes)
IMAGES
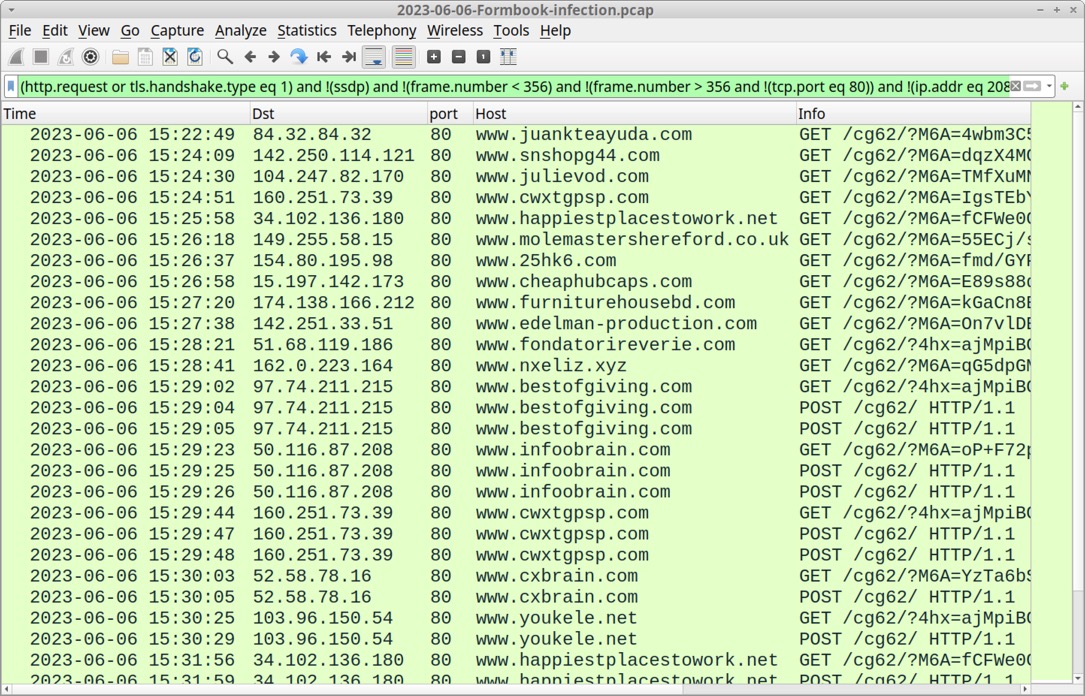
Shown above: Traffic from the infection filtered in Wireshark.
30 DAYS OF FORMBOOK: DAY 2, TUESDAY 2023-06-06 - "CG62"
INFECTION CHAIN:
- Unknown vector, possibly distributed as email attachment.
FORMBOOK SAMPLE:
- SHA256 hash: 51ae5b8b509da891381e9a177d6737ecef23758a78243cb3383d69c6c304f2c8
- File size: 679,171 bytes
- File name: [unknown]
- File type: RAR archive data, v5
- File description: RAR archive containing Formbook EXE
- SHA256 hash: 126716d242524dc742e3f6ac7c548c879501788d74f9280a2214594da270acaf
- File size: 763,904 bytes
- File name: PO CP23-0132_pdf.exe
- Persistent file location: C:\Program Files (x86)\N0fm\nhullv40b8x.exe
- File type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
- File description: Formbook EXE using a database-cylinder icon
- Creation Time: 2023-06-06 01:01:12 UTC
FORMBOOK PERSISTENCE:
- Windows Registry key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Value name: GLHPQT0P
- Value type: REG_SZ
- Value Data: C:\Program Files (x86)\N0fm\nhullv40b8x.exe
DATA STORED FOR EXFILTRATION TO FORMBOOK C2 SERVER:
- C:\Users\[username]\AppData\Roaming\-Q68N5E3\-Q6log.ini - 0 bytes
- C:\Users\[username]\AppData\Roaming\-Q68N5E3\-Q6logim.jpeg - 491,564 bytes (screenshot of desktop)
- C:\Users\[username]\AppData\Roaming\-Q68N5E3\-Q6logrc.ini - 1952 bytes (Outlook Recovery)
- C:\Users\[username]\AppData\Roaming\-Q68N5E3\-Q6logri.ini - 40 bytes (Iexplore Recovery)
- C:\Users\[username]\AppData\Roaming\-Q68N5E3\-Q6logrv.ini - 40 bytes (__Vault Recovery)
- Note: All the above files were deleted after data exfiltation, except for first file at 0 bytes named -Q6log.ini
FORMBOOK HTTP GET AND POST REQUESTS:
- GET /cg62/?[string of alphanumeric characters with the following mixed in: = _ + and /]
- POST /cg62/
FORMBOOK DOMAINS THAT DID NOT RESOLVE:
- DNS query for www.cl-apple[.]online - response: No such name
- DNS query for www.efefamount[.]buzz - response: No such name
- DNS query for www.ibm-crc[.]com - response: No such name
- DNS query for www.itmcnews[.]africa - no response from DNS server
- DNS query for www.kodfest[.]click - no response from DNS server
- DNS query for www.ojaymart[.]africa - no response from DNS server
- DNS query for www.twinstarconsulting[.]net - response: No such name
- DNS query for www.wan-x[.]africa - no response from DNS server
FORMBOOK DOMAINS THAT RESOLVED, BUT NO CONNECTION TO SERVER:
- 104.253.133[.]122 port 80 - www.ceritabintang[.]com - TCP SYN segments only, no response or RST from server
- 20.121.31[.]134 port 80 - www.conradrawford[.]click - TCP SYN segments only, no response or RST from server
FORMBOOK GET URLS ONLY:
- Note: These appear to be parked domain pages or legitimate websites.
- 34.102.136[.]180 port 80 - www.24hr4x4towing[.]com
- 34.117.168[.]233 port 80 - www.americanhorseauctions[.]com
- 194.58.112[.]174 port 80 - www.aticco[.]ru
- 199.34.228[.]74 port 80 - www.blendoregon[.]com
- 91.195.240[.]94 port 80 - www.cannabispowerrelief[.]com
- 3.64.163[.]50 port 80 - www.casimia[.]com
- 34.102.136[.]180 port 80 - www.createaconference[.]com
- 43.131.28[.]236 port 80 - www.ffyjbn[.]live
- 51.68.119[.]186 port 80 - www.fondatorireverie[.]com
- 34.102.136[.]180 port 80 - www.homehuntersny[.]com
- 84.32.84[.]32 port 80 - www.juankteayuda[.]com
- 84.32.84[.]32 port 80 - www.lapetitesaison[.]com
- 81.17.29[.]148 port 80 - www.malemassagebroadstairs[.]co[.]uk
- 23.227.38[.]74 port 80 - www.nextgen-gaming[.]co[.]uk
- 172.67.189[.]62 port 80 - www.prosperex[.]net
- 192.187.111[.]222 port 80 - www.travellingbookes[.]co[.]uk
DOMAINS USING FORMBOOK GET AND POST URLS:
- Note: These appear to be parked domain pages or legitimate websites.
- 154.80.195[.]98 port 80 - www.25hk6[.]com **
- 37.97.224[.]106 port 80 - www.aquaconsoil2023[.]com **
- 97.74.211[.]215 port 80 - www.bestofgiving[.]com **
- 15.197.142[.]173 port 80 - www.cheaphubcaps[.]com
- 160.251.73[.]39 port 80 - www.cwxtgpsp[.]com **
- 52.58.78[.]16 port 80 - www.cxbrain[.]com
- 142.251.33[.]51 port 80 - www.edelman-production[.]com ** !!
- 174.138.166[.]212 port 80 - www.furniturehousebd[.]com
- 34.102.136[.]180 port 80 - www.happiestplacestowork[.]net
- 50.116.87[.]208 port 80 - www.infoobrain[.]com **
- 104.247.82[.]170 port 80 - www.julievod[.]com
- 34.102.136[.]180 port 80 - www.lpnnurseprograms[.]com
- 149.255.58[.]15 port 80 - www.molemastershereford[.]co[.]uk **
- 162.0.223[.]164 port 80 - www.nxeliz[.]xyz **
- 144.91.110[.]16 port 80 - www.pizzatoon[.]net **
- 142.250.114[.]121 port 80 - www.snshopg44[.]com
- 160.202.70[.]27 port 80 - www.yiehu[.]com **
- 103.96.150[.]54 port 80 - www.youkele[.]net
** - Full stolen data (encoded) sent through HTTP POST request.
!! - www.edelman-production[.]com is a Google-hosted site that seems to have been used for Formbook as early as 2023-03-23.
This was the last Formbook-generated HTTP POST request seen during this infection run, and the response headers
indicate this server accepted the stolen data. But when I later checked the site in a web browser, it returned a
Google 404 error page "The requested URL was not found on this server. That's all we know."
Click here to return to the main page.
