30 DAYS OF FORMBOOK: DAY 5, FRIDAY 2023-06-09 - GULOADER FOR FORMBOOK "V16R"
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- This the is 5th of 30 infection runs on recent Formbook samples.
- Today's sample is a GuLoader version of Frombook that's been active since earlier this week.
FINDINGS:
- It looks like Formbook steals login credentials stored on the Firefox web browser (still not for the current version of Microsoft Edge)
ASSOCIATED FILES:
- 2023-06-09-IOCs-for-GuLoader-Formbook-infection.txt.zip 2.5 kB (2,507 bytes)
- 2023-06-09-GuLoader-Formbook-infection.pcap.zip 8.3 MB (8,345,410 bytes)
- 2023-06-09-GuLoader-Formbook-malware-and-artifacts.zip 4.0 MB (4,047,690 bytes)
IMAGES
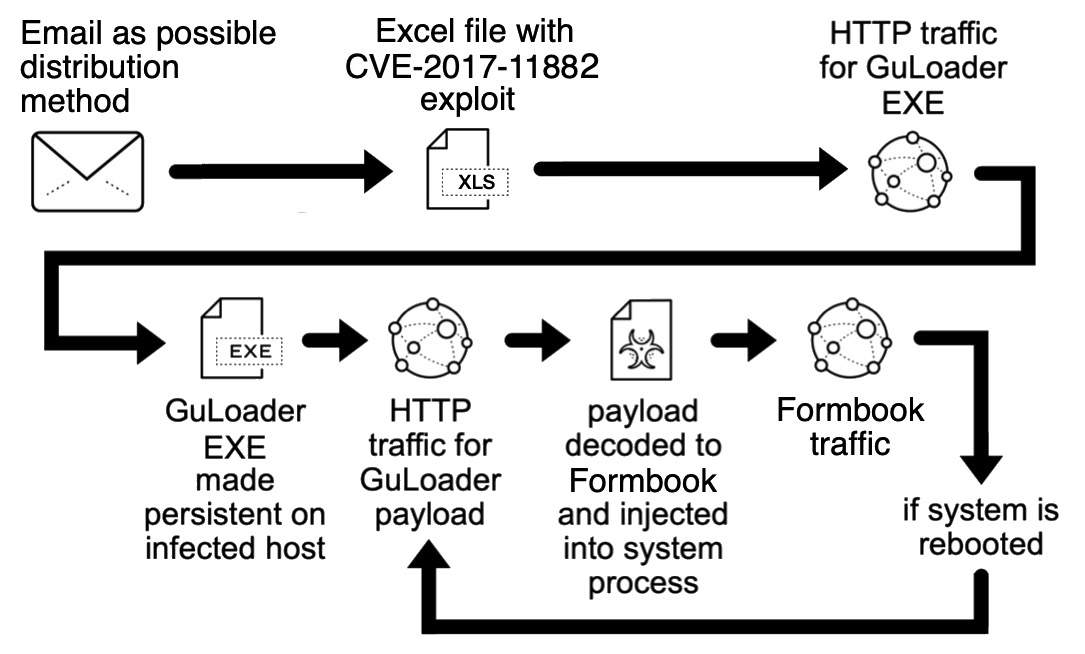
Shown above: Chain of events for this GuLoader Formbook infection.
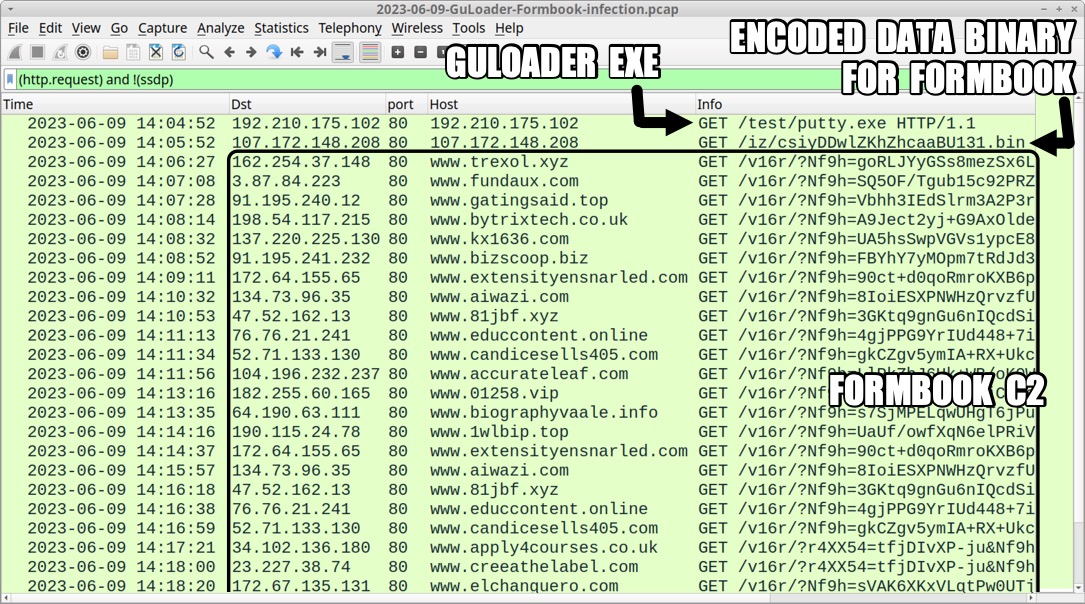
Shown above: Traffic from the infection filtered in Wireshark.
30 DAYS OF FORMBOOK: DAY 5, FRIDAY 2023-06-09 - GULOADER FOR FORMBOOK "V16R" INFECTION CHAIN: - Unknown vector, possibly email --> Excel file with cve-2017-11882 exploit --> URL --> GuLoader --> URL --> encoded/encrypted data binary --> Formbook infection NOTES: - This GuLoader sample was made persistent like a Formbook infection, but the GuLoader EXE always retrieves the data binary every time a victim restarts or logs back into the infected Windows host. MALWARE/ARTIFACTS: - SHA256 hash: 2dfdbe81ec48898307cf9d5373df1a1e0eef3d9fd8560726cedf7e68a9dfc19e - File size: 2,112,512 bytes - File name: unknown file name - File type: Composite Document File V2 Document, created by Microsoft Excel, 2023-06-03 - File description: Excel file with CVE-2017-11882 exploit - SHA256 hash: 73ce02f6b7c4c5109af4ad501aa9206bbfa5cf32bb8276ad06887c95279c907d - File size: 1,042,320 bytes - File location: hxxp[:]//192.210.175[.]102/test/putty.exe - File type: PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive - File description: Retreived by the above Excel file, this is a GuLoader EXE for Formbook - Creation Time: 2018-12-15 22:24:22 UTC (possibly fake timestamp) - SHA256 hash: 222edd15c85539189b1f76544b5ec1f13ec65eb0c1d2b648c84aa234b429ebdc - File size: 189,504 bytes - File location: hxxp[:]//107.172.148[.]208/iz/csiyDDwlZKhZhcaaBU131.bin - File type: Data - File description: encoded/encrypted data binary used by this GuLoader sample for Formbook - SHA256 hash: f07c4fba3fb23b294bfa8ae28753df56e2a4a61bc15e5305454a8a6d72ab919a - File size: 1,042,320 bytes - Persistent file location: C:\Program Files (x86)\Svhp0pp\exuff8l.exe - File type: PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive - File description: Persistent EXE for this infection - Note: File does not execute, giving the NSIS Error: Installer integrity check failed. GULOADER FOR FORMBOOK PERSISTENCE: - Windows Registry key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run - Value name: HBCXSZ9HU2 - Value type: REG_SZ - Value Data: C:\Program Files (x86)\Svhp0pp\exuff8l.exe DATA STORED FOR EXFILTRATION TO FORMBOOK C2 SERVER: - C:\Users\[username]\AppData\Roaming\ON1P4UQB\ON1log.ini - 0 bytes - C:\Users\[username]\AppData\Roaming\ON1P4UQB\ON1logim.jpeg - 481,720 bytes (screenshot of desktop) - C:\Users\[username]\AppData\Roaming\ON1P4UQB\ON1logrc.ini - 1,952 bytes (Outlook Recovery) - C:\Users\[username]\AppData\Roaming\ON1P4UQB\ON1logri.ini - 40 bytes (Iexplore Recovery) - C:\Users\[username]\AppData\Roaming\ON1P4UQB\ON1logrv.ini - 40 bytes (__Vault Recovery) - Note: All the above files were deleted after data exfiltation, except for first file at 0 bytes. XLS FILE RETRIEVES GULOADER EXE: - hxxp[:]//192.210.175[.]102/test/putty.exe GULOADER EXE RETREIVES ENCODED BINARY FOR FORMBOOK: - hxxp[:]//107.172.148[.]208/iz/csiyDDwlZKhZhcaaBU131.bin FORMBOOK HTTP GET AND POST REQUESTS: - GET /v16r/?[string of alphanumeric characters with the following mixed in: = _ + and /] - POST /v16r/ DOMAINS THAT DID NOT RESOLVE: - DNS query for www.bestproductsmarkets[.]com - no response from DNS server - DNS query for www.fashionmomentswithniz[.]africa - no response from DNS server - DNS query for www.kindredself[.]store - no response from DNS server - DNS query for www.nairaptc[.]africa - no response from DNS server - DNS query for www.thetigersstory[.]africa - no response from DNS server - DNS query for www.woox[.]africa - no response from DNS server - DNS query for www.brigghtbrooker[.]online - response: No such name - DNS query for www.curiocouture[.]uk - response: No such name - DNS query for www.fjinjue[.]com - response: No such name - DNS query for www.hmv5w[.]com - response: No such name - DNS query for www.irsprograms[.]com - response: No such name - DNS query for www.avhpet[.].com - no IP returned from DNS server - DNS query for www.sidelpos[.]net - resolved to 127.0.0.1 DOMAINS THAT RESOLVED, BUT NO CONNECTION TO SERVER: - 8.218.85[.]75 port 80 - www.cfplhys16[.]shop - TCP SYN segments only, no response or RST from server DOMAINS USED FOR FORMBOOK GET REQUESTS: - Note: These appear to be legitimate websites or parked domain pages. - www.1wlbip.top - www.3400-sw-27th-ave[.]com - www.apply4courses[.]co[.]uk - www.basaraninsaatemlak[.]com - www.biographyvaale[.]info - www.bizscoop[.]biz - www.blackfridaygundeal[.]com - www.bytrixtech[.].co[.]uk - www.cqbyzv[.]top - www.creeathelabel[.]com - www.elchanguero[.]com - www.fuckcolorado[.]com - www.fundaux[.]com - www.gatingsaid[.]top - www.gemgamut[.]com - www.h74c[.]com - www.kx1636[.]com - www.legacyifg[.]com - www.lotto-horse[.]com - www.pacientescalificados[.]com DOMAINS USED FOR FORMBOOK GET AND POST REQUESTS: - Note: These appear to be legitimate websites or parked domain pages. - www.01258[.]vip ** - www.3415588[.]com - www.81jbf[.]xyz - www.accurateleaf[.]com - www.aiwazi[.]com ** - www.bei-mei[.]com - www.bonafidewhisky[.]net - www.candicesells405[.]com - www.clubeconcept[.]com ** - www.comtetratech[.]com - www.creed[.]foundation - www.educcontent[.]online - www.extensityensnarled[.]com - www.felesten[.]com ** - www.trexol[.]xyz ** ** - Full stolen data (encoded) sent through HTTP POST request.
Click here to return to the main page.
