30 DAYS OF FORMBOOK: DAY 6, SATURDAY 2023-06-10 - "SN84"
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- This the is 6th of 30 infection runs on recent Formbook samples.
ASSOCIATED FILES:
- 2023-06-10-Formbook-malspam.eml.zip 295 kB (295,128 bytes)
- 2023-06-10-IOCs-for-Formbook-infection.txt.zip 2.0 kB (1,951 bytes)
- 2023-06-10-Formbook-infection.pcap.zip 5.8 MB (5,841,885 bytes)
- 2023-06-10-Formbook-malware-and-artifacts.zip 514 kB (514,104 bytes)
IMAGES
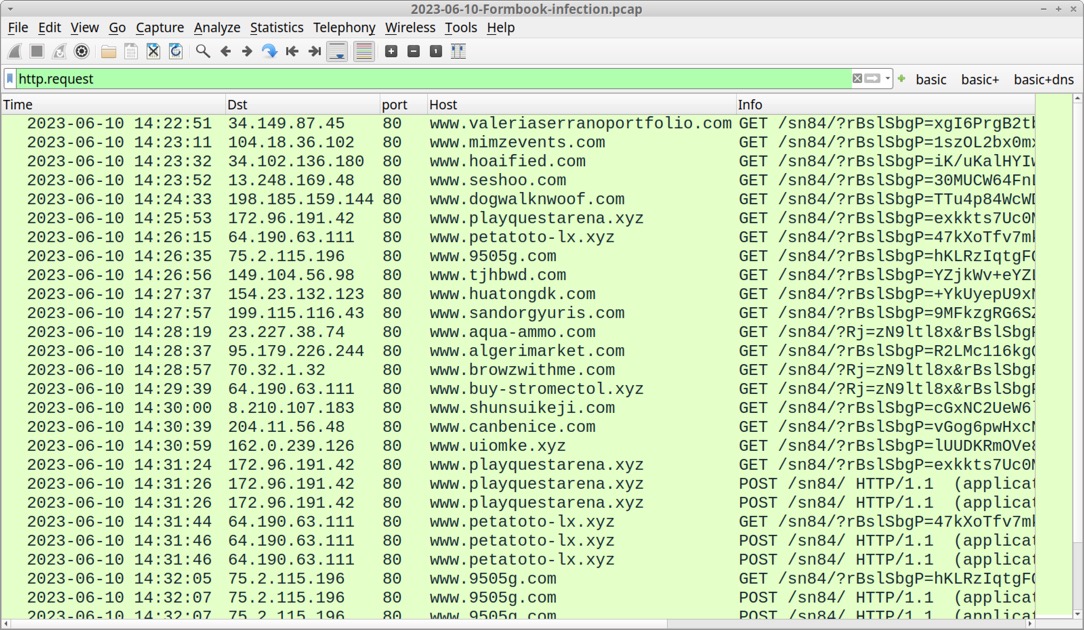
Shown above: Traffic from the infection filtered in Wireshark.
30 DAYS OF FORMBOOK: DAY 6, SATURDAY 2023-06-10 - "SN84" INFECTION CHAIN: - Email --> attached RAR archive --> extracted Formbook EXE --> victim runs Formbook EXE NOTES: - I have a copy of an email from Friday 2023-06-09 distributing this Formbook malware sample. - I ran this infection from WiFi at a pulic location, and probably all of the Formbook C2 traffic was blocked by a firewall. MALWARE/ARTIFACTS: - SHA256 hash: f95430cc24ddfcbbdacf43ea9616e0f76efa9963412f3825cef0f994b1663896 - File size: 255,633 bytes - File name: Agrubu 06092023.pdf.lzh - File type: RAR archive data, v5 - File description: RAR archive containing Formbook EXE - SHA256 hash: 411866fa8b5f27b7254d3bdc1b152c33e8a6420ae444f5242023df50f06b2c21 - File size: 478,297 bytes - File name: Agrubu 06092023.pdf.exe - Persistent file location: C:\Program Files (x86)\Fshlh\hbmhvfj00nuthvhx.exe - File type: PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive - File description: Windows EXE for Formbook version 4.1 FORMBOOK PERSISTENCE: - Windows Registry key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run - Value name: W0HLEFGXGVE - Value type: REG_SZ - Value Data: C:\Program Files (x86)\Fshlh\hbmhvfj00nuthvhx.exe DATA STORED FOR EXFILTRATION TO FORMBOOK C2 SERVER: - C:\Users\[username]\AppData\Roaming\L-LA93RA\L-Llog.ini - 0 bytes - C:\Users\[username]\AppData\Roaming\L-LA93RA\L-Llogim.jpeg (screenshot of desktop) - C:\Users\[username]\AppData\Roaming\L-LA93RA\L-Llogrc.ini (Outlook Recovery) - C:\Users\[username]\AppData\Roaming\L-LA93RA\L-Llogrf.ini (Firefox Recovery) - C:\Users\[username]\AppData\Roaming\L-LA93RA\L-Llogrg.ini (Chrome Recovery) - C:\Users\[username]\AppData\Roaming\L-LA93RA\L-Llogri.ini (Iexplore Recovery) - C:\Users\[username]\AppData\Roaming\L-LA93RA\L-Llogrv.ini (__Vault Recovery) - Note: All the above files were deleted after data exfiltation, except for first file at 0 bytes. FORMBOOK HTTP GET AND POST REQUESTS: - GET /sn84/?[string of alphanumeric characters with the following mixed in: = _ + and /] - POST /sn84/ DOMAINS THAT DID NOT RESOLVE: - DNS query for www.ant-tron[.]com - no response from DNS server - DNS query for www.turkiyebihaber[.]net - no response from DNS server - DNS query for www.esryhs[.]xyz - response: No such name - DNS query for www.nmc380[.]top - response: No such name - DNS query for www.piluyi[.].com - response: No such name - DNS query for www.singularity-labs[.]xyz - response: No such name - DNS query for www.t3-6qf23[.]xyz - response: No such name - DNS query for www.tristone13th[.]shop - response: No such name - DNS query for www.24zps[.]com - no IP returned from DNS server DOMAINS USED FOR FORMBOOK GET REQUESTS: - Note: These appear to be legitimate websites or parked domain pages. - www.959-25[.]review - www.algerimarket[.]com - www.aqua-ammo[.]com - www.breakingbarriersglobal[.]com - www.browzwithme[.]com - www.buy-stromectol[.]xyz - www.canbenice[.]com - www.cdnfiles[.]website - www.dogwalknwoof[.]com - www.fleshlierwickerwork[.]com - www.goodsneaker[.]online - www.journeyto5[.]com - www.kpsseguros[.]com - www.merdamao[.]com - www.mimzevents[.]com - www.nichequilt[.]com - www.seshoo[.]com - www.shunsuikeji[.]com - www.teamdaigle[.]com - www.valeriaserranoportfolio[.]com - www.zncdetailing[.]com DOMAINS USED FOR FORMBOOK GET AND POST REQUESTS: - Note: These appear to be legitimate websites or parked domain pages. - www.9505g[.]com ** - www.archermag[.]com ** - www.clubordinal[.]xyz ** - www.hoaified[.]com ** - www.huatongdk[.]com ** - www.ihopapo[.]com ** - www.indialgbtq[.]com ** - www.kareemandahmed[.]net ** - www.petatoto-lx[.]xyz ** - www.playquestarena[.]xyz ** - www.sandorgyuris[.]com ** - www.tjhbwd[.]com ** - www.uiomke[.]xyz ** - www.xn--12c4dfj4gtc[.]net ** ** - Full stolen data (encoded) sent through HTTP POST request (all of them)
Click here to return to the main page.
