30 DAYS OF FORMBOOK: DAY 9, TUESDAY 2023-06-13 - XLOADER "MD8S"
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- This the is 9th of 30 infection runs on recent Formbook samples.
- Today's sample is a variant of Formbook called XLoader, but post-infection activity is nearly identical to Formbook.
ASSOCIATED FILES:
- 2023-06-13-IOCs-for-XLoader-infection.txt.zip 2.1 kB (2,117 bytes)
- 2023-06-13-XLoader-infection-traffic.pcap.zip 4.6 MB (4,587,175 bytes)
- 2023-06-13-XLoader-malware-and-artifacts.zip 587 kB (586,614 bytes)
IMAGES
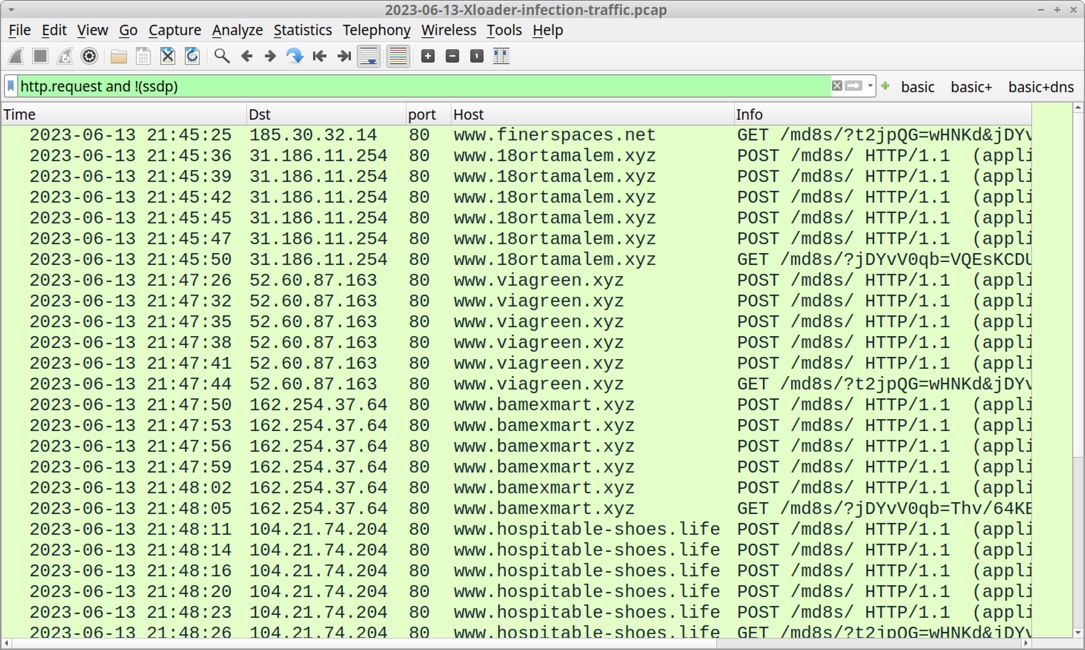
Shown above: Traffic from the infection filtered in Wireshark.
30 DAYS OF FORMBOOK: DAY 9, TUESDAY 2023-06-13 - XLOADER "MD8S" INFECTION CHAIN: - unknown source --> ISO disk image --> XLoader EXE NOTES: - XLoader is a newer variant of Formbook that first appeared in 2020, originally reported as a successor to Formbook -- https://research.checkpoint.com/2021/top-prevalent-malware-with-a-thousand-campaigns-migrates-to-macos/ - But I still find newly-submitted samples of Formbook version 4.1 submitted to VirusTotal on a near-daily basis. FINDINGS: - Formbook starts with HTTP GET requests for at least a few minutes, then HTTP POST requests for data exfiltration. - Except for 1 initial GET request, XLoader starts with POST requests after post-infection traffic starts. - Formbook stores data to be exfiltrated in a random folder created under C:\Users\[username]\AppData\Roaming. - During the XLoader infections I've tried, I have not yet found any data to be exfiltrated stored to disk. MALWARE/ARTIFACTS: - SHA256 hash: 81d5bdb550292a188ea1fbc1890aa730019275427b64620e1d115f376abbdd64 - File size: 1,245,184 bytes - File name: ESP670924.ISO - File type: UDF filesystem data (version 1.5) 'DESKTOP' - File description: File that mounts as a disk image - SHA256 hash: 7382318f5904040997bf14967bce3df6b323bf03901976df75a9b0e822dc5db8 - File size: 307,200 bytes - File name: ESP670924.exe - Persistent file location: C:\Program Files (x86)\T0ts\2pydjv0snwxt.exe - File type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows - Creation Time: 2023-06-12 11:24:14 UTC - File description: XLoader EXE contained in the above disk image PERSISTENCE: - Windows Registry key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run - Value name: HNIDVNPHKL - Value type: REG_SZ - Value Data: C:\Program Files (x86)\T0ts\2pydjv0snwxt.exe XLOADER HTTP GET AND POST REQUESTS: - GET /md8s/?[string of alphanumeric characters with the following mixed in: = _ + and /] - POST /md8s/ DOMAINS THAT DID NOT RESOLVE: - DNS query for www.df3pr[.]shop - response: No such name - DNS query for www.new-balkon-otdelka[.]site - response: No such name - DNS query for www.pymhn[.]top - response: No such name - DNS query for www.superslot50[.]app - response: No such name - DNS query for www - response: No such name DOMAINS USED FOR XLOADER GET REQUESTS ONLY: - Note: These appear to be legitimate websites or parked domain pages. - www.advisuninfotech[.]com - www.ainji3[.]space - www.alphaconqa[.]com - www.animeone[.]org - www.cjwj.vip - www.cmdhau8[.]com - www.finerspaces[.]net - www.forgivemy[.]life - www.gbxgh[.]club - www.getbevtoday[.]click - www.golajme[.]com - www.homeoftogetherness[.]com - www.hooppthames[.]com - www.investwiseehub[.]online - www.isst[.]info - www.iviaggi[.]blog - www.jedcvolj.bond - www.jglblr[.]org - www.kalevunited[.]com - www.lala8[.]top - www.messaggerienazionali[.]com - www.mudwoods[.]com - www.nachhaltig-steuern[.]info - www.novometedodigital[.]fun - www.pdfamazon[.]com - www.qtr954[.]top - www.sdrongfei[.]com - www.sis-b[.]com - www.spanishnoir[.]com - www.sportswpk[.]site - www.thebaewatch[.]com - www.weapon[.]wtf - www.yuinetwork[.]xyz DOMAINS USED FOR XLOADER GET AND POST REQUESTS: - Note: These appear to be legitimate websites or parked domain pages. - www.18ortamalem[.]xyz - www.aalesundapartment[.]online - www.afreeto[.]com - www.alessandrafausto[.]com - www.bamexmart[.]xyz - www.cracksoftwaresite[.]com - www.cyclonescreen[.]com - www.expaol[.]com - www.geoffregsiu[.]com - www.ggusocial[.]com - www.heritage-pnc[.]com - www.hospitable-shoes[.]life - www.ladookhotnikov[.]pro - www.mrfkzd[.]cfd - www.onenoteworkforceap[.]com - www.r-grenader-jackpot[.]lol - www.viagreen[.]xyz - www.wxuvvb[.]icu
Click here to return to the main page.
