30 DAYS OF FORMBOOK: DAY 17, WEDNESDAY 2023-06-21 - MODILOADER FOR XLOADER "NVP4"
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- This the is my 17th of 30 infection runs for recent Formbook activity.
ASSOCIATED FILES:
- 2023-06-21-IOCs-from-ModiLoader-for-XLoader-infection.txt.zip 2.2 kB (2,239 bytes)
- 2023-06-21-ModiLoader-for-XLoader-infection-traffic.pcap.zip 3.2 MB (3,233,943 bytes)
- 2023-06-21-ModiLoader-malware-and-artifacts.zip 1.6 MB (1,617,633 bytes)
IMAGES
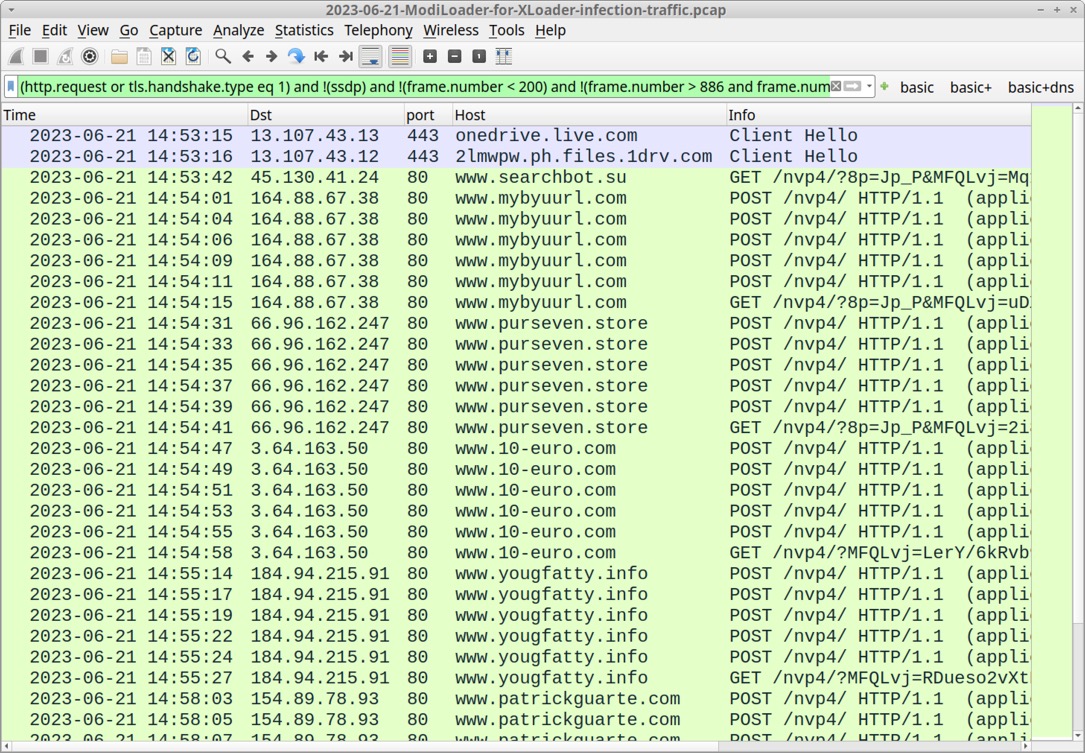
Shown above: Traffic from the infection filtered in Wireshark.
30 DAYS OF FORMBOOK: DAY 17, WEDNESDAY 2023-06-21 - ModiLoader for XLoader "NVP4"
INFECTION CHAIN:
- Email --> attached zip --> extracted ModiLoader EXE --> ModiLoader retrieves base64 text from OneDrive URL -->
XLoader traffic
NOTES:
- ModiLoader is also known as DBatLoader.
- XLoader is a variant of Formbook.
- For XLoader C2 traffic, HTTP POST requests start immediately after the initial C2 HTTP GET request.
- In regular Formbook C2 traffic, the HTTP POST request don't occur until after several C2 HTTP GET requests.
MALWARE/ARTIFACTS:
- SHA256 hash: 134cd98a7cab3ba472337573efdf9bac01ef4de46b5cfb406bbe0649c6525163
- File size: 631,173 bytes
- File name: [unknown]
- File type: Zip archive data, at least v2.0 to extract, compression method=deflate
- File description: Zip archive containing ModiLoader EXE
- SHA256 hash: c6b9351ebdc6c29c327f1c49af903664b8df0ebd221da40c02bfc6aba6a07663
- File size: 1,014,272 bytes
- File name: Purchase Order f.exe
- Persistent file location: C:\Users\Public\Libraries\Cprdqspg.bat
- File type: PE32 executable (GUI) Intel 80386, for MS Windows
- File description: ModiLoader EXE
- SHA256 hash: 954b9e659dc14b67b26f15ff8a96d1a53c4c24db50d023fbaa8acb4cb23cd73a
- File size: 668,872 bytes
- File name: 255_Cprdqspgool
- File location: hxxp[:]//onedrive.live[.]com/download?cid=E0CF7F9E6AAF27EF&resid=E0CF7F9E6AAF27EF%211543&
authkey=AGHKU9NONN82QJ4
- File type: Motorola S-Record; binary data in text format
- File description: Base64 text used by ModiLoader for XLoader
- Note: This file on its own is not malicious.
- SHA256 hash: 1d7e84a9706c9b8ce7c4ebc5ed908b43e5cd6c6a1280f2eefd9306efa5caa9bd
- File size: 226,712 bytes
- File location: C:\Program Files (x86)\Qn2cl\zh9l_rmxph58yfrp.exe
- File description: Copy of SndVol.exe (Microsoft Volume Mixer), a legitimate system file
- Note: This is not malicious.
MODILOADER FOR XLOADER PERSISTENCE:
- Windows Registry key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Value 0 name: Cprdqspg
- Value 0 type: REG_SZ
- Value 0 Data: C:\Users\Public\Cprdqspg.url
- Value 1 name: GPPH0RWH
- Value 1 type: REG_SZ
- Value 1 Data: C:\Program Files (x86)\Qn2cl\zh9l_rmxph58yfrp.exe
XLOADER HTTP GET AND POST REQUESTS:
- GET /nvp4/?[string of alphanumeric characters with the following mixed in: = _ + and /]
- POST /nvp4/
DOMAINS THAT DID NOT RESOLVE:
- DNS query for www.montazeran[.]net - no response from DNS server
- DNS query for www.nnncb[.]top - response: No such name
- DNS query for www.socialabs[.]site - response: No such name
- DNS query for www.genia-tori-ks[.]net - response: No such name
- DNS query for www.noprostatit[.]store - response: No such name
- DNS query for www.socialabs[.]site - response: No such name
- DNS query for www.itticards[.]com - response: No such name
- DNS query for www.printjust[.]online - response: No such name
DOMAINS THAT RESOLVED, BUT NO CONNECTION TO SERVER:
- port 80 - www.chicashentai[.]com - TCP SYN segments only, no response or RST from server
- port 80 - www.middleshanghai[.]com - TCP SYN segments only, no response or RST from server
- port 80 - www.youlian[.]fund - TCP SYN segments only, no response or RST from server
DOMAINS USED FOR XLOADER GET REQUESTS:
- Note: These appear to be legitimate websites or parked domain pages.
- www.5353405[.]com
- www.apidachicago[.]org
- www.familykitchen[.]ch
- www.free-enjoy[.]co[.]uk
- www.ivanhagen[.]com
- www.justremortgage[.]com
- www.k-outlets[.]com
- www.kastamonuhaberleri[.]xyz
- www.masteramericangarage[.]com
- www.ob219[.]com
- www.p2e[.]finance
- www.phootka[.]ru
- www.piaynemo[.]com
- www.pinwheeleffect[.]org
- www.rsvstudio[.]com
- www.searchbot[.]su
- www.seatandfeel[.]com
- www.siddhtechcreators[.]com
- www.smartrykvanniekerk[.]site
- www.steripartners[.]com
- www.verdolaga[.]net
- www.welldaze[.]com
- www.xdawo[.]com
- www.xn--jpochsseafood-fhb[.]com
DOMAINS USED FOR XLOADER GET AND POST REQUESTS:
- Note: These appear to be legitimate websites or parked domain pages.
- www.10-euro[.]com
- www.automotiveparts-store[.]com
- www.brainbookgroup[.]com
- www.certud[.]fun
- www.iran2022[.]info
- www.klbertc[.]com
- www.mybyuurl[.]com
- www.patrickguarte[.]com
- www.promarproperty[.]com
- www.purseven[.]store
- www.travelsandphotos[.]com
- www.wewantabreak[.]com
- www.yougfatty[.]info
Click here to return to the main page.
