30 DAYS OF FORMBOOK: DAY 23, TUESDAY 2023-06-27 - CVE-2017-11882 RTF ".DOC" --> "FGH2"
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- This the is my 23rd of 30 infection runs for recent Formbook activity.
ASSOCIATED FILES:
- 2023-06-27-IOCs-for-Formbook-infection.txt.zip 2.0 kB (1,986 bytes)
- 2023-06-27-Formbook-infection-traffic.pcap.zip 2.5 MB (2,538,167 bytes)
- 2023-06-27-Formbook-malware-and-artifacts.zip 545 kB (545,062 bytes)
IMAGES
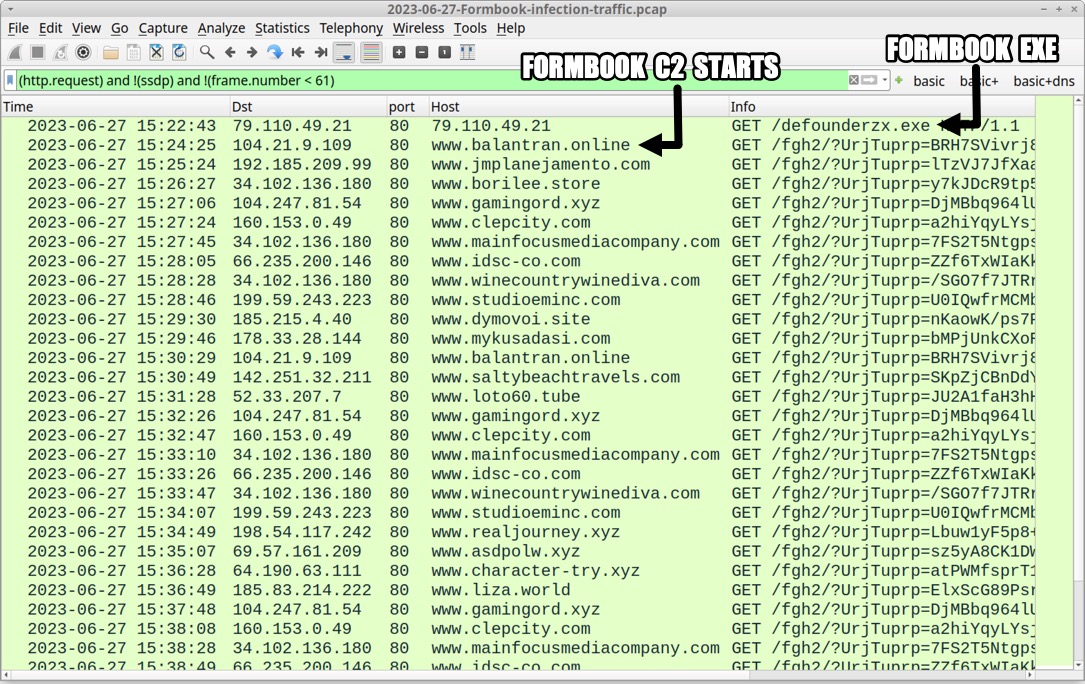
Shown above: Traffic from the infection filtered in Wireshark.
30 DAYS OF FORMBOOK: DAY 23, TUESDAY 2023-06-27 - CVE-2017-11882 RTF ".DOC" --> "FGH2" INFECTION CHAIN: - Email --> attached RTF file with .doc extension --> open RTF ".doc" file in vulnerable version of MS Word --> URL for Formbook EXE --> Formbook infection --> Formbook C2 MALWARE/ARTIFACTS: - SHA256 hash: 132c5242bb6815196b6fba93d32a22735d406b98b0fce6d17e618f3aac192645 - File size: 30,059 bytes - File name: PO28730doc.doc - File type: Rich Text Format data, version 1 - File description: RTF document with CVE-2017-11882 exploit for Microsoft Office - SHA256 hash: c81c9ba400d187e3f9ddbc3c9b31a5ac9ae2d102969a30d0896b19efd1981ceb - File size: 549,888 bytes - File location: hxxp[:]//79.110.49[.]21/defounderzx.exe - Persistent file location: C:\Program Files (x86)\Muxl\cfvyhl0vxeh.exe - File type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows - File description: Windows EXE for Formbook version 4.1 PERSISTENCE: - Windows Registry key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run - Value name: FLJPPLEHT - Value type: REG_SZ - Value Data: C:\Program Files (x86)\Muxl\cfvyhl0vxeh.exe DATA STORED FOR EXFILTRATION TO FORMBOOK C2 SERVER: - C:\Users\[username]\AppData\Roaming\11-P7A7T\11-log.ini - 0 bytes - C:\Users\[username]\AppData\Roaming\11-P7A7T\11-logim.jpeg (screenshot of desktop) - C:\Users\[username]\AppData\Roaming\11-P7A7T\11-logrc.ini (Outlook Recovery) - C:\Users\[username]\AppData\Roaming\11-P7A7T\11-logrf.ini (Firefox Recovery) - C:\Users\[username]\AppData\Roaming\11-P7A7T\11-logrg.ini (Chrome Recovery) - C:\Users\[username]\AppData\Roaming\11-P7A7T\11-logri.ini (Iexplore Recovery) - C:\Users\[username]\AppData\Roaming\11-P7A7T\11-logrv.ini (__Vault Recovery) - Note: All the above files were deleted after data exfiltation, except for first file at 0 bytes. FORMBOOK HTTP GET AND POST REQUESTS: - GET /fgh2/?[string of alphanumeric characters with the following mixed in: = _ + and /] - POST /fgh2/ DOMAINS THAT DID NOT RESOLVE: - DNS query for www.chk7[.]com - no response from DNS server - DNS query for www.xn--12c1cc1b5dd4n[.]com - no response from DNS server - DNS query for www.acadiatesol[.]com - response: No such name - DNS query for www.aigpthome[.]net - response: No such name - DNS query for www.betalingenpayconiq[.]com - response: No such name - DNS query for www.developmentcollective[.]shop - response: No such name - DNS query for www.dollarbillstore[.]com - response: No such name - DNS query for www.dw85[.]xyz - response: No such name - DNS query for www.fantasywagon[.]store - response: No such name - DNS query for www.ffdreakfas514[.]com - response: No such name - DNS query for www.magadonian[.]club - response: No such name - DNS query for www.newenglandsign[.]company - response: No such name - DNS query for www.oconnerflatiron[.]com - response: No such name - DNS query for www.redluckycat[.]com - response: No such name - DNS query for www.southfloridapaintings[.]com - response: No such name - DNS query for www.theinfluencerlink[.]com - response: No such name - DNS query for www.varsasenindir[.]com - response: No such name - DNS query for www.vlokproducties[.]com - response: No such name - DNS query for www.xionqi88[.]com - response: No such name - DNS query for www.70555[.]top - no IP returned from DNS server - DNS query for www.teshack[.]world - no IP returned from DNS server DOMAINS USED FOR FORMBOOK GET REQUESTS: - Note: These appear to be legitimate websites or parked domain pages. - www.33811[.]xyz - www.aimedicarecoverage[.]com - www.balantran[.]online - www.borilee[.]store - www.cdbsoi[.]com - www.character-try[.]xyz - www.chickos[.]bio - www.dymovoi[.]sjte - www.ekinarslan[.]com - www.fensterapp[.]com - www.fredinformatica[.]store - www.intuityx[.]com - www.jeple[.]xyz - www.jmplanejamento[.]com - www.kjszm[.]top - www.ky55[.]xyz - www.kzbjt[.]com - www.loto60[.]tube - www.mykusadasi[.]com - www.niagaraportthorold[.]com - www.ppzwb[.]top - www.realjourney[.]xyz - www.rule34[.]monster - www.tokempoocket[.]com DOMAINS USED FOR FORMBOOK GET AND POST REQUESTS: - Note: These appear to be legitimate websites or parked domain pages. - www.artmartco[.]com - www.asdpolw[.]xyz - www.buygelpen[.]com - www.clepcity[.]com - www.gamingord[.]xyz - www.idsc-co[.]com - www.liza[.]world - www.mainfocusmediacompany[.]com - www.saltybeachtravels[.]com - www.studioeminc[.]com - www.winecountrywinediva[.]com
Click here to return to the main page.
