30 DAYS OF FORMBOOK: DAY 24, WEDNESDAY 2023-06-28 - "RX63"
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- This the is my 24th of 30 infection runs for recent Formbook activity.
ASSOCIATED FILES:
- 2023-06-28-IOCs-for-Formbook-infection.txt.zip 2.0 kB (1,965 bytes)
- 2023-06-28-Formbook-malspam-0825-UTC.eml.zip 362 kB (362,355 bytes)
- 2023-06-28-Formbook-infection-traffic.pcap.zip 6.4 MB (6,387,306 bytes)
- 2023-06-28-Formbook-malware-and-artifacts.zip 825 kB (824,783 bytes)
IMAGES
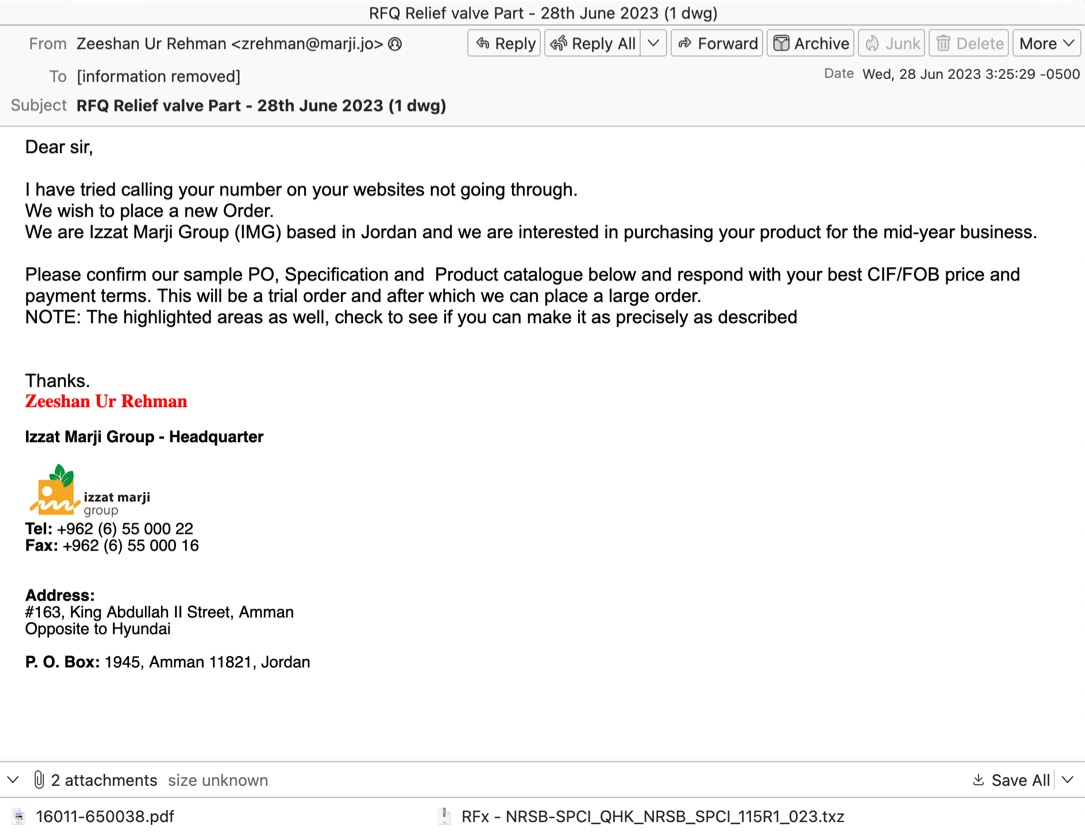
Shown above: Screenshot of email distributing Formbook.

Shown above: Formbook EXE in the RAR arhive.
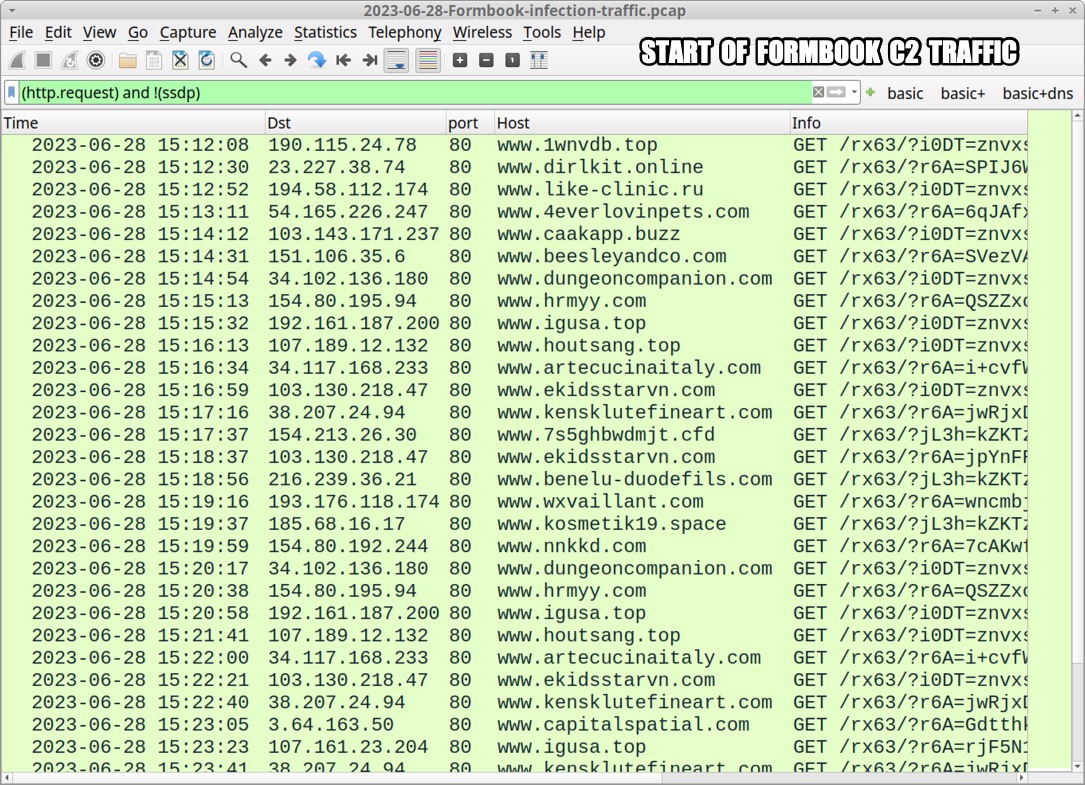
Shown above: Traffic from the infection filtered in Wireshark.
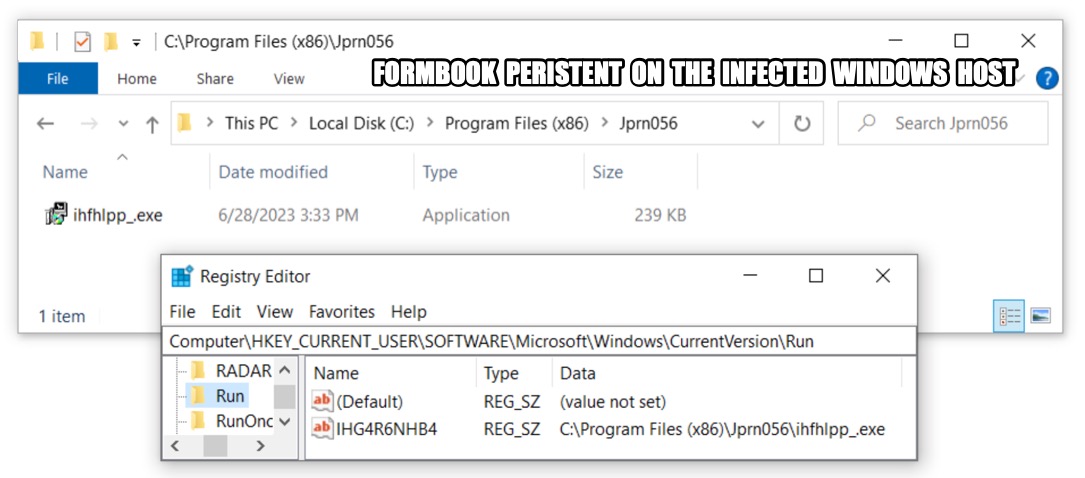
Shown above: Formbook persistent on the infected Windows host.
30 DAYS OF FORMBOOK: DAY 24, WEDNESDAY 2023-06-28 - "RX63" INFECTION CHAIN: - Email --> attached RAR archive --> extracted Formbook EXE --> victim runs Formbook EXE MALWARE/ARTIFACTS: - SHA256 hash: 9eeb0e4740e10819a0d2ecf0a3c7dd93d7ec6348106366f8fff268746aea00e8 - File size: 228,534 bytes - File name: RFx - NRSB-SPCI_QHK_NRSB_SPCI_115R1_023.txz - File type: RAR archive data, v5 - File description: RAR archive containing Formbook EXE - SHA256 hash: 011765b154e93fd26afc6331fa7330996162cd8b9ae00c938a630e6bcca2cc0f - File size: 244,469 bytes - File name: RFx - NRSB-SPCI_QHK_NRSB_SPCI_115R1_023.exe - Persistent file location: C:\Program Files (x86)\Jprn056\ihfhlpp_.exe - File type: PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive - File description: Windows EXE for Formbook version 4.1 PERSISTENCE: - Windows Registry key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run - Value name: IHG4R6NHB4 - Value type: REG_SZ - Value Data: C:\Program Files (x86)\Jprn056\ihfhlpp_.exe DATA STORED FOR EXFILTRATION TO FORMBOOK C2 SERVER: - C:\Users\[username]\AppData\Roaming\609130U8\609log.ini - 0 bytes - C:\Users\[username]\AppData\Roaming\609130U8\609logim.jpeg (screenshot of desktop) - C:\Users\[username]\AppData\Roaming\609130U8\609logrc.ini (Outlook Recovery) - C:\Users\[username]\AppData\Roaming\609130U8\609logrf.ini (Firefox Recovery) - C:\Users\[username]\AppData\Roaming\609130U8\609logrg.ini (Chrome Recovery) - C:\Users\[username]\AppData\Roaming\609130U8\609logri.ini (Iexplore Recovery) - C:\Users\[username]\AppData\Roaming\609130U8\609logrv.ini (__Vault Recovery) - Note: All the above files were deleted after data exfiltation, except for first file at 0 bytes. FORMBOOK HTTP GET AND POST REQUESTS: - GET /rx63/?[string of alphanumeric characters with the following mixed in: = _ + and /] - POST /rx63/ DOMAINS THAT DID NOT RESOLVE: - DNS query for www.lavarlaropa[.]com - no response from DNS server - DNS query for www.vapeaid[.]africa - no response from DNS server - DNS query for www.visiogeomatics[.]africa - no response from DNS server - DNS query for www.aaataxassistants[.]com - response: No such name - DNS query for www.beawallhdmp4[.]com - response: No such name - DNS query for www.begladgardens[.]com - response: No such name - DNS query for www.bmg[.]social - response: No such name - DNS query for www.dotnetfashions[.]com - response: No such name - DNS query for www.efefcause[.]buzz - response: No such name - DNS query for www.elegantshopee[.]com - response: No such name - DNS query for www.prepandgo[.]net - response: No such name - DNS query for www.odinzsky[.]net - no IP returned from DNS server DOMAINS THAT RESOLVED, BUT NO CONNECTION TO SERVER: - port 80 - www.25736[.]football - TCP SYN segments only, no response or RST from server DOMAINS USED FOR FORMBOOK GET REQUESTS: - Note: These appear to be legitimate websites or parked domain pages. - www.1wnvdb[.]top - www.4everlovinpets[.]com - www.7s5ghbwdmjt[.]cfd - www.ailawesquire[.]com - www.amazing-cajun[.]com - www.aretealternatives[.]com - www.beesleyandco[.]com - www.biographtheater[.]com - www.bitprice[.]cash - www.brainstormbotanics[.]com - www.caakapp[.]buzz - www.cadomarketing[.]com - www.capitalspatial[.]com - www.chinacya[.]com - www.covenantchurchag[.]com - www.groomersfirstchoice[.]com - www.kitchenpharmacy[.]co[.]uk - www.kosmetik19[.]space - www.laurellawncare[.]com - www.like-clinic[.]ru - www.nnkkd[.]com - www.wxvaillant[.]com DOMAINS USED FOR FORMBOOK GET AND POST REQUESTS: - Note: These appear to be legitimate websites or parked domain pages. - www.artecucinaitaly[.]com ** - www.benelu-duodefils[.]com ** - www.bipartisan[.]one - www.birslot[.]xyz - www.brixu[.]xyz ** - www.cenik[.]biz - www.dirlkit[.]online ** - www.dollardstown[.]com ** - www.dualio[.]tech - www.dungeoncompanion[.]com - www.ekidsstarvn[.]com ** - www.houtsang[.]top - www.hrmyy[.]com ** - www.igusa[.]top - www.kensklutefineart[.]com ** - Full stolen data (encoded) sent through HTTP POST request.
Click here to return to the main page.
