2023-07-25 (TUESDAY): ICEDID (BOKBOT) INFECTION FROM WAVE OF MALSPAM ON MONDAY 2023-07-24
NOTICE:
- Of note, the zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2023-07-25-IcedID-notes.txt.zip 1.8 kB (1,808 bytes)
- 2023-07-25-IcedID-infection-traffic.pcap.zip 4.7 MB (4,700,409 bytes)
- 2023-07-25-IcedID-malware-and-artifacts.zip 2.1 MB (2,063,101 bytes)
- 2023-07-25-IcedID-with-Keyhole-VNC-traffic.pcap.zip 11.2 MB (11,244,832 bytes)
IMAGES
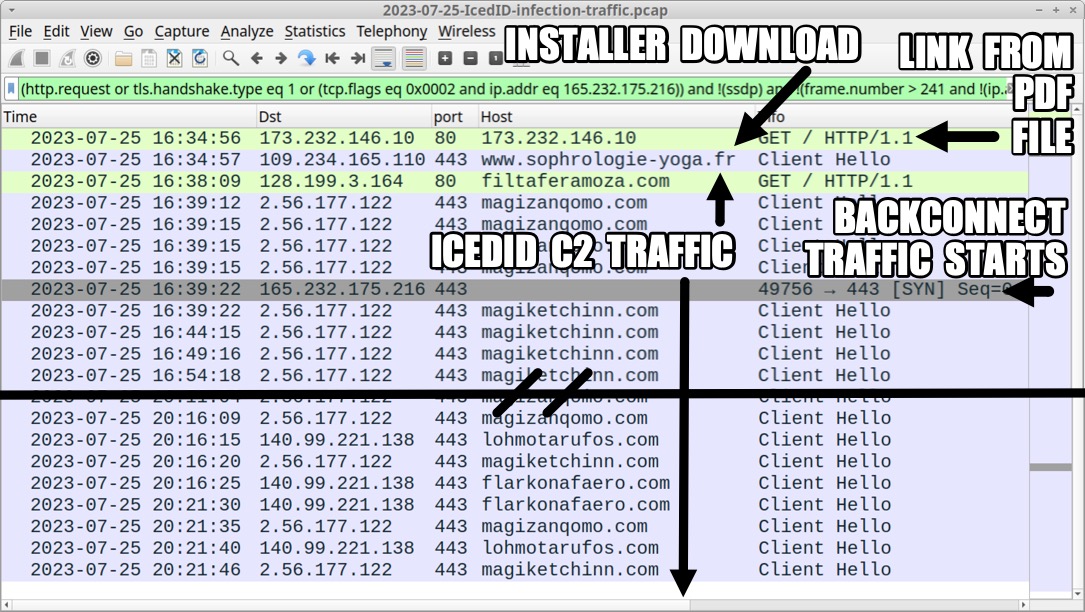
Shown above: Trasffic from the infection filtered in Wireshark.
2023-07-25 (TUESDAY): ICEDID (BOKBOT) INFECTION FROM WAVE OF MALSPAM ON MONDAY 2023-07-24
REFERENCES:
- https://twitter.com/k3dg3/status/1683544196341219341
- https://twitter.com/JAMESWT_MHT/status/1683747418641252360
- https://twitter.com/Tac_Mangusta/status/1683741137784147969
- https://bazaar.abuse.ch/browse/tag/1561373935/
- https://tria.ge/s/campaign:1561373935
INFECTION CHAIN:
- email --> PDF attachment --> link from PDF --> TDS redirect --> zip download --> run extracted EXE --> IcedID infection
ASSOCIATED FILES:
- SHA256 hash: 8715a27a8a263f59335601258c584963cc50822d2c24ba81a9d1b33b48753a70
- File size: 86,558 bytes
- File name: INV-Details-JUL23.pdf
- File type: PDF document, version 1.4, 1 pages
- File description: example of PDF file attachment
- SHA256 hash: fed2651d0e6ef1a2bb6283dba0c52a24a90b3b69ae2b8f08b883dcc6d8ecf4a1
- File size: 185,994 bytes
- File name: INV-Details-JUL2023(14).zip
- File type: Zip archive data, at least v2.0 to extract, compression method=deflate
- File description: example of password-protected zip archive
- Password: 724
- SHA256 hash: 2cf9bef62939a9b645d43d05959e181f3962e7f10c9e4d73288c7f36af7d5ec2
- File size: 458,416 bytes
- File name: INV-Details-JUL2023(14).exe
- File type: PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows
- File description: extracted from the above zip archive, installer EXE for IcedID
- SHA256 hash: 729a9743319f548134a1535291bea0bfdac6cd9a8c4c9ba19ab1b8524d5ebea7
- File size: 1,036,133 bytes
- File location: hxxp[:]//filtaferamoza[.]com/
- File type: gzip compressed data, was "Pledge.txt", from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 2501970
- File description: gzip binary used to create persistent IcedID DLL and license.dat data binary
- SHA256 hash: 332afc80371187881ef9a6f80e5c244b44af746b20342b8722f7b56b61604953
- File size: 354,474 bytes
- File location: C:\Users\user\AppData\Roaming\DisplayBronze\license.dat
- File type: data
- File description: data binary needed to run persistent IcedID DLL
- SHA256 hash: 110ca2ce6308f2731162fa5acf0dd8a89ff22d4c545702c0118c1bccf43e9bee
- File size: 680,904 bytes
- File location: C:\Users\user\AppData\Roaming\user\{45613AD5-6C95-8231-C86F-BF8027DF7176}\Afebwc.dll
- File type: PE32+ executable (DLL) (GUI) x86-64, for MS Windows
- File description: Persistent DLL for IcedID infection
- Run method: rundll32 [filename],init --abim="[path to license.dat]"
LINK FROM PDF:
- 173.232.146[.]10 port 80 - 173.232.146[.]10 - GET /
TDS REDIRECT FOR ZIP DOWNLOAD:
- 109.234.165[.]110 port 443 - hxxps[:]//www.sophrologie-yoga[.]fr/palatial/
INSTALLER EXE CALLS FOR GZIP BINARY:
- 128.199.3[.]164 port 80 - filtaferamoza[.]com - GET /
ICEDID HTTPS C2:
- 2.56.177[.]122 port 443 - magizanqomo[.]com - HTTPS traffic
- 2.56.177[.]122 port 443 - magiketchinn[.]com - HTTPS traffic
- 140.99.221[.]138 port 443 - lohmotarufos[.]com - HTTPS traffic
- 140.99.221[.]138 port 443 - flarkonafaero[.]com - HTTPS traffic
BACKCONNECT TRAFFIC/KEYHOLE VNC IP AND PORT:
- 165.232.175[.]216 port 443 - encoded/encrypted traffic (no Keyhole VNC during initial pcap)
NOTE:
- I started up the Windows host the next day and saw also saw Keyhole VNC traffic from the continued IcedID infection.
- I've added a pcap of this infection traffic with Keyhole VNC: 2023-07-26-IcedID-with-Keyhole-VNC-traffic.pcap.zip
Click here to return to the main page.
